0 Reacties
0 aandelen
23 Views

Bedrijvengids
Bedrijvengids
-
Please log in to like, share and comment!
-
 WWW.ZDNET.COMData-stealing cyberattacks are surging - 7 ways to protect yourself and your businessThe number of infostealers sent through phishing emails jumped by 84% last year. IBM X-Force offers these recommendations for defending yourself from all manner of malware.0 Reacties 0 aandelen 41 Views
WWW.ZDNET.COMData-stealing cyberattacks are surging - 7 ways to protect yourself and your businessThe number of infostealers sent through phishing emails jumped by 84% last year. IBM X-Force offers these recommendations for defending yourself from all manner of malware.0 Reacties 0 aandelen 41 Views -
 WWW.FORBES.COMOvercoming AI Adoption Barriers In Legal With An Embedded ApproachBy embedding AI at the platform level, firms can also support new and emerging use cases without needing to invest in additional technology.0 Reacties 0 aandelen 33 Views
WWW.FORBES.COMOvercoming AI Adoption Barriers In Legal With An Embedded ApproachBy embedding AI at the platform level, firms can also support new and emerging use cases without needing to invest in additional technology.0 Reacties 0 aandelen 33 Views -
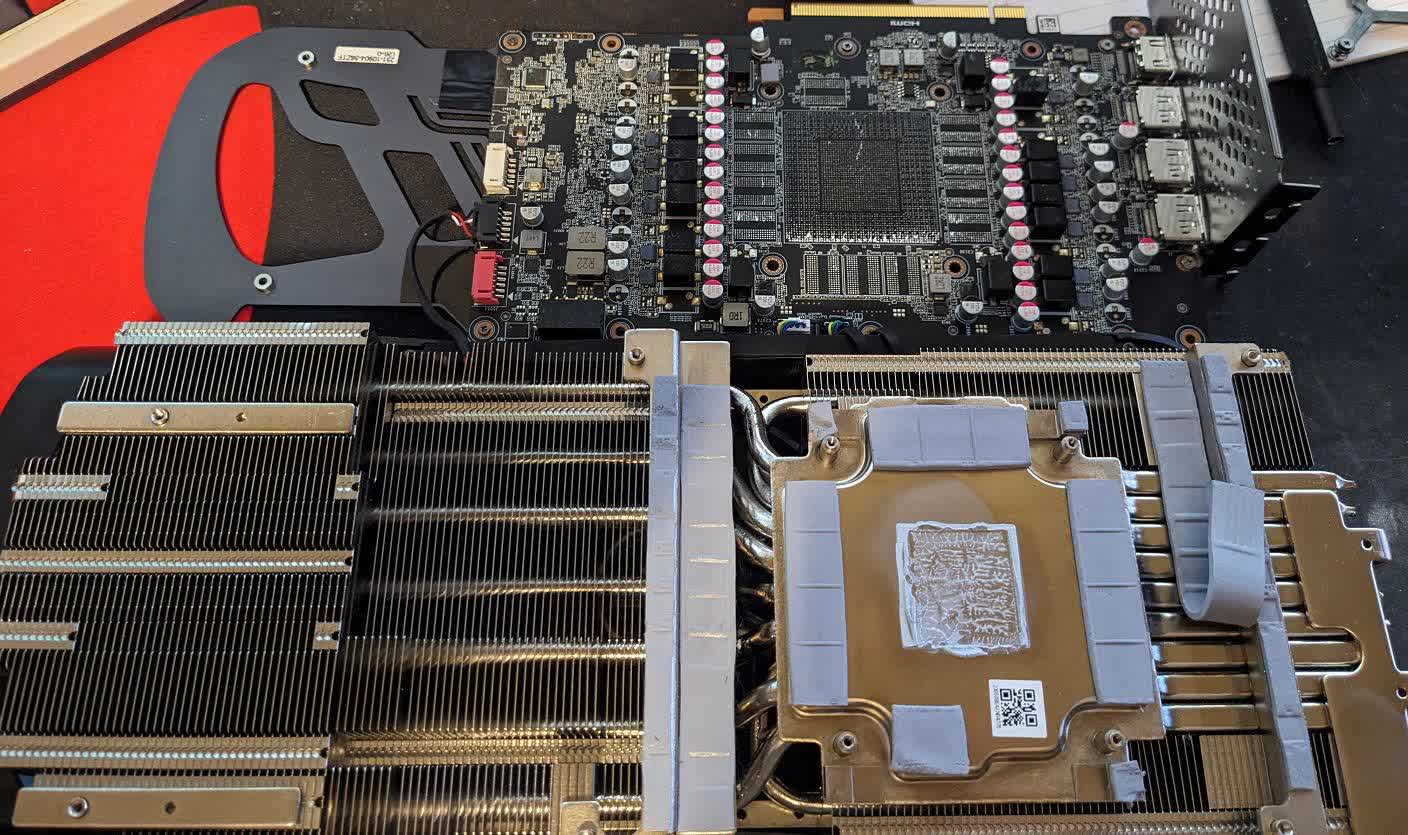 WWW.TECHSPOT.COMNvidia RTX 4090 eBay seller scammed by buyer who returned card with GPU and VRAM removedWTF?! It's a sad truth that there are always risks when buying and selling second hand. But one would assume dealing with an eBay store that has lots of positive feedback wouldn't be dangerous. The person who sold their RTX 4090 to the company, only to have it returned without the GPU or VRAM chips, would likely disagree. The graphics card industry right now is as bad as it was in the pandemic/chip crisis era of sky-high prices and nearly no stock. It's led to the second-hand market becoming a Wild West of opportunists and shady businesses. A Redditor called piscian19 discovered this when he sold his RTX 4090 on eBay a couple of weeks ago. He writes that the buyer had feedback from over 30,000 previous transaction and a storefront. Piscian19 notes that there were some elements of the sale that raised suspicions, including why a business would pay retail price for a card. The California-based business' name, which isn't revealed, also seemed "odd." Out of caution, the Redditor protected himself by taking plenty of pictures of the Lovelace flagship and purchasing the most comprehensive insurance and tracking. It turned out to be a wise decision. On the same day that the business received the card, it started a return due to the problem of "no video." But the RTX 4090 was apparently "pristine" and barely used. // Related Stories All was revealed when the card was returned to the seller. The mounting bracket was bent and a couple of wires were crossed on the RGB, indicating it had been taken apart by the buyer. Piscian19 called eBay, who told him to keep the card and the money he was paid for it. The auction site also gave the buyer a one-time refund. In the hope that the card could be salvaged, piscian19 repaired the bracket, started an RMA, and then decided to strip the card before shipping it. Exposing the internals revealed that the buyer had removed the GPU and VRAM chips. A follow-up comment on Reddit reveals that the buyer has been reported to the Better Business Bureau several times for fraud. It also sells RTX 4090s for up to $4,000. The amount of positive feedback does seem strange, leading to some suggestions that it may have been a hacked account. Piscian19 reported the business to eBay's fraud department and a couple of investigative organizations. Back in November 2023, it was reported that Chinese companies were stripping RTX 4090s of their components. These ended up in makeshift "AI" solutions with blower-style coolers destined for China's artificial intelligence market. What was happening to some of these stripped RTX 4090s became apparent early last year when a buyer of a second hand model found it had no GPU or VRAM chips.0 Reacties 0 aandelen 33 Views
WWW.TECHSPOT.COMNvidia RTX 4090 eBay seller scammed by buyer who returned card with GPU and VRAM removedWTF?! It's a sad truth that there are always risks when buying and selling second hand. But one would assume dealing with an eBay store that has lots of positive feedback wouldn't be dangerous. The person who sold their RTX 4090 to the company, only to have it returned without the GPU or VRAM chips, would likely disagree. The graphics card industry right now is as bad as it was in the pandemic/chip crisis era of sky-high prices and nearly no stock. It's led to the second-hand market becoming a Wild West of opportunists and shady businesses. A Redditor called piscian19 discovered this when he sold his RTX 4090 on eBay a couple of weeks ago. He writes that the buyer had feedback from over 30,000 previous transaction and a storefront. Piscian19 notes that there were some elements of the sale that raised suspicions, including why a business would pay retail price for a card. The California-based business' name, which isn't revealed, also seemed "odd." Out of caution, the Redditor protected himself by taking plenty of pictures of the Lovelace flagship and purchasing the most comprehensive insurance and tracking. It turned out to be a wise decision. On the same day that the business received the card, it started a return due to the problem of "no video." But the RTX 4090 was apparently "pristine" and barely used. // Related Stories All was revealed when the card was returned to the seller. The mounting bracket was bent and a couple of wires were crossed on the RGB, indicating it had been taken apart by the buyer. Piscian19 called eBay, who told him to keep the card and the money he was paid for it. The auction site also gave the buyer a one-time refund. In the hope that the card could be salvaged, piscian19 repaired the bracket, started an RMA, and then decided to strip the card before shipping it. Exposing the internals revealed that the buyer had removed the GPU and VRAM chips. A follow-up comment on Reddit reveals that the buyer has been reported to the Better Business Bureau several times for fraud. It also sells RTX 4090s for up to $4,000. The amount of positive feedback does seem strange, leading to some suggestions that it may have been a hacked account. Piscian19 reported the business to eBay's fraud department and a couple of investigative organizations. Back in November 2023, it was reported that Chinese companies were stripping RTX 4090s of their components. These ended up in makeshift "AI" solutions with blower-style coolers destined for China's artificial intelligence market. What was happening to some of these stripped RTX 4090s became apparent early last year when a buyer of a second hand model found it had no GPU or VRAM chips.0 Reacties 0 aandelen 33 Views -
 WWW.DIGITALTRENDS.COMMicrosoft’s Copilot Vision AI is now free to use, but only for these 9 sitesAfter months of teasers, previews, and select rollouts, Microsoft’s Copilot Vision is now available to try for all Edge users in the U.S. The flashy new AI tool is designed to watch your screen as you browse so you can ask it various questions about what you’re doing and get useful context-appropriate responses. The main catch, however, is that it currently only works with nine websites. For the most part, these nine websites seem like pretty random choices, too. We have Amazon, which makes sense, but also Geoguessr? I’m pretty sure the point of that site is to try and guess where you are on the map without any help. Anyway, the full site list is as follows: Wikipedia Tripadvisor Williams Sonoma Amazon Target Wayfair Food & Wine OpenTable Geoguessr Recommended Videos CEO of Microsoft AI Mustafa Suleyman announced the release on Bluesky yesterday and shared a few of his favorite use cases. Usually, when you want to ask Copilot a question, you have to write out the paragraphs of context yourself, and aside from being slow and annoying, this can also be pretty difficult if you’re trying to ask about something you don’t know much about. Related With Copilot Vision, instead of trying to describe what you’re looking at or what you’re talking about, the AI model can see it right on your screen. So, according to Suleyman’s examples, you can search for “breathable sheets” on Amazon and ask Copilot if any of the results are made from appropriate fabrics. Copilot can point the right ones out to you or give you examples of breathable fabric to search for. On the Food & Wine recipe website, Copilot can help you go hands-free while you cook by answering your questions and reading out parts of the recipe to you. This works because the whole experience is designed to work through voice — you speak directly to the AI and the AI speaks back. According to one of the videos on the Copilot Vision page, however, it looks like you can type out questions too and receive written responses. Microsoft is taking things very slowly and carefully with this feature, almost certainly because it wants to avoid triggering another backlash like it did with Recall. The limited number of compatible sites is connected to copyright issues, and the company makes sure to stress that the feature is “opt-in,” doesn’t record your screen, is only on when you turn it on, and deletes the data as soon as you end a session. If you’re interested in testing it out, you can set things up and see a little tutorial through the Microsoft website. Editors’ Recommendations0 Reacties 0 aandelen 30 Views
WWW.DIGITALTRENDS.COMMicrosoft’s Copilot Vision AI is now free to use, but only for these 9 sitesAfter months of teasers, previews, and select rollouts, Microsoft’s Copilot Vision is now available to try for all Edge users in the U.S. The flashy new AI tool is designed to watch your screen as you browse so you can ask it various questions about what you’re doing and get useful context-appropriate responses. The main catch, however, is that it currently only works with nine websites. For the most part, these nine websites seem like pretty random choices, too. We have Amazon, which makes sense, but also Geoguessr? I’m pretty sure the point of that site is to try and guess where you are on the map without any help. Anyway, the full site list is as follows: Wikipedia Tripadvisor Williams Sonoma Amazon Target Wayfair Food & Wine OpenTable Geoguessr Recommended Videos CEO of Microsoft AI Mustafa Suleyman announced the release on Bluesky yesterday and shared a few of his favorite use cases. Usually, when you want to ask Copilot a question, you have to write out the paragraphs of context yourself, and aside from being slow and annoying, this can also be pretty difficult if you’re trying to ask about something you don’t know much about. Related With Copilot Vision, instead of trying to describe what you’re looking at or what you’re talking about, the AI model can see it right on your screen. So, according to Suleyman’s examples, you can search for “breathable sheets” on Amazon and ask Copilot if any of the results are made from appropriate fabrics. Copilot can point the right ones out to you or give you examples of breathable fabric to search for. On the Food & Wine recipe website, Copilot can help you go hands-free while you cook by answering your questions and reading out parts of the recipe to you. This works because the whole experience is designed to work through voice — you speak directly to the AI and the AI speaks back. According to one of the videos on the Copilot Vision page, however, it looks like you can type out questions too and receive written responses. Microsoft is taking things very slowly and carefully with this feature, almost certainly because it wants to avoid triggering another backlash like it did with Recall. The limited number of compatible sites is connected to copyright issues, and the company makes sure to stress that the feature is “opt-in,” doesn’t record your screen, is only on when you turn it on, and deletes the data as soon as you end a session. If you’re interested in testing it out, you can set things up and see a little tutorial through the Microsoft website. Editors’ Recommendations0 Reacties 0 aandelen 30 Views -
WWW.WSJ.COMMarketers Are Putting More Content and Quality Control in the Hands of AIThe arrival of marketing campaigns generated entirely by artificial intelligence is inevitable, consultants say.0 Reacties 0 aandelen 30 Views
-
WWW.WSJ.COMAccountants Finally Get the Sequel to Their Favorite Film: ‘The Accountant’CPAs are geeked for the morale boost that only the bean-counting badass in the movie can provide; ‘It’s our ‘John Wick.‘’0 Reacties 0 aandelen 30 Views
-
 ARSTECHNICA.COMGovernment IT whistleblower calls out DOGE, says he was threatened at homeDOGE whistle Government IT whistleblower calls out DOGE, says he was threatened at home "Stay out of DOGE's way": IT worker details how Musk group infiltrated US agency. Jon Brodkin – Apr 16, 2025 3:04 pm | 50 Elon Musk at the White House on March 9, 2025 in Washington, DC. Credit: Getty Images | Samuel Corum Elon Musk at the White House on March 9, 2025 in Washington, DC. Credit: Getty Images | Samuel Corum Story text Size Small Standard Large Width * Standard Wide Links Standard Orange * Subscribers only Learn more A government whistleblower told lawmakers that DOGE's access to National Labor Relations Board (NLRB) systems went far beyond what was needed to analyze agency operations and apparently led to a data breach. NLRB employee Daniel Berulis, a DevSecOps architect, also says he received a threat when he was preparing his whistleblower disclosure. "Mr. Berulis is coming forward today because of his concern that recent activity by members of the Department of Government Efficiency ('DOGE') have resulted in a significant cybersecurity breach that likely has and continues to expose our government to foreign intelligence and our nation's adversaries," said a letter from the group Whistleblower Aid to the Senate Select Committee on Intelligence leaders and the US Office of Special Counsel. The letter, Berulis' sworn declaration, and an exhibit with screenshots of technical data are available here. "This declaration details DOGE activity within NLRB, the exfiltration of data from NLRB systems, and—concerningly—near real-time access by users in Russia," Whistleblower Aid Chief Legal Counsel Andrew Bakaj wrote. "Notably, within minutes of DOGE personnel creating user accounts in NLRB systems, on multiple occasions someone or something within Russia attempted to login using all of the valid credentials (e.g. Usernames/Passwords). This, combined with verifiable data being systematically exfiltrated to unknown servers within the continental United States—and perhaps abroad—merits investigation." Bakaj said they notified law enforcement about an "absolutely disturbing" threat Berulis received on April 7. Someone "taped a threatening note to Mr. Berulis' home door with photographs—taken via a drone—of him walking in his neighborhood," Bakaj wrote. "The threatening note made clear reference to this very disclosure he was preparing for you, as the proper oversight authority. While we do not know specifically who did this, we can only speculate that it involved someone with the ability to access NLRB systems." NLRB denies breach Berulis' disclosure said that several days before receiving this threat, he had been instructed to drop his investigation and not report his concerns to US security officials. Bakaj's letter to senators and the Office of Special Counsel requested "that both law enforcement agencies and Congress initiate an immediate investigation into the cybersecurity breach and data exfiltration at NLRB and any other agencies where DOGE has accessed internal systems." An NLRB spokesperson denied that there was any breach. "Tim Bearese, the NLRB's acting press secretary, denied that the agency granted DOGE access to its systems and said DOGE had not requested access to the agency's systems," according to NPR. "Bearese said the agency conducted an investigation after Berulis raised his concerns but 'determined that no breach of agency systems occurred.'" We contacted the NLRB and will update this article if it provides further comment. There have been numerous lawsuits over the access to government systems granted to DOGE, the Trump administration entity led by Elon Musk. One such lawsuit described DOGE's access as "the largest and most consequential data breach in US history." There have been mixed results in the cases so far; a US appeals court decided last week that DOGE can access personal data held by the US Department of Education and Office of Personnel Management (OPM), overturning a lower-court ruling. After the whistleblower disclosure, US Rep. Gerry Connolly (D-Va.) sent a letter urging inspectors general at the NLRB and Department of Labor to investigate. Connolly said the whistleblower report indicates "that Department of Government Efficiency (DOGE) employees may be engaged in technological malfeasance and illegal activity at the National Labor Relations Board (NLRB) and the Department of Labor (DOL)." Connolly asked for a report to Congress on "the nature of the work the DOGE team has performed at NLRB and DOL, including any and all attempts to exfiltrate data and any attempts to cover up their activities." Because of Musk's role at DOGE and the fact that his "companies face a series of enforcement actions from NLRB and DOL," there is "an inherent conflict of interest for him to direct any work at either agency—let alone benefit from stolen nonpublic information," Connolly wrote. Login attempts from Russia Berulis' disclosure said that on March 11, internal metrics indicated there had been "abnormal usage" over the past week with higher-than-usual response times and "increased network output above anywhere it had been historically." When examining the data, "we noticed a user with an IP address in Primorsky Krai, Russia started trying to log in. Those attempts were blocked, but they were especially alarming," he wrote. The person logging in from Russia apparently had the correct credentials for a DOGE account, according to Berulis. "Whoever was attempting to log in was using one of the newly created accounts that were used in the other DOGE-related activities, and it appeared they had the correct username and password due to the authentication flow only stopping them due to our no-out-of-country logins policy activating," he wrote. "There were more than 20 such attempts, and what is particularly concerning is that many of these login attempts occurred within 15 minutes of the accounts being created by DOGE engineers." This was not the first troubling sign described in the disclosure. On March 7, Berulis says he had "started tracking what appeared to be sensitive data leaving the secured location." About 10GB of data was exfiltrated, but it was "unclear which files were copied and removed," he wrote. Berulis said the evidence indicated there was "a data breach facilitated by an internal actor," and that he observed "the exact behaviors (Indicators of Compromise) of one who was trying to erase records of activities, retard detection, and covertly hide what data was being extracted after the fact." The NLRB hosts lots of private information that is supposed to remain confidential, he noted. This includes "sensitive information on unions, ongoing legal cases, and corporate secrets." The database involved in the apparent breach contains "PII [personally identifiable information] of claimants and respondents with pending matters before the agency" and confidential business information "gathered or provided during investigations and litigation that were not intended for public release," he wrote. Berulis has almost two decades of experience, and his "work often includes high-level coordination with executive teams, establishing red-blue war game security events, and building cross-functional teams to align IT capabilities with mission-critical goals," he said in his declaration. "Having worked at sensitive US Government institutions, I have held a Top Secret security clearance with eligibility for access to Sensitive Compartmented Information, commonly known as TS/SCI." “Stay out of DOGE’s way” In late February, Berulis and his team were notified of DOGE's impending arrival. "On or around March 3, 2025, we saw a black SUV and police escort enter the garage, after which building security let the DOGE staffers in. They interacted with only a small group of NLRB staff, never introducing themselves to those of us in Information Technology," he wrote. An assistant chief information officer (ACIO) was given instructions that IT employees "were not to adhere to SOP [standard operating procedure] with the DOGE account creation in regards to creating records," Berulis wrote. "He specifically was told that there were to be no logs or records made of the accounts created for DOGE employees." DOGE officials were to be given "the highest level of access and unrestricted access to internal systems," specifically "tenant owner" accounts in Microsoft Azure that come "with essentially unrestricted permission to read, copy, and alter data," Berulis wrote. These "permissions are above even my CIO's access level to our systems" and "well above what level of access is required to pull metrics, efficiency reports, and any other details that would be needed to assess utilization or usage of systems in our agency." The NLRB systems "have built-in roles that auditors can use and have used extensively in the past," which do not have "the ability to make changes or access subsystems without approval," Berulis wrote. DOGE apparently wasn't willing to use these accounts. "The suggestion that they use these accounts instead was not open to discussion," he wrote. Berulis said IT staff were ordered "to hand over any requested accounts, stay out of DOGE's way entirely, and assist them when they asked. We were further directed not to resist them in any way or deny them any access." More suspicious events Berulis described several more suspicious events that followed DOGE's arrival. There was a new container that he described as "basically an opaque, virtual node that has the ability to build and run programs or scripts without revealing its activities to the rest of the network." There was also a token that "was configured to expire quickly after creation and use, making it harder to gain insight into what it was used for during its lifetime." To Berulis, these were signs of an attack on the NLRB systems. The methods used seemed to reflect "the desire of the attackers to work invisibly, leaving little to no obvious trace of their activities once removed." On March 6, various users "reported login issues to the service desk and, upon inspection, I found some conditional access policies were updated recently," he wrote. This was odd because "policies that had been in place for over a year were suddenly found to have been changed with no corresponding documentation or approvals," he wrote. "Upon my discovery of these changes, I asked the security personnel and information assurance team about it, but they had no knowledge of any planned changes or approvals." On March 7, Berulis says he "started tracking what appeared to be sensitive data leaving the secured location." About 10GB of data was exfiltrated, but it was "unclear which files were copied and removed," he wrote. On that same day, Berulis says he reported his concerns about sensitive data being exfiltrated to CIO Prem Aburvasmy. Aburvasmy took the concerns seriously and put together a leadership group "to discuss insider threat response on an ongoing cadence and how we could get better at detecting it," Berulis wrote. "Going forward after this, the team met every Friday and continue to do so to this day." Berulis described some shortcomings in the NLRB's ability to detect attacks. "During one of these meetings, it was confirmed that our team did not have the technical capability to detect or respond in real time to internal threat actors, and that we likely did not have the ability to obtain more details about the past events," he wrote. The department subsequently "shifted budget to allow for better tooling going forward," which "has vastly improved our detection and logging so we can provide more concrete evidence if covert exfiltration occurs by an insider threat again," Berulis wrote. "We also shut down a public endpoint and corrected rogue policies that had been altered to allow much broader traffic in/out of our network." Berulis: “We were directed not to... create an official report” On March 10, Berulis found that controls in Microsoft Purview to prevent insecure or unauthorized access from mobile devices had been disabled, he wrote. "In addition, outside of expected baselines and with no corresponding approvals or records I could find I noted the following: an interface exposed to the public Internet, a few internal alerting and monitoring systems in the off state, and multi-factor authentication changed," he wrote. The team observed more odd activity in the ensuing weeks, Berulis wrote. Data was sent to "an unknown external endpoint," but the network team was unable to obtain connection logs or determine what data was removed, he wrote. There were also "spikes in billing in Mission Systems related to storage input/output" associated with projects that could no longer be found in the NLRB system, indicating that "resources may have been deleted or short-lived," he wrote. During the week of March 24, an assistant CIO for security at the NLRB "concluded that following a review of data, we should report it" to US-CERT, the US Computer Emergency Readiness Team at the Cybersecurity and Infrastructure Security Agency (CISA), according to Berulis. "Accordingly, we launched a formal review and I provided all evidence of what we deemed to be a serious, ongoing security breach or potentially illegal removal of personally identifiable information," he wrote. But on April 3 or 4, the assistant CIO "and I were informed that instructions had come down to drop the US-CERT reporting and investigation and we were directed not to move forward or create an official report," Berulis wrote. Jon Brodkin Senior IT Reporter Jon Brodkin Senior IT Reporter Jon is a Senior IT Reporter for Ars Technica. He covers the telecom industry, Federal Communications Commission rulemakings, broadband consumer affairs, court cases, and government regulation of the tech industry. 50 Comments0 Reacties 0 aandelen 45 Views
ARSTECHNICA.COMGovernment IT whistleblower calls out DOGE, says he was threatened at homeDOGE whistle Government IT whistleblower calls out DOGE, says he was threatened at home "Stay out of DOGE's way": IT worker details how Musk group infiltrated US agency. Jon Brodkin – Apr 16, 2025 3:04 pm | 50 Elon Musk at the White House on March 9, 2025 in Washington, DC. Credit: Getty Images | Samuel Corum Elon Musk at the White House on March 9, 2025 in Washington, DC. Credit: Getty Images | Samuel Corum Story text Size Small Standard Large Width * Standard Wide Links Standard Orange * Subscribers only Learn more A government whistleblower told lawmakers that DOGE's access to National Labor Relations Board (NLRB) systems went far beyond what was needed to analyze agency operations and apparently led to a data breach. NLRB employee Daniel Berulis, a DevSecOps architect, also says he received a threat when he was preparing his whistleblower disclosure. "Mr. Berulis is coming forward today because of his concern that recent activity by members of the Department of Government Efficiency ('DOGE') have resulted in a significant cybersecurity breach that likely has and continues to expose our government to foreign intelligence and our nation's adversaries," said a letter from the group Whistleblower Aid to the Senate Select Committee on Intelligence leaders and the US Office of Special Counsel. The letter, Berulis' sworn declaration, and an exhibit with screenshots of technical data are available here. "This declaration details DOGE activity within NLRB, the exfiltration of data from NLRB systems, and—concerningly—near real-time access by users in Russia," Whistleblower Aid Chief Legal Counsel Andrew Bakaj wrote. "Notably, within minutes of DOGE personnel creating user accounts in NLRB systems, on multiple occasions someone or something within Russia attempted to login using all of the valid credentials (e.g. Usernames/Passwords). This, combined with verifiable data being systematically exfiltrated to unknown servers within the continental United States—and perhaps abroad—merits investigation." Bakaj said they notified law enforcement about an "absolutely disturbing" threat Berulis received on April 7. Someone "taped a threatening note to Mr. Berulis' home door with photographs—taken via a drone—of him walking in his neighborhood," Bakaj wrote. "The threatening note made clear reference to this very disclosure he was preparing for you, as the proper oversight authority. While we do not know specifically who did this, we can only speculate that it involved someone with the ability to access NLRB systems." NLRB denies breach Berulis' disclosure said that several days before receiving this threat, he had been instructed to drop his investigation and not report his concerns to US security officials. Bakaj's letter to senators and the Office of Special Counsel requested "that both law enforcement agencies and Congress initiate an immediate investigation into the cybersecurity breach and data exfiltration at NLRB and any other agencies where DOGE has accessed internal systems." An NLRB spokesperson denied that there was any breach. "Tim Bearese, the NLRB's acting press secretary, denied that the agency granted DOGE access to its systems and said DOGE had not requested access to the agency's systems," according to NPR. "Bearese said the agency conducted an investigation after Berulis raised his concerns but 'determined that no breach of agency systems occurred.'" We contacted the NLRB and will update this article if it provides further comment. There have been numerous lawsuits over the access to government systems granted to DOGE, the Trump administration entity led by Elon Musk. One such lawsuit described DOGE's access as "the largest and most consequential data breach in US history." There have been mixed results in the cases so far; a US appeals court decided last week that DOGE can access personal data held by the US Department of Education and Office of Personnel Management (OPM), overturning a lower-court ruling. After the whistleblower disclosure, US Rep. Gerry Connolly (D-Va.) sent a letter urging inspectors general at the NLRB and Department of Labor to investigate. Connolly said the whistleblower report indicates "that Department of Government Efficiency (DOGE) employees may be engaged in technological malfeasance and illegal activity at the National Labor Relations Board (NLRB) and the Department of Labor (DOL)." Connolly asked for a report to Congress on "the nature of the work the DOGE team has performed at NLRB and DOL, including any and all attempts to exfiltrate data and any attempts to cover up their activities." Because of Musk's role at DOGE and the fact that his "companies face a series of enforcement actions from NLRB and DOL," there is "an inherent conflict of interest for him to direct any work at either agency—let alone benefit from stolen nonpublic information," Connolly wrote. Login attempts from Russia Berulis' disclosure said that on March 11, internal metrics indicated there had been "abnormal usage" over the past week with higher-than-usual response times and "increased network output above anywhere it had been historically." When examining the data, "we noticed a user with an IP address in Primorsky Krai, Russia started trying to log in. Those attempts were blocked, but they were especially alarming," he wrote. The person logging in from Russia apparently had the correct credentials for a DOGE account, according to Berulis. "Whoever was attempting to log in was using one of the newly created accounts that were used in the other DOGE-related activities, and it appeared they had the correct username and password due to the authentication flow only stopping them due to our no-out-of-country logins policy activating," he wrote. "There were more than 20 such attempts, and what is particularly concerning is that many of these login attempts occurred within 15 minutes of the accounts being created by DOGE engineers." This was not the first troubling sign described in the disclosure. On March 7, Berulis says he had "started tracking what appeared to be sensitive data leaving the secured location." About 10GB of data was exfiltrated, but it was "unclear which files were copied and removed," he wrote. Berulis said the evidence indicated there was "a data breach facilitated by an internal actor," and that he observed "the exact behaviors (Indicators of Compromise) of one who was trying to erase records of activities, retard detection, and covertly hide what data was being extracted after the fact." The NLRB hosts lots of private information that is supposed to remain confidential, he noted. This includes "sensitive information on unions, ongoing legal cases, and corporate secrets." The database involved in the apparent breach contains "PII [personally identifiable information] of claimants and respondents with pending matters before the agency" and confidential business information "gathered or provided during investigations and litigation that were not intended for public release," he wrote. Berulis has almost two decades of experience, and his "work often includes high-level coordination with executive teams, establishing red-blue war game security events, and building cross-functional teams to align IT capabilities with mission-critical goals," he said in his declaration. "Having worked at sensitive US Government institutions, I have held a Top Secret security clearance with eligibility for access to Sensitive Compartmented Information, commonly known as TS/SCI." “Stay out of DOGE’s way” In late February, Berulis and his team were notified of DOGE's impending arrival. "On or around March 3, 2025, we saw a black SUV and police escort enter the garage, after which building security let the DOGE staffers in. They interacted with only a small group of NLRB staff, never introducing themselves to those of us in Information Technology," he wrote. An assistant chief information officer (ACIO) was given instructions that IT employees "were not to adhere to SOP [standard operating procedure] with the DOGE account creation in regards to creating records," Berulis wrote. "He specifically was told that there were to be no logs or records made of the accounts created for DOGE employees." DOGE officials were to be given "the highest level of access and unrestricted access to internal systems," specifically "tenant owner" accounts in Microsoft Azure that come "with essentially unrestricted permission to read, copy, and alter data," Berulis wrote. These "permissions are above even my CIO's access level to our systems" and "well above what level of access is required to pull metrics, efficiency reports, and any other details that would be needed to assess utilization or usage of systems in our agency." The NLRB systems "have built-in roles that auditors can use and have used extensively in the past," which do not have "the ability to make changes or access subsystems without approval," Berulis wrote. DOGE apparently wasn't willing to use these accounts. "The suggestion that they use these accounts instead was not open to discussion," he wrote. Berulis said IT staff were ordered "to hand over any requested accounts, stay out of DOGE's way entirely, and assist them when they asked. We were further directed not to resist them in any way or deny them any access." More suspicious events Berulis described several more suspicious events that followed DOGE's arrival. There was a new container that he described as "basically an opaque, virtual node that has the ability to build and run programs or scripts without revealing its activities to the rest of the network." There was also a token that "was configured to expire quickly after creation and use, making it harder to gain insight into what it was used for during its lifetime." To Berulis, these were signs of an attack on the NLRB systems. The methods used seemed to reflect "the desire of the attackers to work invisibly, leaving little to no obvious trace of their activities once removed." On March 6, various users "reported login issues to the service desk and, upon inspection, I found some conditional access policies were updated recently," he wrote. This was odd because "policies that had been in place for over a year were suddenly found to have been changed with no corresponding documentation or approvals," he wrote. "Upon my discovery of these changes, I asked the security personnel and information assurance team about it, but they had no knowledge of any planned changes or approvals." On March 7, Berulis says he "started tracking what appeared to be sensitive data leaving the secured location." About 10GB of data was exfiltrated, but it was "unclear which files were copied and removed," he wrote. On that same day, Berulis says he reported his concerns about sensitive data being exfiltrated to CIO Prem Aburvasmy. Aburvasmy took the concerns seriously and put together a leadership group "to discuss insider threat response on an ongoing cadence and how we could get better at detecting it," Berulis wrote. "Going forward after this, the team met every Friday and continue to do so to this day." Berulis described some shortcomings in the NLRB's ability to detect attacks. "During one of these meetings, it was confirmed that our team did not have the technical capability to detect or respond in real time to internal threat actors, and that we likely did not have the ability to obtain more details about the past events," he wrote. The department subsequently "shifted budget to allow for better tooling going forward," which "has vastly improved our detection and logging so we can provide more concrete evidence if covert exfiltration occurs by an insider threat again," Berulis wrote. "We also shut down a public endpoint and corrected rogue policies that had been altered to allow much broader traffic in/out of our network." Berulis: “We were directed not to... create an official report” On March 10, Berulis found that controls in Microsoft Purview to prevent insecure or unauthorized access from mobile devices had been disabled, he wrote. "In addition, outside of expected baselines and with no corresponding approvals or records I could find I noted the following: an interface exposed to the public Internet, a few internal alerting and monitoring systems in the off state, and multi-factor authentication changed," he wrote. The team observed more odd activity in the ensuing weeks, Berulis wrote. Data was sent to "an unknown external endpoint," but the network team was unable to obtain connection logs or determine what data was removed, he wrote. There were also "spikes in billing in Mission Systems related to storage input/output" associated with projects that could no longer be found in the NLRB system, indicating that "resources may have been deleted or short-lived," he wrote. During the week of March 24, an assistant CIO for security at the NLRB "concluded that following a review of data, we should report it" to US-CERT, the US Computer Emergency Readiness Team at the Cybersecurity and Infrastructure Security Agency (CISA), according to Berulis. "Accordingly, we launched a formal review and I provided all evidence of what we deemed to be a serious, ongoing security breach or potentially illegal removal of personally identifiable information," he wrote. But on April 3 or 4, the assistant CIO "and I were informed that instructions had come down to drop the US-CERT reporting and investigation and we were directed not to move forward or create an official report," Berulis wrote. Jon Brodkin Senior IT Reporter Jon Brodkin Senior IT Reporter Jon is a Senior IT Reporter for Ars Technica. He covers the telecom industry, Federal Communications Commission rulemakings, broadband consumer affairs, court cases, and government regulation of the tech industry. 50 Comments0 Reacties 0 aandelen 45 Views -
 WWW.TECHNOLOGYREVIEW.COMThese four charts sum up the state of AI and energyWhile it’s rare to look at the news without finding some headline related to AI and energy, a lot of us are stuck waving our hands when it comes to what it all means. Sure, you’ve probably read that AI will drive an increase in electricity demand. But how that fits into the context of the current and future grid can feel less clear from the headlines. That’s true even for people working in the field. A new report from the International Energy Agency digs into the details of energy and AI, and I think it’s worth looking at some of the data to help clear things up. Here are four charts from the report that sum up the crucial points about AI and energy demand. 1. AI is power hungry, and the world will need to ramp up electricity supply to meet demand. This point is the most obvious, but it bears repeating: AI is exploding, and it’s going to lead to higher energy demand from data centers. “AI has gone from an academic pursuit to an industry with trillions of dollars at stake,” as the IEA report’s executive summary puts it. Data centers used less than 300 terawatt-hours of electricity in 2020. That could increase to nearly 1,000 terawatt-hours in the next five years, which is more than Japan’s total electricity consumption today. Today, the US has about 45% of the world’s data center capacity, followed by China. Those two countries will continue to represent the overwhelming majority of capacity through 2035. 2. The electricity needed to power data centers will largely come from fossil fuels like coal and natural gas in the near term, but nuclear and renewables could play a key role, especially after 2030. The IEA report is relatively optimistic on the potential for renewables to power data centers, projecting that nearly half of global growth by 2035 will be met with renewables like wind and solar. (In Europe, the IEA projects, renewables will meet 85% of new demand.) In the near term, though, natural gas and coal will also expand. An additional 175 terawatt-hours from gas will help meet demand in the next decade, largely in the US, according to the IEA’s projections. Another report, published this week by the energy consultancy BloombergNEF, suggests that fossil fuels will play an even larger role than the IEA projects, accounting for two-thirds of additional electricity generation between now and 2035. Nuclear energy, a favorite of big tech companies looking to power operations without generating massive emissions, could start to make a dent after 2030, according to the IEA data. 3. Data centers are just a small piece of expected electricity demand growth this decade. We should be talking more about appliances, industry, and EVs when we talk about energy! Electricity demand is on the rise from a whole host of sources: Electric vehicles, air-conditioning, and appliances will each drive more electricity demand than data centers between now and the end of the decade. In total, data centers make up a little over 8% of electricity demand expected between now and 2030. There are interesting regional effects here, though. Growing economies will see more demand from the likes of air-conditioning than from data centers. On the other hand, the US has seen relatively flat electricity demand from consumers and industry for years, so newly rising demand from high-performance computing will make up a larger chunk. 4. Data centers tend to be clustered together and close to population centers, making them a unique challenge for the power grid. The grid is no stranger to facilities that use huge amounts of energy: Cement plants, aluminum smelters, and coal mines all pull a lot of power in one place. However, data centers are a unique sort of beast. First, they tend to be closely clustered together. Globally, data centers make up about 1.5% of total electricity demand. However, in Ireland, that number is 20%, and in Virginia, it’s 25%. That trend looks likely to continue, too: Half of data centers under development in the US are in preexisting clusters. Data centers also tend to be closer to urban areas than other energy-intensive facilities like factories and mines. Since data centers are close both to each other and to communities, they could have significant impacts on the regions where they’re situated, whether by bringing on more fossil fuels close to urban centers or by adding strain to the local grid. Or both. Overall, AI and data centers more broadly are going to be a major driving force for electricity demand. It’s not the whole story, but it’s a unique part of our energy picture to continue watching moving forward. This article is from The Spark, MIT Technology Review’s weekly climate newsletter. To receive it in your inbox every Wednesday, sign up here.0 Reacties 0 aandelen 36 Views
WWW.TECHNOLOGYREVIEW.COMThese four charts sum up the state of AI and energyWhile it’s rare to look at the news without finding some headline related to AI and energy, a lot of us are stuck waving our hands when it comes to what it all means. Sure, you’ve probably read that AI will drive an increase in electricity demand. But how that fits into the context of the current and future grid can feel less clear from the headlines. That’s true even for people working in the field. A new report from the International Energy Agency digs into the details of energy and AI, and I think it’s worth looking at some of the data to help clear things up. Here are four charts from the report that sum up the crucial points about AI and energy demand. 1. AI is power hungry, and the world will need to ramp up electricity supply to meet demand. This point is the most obvious, but it bears repeating: AI is exploding, and it’s going to lead to higher energy demand from data centers. “AI has gone from an academic pursuit to an industry with trillions of dollars at stake,” as the IEA report’s executive summary puts it. Data centers used less than 300 terawatt-hours of electricity in 2020. That could increase to nearly 1,000 terawatt-hours in the next five years, which is more than Japan’s total electricity consumption today. Today, the US has about 45% of the world’s data center capacity, followed by China. Those two countries will continue to represent the overwhelming majority of capacity through 2035. 2. The electricity needed to power data centers will largely come from fossil fuels like coal and natural gas in the near term, but nuclear and renewables could play a key role, especially after 2030. The IEA report is relatively optimistic on the potential for renewables to power data centers, projecting that nearly half of global growth by 2035 will be met with renewables like wind and solar. (In Europe, the IEA projects, renewables will meet 85% of new demand.) In the near term, though, natural gas and coal will also expand. An additional 175 terawatt-hours from gas will help meet demand in the next decade, largely in the US, according to the IEA’s projections. Another report, published this week by the energy consultancy BloombergNEF, suggests that fossil fuels will play an even larger role than the IEA projects, accounting for two-thirds of additional electricity generation between now and 2035. Nuclear energy, a favorite of big tech companies looking to power operations without generating massive emissions, could start to make a dent after 2030, according to the IEA data. 3. Data centers are just a small piece of expected electricity demand growth this decade. We should be talking more about appliances, industry, and EVs when we talk about energy! Electricity demand is on the rise from a whole host of sources: Electric vehicles, air-conditioning, and appliances will each drive more electricity demand than data centers between now and the end of the decade. In total, data centers make up a little over 8% of electricity demand expected between now and 2030. There are interesting regional effects here, though. Growing economies will see more demand from the likes of air-conditioning than from data centers. On the other hand, the US has seen relatively flat electricity demand from consumers and industry for years, so newly rising demand from high-performance computing will make up a larger chunk. 4. Data centers tend to be clustered together and close to population centers, making them a unique challenge for the power grid. The grid is no stranger to facilities that use huge amounts of energy: Cement plants, aluminum smelters, and coal mines all pull a lot of power in one place. However, data centers are a unique sort of beast. First, they tend to be closely clustered together. Globally, data centers make up about 1.5% of total electricity demand. However, in Ireland, that number is 20%, and in Virginia, it’s 25%. That trend looks likely to continue, too: Half of data centers under development in the US are in preexisting clusters. Data centers also tend to be closer to urban areas than other energy-intensive facilities like factories and mines. Since data centers are close both to each other and to communities, they could have significant impacts on the regions where they’re situated, whether by bringing on more fossil fuels close to urban centers or by adding strain to the local grid. Or both. Overall, AI and data centers more broadly are going to be a major driving force for electricity demand. It’s not the whole story, but it’s a unique part of our energy picture to continue watching moving forward. This article is from The Spark, MIT Technology Review’s weekly climate newsletter. To receive it in your inbox every Wednesday, sign up here.0 Reacties 0 aandelen 36 Views -
WWW.BUSINESSINSIDER.COMI walked every block of Manhattan. It was the best way to get to know my new city.Krissy Oechslin walked every block of Manhattan in 13 months. Krissy Oechslin 2025-04-17T10:30:02Z Save Saved Read in app This story is available exclusively to Business Insider subscribers. Become an Insider and start reading now. Have an account? Krissy Oechslin, 48, moved to New York City from Charlotte, North Carolina, in February 2024. She always wanted to walk every block of a city, but Charlotte wasn't pedestrian-friendly enough. It took her 13 months to walk every block in Manhattan. It helped her adjust to her new home. This as-told-to story is based on a conversation with Krissy Oechslin. The following has been edited for length and clarity.For years, I wanted to walk every block of a city.In 2012, I read a New York Times story about Matt Green, who was on a mission to walk every block of all five boroughs of NYC. I thought it was incredible and wanted to replicate a similar walking project one day.During the pandemic lockdowns, I toyed with the idea of doing it in Charlotte, North Carolina, where I lived at the time. It wouldn't really be possible — Charlotte is very car-centric, and there are parts of the city that just aren't pedestrian-friendly. I knew I would get odd looks if I was strolling next to a highway. Not all of Charlotte, North Carolina is pedestrian-friendly. joe daniel price/Getty Images When I decided to move to New York in February 2024, I thought exploring every block of Manhattan would be a cool way to get to know my new city.It took me 13 months of on-and-off effort to walk every block. When I was finished, I felt like I saw so many unique parts of Manhattan — ones even lifelong New Yorkers might not know about.I tracked my progress with a 6-foot map I hung up a six-foot-long map to help track my progress. Krissy Oechslin Originally, I planned to both bike and walk the city, so I couldn't use CityStrides, a map that only tracks running and walking. (In the end, I walked over 99.5% of the project.)Because I wanted to tackle the blocks out of order, tracking them was a multi-step process. First, I needed a map of Manhattan.Finding a complete one was trickier than I expected. The first one I bought on Amazon stopped after 110th Street and many I found capped the island at Central Park. Manhattan stretches over 100 blocks further north, ending at Marble Hill right before West 230th Street. Sylvan Terrace, on St. Nicholas Ave between 160th and 162nd Street, wouldn't show up on some of the Manhattan maps I saw. Krissy Oechslin The best one I could find was from 2011, a 6-foot-long version that I stuck to the wall in my apartment.By the time I was done with the project, I learned that one was not fully up to date, either — I encountered areas in real life that were blank on the map, like Waterline Square on the Upper West Side, which was completed in 2020. Some of my favorite buildings, like the UN Headquarters' Turkevi Center (left) and the Lantern House in Chelsea (right) were finished in 2021 and 2020, respectively. Krissy Oechslin I downloaded Strava to track exact steps every day, then traced my progress to the map with a Sharpie.My first entry began in Harlem, right after I returned my moving truck and walked 10 blocks to my new home. Afterward, I started trying to find unique routes when I made plans — how could I incorporate a new block on my way to meet my friends? Other times, I specifically walked to new areas on my list, like the FDR Drive highway service road on the easternmost side of the borough.The oldest streets were my favorites Historic rowhouses in Hamilton Heights; a building in Sugar Hill, built in the late 1800s. Krissy Oechslin I didn't want to miss any historic landmarks.When I started the project, I bought "The New York Nobody Knows" by William B. Helmreich, a sociologist who walked every block in NYC. It felt more like a sociology textbook than a walking guide, but it gave me some ideas of what I wanted to stop and look at on certain blocks, so I saved them in Google Maps. The original Statue of Liberty sculpture, used to cast the real one, located in Midtown; vintage ads in Harlem. Krissy Oechslin I also stopped a lot during my walks to search different buildings or historical figures on Wikipedia, with what felt like hundreds of tabs open on my phone.Walking up to 10 miles a day sometimes, I ended up saving a lot of buildings on Google Maps that I plan to revisit during Open House New York, a weekend when normally private buildings are accessible to the public.I'm a sucker for cobblestone streets, so some of my favorite neighborhoods were the West Village and Tribeca. I also loved the Financial District — some of the oldest streets in New York combined with towering skyscrapers made for such a cool contrast of old and new. The West Village was one of my favorite neighborhoods, especially around the holidays. Krissy Oechslin One of the most beautiful streetsIn the East Village, I encountered the two oldest cemeteries in New York: New York Marble Cemetery and New York City Marble Cemetery. The former, established in 1830, is partially obscured: I could only see it at the end of the block through an iron gate.I stumbled upon other hidden gems like a Mexican folk art store or a used record shop in the middle of an apartment block. I loved learning that they exist.I finished at an iconic New York spot I ended my project at Tom's Restaurant, which served as the exterior diner shot in "Seinfeld." Krissy Oechslin/NBC By March 2025, I bought a co-op apartment in a neighborhood I hadn't finished exploring: Morningside Heights, at the top of Manhattan.That month, I officially ended my project near my new home, in front of Tom's Restaurant, otherwise known as the "Seinfeld" diner.Four people completely ignored me when I asked them to take a photo of me in front of the restaurant. It made me feel like a real New Yorker.Moving to a new city, I didn't have many friends yet. Having this project gave me built-in plans every weekend — if I had nothing else going on, I could always go for a walk.When I tell people I walked every block of Manhattan, I can tell how long someone's lived here based on their response. The ones who've been here the longest aren't too impressed: walking everywhere is just part of the experience. Recommended video0 Reacties 0 aandelen 29 Views