Musk claims of Ukraine DDoS attack derided by cyber community
www.computerweekly.com
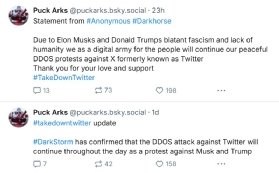
Tech oligarch Elon Musk has drawn criticism from cyber security experts following unsubstantiated claims that Ukraine was behind an apparent distributed denial of service (DDoS) attack on his social media platform, X, formerly known as Twitter.Musk, who currently heads the US governments Department of Government Efficiency (Doge) that has fired thousands of federal workers, accused the Ukrainian government of being behind the incident that brought down X services for many users on Monday 10 March. Speaking to the Fox Business news channel, he claimed a massive cyber attack targeting X appeared to have originated from IP addresses located in Ukraine.The incident came amid a serious deterioration in relations between Ukraine and the US, and just days after US Cyber Command, the countrys military offensive and defensive cyber unit, suspended offensive operations against Russia in a significant climbdown.Ukrainian officials were quick to refute the suggestion Kyiv was behind the cyber attack, and in conversation with the BBC, former National Cyber Security Centre head Ciaran Martin described Musks accusations as unconvincing and pretty much garbage.Martin told the BBC he would be hard-pressed to think of an organisation of Xs scale that has been so badly impacted by such an incident in recent years and suggested the incident did not paint a good picture of the platforms wider cyber resilience.In a DDoS attack, malicious actors bombard a server with junk web traffic to overwhelm it, forcing it offline and leaving legitimate users unable to access it.Such crude forms of cyber attack are well-known and relatively common they frequently form a key element in hacktivist actions thanks to their accessibility, which at first glance lends a certain element of credibility to Musks claims.However, DDoS attacks are launched via geographically disperse networks of computers and other devices that have been co-opted into botnets without their owners knowledge or consent. This makes it very hard to accurately locate the individuals responsible for them.Tom Parker, cyber security author and chief technology officer (CTO) at NetSPI, said the magnitude of the attack did strongly suggest the involvement of a sophisticated threat actor but it was important to understand that accurately attributing DDoS incidents is notoriously difficult.Such adversaries are highly adept at concealing their tracks. We must be extremely cautious about pointing fingers and sabre rattling without clear and compelling evidence to demonstrate capability, motive,and likely benefit for the party involved, Parker told Computer Weekly.Despite recent events, I do believe Ukraine is still seeking to foster a more positive relationship with the US, which would make it unlikely that the claims of Ukrainian involvement are well-grounded. Rather, the scenario appears to align more with a false flag operation deliberately crafted to implicate Ukraine.As we often see in these complex situations, the most straightforward explanation isnt always correct, and drawing conclusions prematurely can lead us astray, he said.Lending more weight to arguments against Musk, a pro-Palestinian hacktivist group known as Dark Storm Team subsequently claimed via Telegram that it had been behind the incident.An account on the Bluesky social media platform claiming to be associated with this group and appearing to have links to the Anonymous collective, described the DDoS attack as a peaceful protest and said attacks would continue.Jake Moore, global cyber security advisor at ESET, said: Cyber criminals attack from all angles and are incredibly fearless in their attempts. Whether they are directed by geopolitical groups or financially motivated gangs, DDoS attacks are a clever way of targeting a website without having to hack into the mainframe, and therefore the perpetrators can remain largely anonymous and difficult to point a finger at.This also makes it that much more difficult to protect from when the landscape is completely unknown apart from having generic DDoS protection. However, even with such protection, each year, threat actors become better equipped and use even more IP addresses such as home IoT devices to flood systems, making it increasingly more difficult to protect from.Added Moore: Unfortunately, X remains one of the most talked about platforms, making it a typical target for hackers marking their own territory. All that can be done to future-proof their networks is to continue to expect the unexpected and build even more robust DDoS protection layers.Read more about DDoS attacksDDoS attacks are on the rise again. While they usually strike without warning, there are some red flags to be aware of. Rapid detection is key to surviving such an attack.A DDoS attack can wreak havoc on an organisation, but a number of strategies can help stop such attacks and minimise their damage.Learn how to recover from a DDoS attack and get operations back online quickly, while minimising impact on customers and brand reputation.
0 Comentários
·0 Compartilhamentos
·60 Visualizações


