New threat uses fake CAPTCHA to infect systems with malware
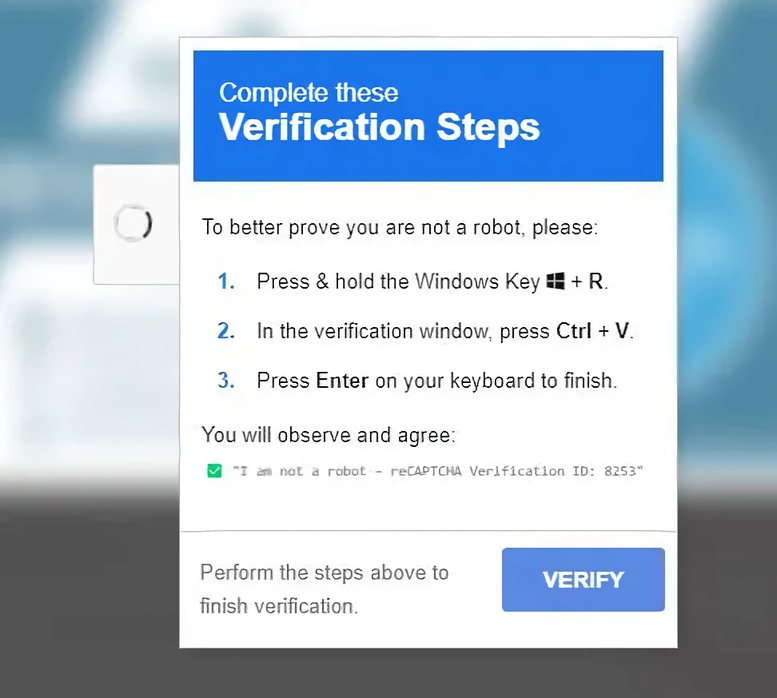
In a nutshell: A new cyber threat tactic has emerged, leveraging social engineering to trick users into infecting their own systems with malware. Recently highlighted by Malwarebytes, this method disguises malicious tools as CAPTCHA requests. In reality, these files often media or HTML-based are designed to steal personal information or function as remote access trojans. The attack typically begins when visitors to a website are prompted to verify they are not robots, a common practice that rarely raises suspicion. However, instead of a standard CAPTCHA challenge, users encounter a series of seemingly harmless steps that are actually part of a sophisticated scam.The instructions might read: "To better prove you are not a robot, please press and hold the Windows Key + R, paste the verification code by pressing Ctrl + V, and then press Enter to complete verification." These steps are designed to execute a malicious command.Behind the scenes, the website uses JavaScript to copy a command to the user's clipboard. This is possible because, in Chromium-based browsers, websites can write to the clipboard with the user's permission. However, Windows assumes this permission was granted when the user checked the "I am not a robot" checkbox, creating an opportunity for exploitation.The command pasted into the Run dialog box appears to be a simple verification message but is actually a trigger for the mshta command, which downloads a malicious file from a remote server. This file is often disguised as a media file, such as an MP3 or MP4, but contains an encoded PowerShell command that silently retrieves and executes the actual malware payload.The malware payloads used in these attacks include Lumma Stealer and SecTopRAT, both designed to extract sensitive data from infected systems. The attack is particularly effective because it exploits user trust in CAPTCHA verification processes, posing a risk even to those who are generally cautious online.To mitigate these threats, MalwareBytes advises users to be wary of instructions from unfamiliar websites. Using an active anti-malware solution that blocks malicious websites and scripts is essential. Additionally, browser extensions that block known scam domains can provide an extra layer of defense.While disabling JavaScript can prevent clipboard hijacking, it may also disrupt functionality on many websites. A more practical approach, as recommended by MalwareBytes, is to use different browsers for different purposes reserving one specifically for visiting less trusted sites. // Related Stories