Novel Russian hacking method daisy chains Wi-Fi networks to reach intended target
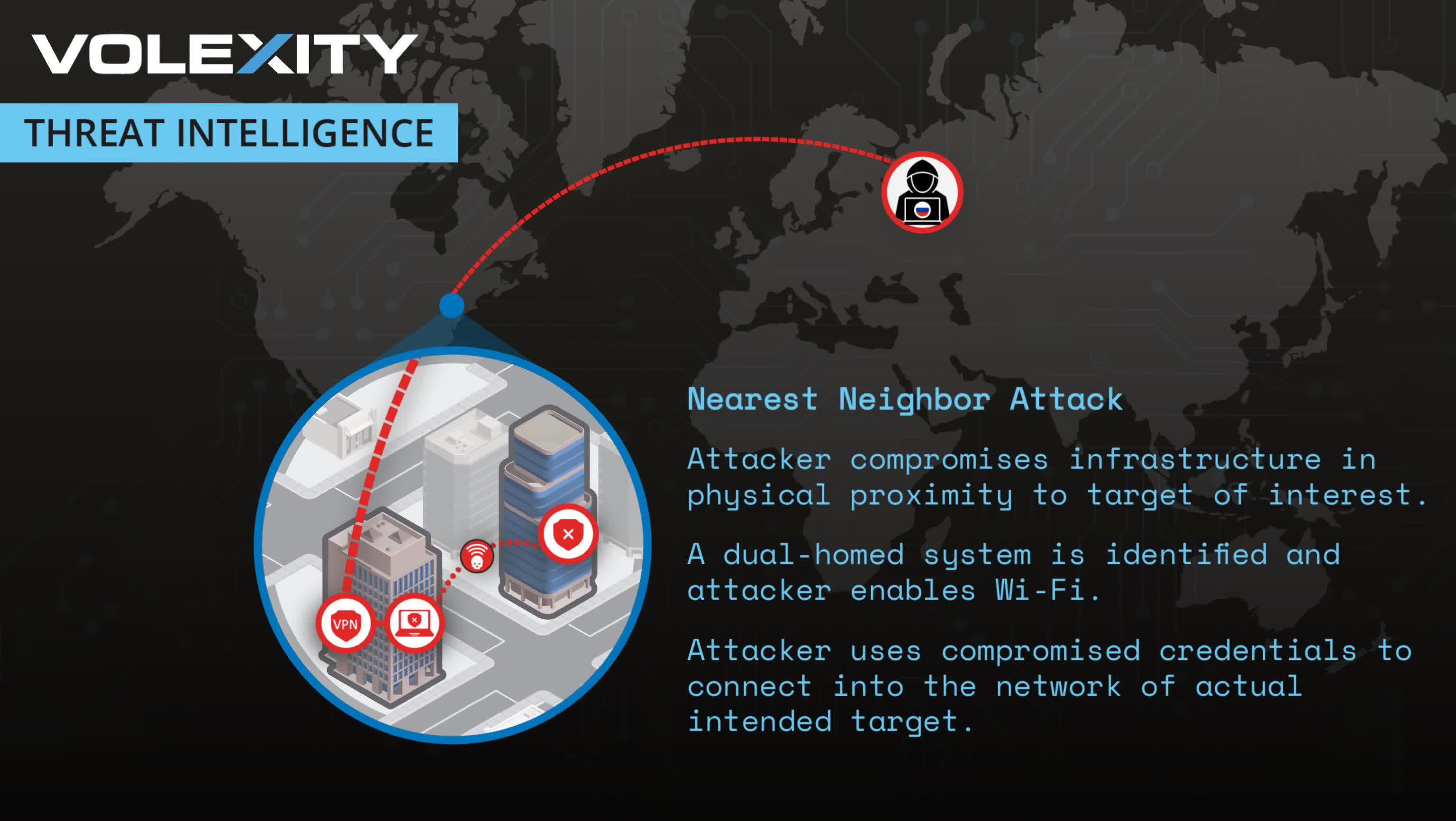
In context: A new hacking technique raises concerns about how cyber warfare and espionage continue to evolve. As nation-state actors develop more sophisticated methods, the line between physical and digital security becomes increasingly blurred. Russian hackers have devised a highly sophisticated method of breaching Wi-Fi networks from afar that researchers have dubbed the "nearest neighbor attack," as it allows hackers to infiltrate target networks without physically approaching the premises.The new technique involves a multi-step process that leverages vulnerabilities in neighboring networks to breach the intended target. Instead of risking detection by getting close to the target, as has been the norm in previous Wi-Fi hacking attempts, hackers can now orchestrate their attacks from a safe distance.Cybersecurity firm Volexity uncovered this unprecedented Wi-Fi hacking technique while investigating a network breach targeting a customer in Washington, DC, in 2022. The firm's researchers traced the intrusion to a Russian hacker group known by various monikers, including Fancy Bear, APT28, and Unit 26165, part of Russia's GRU military intelligence agency.Wired notes that cybersecurity researcher Steven Adair revealed how his firm discovered this technique at the Cyberwarcon security conference held this week in Arlington, Virginia.A "nearest neighbor attack" operates through a series of calculated steps. Hackers first breach a vulnerable network in a building near the intended target. They then gain control of a laptop within this compromised network. They use the device's Wi-Fi from there to breach the targeted network. This method allows the attackers to remain physically distant while exploiting local Wi-Fi vulnerabilities. // Related StoriesIn the case investigated by Volexity, the attack's sophistication extended beyond a single jump. The researchers discovered evidence of a daisy chain of Wi-Fi network breaches that involved up to three separate networks before reaching the final target. The attack's success hinged on several technical elements, including credential exploitation, two-factor authentication bypass, and domain name leakage. The hackers were very determined, according to Volexity, making multiple intrusion attempts even after initial discovery.This technique is an evolution of the GRU's previous "close-access" hacking methods. In 2018, officials caught Russian spies attempting to hack the Wi-Fi network of the Organization for the Prohibition of Chemical Weapons in The Hague using equipment hidden in a car trunk. The "nearest neighbor attack" seems to directly respond to the operational security risks exposed by that incident.This new attack vector presents significant challenges for cybersecurity professionals. Organizations must now consider the security of neighboring networks as part of their threat landscape. The ability to conduct these attacks from afar increases the potential pool of attackers and complicates identifying who is behind an attack.In light of this new threat, cybersecurity experts recommend several protective measures, including limiting Wi-Fi range, obfuscating network names, implementing more robust authentication protocols, and monitoring Wi-Fi access points, especially those near windows or external walls.Cybersecurity experts warn that nearest-neighbor attacks may become more prevalent. John Hultquist, a threat intelligence expert at Google-owned Mandiant, suggests that this technique represents a "major improvement" for close-access operations, and hackers are likely to use it more frequently.Image credit: Volexity