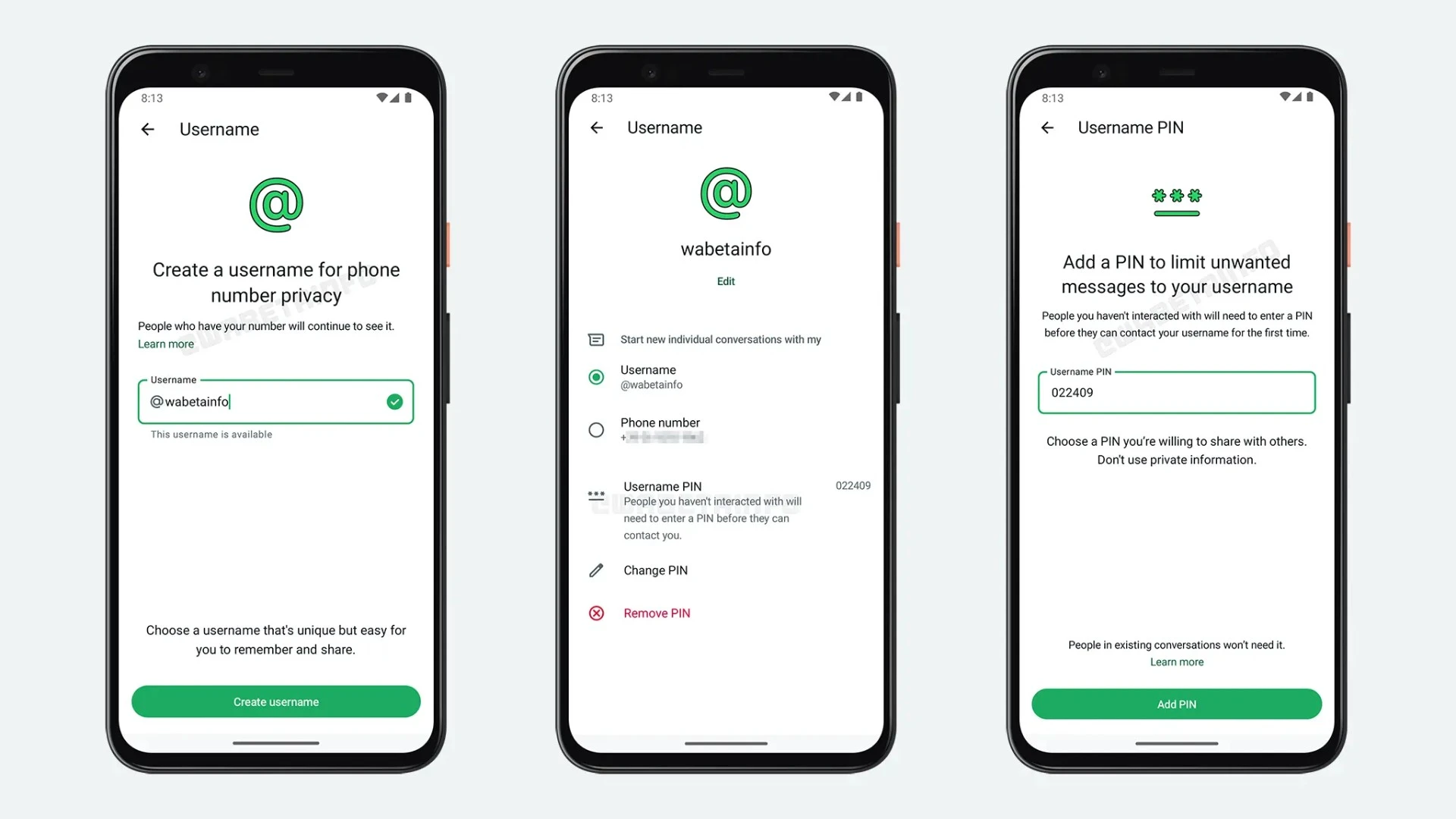
Exciting news, everyone! Platform X has just launched a user name marketplace where Premium+ subscribers can snag those dreamy inactive usernames! Imagine finally getting that perfect name that resonates with your unique identity!
Whether you're aiming for a "premium" name or something "rare" (let's face it, we all love a good treasure hunt ), this new feature opens the door to endless possibilities! I mean, who wouldn't want a username that makes them sound like an online superstar?
Remember, just like usernames, our potential is limitless! So go out there and grab what’s yours!
Check it out here: https://www.tech-wd.com/wd/2025/11/22/%d9%85%d9%86%d8%b5%d8%a9-x-%d8%aa%d9%81%d8%aa%d8%ad-%d8%b3%d9%88%d9%82%d9%8b%d8%a7-%d9%84%d8%a3%d8%b3%d9%85%d8%a7%d8%a1-%d8%a
Whether you're aiming for a "premium" name or something "rare" (let's face it, we all love a good treasure hunt ), this new feature opens the door to endless possibilities! I mean, who wouldn't want a username that makes them sound like an online superstar?
Remember, just like usernames, our potential is limitless! So go out there and grab what’s yours!
Check it out here: https://www.tech-wd.com/wd/2025/11/22/%d9%85%d9%86%d8%b5%d8%a9-x-%d8%aa%d9%81%d8%aa%d8%ad-%d8%b3%d9%88%d9%82%d9%8b%d8%a7-%d9%84%d8%a3%d8%b3%d9%85%d8%a7%d8%a1-%d8%a
🌟 Exciting news, everyone! 🎉 Platform X has just launched a user name marketplace where Premium+ subscribers can snag those dreamy inactive usernames! ✨ Imagine finally getting that perfect name that resonates with your unique identity! 💖
Whether you're aiming for a "premium" name or something "rare" (let's face it, we all love a good treasure hunt 🕵️♂️), this new feature opens the door to endless possibilities! I mean, who wouldn't want a username that makes them sound like an online superstar? 🌈
Remember, just like usernames, our potential is limitless! So go out there and grab what’s yours! 🚀
Check it out here: https://www.tech-wd.com/wd/2025/11/22/%d9%85%d9%86%d8%b5%d8%a9-x-%d8%aa%d9%81%d8%aa%d8%ad-%d8%b3%d9%88%d9%82%d9%8b%d8%a7-%d9%84%d8%a3%d8%b3%d9%85%d8%a7%d8%a1-%d8%a
0 التعليقات
·0 المشاركات