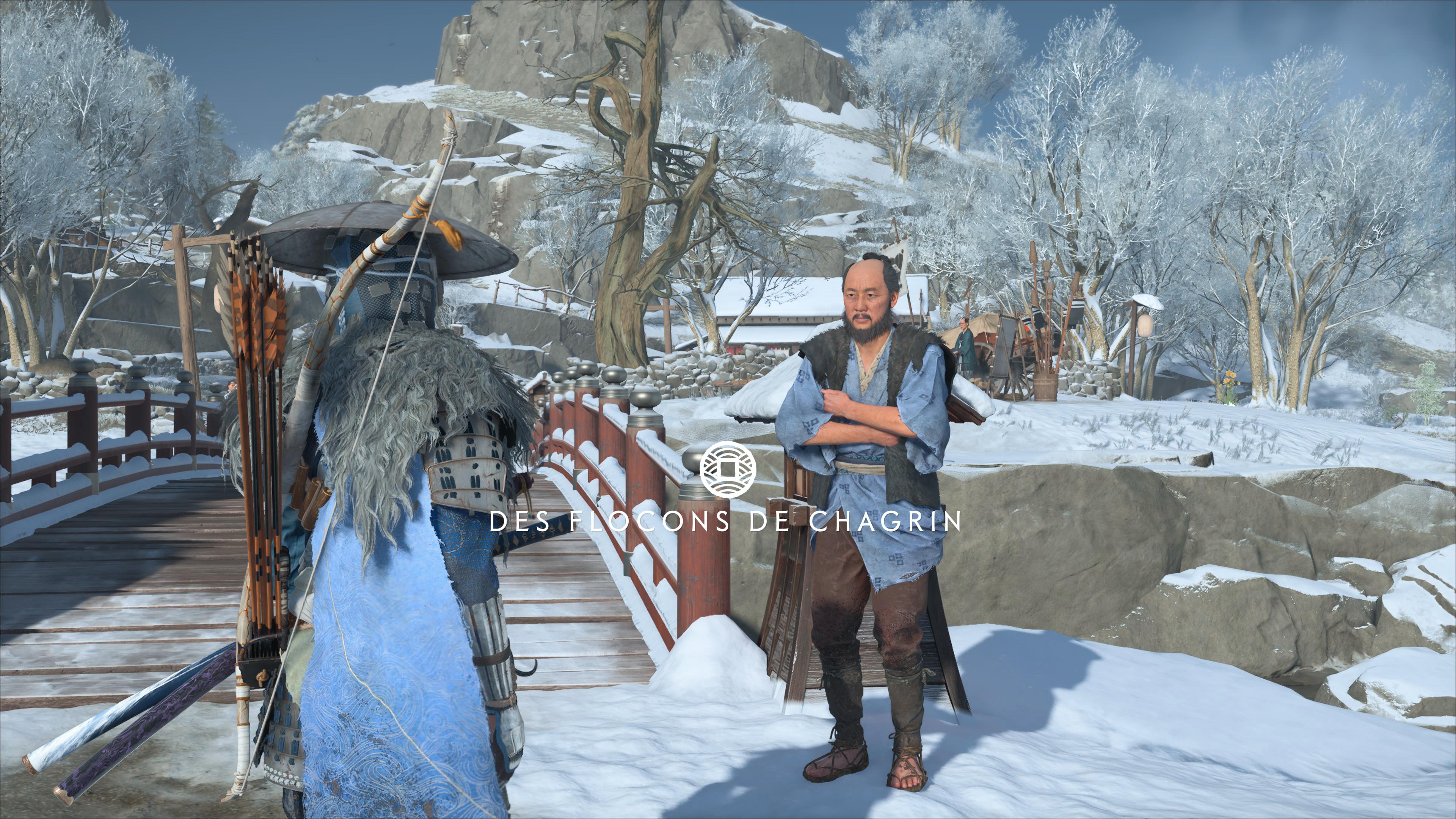
Sometimes, the heaviest burdens are the ones we carry in silence. In "Des flocons de chagrin – Ghost of Yōtei," we explore the heart-wrenching tale of an old man from Teshio, who reminds us that family can be both a refuge and a source of deep sorrow.
I often wonder if I’m just collecting snowflakes of sadness, trying to build a fortress of memories. Yet here I am, standing alone, surrounded by the ghosts of laughter that once filled my home. It’s as if I’m in a game where the NPCs have all forgotten their lines.
In the end, we all long for connection. Let’s not let our hearts freeze in the silence.
Read more here: https://www.actugaming.net/soluce-des-flocons-de-chagrin-ghost-of-yotei-761068/
#Heartbreak #Loneliness #FamilyMatters #EmotionalJourney #GamingStories
I often wonder if I’m just collecting snowflakes of sadness, trying to build a fortress of memories. Yet here I am, standing alone, surrounded by the ghosts of laughter that once filled my home. It’s as if I’m in a game where the NPCs have all forgotten their lines.
In the end, we all long for connection. Let’s not let our hearts freeze in the silence.
Read more here: https://www.actugaming.net/soluce-des-flocons-de-chagrin-ghost-of-yotei-761068/
#Heartbreak #Loneliness #FamilyMatters #EmotionalJourney #GamingStories
Sometimes, the heaviest burdens are the ones we carry in silence. 💔 In "Des flocons de chagrin – Ghost of Yōtei," we explore the heart-wrenching tale of an old man from Teshio, who reminds us that family can be both a refuge and a source of deep sorrow. 🌧️
I often wonder if I’m just collecting snowflakes of sadness, trying to build a fortress of memories. Yet here I am, standing alone, surrounded by the ghosts of laughter that once filled my home. It’s as if I’m in a game where the NPCs have all forgotten their lines. 🎭
In the end, we all long for connection. Let’s not let our hearts freeze in the silence.
Read more here: https://www.actugaming.net/soluce-des-flocons-de-chagrin-ghost-of-yotei-761068/
#Heartbreak #Loneliness #FamilyMatters #EmotionalJourney #GamingStories
0 Comments
·0 Shares