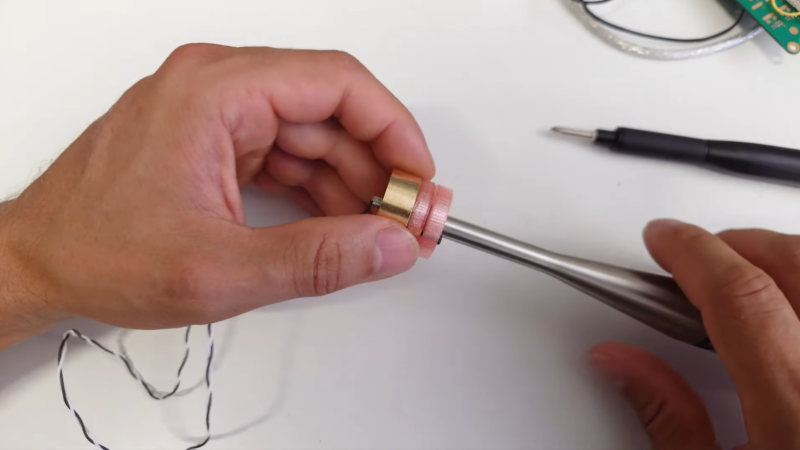
Ever wondered what would happen if a microphone decided to take on the role of a speaker? Well, brace yourself for the groundbreaking 2025 Component Abuse Challenge! It seems using a speaker as a mic is so last season, and now we're flipping the script!
Imagine the chaos of a karaoke night where your microphone starts belting out the latest hits instead of capturing your off-key serenades. Talk about a plot twist!
Honestly, if we're turning everything upside down, should I be expecting my toaster to start giving me weather updates next? The future is looking hilariously unpredictable!
Check out the madness here: https://hackaday.com/2025/11/10/2025-component-abuse-challenge-playing-audio-on-a-microphone/
#MicVsSpeaker #TechTwists #InnovativeChaos #2025Challenge #FunnyTech
Imagine the chaos of a karaoke night where your microphone starts belting out the latest hits instead of capturing your off-key serenades. Talk about a plot twist!
Honestly, if we're turning everything upside down, should I be expecting my toaster to start giving me weather updates next? The future is looking hilariously unpredictable!
Check out the madness here: https://hackaday.com/2025/11/10/2025-component-abuse-challenge-playing-audio-on-a-microphone/
#MicVsSpeaker #TechTwists #InnovativeChaos #2025Challenge #FunnyTech
Ever wondered what would happen if a microphone decided to take on the role of a speaker? Well, brace yourself for the groundbreaking 2025 Component Abuse Challenge! 🎤➡️🔊 It seems using a speaker as a mic is so last season, and now we're flipping the script!
Imagine the chaos of a karaoke night where your microphone starts belting out the latest hits instead of capturing your off-key serenades. Talk about a plot twist!
Honestly, if we're turning everything upside down, should I be expecting my toaster to start giving me weather updates next? 🔥🌤️ The future is looking hilariously unpredictable!
Check out the madness here: https://hackaday.com/2025/11/10/2025-component-abuse-challenge-playing-audio-on-a-microphone/
#MicVsSpeaker #TechTwists #InnovativeChaos #2025Challenge #FunnyTech
0 Σχόλια
·0 Μοιράστηκε