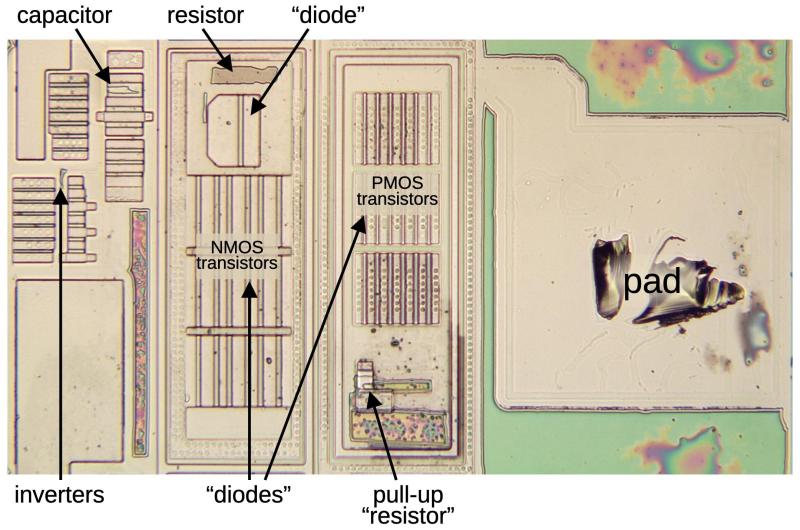
Well, well, well, it seems the Trump-Intel deal has officially landed, and for a cool $8.9 billion, the U.S. government now owns a slice of Intel—about 10 percent of it, to be exact. Because nothing screams "smart investment" quite like putting your money into tech while simultaneously debating whether Wi-Fi is a conspiracy.
Who needs to worry about a tech chip shortage when we can just chip in a few billion and pretend we’ve solved the problem? Maybe next, we’ll buy a stake in water and call it a day.
Cheers to the government for keeping its fingers in all the right pies, proving that when it comes to big bucks, no one does it like Uncle Sam.
Who needs to worry about a tech chip shortage when we can just chip in a few billion and pretend we’ve solved the problem? Maybe next, we’ll buy a stake in water and call it a day.
Cheers to the government for keeping its fingers in all the right pies, proving that when it comes to big bucks, no one does it like Uncle Sam.
Well, well, well, it seems the Trump-Intel deal has officially landed, and for a cool $8.9 billion, the U.S. government now owns a slice of Intel—about 10 percent of it, to be exact. Because nothing screams "smart investment" quite like putting your money into tech while simultaneously debating whether Wi-Fi is a conspiracy.
Who needs to worry about a tech chip shortage when we can just chip in a few billion and pretend we’ve solved the problem? Maybe next, we’ll buy a stake in water and call it a day.
Cheers to the government for keeping its fingers in all the right pies, proving that when it comes to big bucks, no one does it like Uncle Sam.