0 Comments
0 Shares
146 Views

Directory
Directory
-
Please log in to like, share and comment!
-
 WWW.THISISCOLOSSAL.COMEmpowering and Protective Bodies Merge in Laura Bergers Metaphysical PaintingsGhost Garden. All images courtesy of Laura Berger, shared with permissionEmpowering and Protective Bodies Merge in Laura Bergers Metaphysical PaintingsNovember 12, 2024ArtKate MothesIn complementary shades of blue and orange or pink and green, Laura Bergers oil paintings (previously) meld embracing figures with botanicals, landscapes, and celestial phenomena. Women lounge comfortably in a steam bath or walk across an expanse of dunes, often rendered lightly transparent as if floating over or absorbing their surroundings.Berger situates the figures interactions in the center of the composition, bending and arranging limbs, foliage, fabric, or strings of stars into intimate, metaphysical geometries.ResurfacingHer imagery adopts a subtle rhythm, sometimes even near-symmetry, in a nod to spirituality and transformation. Emanating empowerment and a sense of safety, the women wrap around one another in endearing, protective collectivity.Berger will have work in a booth presented by Mama Projects at Untitled Art Fair, which runs December 4 to 8 in Miami Beach, and will be part of the exhibition Ultraviolet Catastrophe at The Pits Palm Springs location, which is scheduled to open on December 17.Find more on the artists website, and follow updates on Instagram.Desert WalkingThe Steam BathNight ThoughtsBehind the GardenThe GarlandTracing Your OutlineTransienceNext article0 Comments 0 Shares 184 Views
WWW.THISISCOLOSSAL.COMEmpowering and Protective Bodies Merge in Laura Bergers Metaphysical PaintingsGhost Garden. All images courtesy of Laura Berger, shared with permissionEmpowering and Protective Bodies Merge in Laura Bergers Metaphysical PaintingsNovember 12, 2024ArtKate MothesIn complementary shades of blue and orange or pink and green, Laura Bergers oil paintings (previously) meld embracing figures with botanicals, landscapes, and celestial phenomena. Women lounge comfortably in a steam bath or walk across an expanse of dunes, often rendered lightly transparent as if floating over or absorbing their surroundings.Berger situates the figures interactions in the center of the composition, bending and arranging limbs, foliage, fabric, or strings of stars into intimate, metaphysical geometries.ResurfacingHer imagery adopts a subtle rhythm, sometimes even near-symmetry, in a nod to spirituality and transformation. Emanating empowerment and a sense of safety, the women wrap around one another in endearing, protective collectivity.Berger will have work in a booth presented by Mama Projects at Untitled Art Fair, which runs December 4 to 8 in Miami Beach, and will be part of the exhibition Ultraviolet Catastrophe at The Pits Palm Springs location, which is scheduled to open on December 17.Find more on the artists website, and follow updates on Instagram.Desert WalkingThe Steam BathNight ThoughtsBehind the GardenThe GarlandTracing Your OutlineTransienceNext article0 Comments 0 Shares 184 Views -
 WWW.THISISCOLOSSAL.COMEndless Fields of Detritus Blanket Cssio Vasconcelloss Aerial CompositesDetail of Air Force. All images courtesy of Cssio Vasconcellos and Nara Roesler Gallery, shared with permissionEndless Fields of Detritus Blanket Cssio Vasconcelloss Aerial CompositesNovember 12, 2024Kate MothesWhere do jets go when they no longer fly? What happens to shipping containers when they arent useful anymore for cargo? The answer is invisible to most of us, but for Cssio Vasconcellos, abandoned trains, planes, and automobiles are far from forgotten.For more than four decades, the So Paolo-based artist has been fascinated by the relationship between humans and the landscape. Over the years, his work has captured dramatic impressions of sprawling cities around the globe, often from the air, spurring an ongoing series called Collectives that condenses details of urban infrastructure like highways and parking lots into sprawling, all-over compositions.Collective 11: AirplanesCollectives 2, to which these images belong, focuses solely on the mesmerizingand mind-bogglingquantity of scrapped vehicles and metal indefinitely parked in nondescript places. Vasconcellos draws from tens of thousands of aerial photographs he has made of junkyards, scrap heaps, airplane graveyards, and dumps to create remarkable, large-scale composite images.The artist has mapped all of the junkyards around So Paolo, plus numerous more near the Brazilian cities of Cubato, Santos, and Rio de Janeiro. He has also documented desert landscapes in the U.S. that serve as final resting places for commercial airliners and military jets.Over, for example, considers numerous associated meanings, like overview, all-over, overdose, or game over. The title references not only excess but the overflow of visual information in contemporary society.Seeing an image like this is to make clear that there is no throw away,' Vasconcellos says in a video about OVER, which took him about a year and three months to complete. This volume of things that are in the work they are out there, he adds. I just put them together.Detail of OverThese photos may look like post-apocalyptic scenarios, but they could be our future, the artist says in a statement. We still have to learn that by throwing things away and taking them out of our sight, we dont make themdisappear. In fact, they keep existing somewhere else, outliving us mostof the time.Vasconcellos cuts out individual shipping containers, trucks, dumpsters, and piles of detritus in a meticulous and time-consuming digital process. He never repeats an element in a composition, and each piece is scaled and situated so that the shadows align with the directionality of the light. He then adds dust and dirt to the surfaces, simultaneously emphasizing the patina of time and an eerie sense of timelessness. Devoid of people, Vasconcelloss images nevertheless describe the human predilection to produce, consume, and cast aside. Its kind of nonsense, because there are some paths, but you dont really understand how a person or a car can get in thereor get out, Vasconcellos says. It is a possible world, but at the same time, an absurd one.Vasconcellos is represented by Nara Roesler Gallery, and you can explore more of his work on his website and Instagram.Collective 12: BoatsCollective 10: ContainersAir ForceCollective 7: Metal ScrapDetail of Collective 7: Metal ScrapCollective 9: Scrap DumpsterPrevious articleNext article0 Comments 0 Shares 183 Views
WWW.THISISCOLOSSAL.COMEndless Fields of Detritus Blanket Cssio Vasconcelloss Aerial CompositesDetail of Air Force. All images courtesy of Cssio Vasconcellos and Nara Roesler Gallery, shared with permissionEndless Fields of Detritus Blanket Cssio Vasconcelloss Aerial CompositesNovember 12, 2024Kate MothesWhere do jets go when they no longer fly? What happens to shipping containers when they arent useful anymore for cargo? The answer is invisible to most of us, but for Cssio Vasconcellos, abandoned trains, planes, and automobiles are far from forgotten.For more than four decades, the So Paolo-based artist has been fascinated by the relationship between humans and the landscape. Over the years, his work has captured dramatic impressions of sprawling cities around the globe, often from the air, spurring an ongoing series called Collectives that condenses details of urban infrastructure like highways and parking lots into sprawling, all-over compositions.Collective 11: AirplanesCollectives 2, to which these images belong, focuses solely on the mesmerizingand mind-bogglingquantity of scrapped vehicles and metal indefinitely parked in nondescript places. Vasconcellos draws from tens of thousands of aerial photographs he has made of junkyards, scrap heaps, airplane graveyards, and dumps to create remarkable, large-scale composite images.The artist has mapped all of the junkyards around So Paolo, plus numerous more near the Brazilian cities of Cubato, Santos, and Rio de Janeiro. He has also documented desert landscapes in the U.S. that serve as final resting places for commercial airliners and military jets.Over, for example, considers numerous associated meanings, like overview, all-over, overdose, or game over. The title references not only excess but the overflow of visual information in contemporary society.Seeing an image like this is to make clear that there is no throw away,' Vasconcellos says in a video about OVER, which took him about a year and three months to complete. This volume of things that are in the work they are out there, he adds. I just put them together.Detail of OverThese photos may look like post-apocalyptic scenarios, but they could be our future, the artist says in a statement. We still have to learn that by throwing things away and taking them out of our sight, we dont make themdisappear. In fact, they keep existing somewhere else, outliving us mostof the time.Vasconcellos cuts out individual shipping containers, trucks, dumpsters, and piles of detritus in a meticulous and time-consuming digital process. He never repeats an element in a composition, and each piece is scaled and situated so that the shadows align with the directionality of the light. He then adds dust and dirt to the surfaces, simultaneously emphasizing the patina of time and an eerie sense of timelessness. Devoid of people, Vasconcelloss images nevertheless describe the human predilection to produce, consume, and cast aside. Its kind of nonsense, because there are some paths, but you dont really understand how a person or a car can get in thereor get out, Vasconcellos says. It is a possible world, but at the same time, an absurd one.Vasconcellos is represented by Nara Roesler Gallery, and you can explore more of his work on his website and Instagram.Collective 12: BoatsCollective 10: ContainersAir ForceCollective 7: Metal ScrapDetail of Collective 7: Metal ScrapCollective 9: Scrap DumpsterPrevious articleNext article0 Comments 0 Shares 183 Views -
 WWW.FOXNEWS.COMAlarming rise of fake legal requests: What it means for your privacyPublished November 12, 2024 10:00am EST close Tips to protect yourself against bank scams Scammers often ask for answers to secret questions for crucial information needed to access accounts. Phishing emails are one of the most common tricks scammers use, but theyre usually easy to catch if you pay attention. Awkward grammar, random details and, most importantly, an unofficial email address are dead giveaways. For example, you might get an email saying your Apple IDs been disabled, but the senders email wont actually be from Apple. Now, though, scammers are finding ways to get around this.According to the FBI, theres been a recent rise in cybercriminal services using hacked police and government email accounts to send fake subpoenas and data requests to U.S.-based tech companies.IM GIVING AWAY A $500 GIFT CARD FOR THE HOLIDAYSEnter bysigning up for my free newsletter! Illustration of a scammer at work (Kurt "CyberGuy" Knutsson)What you need to knowTheFBI has seen a spike in criminal forum posts about emergency data requests and stolen email credentials from police departments and government agencies. Cybercriminals are getting into compromised U.S. and foreign government email accounts and using them to send fake emergency data requests to U.S.-based companies, which exposes customer data for further misuse in other crimes.In August 2024, a popular cybercriminal on an online forum advertised "high-quality .gov emails" for sale, meant for espionage, social engineering, data extortion, emergency data requests and more. The listing even included U.S. credentials, and the seller claimed they could guide buyers on making emergency data requests and even sell real stolen subpoena documents to help them pose as law enforcement.Another cybercriminal boasted about owning government emails from over 25 countries. They claimed anyone can use these emails to send a subpoena to a tech company and get access to usernames, emails, phone numbers and other personal client info. Some con artists are even hosting a "masterclass" on how to create and submit their own emergency data requests to pull data on any social media account, charging $100 for the full rundown. Illustration of a scammer at work (Kurt "CyberGuy" Knutsson)How this phishing scam worksWhen law enforcement, whether federal, state or local, wants information about someones account at a tech company, like their email address or other account details, they typically need a warrant, subpoena or court order. When a tech company receives one of these requests from an official email address, theyre required to comply. So, if a scammer gets access to a government email, they can fake a subpoena and get information on just about anyone.To bypass verification, scammers often send emergency data requests, claiming that someones life is at risk and that the data is needed urgently. Because companies dont want to delay in case of an actual emergency, they may hand over the information, even if the request turns out to be fake. By portraying it as a life-or-death situation, scammers make it harder for companies to take time to verify the request.For example, the FBI reported that earlier this year, a known cybercriminal posted pictures on an online forum of a fake emergency data request theyd sent to PayPal. The scammer tried to make it look legitimate by using a fraudulent mutual legal assistance treaty, claiming it was part of a local investigation into child trafficking, complete with a case number and legal code for verification. However, PayPal recognized that it wasnt a real law enforcement request and denied it. Illustration of a person receiving a phishing email (Kurt "CyberGuy" Knutsson)What can companies do to avoid falling for these phishing scams?1) Verify all data requests: Before sharing sensitive information, companies should verify every data request, even those that look legitimate. Establish a protocol for confirming requests directly with the agency or organization that supposedly sent them.2) Strengthen email security:Use email authentication protocols like DMARC, SPF and DKIM to block emails from unauthorized sources. Implement anti-phishing filters to detect suspicious content in messages.3) Train employees on phishing awareness: Regular training sessions on phishing scams can help employees recognize red flags, such as urgent language, unusual requests or emails from unknown addresses. Employees should be encouraged to report suspicious emails.4) Limit access to sensitive data: Restrict who can view or share sensitive customer data. Fewer people with access means fewer chances for accidental or intentional data leaks.5) Implement emergency verification procedures: Have a clear verification process in place for "emergency" data requests, including steps for double-checking with higher management or legal teams before responding to any urgent request for customer information. Illustration of a scammer at work (Kurt "CyberGuy" Knutsson)Is there something you need to do?This particular phishing scam mostly targets big tech companies, so theres not much you can do directly. However, its a reminder that you shouldnt automatically trust an email, even if it comes from a .gov address. Here are some steps you can take to stay safe.1) Double-check email addresses and links: Even if an email looks official, take a moment to check the senders email address and hover over any links to see where they actually lead. Be cautious if anything looks off. The best way to safeguard yourself from malicious links is to have antivirus software installed on all your devices. This protection can also alert you to phishing emails and ransomware scams, keeping your personal information and digital assets safe.Get my picks for the best 2024 antivirus protection winners for your Windows, Mac, Android and iOS devices.2) Enable two-factor authentication (2FA):Use2FA for all sensitive accounts. This extra layer of security helps protect you even if your login credentials are compromised.3) Stay updated on phishing scams:Keep an eye on the latest phishing tactics, so you know what to look out for. Regular updates help you spot new types of scams before they affect you.4) Verify suspicious requests:If you get an unexpected email asking for sensitive info, contact the sender directly through an official channel to confirm the request. Illustration of a scammer at work (Kurt "CyberGuy" Knutsson)Kurts key takeawayScammers are taking phishing emails to a whole new level. I often recommend checking the email carefully when you receive anything suspicious to see if its legit. But now, since scammers can even access government emails, you need to be extra cautious. This phishing scam seems to target mostly big tech companies, so its on them to strengthen their security and verify every request thoroughly before sharing any user information. It's also up to governments worldwide to protect their digital assets from being compromised.Whats your stance on how governments are handling cybersecurity? Are they doing enough to protect sensitive data? Let us know by writing us at Cyberguy.com/Contact.CLICK HERE TO GET THE FOX NEWS APPFor more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.Follow Kurt on his social channels:Answers to the most asked CyberGuy questions:New from Kurt:Copyright 2024 CyberGuy.com.All rights reserved. Kurt "CyberGuy" Knutsson is an award-winning tech journalist who has a deep love of technology, gear and gadgets that make life better with his contributions for Fox News & FOX Business beginning mornings on "FOX & Friends." Got a tech question? Get Kurts free CyberGuy Newsletter, share your voice, a story idea or comment at CyberGuy.com.0 Comments 0 Shares 146 Views
WWW.FOXNEWS.COMAlarming rise of fake legal requests: What it means for your privacyPublished November 12, 2024 10:00am EST close Tips to protect yourself against bank scams Scammers often ask for answers to secret questions for crucial information needed to access accounts. Phishing emails are one of the most common tricks scammers use, but theyre usually easy to catch if you pay attention. Awkward grammar, random details and, most importantly, an unofficial email address are dead giveaways. For example, you might get an email saying your Apple IDs been disabled, but the senders email wont actually be from Apple. Now, though, scammers are finding ways to get around this.According to the FBI, theres been a recent rise in cybercriminal services using hacked police and government email accounts to send fake subpoenas and data requests to U.S.-based tech companies.IM GIVING AWAY A $500 GIFT CARD FOR THE HOLIDAYSEnter bysigning up for my free newsletter! Illustration of a scammer at work (Kurt "CyberGuy" Knutsson)What you need to knowTheFBI has seen a spike in criminal forum posts about emergency data requests and stolen email credentials from police departments and government agencies. Cybercriminals are getting into compromised U.S. and foreign government email accounts and using them to send fake emergency data requests to U.S.-based companies, which exposes customer data for further misuse in other crimes.In August 2024, a popular cybercriminal on an online forum advertised "high-quality .gov emails" for sale, meant for espionage, social engineering, data extortion, emergency data requests and more. The listing even included U.S. credentials, and the seller claimed they could guide buyers on making emergency data requests and even sell real stolen subpoena documents to help them pose as law enforcement.Another cybercriminal boasted about owning government emails from over 25 countries. They claimed anyone can use these emails to send a subpoena to a tech company and get access to usernames, emails, phone numbers and other personal client info. Some con artists are even hosting a "masterclass" on how to create and submit their own emergency data requests to pull data on any social media account, charging $100 for the full rundown. Illustration of a scammer at work (Kurt "CyberGuy" Knutsson)How this phishing scam worksWhen law enforcement, whether federal, state or local, wants information about someones account at a tech company, like their email address or other account details, they typically need a warrant, subpoena or court order. When a tech company receives one of these requests from an official email address, theyre required to comply. So, if a scammer gets access to a government email, they can fake a subpoena and get information on just about anyone.To bypass verification, scammers often send emergency data requests, claiming that someones life is at risk and that the data is needed urgently. Because companies dont want to delay in case of an actual emergency, they may hand over the information, even if the request turns out to be fake. By portraying it as a life-or-death situation, scammers make it harder for companies to take time to verify the request.For example, the FBI reported that earlier this year, a known cybercriminal posted pictures on an online forum of a fake emergency data request theyd sent to PayPal. The scammer tried to make it look legitimate by using a fraudulent mutual legal assistance treaty, claiming it was part of a local investigation into child trafficking, complete with a case number and legal code for verification. However, PayPal recognized that it wasnt a real law enforcement request and denied it. Illustration of a person receiving a phishing email (Kurt "CyberGuy" Knutsson)What can companies do to avoid falling for these phishing scams?1) Verify all data requests: Before sharing sensitive information, companies should verify every data request, even those that look legitimate. Establish a protocol for confirming requests directly with the agency or organization that supposedly sent them.2) Strengthen email security:Use email authentication protocols like DMARC, SPF and DKIM to block emails from unauthorized sources. Implement anti-phishing filters to detect suspicious content in messages.3) Train employees on phishing awareness: Regular training sessions on phishing scams can help employees recognize red flags, such as urgent language, unusual requests or emails from unknown addresses. Employees should be encouraged to report suspicious emails.4) Limit access to sensitive data: Restrict who can view or share sensitive customer data. Fewer people with access means fewer chances for accidental or intentional data leaks.5) Implement emergency verification procedures: Have a clear verification process in place for "emergency" data requests, including steps for double-checking with higher management or legal teams before responding to any urgent request for customer information. Illustration of a scammer at work (Kurt "CyberGuy" Knutsson)Is there something you need to do?This particular phishing scam mostly targets big tech companies, so theres not much you can do directly. However, its a reminder that you shouldnt automatically trust an email, even if it comes from a .gov address. Here are some steps you can take to stay safe.1) Double-check email addresses and links: Even if an email looks official, take a moment to check the senders email address and hover over any links to see where they actually lead. Be cautious if anything looks off. The best way to safeguard yourself from malicious links is to have antivirus software installed on all your devices. This protection can also alert you to phishing emails and ransomware scams, keeping your personal information and digital assets safe.Get my picks for the best 2024 antivirus protection winners for your Windows, Mac, Android and iOS devices.2) Enable two-factor authentication (2FA):Use2FA for all sensitive accounts. This extra layer of security helps protect you even if your login credentials are compromised.3) Stay updated on phishing scams:Keep an eye on the latest phishing tactics, so you know what to look out for. Regular updates help you spot new types of scams before they affect you.4) Verify suspicious requests:If you get an unexpected email asking for sensitive info, contact the sender directly through an official channel to confirm the request. Illustration of a scammer at work (Kurt "CyberGuy" Knutsson)Kurts key takeawayScammers are taking phishing emails to a whole new level. I often recommend checking the email carefully when you receive anything suspicious to see if its legit. But now, since scammers can even access government emails, you need to be extra cautious. This phishing scam seems to target mostly big tech companies, so its on them to strengthen their security and verify every request thoroughly before sharing any user information. It's also up to governments worldwide to protect their digital assets from being compromised.Whats your stance on how governments are handling cybersecurity? Are they doing enough to protect sensitive data? Let us know by writing us at Cyberguy.com/Contact.CLICK HERE TO GET THE FOX NEWS APPFor more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.Follow Kurt on his social channels:Answers to the most asked CyberGuy questions:New from Kurt:Copyright 2024 CyberGuy.com.All rights reserved. Kurt "CyberGuy" Knutsson is an award-winning tech journalist who has a deep love of technology, gear and gadgets that make life better with his contributions for Fox News & FOX Business beginning mornings on "FOX & Friends." Got a tech question? Get Kurts free CyberGuy Newsletter, share your voice, a story idea or comment at CyberGuy.com.0 Comments 0 Shares 146 Views -
 WWW.FOXNEWS.COMPrada's out-of-this-world spacesuit for NASAPublished November 12, 2024 6:00am EST close 'CyberGuy': Prada's out-of-this-world spacesuit for NASA Kurt Knutsson discusses how Axiom Space and luxury designer Prada are collaborating on NASA's Artemis III spacesuit design. In an unexpected yet fascinating collaboration, Axiom Space has joined forces with the prestigious luxury Italian fashion house Prada to design the next-generation spacesuit for NASA's Artemis program. This partnership marks a significant shift in how spacesuits are conceived, merging high fashion with advanced engineering.IM GIVING AWAY A $500 GIFT CARD FOR THE HOLIDAYSEnter bysigning up for my free newsletterhere! AxEMU space suit (Axiom Space) (Kurt "CyberGuy" Knutsson)The need for new spacesuitsNASA has been using the same extravehicular activity suits since 1982, and there have been no new designs for lunar missions since the Apollo program ended in 1972. To address this gap, NASA awarded Axiom Space a contract worth $228 million in 2022 to develop a modern version of the Apollo suit, leading to the creation of theAxiom Extravehicular Mobility Unit (AxEMU) suit. AxEMU space suit (Axiom Space) (Kurt "CyberGuy" Knutsson)Blending fashion with functionAt first glance, involving a fashion designer in an engineering project may seem unusual. However, Axiom and Prada's collaboration highlights an innovative approach to spacesuit design. The AxEMU suit incorporates aesthetic considerations alongside functionality, reflecting a trend seen inprevious designs, such as those for SpaceX's Dragon astronauts. AxEMU space suit (Axiom Space) (Kurt "CyberGuy" Knutsson)Key features of the AxEMU SuitAdaptive fit: Unlike previous suits tailored for individual astronauts, the AxEMU is designed to fit 99% of both males and females, enhancing comfort and usability.Advanced materials: The suit features high-performance materials developed through Prada's expertise, ensuring durability against lunar conditions.Enhanced mobility: Innovative joint designs allow for a greater range of motion, enabling astronauts to perform tasks more effectively.Safety innovations: The AxEMU includes redundant systems and self-diagnostic capabilities to ensure astronaut safety during missions. AxEMU space suit (Axiom Space) (Kurt "CyberGuy" Knutsson)Unveiling at the International Astronautical CongressThe AxEMU was formally unveiled at the International Astronautical Congress in Milan. During this event, both Axiom Space and Prada emphasized their commitment to pushing boundaries in space exploration through collaborative efforts.Russell Ralston, executive vice president of extravehicular activity at Axiom Space, said,"We are pioneering a new era in space exploration where partnerships are imperative to the commercialization of space."Lorenzo Bertelli, Prada Group chief marketing officer, added,"Going beyond our limits is one of the companys values that perfectly reflects the spirit of the Prada brand." AxEMU space suit (Axiom Space) (Kurt "CyberGuy" Knutsson)Testing and future prospectsThe AxEMU is currently undergoing extensive testing, including simulations designed to mimic lunar conditions. It is expected to enter its critical design review phase in 2025. This rigorous testing process aims to ensure that astronauts are equipped with reliable and advanced capabilities for future lunar missions. AxEMU space suit (Axiom Space) (Kurt "CyberGuy" Knutsson)Kurt's key takeawaysWho would have thought that high fashion and space exploration could find common ground? Yet here we are, witnessing a luxury brand contribute its expertise to one of humanity's most ambitious endeavors. By combining Prada's knowledge of materials and craftsmanship with Axiom's engineering prowess, we're seeing a suit that promises to be more comfortable, more adaptable and more efficient than anything that's come before.Could we see more fashion houses getting involved in space tech? One thing's for sure: The AxEMU suit is a perfect example of what can happen when we think outside the box and bring diverse expertise together. As we continue to reach for the stars, it seems that the sky is no longer the limit, not even for fashion.How do you feel about the role of aesthetics in spacesuit design? Do you think looking good in space is just as important as functionality?Let us know by writing us at Cyberguy.com/Contact.CLICK HERE TO GET THE FOX NEWS APPFor more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.Follow Kurt on his social channels:Answers to the most asked CyberGuy questions:New from Kurt:Copyright 2024 CyberGuy.com.All rights reserved. Kurt "CyberGuy" Knutsson is an award-winning tech journalist who has a deep love of technology, gear and gadgets that make life better with his contributions for Fox News & FOX Business beginning mornings on "FOX & Friends." Got a tech question? Get Kurts free CyberGuy Newsletter, share your voice, a story idea or comment at CyberGuy.com.0 Comments 0 Shares 140 Views
WWW.FOXNEWS.COMPrada's out-of-this-world spacesuit for NASAPublished November 12, 2024 6:00am EST close 'CyberGuy': Prada's out-of-this-world spacesuit for NASA Kurt Knutsson discusses how Axiom Space and luxury designer Prada are collaborating on NASA's Artemis III spacesuit design. In an unexpected yet fascinating collaboration, Axiom Space has joined forces with the prestigious luxury Italian fashion house Prada to design the next-generation spacesuit for NASA's Artemis program. This partnership marks a significant shift in how spacesuits are conceived, merging high fashion with advanced engineering.IM GIVING AWAY A $500 GIFT CARD FOR THE HOLIDAYSEnter bysigning up for my free newsletterhere! AxEMU space suit (Axiom Space) (Kurt "CyberGuy" Knutsson)The need for new spacesuitsNASA has been using the same extravehicular activity suits since 1982, and there have been no new designs for lunar missions since the Apollo program ended in 1972. To address this gap, NASA awarded Axiom Space a contract worth $228 million in 2022 to develop a modern version of the Apollo suit, leading to the creation of theAxiom Extravehicular Mobility Unit (AxEMU) suit. AxEMU space suit (Axiom Space) (Kurt "CyberGuy" Knutsson)Blending fashion with functionAt first glance, involving a fashion designer in an engineering project may seem unusual. However, Axiom and Prada's collaboration highlights an innovative approach to spacesuit design. The AxEMU suit incorporates aesthetic considerations alongside functionality, reflecting a trend seen inprevious designs, such as those for SpaceX's Dragon astronauts. AxEMU space suit (Axiom Space) (Kurt "CyberGuy" Knutsson)Key features of the AxEMU SuitAdaptive fit: Unlike previous suits tailored for individual astronauts, the AxEMU is designed to fit 99% of both males and females, enhancing comfort and usability.Advanced materials: The suit features high-performance materials developed through Prada's expertise, ensuring durability against lunar conditions.Enhanced mobility: Innovative joint designs allow for a greater range of motion, enabling astronauts to perform tasks more effectively.Safety innovations: The AxEMU includes redundant systems and self-diagnostic capabilities to ensure astronaut safety during missions. AxEMU space suit (Axiom Space) (Kurt "CyberGuy" Knutsson)Unveiling at the International Astronautical CongressThe AxEMU was formally unveiled at the International Astronautical Congress in Milan. During this event, both Axiom Space and Prada emphasized their commitment to pushing boundaries in space exploration through collaborative efforts.Russell Ralston, executive vice president of extravehicular activity at Axiom Space, said,"We are pioneering a new era in space exploration where partnerships are imperative to the commercialization of space."Lorenzo Bertelli, Prada Group chief marketing officer, added,"Going beyond our limits is one of the companys values that perfectly reflects the spirit of the Prada brand." AxEMU space suit (Axiom Space) (Kurt "CyberGuy" Knutsson)Testing and future prospectsThe AxEMU is currently undergoing extensive testing, including simulations designed to mimic lunar conditions. It is expected to enter its critical design review phase in 2025. This rigorous testing process aims to ensure that astronauts are equipped with reliable and advanced capabilities for future lunar missions. AxEMU space suit (Axiom Space) (Kurt "CyberGuy" Knutsson)Kurt's key takeawaysWho would have thought that high fashion and space exploration could find common ground? Yet here we are, witnessing a luxury brand contribute its expertise to one of humanity's most ambitious endeavors. By combining Prada's knowledge of materials and craftsmanship with Axiom's engineering prowess, we're seeing a suit that promises to be more comfortable, more adaptable and more efficient than anything that's come before.Could we see more fashion houses getting involved in space tech? One thing's for sure: The AxEMU suit is a perfect example of what can happen when we think outside the box and bring diverse expertise together. As we continue to reach for the stars, it seems that the sky is no longer the limit, not even for fashion.How do you feel about the role of aesthetics in spacesuit design? Do you think looking good in space is just as important as functionality?Let us know by writing us at Cyberguy.com/Contact.CLICK HERE TO GET THE FOX NEWS APPFor more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.Follow Kurt on his social channels:Answers to the most asked CyberGuy questions:New from Kurt:Copyright 2024 CyberGuy.com.All rights reserved. Kurt "CyberGuy" Knutsson is an award-winning tech journalist who has a deep love of technology, gear and gadgets that make life better with his contributions for Fox News & FOX Business beginning mornings on "FOX & Friends." Got a tech question? Get Kurts free CyberGuy Newsletter, share your voice, a story idea or comment at CyberGuy.com.0 Comments 0 Shares 140 Views -
 WWW.COMPUTERWEEKLY.COMMicrosoft fixes 89 CVEs on penultimate Patch Tuesday of 2024Microsoft has issued fixes addressing a total of 89 new Common Vulnerabilities and Exposures (CVEs) 92 including third-party disclosures to mark the penultimate Patch Tuesday of 2024, including four critical issues and a number of flaws that could be considered zero-days.Of these issues, one meets the full traditional definition of a full zero-day, a vulnerability that is both public and known to be exploited. This is CVE-2024-43451, a spoofing vulnerability in New Technology LAN Manager (NTLM) Hash.NTLM is a set of security protocols used to authenticate users identities. It dates back years and has been largely supplanted by vastly more secure protocols Microsoft has not recommended its use in over a decade, but since it was used in Internet Explorer, it remains supported to some extent and continues to cause problems, not least because at this stage, it is incredibly insecure.In this instance, successful exploitation of this issue could lead to total loss of confidentiality, according to Microsoft, as it discloses a users NTLMv2 hash to an attacker who could then use it to authenticate as the user if the victim can be tricked into minimal interaction with a malicious file, which could include merely selecting or clicking it, not even opening it. This may make it considerably more dangerous than its comparatively low severity score may indicate.Mike Walters, president and co-founder of Action1, explained: This issue arises from the mechanism where NTLM authentication credentials, specifically NTLMv2 hashes, are improperly exposed via a maliciously crafted file.The root cause of this vulnerability lies in improperly handling file interactions within systems, potentially allowing attackers to extract NTLMv2 hashes without requiring complete file execution, he told Computer Weekly in emailed commentary.All supported versions of Microsoft Windows are vulnerable to this issue, said Walters, especially if they use applications reliant on MSHTML and EdgeHTML platforms, while risk is further increased across different system environments thanks to the involvement of other scripting engines.Walters said the main concern with CVE-2024-43451 is the disclosure of NTLMv2 hashes that can be used to authenticate as the user and leveraged in pass-the-hash attacks, enabling further lateral movement for a canny threat actor.This vulnerability is particularly effective in phishing scenarios, where users might be deceived into interacting with malicious files. Once NTLM hashes are obtained, attackers can combine them with other network vulnerabilities to extend their access and compromise additional systems, he said.Organisations that heavily use Windows in environments with substantial network file sharing or legacy applications dependent on Internet Explorer and related platforms face heightened risk. Those lacking robust user training and monitoring systems to detect unusual file interactions may be more susceptible to exploitation.Also on the list is CVE-2024-49309, which is exploited but not yet public. This is an elevation of privilege (EoP) vulnerability in Windows Task Scheduler.This stems from an issue where authentication tokens or credentials are improperly managed and could allow a low-privileged attacker to gain deeper access if they can execute a malicious application designed for the purpose. It impacts multiple versions of Windows that incorporate Task Scheduler as part of their routine task automation processes, and it is thought that environments with shared or multiple-user setups may be particularly vulnerable to it.This vulnerability serves as a potential entry point for attackers who have already accessed a system with low privilege. Once privileges are escalated, these attackers can utilise this foothold for further lateral movement within a network or to exploit other vulnerabilities that necessitate higher access levels, said Walters.The nature of this vulnerability is especially concerning in corporate settings where individual users possess specific task automation privileges that could be exploited to gain unauthorised access.Four further vulnerabilities have been made public but as of yet have seen no exploitation, according to Microsoft, and one of these, CVE-2024-5535, a remote code execution issue in OpenSSL, is among the three third-party disclosures incorporated into this months drop.The other three are CVE-2024-43498, a remote code execution (RCE) vulnerability in .NET and Visual Studio, CVE-2024-49019, an EoP vulnerability in Active Directory Certificate Services, and CVE-2024-49040, a spoofing vulnerability in Microsoft Exchange Server.Chris Goettl, vice president of security products at Ivanti, shared further thoughts on both the Active Directory and Microsoft Exchange Server issues, and urged defenders to treat them as higher priorities than the official guidance might imply.[CVE-2024-49019] is rated Important and has a CVSS v3.1 score of 7.8. If exploited, the attacker could gain domain administrator privileges. The vulnerability does provide additional mitigations including removing overly broad enrol or auto-enrol permissions, removing unused templates from certificate authorities, and securing templates that allow you to specify the subject in the request, said Goettl.The vulnerability affects Windows Server 2008 and later Server OS editions. From a risk-based perspective, a public disclosure puts this vulnerability at a higher risk of being exploited and may warrant treating the vulnerability as a higher severity.Goettl continued: [CVE-2024-49040] is rated Important and has a CVSS v3.1 score of 7.5. The vulnerability exists in the P2 From header verification. Microsoft Exchange Server is often targeted by threat actors who specialise in Exchange exploits. From a risk-based prioritisation perspective, the public disclosure and availably of PoC level exploit code warrants treating this vulnerability as Critical.Finally, three other Critical issues are listed as, CVE-2024-43625, an EoP vulnerability in Microsoft Windows VMSwitch; CVE-2024-43639, an RCE vulnerability in Windows Kerberos; and CVE-2024-49056, an EoP vulnerability in Airlift.microsoft.com. In each of these instances, no proof of concept has yet been made public and no exploitation in the wild has been observed.Read more about Patch TuesdayOctober 2024: Stand-out vulnerabilities in Microsofts latest Patch Tuesday drop include problems in Microsoft Management Console and the Windows MSHTML Platform.September 2024: Four critical remote code execution bugs in Windows and three critical elevated privileges vulnerabilitieswill keep admins busy.August 2024: Microsoft patches six actively exploited zero-days among over 100 issuesduring its regular monthly update.July 2024: Microsoft has fixed almost 140 vulnerabilities in its latest monthly update, with a Hyper-V zero-daysingled out for urgent attention.June 2024: An RCE vulnerability in a Microsoft messaging feature and a third-party flaw in a DNS authentication protocol are the most pressing issues to address inMicrosofts latest Patch Tuesday update.May 2024: A critical SharePoint vulnerability warrants attention this month, but it is another flaw that seems to be linked to the infamous Qakbot malwarethat is drawing attention.April 2024: Support for the Windows Server 2008 OS ended in 2020, but four years on and there's a live exploit of a security flawthat impacts all Windows users.March 2024: Two critical vulnerabilities in Windows Hyper-V stand out onan otherwise unremarkable Patch Tuesday.February 2024: Two security feature bypasses impacting Microsoft SmartScreen are on the February Patch Tuesday docket,among more than 70 issues.January 2024: Microsoft starts 2024 right with another slimline Patch Tuesday drop, but there are some critical vulnerabilities to be alert to, including a number ofman-in-the-middle attack vectors.0 Comments 0 Shares 125 Views
WWW.COMPUTERWEEKLY.COMMicrosoft fixes 89 CVEs on penultimate Patch Tuesday of 2024Microsoft has issued fixes addressing a total of 89 new Common Vulnerabilities and Exposures (CVEs) 92 including third-party disclosures to mark the penultimate Patch Tuesday of 2024, including four critical issues and a number of flaws that could be considered zero-days.Of these issues, one meets the full traditional definition of a full zero-day, a vulnerability that is both public and known to be exploited. This is CVE-2024-43451, a spoofing vulnerability in New Technology LAN Manager (NTLM) Hash.NTLM is a set of security protocols used to authenticate users identities. It dates back years and has been largely supplanted by vastly more secure protocols Microsoft has not recommended its use in over a decade, but since it was used in Internet Explorer, it remains supported to some extent and continues to cause problems, not least because at this stage, it is incredibly insecure.In this instance, successful exploitation of this issue could lead to total loss of confidentiality, according to Microsoft, as it discloses a users NTLMv2 hash to an attacker who could then use it to authenticate as the user if the victim can be tricked into minimal interaction with a malicious file, which could include merely selecting or clicking it, not even opening it. This may make it considerably more dangerous than its comparatively low severity score may indicate.Mike Walters, president and co-founder of Action1, explained: This issue arises from the mechanism where NTLM authentication credentials, specifically NTLMv2 hashes, are improperly exposed via a maliciously crafted file.The root cause of this vulnerability lies in improperly handling file interactions within systems, potentially allowing attackers to extract NTLMv2 hashes without requiring complete file execution, he told Computer Weekly in emailed commentary.All supported versions of Microsoft Windows are vulnerable to this issue, said Walters, especially if they use applications reliant on MSHTML and EdgeHTML platforms, while risk is further increased across different system environments thanks to the involvement of other scripting engines.Walters said the main concern with CVE-2024-43451 is the disclosure of NTLMv2 hashes that can be used to authenticate as the user and leveraged in pass-the-hash attacks, enabling further lateral movement for a canny threat actor.This vulnerability is particularly effective in phishing scenarios, where users might be deceived into interacting with malicious files. Once NTLM hashes are obtained, attackers can combine them with other network vulnerabilities to extend their access and compromise additional systems, he said.Organisations that heavily use Windows in environments with substantial network file sharing or legacy applications dependent on Internet Explorer and related platforms face heightened risk. Those lacking robust user training and monitoring systems to detect unusual file interactions may be more susceptible to exploitation.Also on the list is CVE-2024-49309, which is exploited but not yet public. This is an elevation of privilege (EoP) vulnerability in Windows Task Scheduler.This stems from an issue where authentication tokens or credentials are improperly managed and could allow a low-privileged attacker to gain deeper access if they can execute a malicious application designed for the purpose. It impacts multiple versions of Windows that incorporate Task Scheduler as part of their routine task automation processes, and it is thought that environments with shared or multiple-user setups may be particularly vulnerable to it.This vulnerability serves as a potential entry point for attackers who have already accessed a system with low privilege. Once privileges are escalated, these attackers can utilise this foothold for further lateral movement within a network or to exploit other vulnerabilities that necessitate higher access levels, said Walters.The nature of this vulnerability is especially concerning in corporate settings where individual users possess specific task automation privileges that could be exploited to gain unauthorised access.Four further vulnerabilities have been made public but as of yet have seen no exploitation, according to Microsoft, and one of these, CVE-2024-5535, a remote code execution issue in OpenSSL, is among the three third-party disclosures incorporated into this months drop.The other three are CVE-2024-43498, a remote code execution (RCE) vulnerability in .NET and Visual Studio, CVE-2024-49019, an EoP vulnerability in Active Directory Certificate Services, and CVE-2024-49040, a spoofing vulnerability in Microsoft Exchange Server.Chris Goettl, vice president of security products at Ivanti, shared further thoughts on both the Active Directory and Microsoft Exchange Server issues, and urged defenders to treat them as higher priorities than the official guidance might imply.[CVE-2024-49019] is rated Important and has a CVSS v3.1 score of 7.8. If exploited, the attacker could gain domain administrator privileges. The vulnerability does provide additional mitigations including removing overly broad enrol or auto-enrol permissions, removing unused templates from certificate authorities, and securing templates that allow you to specify the subject in the request, said Goettl.The vulnerability affects Windows Server 2008 and later Server OS editions. From a risk-based perspective, a public disclosure puts this vulnerability at a higher risk of being exploited and may warrant treating the vulnerability as a higher severity.Goettl continued: [CVE-2024-49040] is rated Important and has a CVSS v3.1 score of 7.5. The vulnerability exists in the P2 From header verification. Microsoft Exchange Server is often targeted by threat actors who specialise in Exchange exploits. From a risk-based prioritisation perspective, the public disclosure and availably of PoC level exploit code warrants treating this vulnerability as Critical.Finally, three other Critical issues are listed as, CVE-2024-43625, an EoP vulnerability in Microsoft Windows VMSwitch; CVE-2024-43639, an RCE vulnerability in Windows Kerberos; and CVE-2024-49056, an EoP vulnerability in Airlift.microsoft.com. In each of these instances, no proof of concept has yet been made public and no exploitation in the wild has been observed.Read more about Patch TuesdayOctober 2024: Stand-out vulnerabilities in Microsofts latest Patch Tuesday drop include problems in Microsoft Management Console and the Windows MSHTML Platform.September 2024: Four critical remote code execution bugs in Windows and three critical elevated privileges vulnerabilitieswill keep admins busy.August 2024: Microsoft patches six actively exploited zero-days among over 100 issuesduring its regular monthly update.July 2024: Microsoft has fixed almost 140 vulnerabilities in its latest monthly update, with a Hyper-V zero-daysingled out for urgent attention.June 2024: An RCE vulnerability in a Microsoft messaging feature and a third-party flaw in a DNS authentication protocol are the most pressing issues to address inMicrosofts latest Patch Tuesday update.May 2024: A critical SharePoint vulnerability warrants attention this month, but it is another flaw that seems to be linked to the infamous Qakbot malwarethat is drawing attention.April 2024: Support for the Windows Server 2008 OS ended in 2020, but four years on and there's a live exploit of a security flawthat impacts all Windows users.March 2024: Two critical vulnerabilities in Windows Hyper-V stand out onan otherwise unremarkable Patch Tuesday.February 2024: Two security feature bypasses impacting Microsoft SmartScreen are on the February Patch Tuesday docket,among more than 70 issues.January 2024: Microsoft starts 2024 right with another slimline Patch Tuesday drop, but there are some critical vulnerabilities to be alert to, including a number ofman-in-the-middle attack vectors.0 Comments 0 Shares 125 Views -
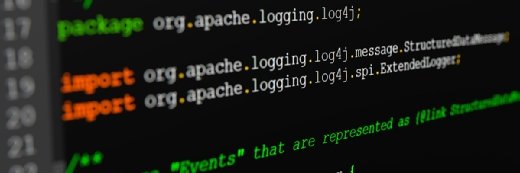 WWW.COMPUTERWEEKLY.COMZero-day exploits increasingly sought out by attackersAndreas Prott - stock.adobe.comNewsZero-day exploits increasingly sought out by attackersThreat actors increasingly favour zero-day exploits to attack their victims before patches become available according to the NCSC and CISA, which have just published a list of the most widely-used vulnerabilities of 2023ByAlex Scroxton,Security EditorPublished: 12 Nov 2024 16:49 Threat actors both state-backed and financially-motivated are increasingly taking advantage of previously unknown vulnerabilities, or zero-days, to compromise their victims before fixes or patches are made available by the tech industry, according to a new advisory published by the Five Eyes cyber agencies, including the UKs National Cyber Security Centre (NCSC) and the United States Cybersecurity and Infrastructure Security Agency (CISA).The agencies have collectively drawn up a list of the 15 most exploited vulnerabilities of 2023 and found that the majority of exploited vulnerabilities were zero-days compared to less than half in 2022. The trend has continued through 2024, said the NCSC.The NCSC said that defenders needed to up their game when it comes to vulnerability management, paying particular attention to applying updates as quickly as possible when they do arrive, and to making sure they have identified all the potentially affected IT assets in their estates.The organisation also urged suppliers and developers to do more to implement secure-by-design principles into their products, something that the Five Eyes governments Australia, Canada, New Zealand, the UK and the United States have become particularly vocal about in the past 18 months. Doing so helps reduce the risk of vulnerabilities being accidentally introduced during development, only to be taken advantage off further down the line.More routine initial exploitation of zero-day vulnerabilities represents the new normal which should concern end-user organisations and vendors alike as malicious actors seek to infiltrate networks, said NCSC chief technology officer (CTO) Ollie Whitehouse.To reduce the risk of compromise, it is vital all organisations stay on the front foot by applying patches promptly and insisting upon secure-by-design products in the technology marketplace, said Whitehouse.We urge network defenders to be vigilant with vulnerability management, have situational awareness in operations and call on product developers to make security a core component of product design and life-cycle to help stamp out this insidious game of whack-a-mole at source, he added.The full list of the vulnerabilities most frequently exploited during 2023 is as follows:CVE-2023-3519, a code injection flaw in Citrix NetScaler ADC and NetScaler Gateway;CVE-2023-4966, a buffer overflow vulnerability in Citrix NetScaler ADC and NetScaler Gateway, aka Citrix Bleed;CVE-2023-20198, an elevation of privilege (EoP) issue in Cisco IOS XE Web UI;CVE-2023-20273, a web UI command injection bug in Cisco IOS XE;CVE-2023-27997, a heap-based buffer overflow flaw in Fortinet FortiOS and FortiProxy SSL-VPN;CVE-2023-34362, a SQL injection vulnerability in Progress MOVEit Transfer, infamously exploited by the Cl0p ransomware gang, the fall-out from which is still being felt;CVE-2023-22515, a broken access control vuln it Atlassian Confluence Data Center and Server;CVE-2021-44228, a remote code execution (RCE) issue in Apache Log4j2, aka Log4Shell, the source of a major incident at the end of 2021 and still being widely-abused years later;CVE-2023-2868, an improper input validation flaw in Barracuda Networks ESG Appliance;CVE-2022-47966, an RCE issue in Zoho ManageEngine;CVE-2023-27350, an improper access control vulnerability in PaperCut MF/NG;CVE-2020-1472, an EoP vuln in Microsoft Netlogon, the source of another high-profile historic incident that there is now no excuse for not having addressed;CVE-2023-427983, an authentication bypass flaw in JetBrains TeamCity;CVE-2023-23397, an EoP issue in Microsoft Office Outlook, widely-used by Russian spooks;And last but not least, CVE-2023-49103, an information disclosure vuln in ownCloud graphapi.The full list, which can be downloaded from CISA, also contains details of a number of other issues that were observed being routinely exploited during 2023, prominent among them two vulnerabilities in Ivanti products disclosed in August 2023, and the infamous Fortra GoAnywhere flaw exploited, yet again, by the Cl0p gang.Read more about recent zero-daysQualcomm urges customers to patch the memory corruption vulnerability as Google researchers have observed targeted exploitation in the wild against the flaw.According to Fortinet, the FortiManager vulnerability 'may allow a remote unauthenticated attacker to execute arbitrary code or commands via specially crafted requests.More than two weeks after threat actors exploited a zero-day vulnerability in a third-party utility to breach Rackspace, the details about the flaw and the utility remain unknown.In The Current Issue:Interview: Niall Robinson, head of product innovation, Met OfficeIAM: Enterprises face a long, hard road to improveDownload Current IssueHow enterprises can improve ROI on AI investments Data MattersHow To "Vawlt" Superclouds Networks GenerationView All Blogs0 Comments 0 Shares 150 Views
WWW.COMPUTERWEEKLY.COMZero-day exploits increasingly sought out by attackersAndreas Prott - stock.adobe.comNewsZero-day exploits increasingly sought out by attackersThreat actors increasingly favour zero-day exploits to attack their victims before patches become available according to the NCSC and CISA, which have just published a list of the most widely-used vulnerabilities of 2023ByAlex Scroxton,Security EditorPublished: 12 Nov 2024 16:49 Threat actors both state-backed and financially-motivated are increasingly taking advantage of previously unknown vulnerabilities, or zero-days, to compromise their victims before fixes or patches are made available by the tech industry, according to a new advisory published by the Five Eyes cyber agencies, including the UKs National Cyber Security Centre (NCSC) and the United States Cybersecurity and Infrastructure Security Agency (CISA).The agencies have collectively drawn up a list of the 15 most exploited vulnerabilities of 2023 and found that the majority of exploited vulnerabilities were zero-days compared to less than half in 2022. The trend has continued through 2024, said the NCSC.The NCSC said that defenders needed to up their game when it comes to vulnerability management, paying particular attention to applying updates as quickly as possible when they do arrive, and to making sure they have identified all the potentially affected IT assets in their estates.The organisation also urged suppliers and developers to do more to implement secure-by-design principles into their products, something that the Five Eyes governments Australia, Canada, New Zealand, the UK and the United States have become particularly vocal about in the past 18 months. Doing so helps reduce the risk of vulnerabilities being accidentally introduced during development, only to be taken advantage off further down the line.More routine initial exploitation of zero-day vulnerabilities represents the new normal which should concern end-user organisations and vendors alike as malicious actors seek to infiltrate networks, said NCSC chief technology officer (CTO) Ollie Whitehouse.To reduce the risk of compromise, it is vital all organisations stay on the front foot by applying patches promptly and insisting upon secure-by-design products in the technology marketplace, said Whitehouse.We urge network defenders to be vigilant with vulnerability management, have situational awareness in operations and call on product developers to make security a core component of product design and life-cycle to help stamp out this insidious game of whack-a-mole at source, he added.The full list of the vulnerabilities most frequently exploited during 2023 is as follows:CVE-2023-3519, a code injection flaw in Citrix NetScaler ADC and NetScaler Gateway;CVE-2023-4966, a buffer overflow vulnerability in Citrix NetScaler ADC and NetScaler Gateway, aka Citrix Bleed;CVE-2023-20198, an elevation of privilege (EoP) issue in Cisco IOS XE Web UI;CVE-2023-20273, a web UI command injection bug in Cisco IOS XE;CVE-2023-27997, a heap-based buffer overflow flaw in Fortinet FortiOS and FortiProxy SSL-VPN;CVE-2023-34362, a SQL injection vulnerability in Progress MOVEit Transfer, infamously exploited by the Cl0p ransomware gang, the fall-out from which is still being felt;CVE-2023-22515, a broken access control vuln it Atlassian Confluence Data Center and Server;CVE-2021-44228, a remote code execution (RCE) issue in Apache Log4j2, aka Log4Shell, the source of a major incident at the end of 2021 and still being widely-abused years later;CVE-2023-2868, an improper input validation flaw in Barracuda Networks ESG Appliance;CVE-2022-47966, an RCE issue in Zoho ManageEngine;CVE-2023-27350, an improper access control vulnerability in PaperCut MF/NG;CVE-2020-1472, an EoP vuln in Microsoft Netlogon, the source of another high-profile historic incident that there is now no excuse for not having addressed;CVE-2023-427983, an authentication bypass flaw in JetBrains TeamCity;CVE-2023-23397, an EoP issue in Microsoft Office Outlook, widely-used by Russian spooks;And last but not least, CVE-2023-49103, an information disclosure vuln in ownCloud graphapi.The full list, which can be downloaded from CISA, also contains details of a number of other issues that were observed being routinely exploited during 2023, prominent among them two vulnerabilities in Ivanti products disclosed in August 2023, and the infamous Fortra GoAnywhere flaw exploited, yet again, by the Cl0p gang.Read more about recent zero-daysQualcomm urges customers to patch the memory corruption vulnerability as Google researchers have observed targeted exploitation in the wild against the flaw.According to Fortinet, the FortiManager vulnerability 'may allow a remote unauthenticated attacker to execute arbitrary code or commands via specially crafted requests.More than two weeks after threat actors exploited a zero-day vulnerability in a third-party utility to breach Rackspace, the details about the flaw and the utility remain unknown.In The Current Issue:Interview: Niall Robinson, head of product innovation, Met OfficeIAM: Enterprises face a long, hard road to improveDownload Current IssueHow enterprises can improve ROI on AI investments Data MattersHow To "Vawlt" Superclouds Networks GenerationView All Blogs0 Comments 0 Shares 150 Views -
 WWW.ZDNET.COMGet 3 months of Xbox Game Pass Ultimate for 28% off right nowTry or gift Xbox Game Pass for three months for nearly one-third off and play over 100 games including Starfield, Forza Motorsport, and Football Manager 2024 on your Xbox, PC, or mobile device.0 Comments 0 Shares 122 Views
WWW.ZDNET.COMGet 3 months of Xbox Game Pass Ultimate for 28% off right nowTry or gift Xbox Game Pass for three months for nearly one-third off and play over 100 games including Starfield, Forza Motorsport, and Football Manager 2024 on your Xbox, PC, or mobile device.0 Comments 0 Shares 122 Views -
 WWW.ZDNET.COMGrab a Microsoft Office 2019 license for Mac or Windows for $27This deal gets you a lifetime license to Microsoft Office 2019 for Windows or Mac and access to Microsoft Word, Excel, PowerPoint, and more for 88% off.0 Comments 0 Shares 119 Views
WWW.ZDNET.COMGrab a Microsoft Office 2019 license for Mac or Windows for $27This deal gets you a lifetime license to Microsoft Office 2019 for Windows or Mac and access to Microsoft Word, Excel, PowerPoint, and more for 88% off.0 Comments 0 Shares 119 Views -
 WWW.FORBES.COMMainframes: The Backbone Of The Worldwide EconomyMainframes continue to be the backbone of the global economygettyMainframe computers are often perceived as relics of the past but in reality, they continue to be the backbone of the global economy. Critical data related to finance, government, and other sensitive transactions pass through these systems daily. Over 70 percent of Fortune 500 companies still rely on mainframes despite the rise of cloud computing. The key to their continued relevance is modernizationadapting these powerful systems to meet the needs and opportunities of todays technological landscape without losing the stability and security they provide.Why Mainframes Still MatterPeter Rutten is Research Vice President at International Data CorporationIDCMainframes have been around for over 60 years and remain the most reliable platform for handling massive amounts of data and transactions. As Peter Rutten, Research Vice President at IDC, explained, Mainframes were built for the highest possible performance and uptime, with the greatest security. In fact, theyre still used by industries like banking, airlines, and healthcare, where data integrity and continuous uptime are mission critical.These industries process billions of transactions daily, for which downtime is not an option.CEO of Rocket Software Milan Shetti echoes this sentiment, emphasizing that mainframes are "the backbone of the world economy because of their three major capabilities: security, governance, and very high performance." They are trusted for sensitive transactions such as wire transfers and insurance claims due to the degree of security and reliability that few other systems can match. The lack of headlines about mainframe failures or security breaches is a testament to their robustness, something Shetti proudly notes: Mainframe has done a really good job of staying out of the headlines for the wrong reasons.Yet, while mainframes are still trusted for mission-critical tasks, there is no denying the growing pressure to adapt to emerging technologies, such as cloud computing and artificial intelligence. This is where mainframe modernization comes into play.MORE FOR YOUThe Need for ModernizationMax de Groen, Partner at Bain CapitalJennifer Cimino PhotographyModernization is not about replacing mainframes but enhancing them to work seamlessly with modern technologies like cloud and AI. Max de Groen, Partner at Bain Capital, says, mainframe modernization is increasingly seen not as a necessary evil, but as an opportunity to leverage existing investments and integrate emerging technologies. Indeed, many enterprises are recognizing that modernization is essential to stay competitive, meet consumer demands, and manage costs effectively.The process, however, is not simple. A basic mainframe modernization project can take two years, while more complex ones can take five or more, explains Rutten. This timeline highlights the difficulty of integrating decades-old systems with newer, more flexible cloud environments.Shetti emphasizes that the goal is "modernization without disruption." Rocket Software, for instance, focuses on helping organizations modernize in placeupgrading their existing mainframe systems to work with new technologies without the need for a complete overhaul. He cites the example of a banks mobile application, which might be cloud-based but will still rely on the mainframe to access secure customer data.CEO of Rocket Software Milan ShettiRocket SoftwareThis hybrid approachconnecting the cloud to the mainframeis becoming the preferred method for many enterprises. "Youll never see end-to-end banking in the cloud," Shetti insists, explaining that cloud computing may be better for scaling applications and attracting developers, but the mainframe is preferred when handling sensitive data with the highest levels of security.The Role of AI in ModernizationAI is playing an increasingly important role in mainframe modernization. Rocket Software and other companies are using AI for "code explainability, which helps current engineers understand and modernize the vast amounts of legacy code that power mainframes today. This is crucial because many original developers who wrote this code have retired, leaving a knowledge gap that AI can help bridge.Shetti also envisions AI simplifying mainframe operations to the point where managing a mainframe could be as intuitive as operating an iPhone. This use of AI improves operational efficiency and helps attract new talent to an industry that has long been associated with complex, outdated technology.The Economic and Security ImpactsMainframe modernization has broader implications for the economy and security. Rutten points out that "70% of enterprise data still runs on mainframes," meaning that any failure or breach would have far-reaching consequences. This is why modernization is so criticalit allows enterprises to take advantage of cloud scalability and AI innovation while maintaining the security and reliability of their core systems.Moreover, de Groen highlights that modernization is about more than just keeping the lights on. Its about leveraging the power of datadata that resides on the mainframeto drive new business models, improve customer experiences, and stay competitive in a rapidly changing digital landscape.Mainframes may not be flashy, but they are indispensable. As Rutten wisely states, You dont move off the mainframe; you integrate with it. The future of enterprise IT lies in this integrationblending the unmatched security and reliability of mainframes with the flexibility and innovation of cloud computing and AI. For organizations that rely on these systems, modernization is not just an option; its necessary to remain competitive and secure in the digital age.Follow me on LinkedIn or check out my other columns here.0 Comments 0 Shares 117 Views
WWW.FORBES.COMMainframes: The Backbone Of The Worldwide EconomyMainframes continue to be the backbone of the global economygettyMainframe computers are often perceived as relics of the past but in reality, they continue to be the backbone of the global economy. Critical data related to finance, government, and other sensitive transactions pass through these systems daily. Over 70 percent of Fortune 500 companies still rely on mainframes despite the rise of cloud computing. The key to their continued relevance is modernizationadapting these powerful systems to meet the needs and opportunities of todays technological landscape without losing the stability and security they provide.Why Mainframes Still MatterPeter Rutten is Research Vice President at International Data CorporationIDCMainframes have been around for over 60 years and remain the most reliable platform for handling massive amounts of data and transactions. As Peter Rutten, Research Vice President at IDC, explained, Mainframes were built for the highest possible performance and uptime, with the greatest security. In fact, theyre still used by industries like banking, airlines, and healthcare, where data integrity and continuous uptime are mission critical.These industries process billions of transactions daily, for which downtime is not an option.CEO of Rocket Software Milan Shetti echoes this sentiment, emphasizing that mainframes are "the backbone of the world economy because of their three major capabilities: security, governance, and very high performance." They are trusted for sensitive transactions such as wire transfers and insurance claims due to the degree of security and reliability that few other systems can match. The lack of headlines about mainframe failures or security breaches is a testament to their robustness, something Shetti proudly notes: Mainframe has done a really good job of staying out of the headlines for the wrong reasons.Yet, while mainframes are still trusted for mission-critical tasks, there is no denying the growing pressure to adapt to emerging technologies, such as cloud computing and artificial intelligence. This is where mainframe modernization comes into play.MORE FOR YOUThe Need for ModernizationMax de Groen, Partner at Bain CapitalJennifer Cimino PhotographyModernization is not about replacing mainframes but enhancing them to work seamlessly with modern technologies like cloud and AI. Max de Groen, Partner at Bain Capital, says, mainframe modernization is increasingly seen not as a necessary evil, but as an opportunity to leverage existing investments and integrate emerging technologies. Indeed, many enterprises are recognizing that modernization is essential to stay competitive, meet consumer demands, and manage costs effectively.The process, however, is not simple. A basic mainframe modernization project can take two years, while more complex ones can take five or more, explains Rutten. This timeline highlights the difficulty of integrating decades-old systems with newer, more flexible cloud environments.Shetti emphasizes that the goal is "modernization without disruption." Rocket Software, for instance, focuses on helping organizations modernize in placeupgrading their existing mainframe systems to work with new technologies without the need for a complete overhaul. He cites the example of a banks mobile application, which might be cloud-based but will still rely on the mainframe to access secure customer data.CEO of Rocket Software Milan ShettiRocket SoftwareThis hybrid approachconnecting the cloud to the mainframeis becoming the preferred method for many enterprises. "Youll never see end-to-end banking in the cloud," Shetti insists, explaining that cloud computing may be better for scaling applications and attracting developers, but the mainframe is preferred when handling sensitive data with the highest levels of security.The Role of AI in ModernizationAI is playing an increasingly important role in mainframe modernization. Rocket Software and other companies are using AI for "code explainability, which helps current engineers understand and modernize the vast amounts of legacy code that power mainframes today. This is crucial because many original developers who wrote this code have retired, leaving a knowledge gap that AI can help bridge.Shetti also envisions AI simplifying mainframe operations to the point where managing a mainframe could be as intuitive as operating an iPhone. This use of AI improves operational efficiency and helps attract new talent to an industry that has long been associated with complex, outdated technology.The Economic and Security ImpactsMainframe modernization has broader implications for the economy and security. Rutten points out that "70% of enterprise data still runs on mainframes," meaning that any failure or breach would have far-reaching consequences. This is why modernization is so criticalit allows enterprises to take advantage of cloud scalability and AI innovation while maintaining the security and reliability of their core systems.Moreover, de Groen highlights that modernization is about more than just keeping the lights on. Its about leveraging the power of datadata that resides on the mainframeto drive new business models, improve customer experiences, and stay competitive in a rapidly changing digital landscape.Mainframes may not be flashy, but they are indispensable. As Rutten wisely states, You dont move off the mainframe; you integrate with it. The future of enterprise IT lies in this integrationblending the unmatched security and reliability of mainframes with the flexibility and innovation of cloud computing and AI. For organizations that rely on these systems, modernization is not just an option; its necessary to remain competitive and secure in the digital age.Follow me on LinkedIn or check out my other columns here.0 Comments 0 Shares 117 Views


