0 Comentários
0 Compartilhamentos

Diretório
Diretório
-
Faça Login para curtir, compartilhar e comentar!
-
 LIFEHACKER.COMFive Examples of Trash That You Can Sell for Decent MoneyMany of us could use more money, and we go about finding it in a variety of ways: asking for a raise, changing jobs, or taking a second job, for example. But you could also start selling trash. Not just any trash, of coursemost trash is, well, just trashbut the kinds of things people routinely throw away or leave behind that actually keep enough value to make them worth picking up and reselling them. While these are usually volume businesses (meaning you have to sell a large number of them to make real money), you can make real money just grabbing this stuff from trash, homes, or even public spaces. Six examples of surprisingly profitable trash are golf balls, wood pallets, cardboard boxes, wine corks, and egg cartons.Lost golf balls can be worth up to $2 eachMore than 25 million people play golf in the United States, and if youve ever played a round, you know that means a lot of lost golf balls. Approximately 1.5 billion golf balls go missing every year in this country. The surprising part is that used golf balls actually retain a lot of their value. According to Lashan Wanigatunga, co-owner of Two Guys with Balls, used golf balls can go for anywhere from 15 cents to $2 depending on brand, so you can make a fair amount of money just picking up golf balls you find on the ground.The real money is in diving for golf balls, as water hazards often contain a large volume of them that no one is going to chase after. This is such a real thing theres even a listing on the Bureau of Labor Statistics website for the career, where its noted that divers can make $200 per day retrieving golf balls (Todd Hutchinson of Ballhawker claims you can actually make $800 per day doing it). Diving for golf balls can be dangerous if youre not familiar with underwater work or skip safety protocols, but where else can you make a few hundred bucks a day by picking up stuff someone else left behind?Discarded wood pallets can be worth up to $4 eachWood pallets are pretty ubiquitousand pretty useful. If youve noticed a business in your area that routinely has a bunch of pallets piled up or in dumpsters, you might have an opportunity: Used wood pallets in decent condition are actually worth anywhere from 50 cents to $4 per pallet. All you need are pallets that you can legally take (many businesses are happy to get rid of them if you just ask), a way to transport them, and possibly some tools to repair pallets if you want to maximize your success. You can use the North American Pallet Recycling Network to locate pallet brokers in your area, and companies like Kamps Pallets will actually pay you and come and get your pallets if you have at least 500 per year to sell them. There are usually local pallet brokers in your area, so a little research might lead you to other resources.Used cardboard boxes can be worth $1.25 eachThose Amazon and UPS boxes we toss into the recycling bin or give to friends when theyre moving can actually be worth some money. You can sell empty, used cardboard boxes on platforms like BoxCycle, which pays anywhere from 10 cents to $1.25 for standard moving boxes and buys just about any box you might have on hand; U-Haul Box Exchange, where people post boxes for sale or for free; and Used Cardboard Boxes will buy your used shipping boxes. You can also try to sell used boxes eBay.Wine corks can be worth about 10 cents eachPeople in the U.S. tear through more than 4 billion bottles of wine each year, many of which wind up in recycling bins, but wine corks can actually sell for a pretty decent margin on places like Etsy or eBay. They tend to sell for about 10 cents a pop, although some branded varieties can fetch more. Of course, that's not a lot for someone relying on the average Americans consumption of 16 bottles per year for inventory, but if a local restaurant is just tossing their used corks into the bin, you might be in business.Egg cartons can sell for 30-40 cents eachUsed egg cartons are a surprisingly large market: People use them in crafts, and small farms also buy them for their own egg sales. Your standard supermarket-derived egg cartons can go for about 30-40 cents apiece on sites like eBay, which means that if you eat the average number of eggs each year (around 285, or close to 24 dozen), thats an extra $60-70 alone. If you actually go out and collect 24 egg cartons from local restaurants, hotels, or other businesses every day, thats a few hundred bucks a week.0 Comentários 0 Compartilhamentos
LIFEHACKER.COMFive Examples of Trash That You Can Sell for Decent MoneyMany of us could use more money, and we go about finding it in a variety of ways: asking for a raise, changing jobs, or taking a second job, for example. But you could also start selling trash. Not just any trash, of coursemost trash is, well, just trashbut the kinds of things people routinely throw away or leave behind that actually keep enough value to make them worth picking up and reselling them. While these are usually volume businesses (meaning you have to sell a large number of them to make real money), you can make real money just grabbing this stuff from trash, homes, or even public spaces. Six examples of surprisingly profitable trash are golf balls, wood pallets, cardboard boxes, wine corks, and egg cartons.Lost golf balls can be worth up to $2 eachMore than 25 million people play golf in the United States, and if youve ever played a round, you know that means a lot of lost golf balls. Approximately 1.5 billion golf balls go missing every year in this country. The surprising part is that used golf balls actually retain a lot of their value. According to Lashan Wanigatunga, co-owner of Two Guys with Balls, used golf balls can go for anywhere from 15 cents to $2 depending on brand, so you can make a fair amount of money just picking up golf balls you find on the ground.The real money is in diving for golf balls, as water hazards often contain a large volume of them that no one is going to chase after. This is such a real thing theres even a listing on the Bureau of Labor Statistics website for the career, where its noted that divers can make $200 per day retrieving golf balls (Todd Hutchinson of Ballhawker claims you can actually make $800 per day doing it). Diving for golf balls can be dangerous if youre not familiar with underwater work or skip safety protocols, but where else can you make a few hundred bucks a day by picking up stuff someone else left behind?Discarded wood pallets can be worth up to $4 eachWood pallets are pretty ubiquitousand pretty useful. If youve noticed a business in your area that routinely has a bunch of pallets piled up or in dumpsters, you might have an opportunity: Used wood pallets in decent condition are actually worth anywhere from 50 cents to $4 per pallet. All you need are pallets that you can legally take (many businesses are happy to get rid of them if you just ask), a way to transport them, and possibly some tools to repair pallets if you want to maximize your success. You can use the North American Pallet Recycling Network to locate pallet brokers in your area, and companies like Kamps Pallets will actually pay you and come and get your pallets if you have at least 500 per year to sell them. There are usually local pallet brokers in your area, so a little research might lead you to other resources.Used cardboard boxes can be worth $1.25 eachThose Amazon and UPS boxes we toss into the recycling bin or give to friends when theyre moving can actually be worth some money. You can sell empty, used cardboard boxes on platforms like BoxCycle, which pays anywhere from 10 cents to $1.25 for standard moving boxes and buys just about any box you might have on hand; U-Haul Box Exchange, where people post boxes for sale or for free; and Used Cardboard Boxes will buy your used shipping boxes. You can also try to sell used boxes eBay.Wine corks can be worth about 10 cents eachPeople in the U.S. tear through more than 4 billion bottles of wine each year, many of which wind up in recycling bins, but wine corks can actually sell for a pretty decent margin on places like Etsy or eBay. They tend to sell for about 10 cents a pop, although some branded varieties can fetch more. Of course, that's not a lot for someone relying on the average Americans consumption of 16 bottles per year for inventory, but if a local restaurant is just tossing their used corks into the bin, you might be in business.Egg cartons can sell for 30-40 cents eachUsed egg cartons are a surprisingly large market: People use them in crafts, and small farms also buy them for their own egg sales. Your standard supermarket-derived egg cartons can go for about 30-40 cents apiece on sites like eBay, which means that if you eat the average number of eggs each year (around 285, or close to 24 dozen), thats an extra $60-70 alone. If you actually go out and collect 24 egg cartons from local restaurants, hotels, or other businesses every day, thats a few hundred bucks a week.0 Comentários 0 Compartilhamentos -
LIFEHACKER.COMThe Dreo Baristamaker Is My Favorite Frother for Professional-Grade Foamed MilkWe may earn a commission from links on this page.One of the reasons lattes from a coffee shop are so special is that perfectly creamy foamed milk swirl. The foam is essential, the latte art is a bonusthough I love admiring a coffee-striped heart before I sip it away. You may have tried duplicating these fancy drinks at home, only to fall short with clumsy steaming wands and battery-powered frothing sticks. I certainly have. It might seem like time to give up on homemade microfoam, but hang in there a second longer. Theres one device that can actually do it for the at-home latte novice (and it is significantly easier than using a steam wand): The Dreo BaristaMaker. I've been testing one for nearly six months, and it's been a foaming wonder. Dreo BaristaMaker Milk Frother, All-in-1, 27oz/800ml Hot/Cold Electric Foam Maker for Coffee, Latte Art-level Microfoam, Automatic Milk Warmer, Dairy/Plant-Based Milk, 30+ Drinks, Dishwasher Safe $99.99 at Amazon Shop Now Shop Now $99.99 at Amazon What does it do?The Dreo BaristaMaker is an appliance specifically designed to make professional barista-grade foamed milk at home. Not just foamy milk with big bubbles that pop and fizzle-out after sitting for five minutes, but serious microfoam. This kind of foam has extra fine bubbles that hold their composition for as long as your drink lasts. Theyre so small and compact that theyre barely visible; only detectable by that overall creamy appearance we associate with latte foam. You can see in the picture that the foam isnt bubbly as much as it is dense and fluffy. (Note that this appliance does not make the coffee thoughyoure in charge of that.) I'm no good at latte art, but foam I can do with the BaristaMaker. Credit: Allie Chanthorn Reinmann The BaristaMaker is a two-part appliance. The heavy base is where the engine and the digital control panel live. The stainless steel container sits right on top, and thats where you insert the agitation attachment (a little propeller or a circular mesh screen), and pour the milk in. Simply make your selections on the digital screen and press start.Whats special about the Dreo BaristaMaker?What makes this appliance stand out from the rest is that it addresses two issues Ive noticed with other milk frothing devices: frothing alternative milks, and temperature control.Ive tried frothing oat and almond milk with steam wands, only to find out afterward that the temperature was so hot it denatured the proteins in the milk, leaving it watery. I then turned to the milk frothing stick. You know, the long metal stick with a spiral wire at the end that vibrates your milk? That one. Those work on the same premise of hand whisking heavy cream to make whipped cream. The agitation causes the proteins to link up and capture air bubbles, but on a lighter level. This works decently. But the bubbles are usually big and weak, and the milk is cold unless youve preheated it, which is risky (re: denaturing proteins again). Id rather just pour cold milk into my espresso. Credit: Allie Chanthorn Reinmann The BaristaMaker froths them all. The machine allows you to select the milk youre usingregular cow milk, half and half, oat, coconut, almond, or soyand heats up that particular milk slowly and to the correct temperature to best achieve a sturdy and elegant microfoam. Not only do those presets work like a dream for milks, but you can also go rogue and choose your own temperature if you need something else stirred, warmed, and foamed, like hot cocoa or a chai latte.Pros and consI am committed to this machine based on the milk options and temperature control alone. But there are other benefits too. This machine is good enough at making microfoam where you could actually become a latte art specialist. It has a latte art marker on the inside of the container so you can add enough milk. It has a sharp, pointed pour spout for precision pouring and detail work as you draw. Credit: Allie Chanthorn Reinmann Additionally, this is one of the best machines Ive ever used for cold foam. Cold foam is notoriously difficult to make. Hot foam is made with steam wands at cafscombining heat, and violent bubbling from the wandbut cold foam is made purely from agitation. Shaking the milk or using a blender can lead to uneven foam and big, clunky bubbles. Once again, the Dreo BaristaMaker excels. Its as easy to do as any of the other settingssimply pop in the mesh screen attachment, pour in the cold milk, and press start. The cold foam is luxurious, consistent, and creamythe perfect adornment for your cold brew in spring.The cons for this machine are few. Overall, the machine is a bit large compared to a thin milk foamer stick or a steam wand that might be already attached to your espresso machine. At 5.31-inches wide by 9.65-inches high, its the size of a personal blender. Secondly, my partner (who uses the BaristaMaker at least once a week) has had two instances when the foam was lackluster. Meaning, it just didnt get very foamy. He never gives up though, so after a few more tries, the Dreo always came back to full strength. What that means for longevity, Im not sure yet. Weve used it since the summer, and its still frothing away after about six months.Is it worth the money?If you (or as a gift for someone you love) are a total latte-head, flat white champion, cappuccino stan, or a weirdo who eats the scoopable foam from the top first (its me), you will absolutely fall in love with this machine. It is effective, fast, quiet (which is a blessing, especially compared to most kitchen appliances), and significantly better than any other milk frother Ive tried. Even if you prefer a weekly matcha latte, hot cocoa, or warm homemade pumpkin spice latte, this appliance will be well worth it.However, if you think of the BaristaMaker as more of a party trick, or your home has no cupboard space for yet another appliance, then maybe your $99.99 is better spent elsewhere. Plus, if you want to learn latte art, this frother is a great tool to have. You should know though, you have to provide the pouring skills yourself.0 Comentários 0 Compartilhamentos
-
 WWW.TECHRADAR.COMElon Musks xAI supercomputer gets 150MW power boost despite concerns over grid impact and local power stabilityxAI gains 150MW power approval for its supercomputer, but locals fear impact on grid and future power availability.0 Comentários 0 Compartilhamentos
WWW.TECHRADAR.COMElon Musks xAI supercomputer gets 150MW power boost despite concerns over grid impact and local power stabilityxAI gains 150MW power approval for its supercomputer, but locals fear impact on grid and future power availability.0 Comentários 0 Compartilhamentos -
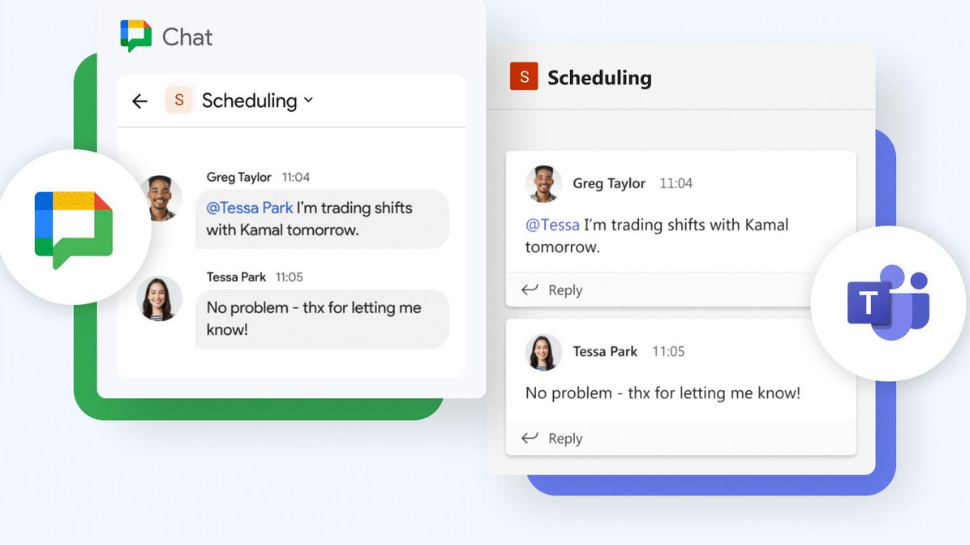 WWW.TECHRADAR.COMGoogle Chat is making it easy for you to ditch Microsoft TeamsGoogle is making it even easier for you to ditch Microsoft Teams with its chat migration service.0 Comentários 0 Compartilhamentos
WWW.TECHRADAR.COMGoogle Chat is making it easy for you to ditch Microsoft TeamsGoogle is making it even easier for you to ditch Microsoft Teams with its chat migration service.0 Comentários 0 Compartilhamentos -
 WWW.TECHRADAR.COMGoogle CEO reveals major job cuts as part of "efficiency" moveAfter months of layoffs, Google is now slimming down its manager, director and VP headcount by 10%.0 Comentários 0 Compartilhamentos
WWW.TECHRADAR.COMGoogle CEO reveals major job cuts as part of "efficiency" moveAfter months of layoffs, Google is now slimming down its manager, director and VP headcount by 10%.0 Comentários 0 Compartilhamentos -
 WWW.FASTCOMPANY.COMSouthern farmers are still reeling months after Hurricane HeleneTwisted equipment and snapped tree limbs still litter Chris Hopkins Georgia farm more than two months after Hurricane Helene made its deadly march across the South.An irrigation sprinkler system about 300 feet (92 meters) long lay overturned in a field, its steel pipes bent and welded joints broken. The mangled remains of a grain bin sat crumpled by a road. On a Friday in early December, Hopkins dragged burly limbs from the path of the tractor-like machine that picks his cotton crop six rows at a time.I have wrestled with lots of emotions the past two months, said Hopkins, who also grows corn and peanuts in rural Toombs County, about 75 miles (120 kilometers) west of Savannah. Do we just get through this one and quit? Do we build back? It is emotionally draining.Hopkins is among farmers across the South who are still reeling from Helenes devastation. The storm made landfall in Florida on Sept. 26 as a major Category 4 storm and then raced north across Georgia and neighboring states.Experts estimate the cost to farmers, timber growers and other agribusinesses from Florida to Virginia will reach more than $10 billion. The toll includes ravaged crops, uprooted timber, wrecked farm equipment and mangled chicken houses, as well as indirect costs such as lost productivity at cotton gins and poultry processing plants.For cotton growers like Hopkins, Helene hit just as the fall harvest was starting. Many put most cleanup on hold to try to salvage what remained of their crops.Staggering losses to cotton, pecans and fall vegetablesGeorgia farmers suffered storm losses of at least $5.5 billion, according to an analysis by the University of Georgia. In North Carolina, a state agency calculated farmers suffered $3.1 billion in crop losses and recovery costs after Helene brought record rainfall and flooding. Separate economic analyses of farm damage tallied losses of up to $630 million in Virginia, $452 million in South Carolina and $162 million in Florida.Hopkins figures he lost half the cotton on his 1,400 acres (560 hectares).We were at the most vulnerable stage we could be, he said. The lint was open and fluffy and hanging there, waiting to be defoliated or picked. About 50% of the harvestable lint ended up on the ground.Even with insurance, Hopkins said, he wont recoup an estimated $430,000 in losses from his cotton crop alone. That doesnt include the cost of debris removal, repairing or replacing damaged machinery and the loss of two small pecan orchards uprooted by the storm.The storm ripped through blooming cotton fields, pecan orchards laden with nuts and fields where fall vegetables like cucumbers and squash awaited picking. Hundreds of large poultry houses used to raise thousands of chickens at a time got destroyed.Farmers far from Helenes center werent spared, as tropical-storm force winds reached outward up to 310 miles (499 kilometers).It was staggering, said Timothy Coolong, a University of Georgia horticulture professor. This may be just too much for some folks.Helene was one of the deadliest U.S. hurricanes in nearly two decades, killing more than 200 people. It left more than 100,000 homes damaged or destroyed across the South.Will aid to farmers come soon enough?Georgia farmers suffered storm losses of at least$5.5 billion, according to an analysis by the University of Georgia. In North Carolina, a state agency calculated farmers suffered $3.1 billion in crop losses and recovery costs after Helene broughtrecord rainfall and flooding. Separate economic analyses of farm damage tallied losses of up to $630 million in Virginia, $452 million in South Carolina and $162 million in Florida.But Georgias constitution prohibits using state funds to give direct disaster aid to individuals and private businesses.In Congress, a spending bill passed early Saturday to avoid a government shutdown included $21 billion in disaster aid to U.S. farmers.We need help, but we need it quick, said Jeffrey Pridgen, a fifth-generation farmer who raises chickens in south Georgias Coffee County.Pridgen operated a dozen poultry houses, each large enough to raise up to 20,000 chickens at a time. Helene destroyed four of them, along with thousands of chickens. Only one of Pridgens houses remains in working condition, the others having been badly damaged.Pridgen said new chicken houses will cost about $450,000 apiece. Because most of his were decades old, he expects insurance to cover just half the cost.I was looking at retirement, but I lost my retirement and my income in one day, said Pridgen, 62. Itll be two years before we get fully operational again. Im basically starting over.Everybody lost somethingGeorgias poultry industry took an estimated $683 million hit, with farmers having to rebuild about 300 chicken houses and repair hundreds more.The poultry processing plant that relies on Pridgen and other storm-impacted farmers for chickens is now operating just four days per week, he said.Now for at least a year, perhaps a little bit longer, were in rebuilding mode, said Mike Giles, president of the Georgia Poultry Federation. That affects production in an area for an extended period of time.Helenes devastation shouldnt have much impact on consumer prices because crops grown elsewhere can make up for most shortages, said Michael Adjemian, a University of Georgia professor of agricultural economics. Pecans are one possible exception. Georgia is responsible for roughly one-third of U.S. production.In most cases, even a terrible storm like this is going to have a relatively small impact, Adjemian said. And maybe its not even noticeable, depending on the product.Helene cost Georgia cotton farmers roughly one-third of their crop, with direct and indirect losses valued at $560 million. Some were still recovering from Hurricane Michael in 2018.Cotton growers also were facing low prices this harvest season of around 70 cents per pound (per 0.45 kilograms), said Taylor Sills, executive director of the Georgia Cotton Commission. That meant they needed a big yield to turn any profit.Times were awful, and then they got hit by a hurricane, Sills said. There are people who lost everything and there are people who didnt. But everybody lost something.Russ Bynum, Associated Press0 Comentários 0 Compartilhamentos
WWW.FASTCOMPANY.COMSouthern farmers are still reeling months after Hurricane HeleneTwisted equipment and snapped tree limbs still litter Chris Hopkins Georgia farm more than two months after Hurricane Helene made its deadly march across the South.An irrigation sprinkler system about 300 feet (92 meters) long lay overturned in a field, its steel pipes bent and welded joints broken. The mangled remains of a grain bin sat crumpled by a road. On a Friday in early December, Hopkins dragged burly limbs from the path of the tractor-like machine that picks his cotton crop six rows at a time.I have wrestled with lots of emotions the past two months, said Hopkins, who also grows corn and peanuts in rural Toombs County, about 75 miles (120 kilometers) west of Savannah. Do we just get through this one and quit? Do we build back? It is emotionally draining.Hopkins is among farmers across the South who are still reeling from Helenes devastation. The storm made landfall in Florida on Sept. 26 as a major Category 4 storm and then raced north across Georgia and neighboring states.Experts estimate the cost to farmers, timber growers and other agribusinesses from Florida to Virginia will reach more than $10 billion. The toll includes ravaged crops, uprooted timber, wrecked farm equipment and mangled chicken houses, as well as indirect costs such as lost productivity at cotton gins and poultry processing plants.For cotton growers like Hopkins, Helene hit just as the fall harvest was starting. Many put most cleanup on hold to try to salvage what remained of their crops.Staggering losses to cotton, pecans and fall vegetablesGeorgia farmers suffered storm losses of at least $5.5 billion, according to an analysis by the University of Georgia. In North Carolina, a state agency calculated farmers suffered $3.1 billion in crop losses and recovery costs after Helene brought record rainfall and flooding. Separate economic analyses of farm damage tallied losses of up to $630 million in Virginia, $452 million in South Carolina and $162 million in Florida.Hopkins figures he lost half the cotton on his 1,400 acres (560 hectares).We were at the most vulnerable stage we could be, he said. The lint was open and fluffy and hanging there, waiting to be defoliated or picked. About 50% of the harvestable lint ended up on the ground.Even with insurance, Hopkins said, he wont recoup an estimated $430,000 in losses from his cotton crop alone. That doesnt include the cost of debris removal, repairing or replacing damaged machinery and the loss of two small pecan orchards uprooted by the storm.The storm ripped through blooming cotton fields, pecan orchards laden with nuts and fields where fall vegetables like cucumbers and squash awaited picking. Hundreds of large poultry houses used to raise thousands of chickens at a time got destroyed.Farmers far from Helenes center werent spared, as tropical-storm force winds reached outward up to 310 miles (499 kilometers).It was staggering, said Timothy Coolong, a University of Georgia horticulture professor. This may be just too much for some folks.Helene was one of the deadliest U.S. hurricanes in nearly two decades, killing more than 200 people. It left more than 100,000 homes damaged or destroyed across the South.Will aid to farmers come soon enough?Georgia farmers suffered storm losses of at least$5.5 billion, according to an analysis by the University of Georgia. In North Carolina, a state agency calculated farmers suffered $3.1 billion in crop losses and recovery costs after Helene broughtrecord rainfall and flooding. Separate economic analyses of farm damage tallied losses of up to $630 million in Virginia, $452 million in South Carolina and $162 million in Florida.But Georgias constitution prohibits using state funds to give direct disaster aid to individuals and private businesses.In Congress, a spending bill passed early Saturday to avoid a government shutdown included $21 billion in disaster aid to U.S. farmers.We need help, but we need it quick, said Jeffrey Pridgen, a fifth-generation farmer who raises chickens in south Georgias Coffee County.Pridgen operated a dozen poultry houses, each large enough to raise up to 20,000 chickens at a time. Helene destroyed four of them, along with thousands of chickens. Only one of Pridgens houses remains in working condition, the others having been badly damaged.Pridgen said new chicken houses will cost about $450,000 apiece. Because most of his were decades old, he expects insurance to cover just half the cost.I was looking at retirement, but I lost my retirement and my income in one day, said Pridgen, 62. Itll be two years before we get fully operational again. Im basically starting over.Everybody lost somethingGeorgias poultry industry took an estimated $683 million hit, with farmers having to rebuild about 300 chicken houses and repair hundreds more.The poultry processing plant that relies on Pridgen and other storm-impacted farmers for chickens is now operating just four days per week, he said.Now for at least a year, perhaps a little bit longer, were in rebuilding mode, said Mike Giles, president of the Georgia Poultry Federation. That affects production in an area for an extended period of time.Helenes devastation shouldnt have much impact on consumer prices because crops grown elsewhere can make up for most shortages, said Michael Adjemian, a University of Georgia professor of agricultural economics. Pecans are one possible exception. Georgia is responsible for roughly one-third of U.S. production.In most cases, even a terrible storm like this is going to have a relatively small impact, Adjemian said. And maybe its not even noticeable, depending on the product.Helene cost Georgia cotton farmers roughly one-third of their crop, with direct and indirect losses valued at $560 million. Some were still recovering from Hurricane Michael in 2018.Cotton growers also were facing low prices this harvest season of around 70 cents per pound (per 0.45 kilograms), said Taylor Sills, executive director of the Georgia Cotton Commission. That meant they needed a big yield to turn any profit.Times were awful, and then they got hit by a hurricane, Sills said. There are people who lost everything and there are people who didnt. But everybody lost something.Russ Bynum, Associated Press0 Comentários 0 Compartilhamentos -
 WWW.FASTCOMPANY.COMBluesky users report AI bots, disinformation, and copycat accountsBluesky has seen its user base soar since the U.S. presidential election, boosted by people seeking refuge from Elon Musks X, which they view as increasingly leaning too far to the right given its owners support of President-elect Donald Trump, or wanting an alternative to Metas Threads and its algorithms.The platform grew out of the company then known as Twitter, championed by its former CEO Jack Dorsey. Its decentralized approach to social networking was eventually intended to replace Twitters core mechanic. Thats unlikely now that the two companies have parted ways. But Blueskys growth trajectory with a user base that has more than doubled since October could make it a serious competitor to other social platforms.But with growth comes growing pains. Its not just human users whove been flocking to Bluesky but also bots, including those designed to create partisan division or direct users to junk websites.The skyrocketing user base now surpassing 25 million is the biggest test yet for a relatively young platform that has branded itself as a social media alternative free of the problems plaguing its competitors. According to research firm Similarweb, Bluesky added 7.6 million monthly active app users on iOS and Android in November, an increase of 295.4% since October. It also saw 56.2 million desktop and mobile web visits, in the same period, up 189% from October.Besides the U.S. elections, Bluesky also got a boost when X was briefly banned in Brazil.They got this spike in attention, theyve crossed the threshold where it is now worth it for people to flood the platform with spam, said Laura Edelson, an assistant professor of computer science at Northeastern University and a member of Issue Ones Council for Responsible Social Media. But they dont have the cash flow, they dont have the established team that a larger platform would, so they have to do it all very, very quickly.To manage growth for its tiny staff, Bluesky started as an invitation-only space until it opened to the public in February. That period gave the site time to build out moderation tools and other distinctive features to attract new users, such as starter packs that provide lists of topically curated feeds. Meta recently announced that it is testing a similar feature.Compared to the bigger players like Metas platforms or X, Bluesky has a quite different value system, said Claire Wardle, a professor at Cornell University and an expert in misinformation. This includes giving users more control over their experience.The first generation of social media platforms connected the world, but ended up consolidating power in the hands of a few corporations and their leaders, Bluesky said on its blog in March. Our online experience doesnt have to depend on billionaires unilaterally making decisions over what we see. On an open social network like Bluesky, you can shape your experience for yourself.Because of this mindset, Bluesky has achieved a scrappy underdog status that has attracted users whove grown tired of the big players.People had this idea that it was going to be a different type of social network, Wardle said. But the truth is, when you get lots of people in a place and there are eyeballs, it means that its in other peoples interests to use bots to create, you know, information that aligns with their perspective.Little data has emerged to help quantify the rise in impersonator accounts, artificial intelligence-fueled networks and other potentially harmful content on Bluesky. But in recent weeks, users have begun reporting large numbers of apparent AI bots following them, posting plagiarized articles or making seemingly automated divisive comments in replies.Lion Cassens, a Bluesky user and doctoral candidate in the Netherlands, found one such network by accident a group of German-language accounts with similar bios and AI-generated profile pictures posting in replies to three German newspapers.I noticed some weird replies under a news post by the German newspaper Die Ziet,' he said in an email to The Associated Press. I have a lot of trust in the moderation mechanism on Bluesky, especially compared to Twitter since the layoffs and due to Musks more radical stance on freedom of speech. But AI bots are a big challenge, as they will only improve. I hope social media can keep up with that.Cassens said the bots messages have been relatively innocuous so far, but he was concerned about how they could be repurposed in the future to mislead.There are also signs that foreign disinformation narratives have made their way to Bluesky. The disinformation research group Alethea pointed to one low-traction post sharing a false claim about ABC News that had circulated on Russian Telegram channels.Copycat accounts are another challenge. In late November, Alexios Mantzarlis, director of the Security, Trust and Safety Initiative at Cornell Tech, found that of the top 100 most followed named individuals on Bluesky, 44% had at least one duplicate account posing as them. Two weeks later, Mantzarlis said Bluesky had removed around two-thirds of the duplicate accounts hed initially detected a sign the site was aware of the issue and attempting to address it.Bluesky posted earlier this month that it had quadrupled its moderation team to keep up with its growing user base. The company also announced it had introduced a new system to detect impersonation and was working to improve its Community Guidelines to provide more detail on whats allowed. Because of the way the site is built, users also have the option to subscribe to third-party Labelers that outsource content moderation by tagging accounts with warnings and context.The company didnt respond to multiple requests for comment for this story.Even as its challenges arent yet at the scale other platforms face, Bluesky is at a crossroads, said Edward Perez, a board member at the nonpartisan nonprofit OSET Institute, who previously led Twitters civic integrity team.Whether BlueSky likes it or not, it is being pulled into the real world, Perez said, noting that it needs to quickly prioritize threats and work to mitigate them if it hopes to continue to grow.That said, disinformation and bots wont be Blueskys only challenges in the months and years to come. As a text-based social network, its entire premise is falling out of favor with younger generations. A recent Pew Research Center poll found that only 17% of American teenagers used X, for instance, down from 23% in 2022. For teens and young adults, TikTok, Instagram and other visual-focused platforms are the places to be.Political polarization is also going against Bluesky ever reaching the size of TikTok, Instagram or even X.Bluesky is not trying to be all things to all people, Wardle said, adding that, likely, the days of a Facebook or Instagram emerging where theyre trying to keep everybody happy are over. Social platforms are increasingly splintered along political lines and when they arent see Metas platforms the companies behind them are actively working to de-emphasize political content and news.The Associated Press receives support from several private foundations to enhance its explanatory coverage of elections and democracy. See more about APs democracy initiative here. The AP is solely responsible for all content.Ali Swenson and Barara Ortutay, Associated Press0 Comentários 0 Compartilhamentos
WWW.FASTCOMPANY.COMBluesky users report AI bots, disinformation, and copycat accountsBluesky has seen its user base soar since the U.S. presidential election, boosted by people seeking refuge from Elon Musks X, which they view as increasingly leaning too far to the right given its owners support of President-elect Donald Trump, or wanting an alternative to Metas Threads and its algorithms.The platform grew out of the company then known as Twitter, championed by its former CEO Jack Dorsey. Its decentralized approach to social networking was eventually intended to replace Twitters core mechanic. Thats unlikely now that the two companies have parted ways. But Blueskys growth trajectory with a user base that has more than doubled since October could make it a serious competitor to other social platforms.But with growth comes growing pains. Its not just human users whove been flocking to Bluesky but also bots, including those designed to create partisan division or direct users to junk websites.The skyrocketing user base now surpassing 25 million is the biggest test yet for a relatively young platform that has branded itself as a social media alternative free of the problems plaguing its competitors. According to research firm Similarweb, Bluesky added 7.6 million monthly active app users on iOS and Android in November, an increase of 295.4% since October. It also saw 56.2 million desktop and mobile web visits, in the same period, up 189% from October.Besides the U.S. elections, Bluesky also got a boost when X was briefly banned in Brazil.They got this spike in attention, theyve crossed the threshold where it is now worth it for people to flood the platform with spam, said Laura Edelson, an assistant professor of computer science at Northeastern University and a member of Issue Ones Council for Responsible Social Media. But they dont have the cash flow, they dont have the established team that a larger platform would, so they have to do it all very, very quickly.To manage growth for its tiny staff, Bluesky started as an invitation-only space until it opened to the public in February. That period gave the site time to build out moderation tools and other distinctive features to attract new users, such as starter packs that provide lists of topically curated feeds. Meta recently announced that it is testing a similar feature.Compared to the bigger players like Metas platforms or X, Bluesky has a quite different value system, said Claire Wardle, a professor at Cornell University and an expert in misinformation. This includes giving users more control over their experience.The first generation of social media platforms connected the world, but ended up consolidating power in the hands of a few corporations and their leaders, Bluesky said on its blog in March. Our online experience doesnt have to depend on billionaires unilaterally making decisions over what we see. On an open social network like Bluesky, you can shape your experience for yourself.Because of this mindset, Bluesky has achieved a scrappy underdog status that has attracted users whove grown tired of the big players.People had this idea that it was going to be a different type of social network, Wardle said. But the truth is, when you get lots of people in a place and there are eyeballs, it means that its in other peoples interests to use bots to create, you know, information that aligns with their perspective.Little data has emerged to help quantify the rise in impersonator accounts, artificial intelligence-fueled networks and other potentially harmful content on Bluesky. But in recent weeks, users have begun reporting large numbers of apparent AI bots following them, posting plagiarized articles or making seemingly automated divisive comments in replies.Lion Cassens, a Bluesky user and doctoral candidate in the Netherlands, found one such network by accident a group of German-language accounts with similar bios and AI-generated profile pictures posting in replies to three German newspapers.I noticed some weird replies under a news post by the German newspaper Die Ziet,' he said in an email to The Associated Press. I have a lot of trust in the moderation mechanism on Bluesky, especially compared to Twitter since the layoffs and due to Musks more radical stance on freedom of speech. But AI bots are a big challenge, as they will only improve. I hope social media can keep up with that.Cassens said the bots messages have been relatively innocuous so far, but he was concerned about how they could be repurposed in the future to mislead.There are also signs that foreign disinformation narratives have made their way to Bluesky. The disinformation research group Alethea pointed to one low-traction post sharing a false claim about ABC News that had circulated on Russian Telegram channels.Copycat accounts are another challenge. In late November, Alexios Mantzarlis, director of the Security, Trust and Safety Initiative at Cornell Tech, found that of the top 100 most followed named individuals on Bluesky, 44% had at least one duplicate account posing as them. Two weeks later, Mantzarlis said Bluesky had removed around two-thirds of the duplicate accounts hed initially detected a sign the site was aware of the issue and attempting to address it.Bluesky posted earlier this month that it had quadrupled its moderation team to keep up with its growing user base. The company also announced it had introduced a new system to detect impersonation and was working to improve its Community Guidelines to provide more detail on whats allowed. Because of the way the site is built, users also have the option to subscribe to third-party Labelers that outsource content moderation by tagging accounts with warnings and context.The company didnt respond to multiple requests for comment for this story.Even as its challenges arent yet at the scale other platforms face, Bluesky is at a crossroads, said Edward Perez, a board member at the nonpartisan nonprofit OSET Institute, who previously led Twitters civic integrity team.Whether BlueSky likes it or not, it is being pulled into the real world, Perez said, noting that it needs to quickly prioritize threats and work to mitigate them if it hopes to continue to grow.That said, disinformation and bots wont be Blueskys only challenges in the months and years to come. As a text-based social network, its entire premise is falling out of favor with younger generations. A recent Pew Research Center poll found that only 17% of American teenagers used X, for instance, down from 23% in 2022. For teens and young adults, TikTok, Instagram and other visual-focused platforms are the places to be.Political polarization is also going against Bluesky ever reaching the size of TikTok, Instagram or even X.Bluesky is not trying to be all things to all people, Wardle said, adding that, likely, the days of a Facebook or Instagram emerging where theyre trying to keep everybody happy are over. Social platforms are increasingly splintered along political lines and when they arent see Metas platforms the companies behind them are actively working to de-emphasize political content and news.The Associated Press receives support from several private foundations to enhance its explanatory coverage of elections and democracy. See more about APs democracy initiative here. The AP is solely responsible for all content.Ali Swenson and Barara Ortutay, Associated Press0 Comentários 0 Compartilhamentos -
 WWW.FASTCOMPANY.COMSouth Side of Chicago gets funding for a transit project before Trump takeoverAdella Bass dropped her in-person college classes because it was just too hard to get there from the far South Side of Chicago, where the citys famous elevated train doesnt run. And it can take her nearly two hours to get to the hospital where she is treated for a heart condition.But things are looking up, with bright red signs across the area boldly proclaiming, Ready, Set, Soon! Next year, the city is poised to start making good on a decades-old promise to connect some of its most isolated, poor and polluted neighborhoods to the rest of the city through mass transit.The Biden administration notified Congress last week that it would commit $1.9 billion toward a nearly $5.7 billion project to add four new L stations on the South Side, the Chicago systems largest expansion project in history. The pledge, which the Federal Transit Administration is expected to formally sign before President Joe Biden leaves office in January, essentially locks in current and future funding.Still, Bass fears President-elect Donald Trumps administration might try to scuttle it.Signals abound to assure residents that the project is a go, said Bass, who is raising three young children and works on health equity issues that affect residents of a massive public housing development near her South Side home. But you just never know with Trump.Could Trump slash transit funding?The $1 trillion infrastructure plan Biden signed into law in 2021 focused far more heavily on transit than anything his predecessor advocated. That is why there has been a scramble to finalize some transit grants before Bidens term ends, including commitments last week for rapid transit upgrades in San Antonio and Salt Lake City.Yonah Freemark, a researcher at the Urban Institute, said Trump unsuccessfully encouraged Congress in his first term to pass budgets eliminating funding for some new transit projects that hadnt secured their grant agreements. But it has been practically unheard of for administrations to claw back projects after they won final approval.Steve Davis, who handles transportation strategy for Smart Growth America, said Trump could try to redirect future competitive grants to prioritize highway construction over alternative transportation methods such as transit. He said Trumps Transportation Department could potentially slow down some allocations from already approved infrastructure projects but would have trouble halting them entirely.If youre building an enormous $2 billion road widening, you need to know youre going to have money in year four or five and theres nothing a hostile administration could do to stop it, Davis said.Bringing back jobs through accessOne of the communities that would be served by a new Chicago L station is Roseland, a once-thriving, predominantly Black business district that has fallen victim to the loss of manufacturing and a spike in crime.Jervon Hicks, who spent many years in and out of jail on gun charges, turned his life around and ended up becoming a mentor for at-risk youth. The new station could help quicken the same transition for others, he said.Roseland needs a makeover, Hicks said. We lack a pet store. We used to have a theater. Take some of these abandoned buildings and turn them into job opportunities.Unlike the busy Magnificent Mile shopping district on Michigan Avenue in the downtown Chicago Loop, the business district on South Michigan Avenue in Roseland has fallen from more than 90% occupancy decades ago to around 10% now.Among the surviving businesses is Edwards Fashions. Owner Ledall Edwards hopes transportation will spur more to return.I dont think itll get to the level it was back in the 1970s, but I think the environment is going to improve because of the accessibility, he said. Youre going to be able to get people here in this area much faster.Rogers Jones, who for 30 years has run the Youth Peace Center next to the future train station, said he cant wait for the transformation.The community is going to change, Jones said. Its going to be a vibrant community, and people are excited. I know Im excited.A 55-year-old promiseFormer Chicago Mayor Richard J. Daley told residents of Roseland and surrounding areas in 1969 that the L would eventually expand there.Tammy Chase, a spokesperson for the Chicago Transit Authority, said the cost then would have been $114 million compared to around $5.7 billion now, a figure that would keep rising the longer construction is delayed.The agency has hired a construction firm, opened a Roseland office in a former paint store and begun boarding up homes that will be demolished for the tracks to run through. Ground is expected to be broken in late 2025, Chase said.U.S. Rep. Mike Quigley of Illinois, the top Democrat on the subcommittee that oversees transportation spending, points out Chicagos transit system survived wars and depression. It surely also can withstand a pandemic and a presidential administration with different priorities, he said.The big infrastructure projects stand the test of time, Quigley said. These ups and downs, you have to adjust to them, but you recognize transit always comes back. If transit doesnt come back, it stymies opportunities going forward.Jeff McMurray, Associated Press0 Comentários 0 Compartilhamentos
WWW.FASTCOMPANY.COMSouth Side of Chicago gets funding for a transit project before Trump takeoverAdella Bass dropped her in-person college classes because it was just too hard to get there from the far South Side of Chicago, where the citys famous elevated train doesnt run. And it can take her nearly two hours to get to the hospital where she is treated for a heart condition.But things are looking up, with bright red signs across the area boldly proclaiming, Ready, Set, Soon! Next year, the city is poised to start making good on a decades-old promise to connect some of its most isolated, poor and polluted neighborhoods to the rest of the city through mass transit.The Biden administration notified Congress last week that it would commit $1.9 billion toward a nearly $5.7 billion project to add four new L stations on the South Side, the Chicago systems largest expansion project in history. The pledge, which the Federal Transit Administration is expected to formally sign before President Joe Biden leaves office in January, essentially locks in current and future funding.Still, Bass fears President-elect Donald Trumps administration might try to scuttle it.Signals abound to assure residents that the project is a go, said Bass, who is raising three young children and works on health equity issues that affect residents of a massive public housing development near her South Side home. But you just never know with Trump.Could Trump slash transit funding?The $1 trillion infrastructure plan Biden signed into law in 2021 focused far more heavily on transit than anything his predecessor advocated. That is why there has been a scramble to finalize some transit grants before Bidens term ends, including commitments last week for rapid transit upgrades in San Antonio and Salt Lake City.Yonah Freemark, a researcher at the Urban Institute, said Trump unsuccessfully encouraged Congress in his first term to pass budgets eliminating funding for some new transit projects that hadnt secured their grant agreements. But it has been practically unheard of for administrations to claw back projects after they won final approval.Steve Davis, who handles transportation strategy for Smart Growth America, said Trump could try to redirect future competitive grants to prioritize highway construction over alternative transportation methods such as transit. He said Trumps Transportation Department could potentially slow down some allocations from already approved infrastructure projects but would have trouble halting them entirely.If youre building an enormous $2 billion road widening, you need to know youre going to have money in year four or five and theres nothing a hostile administration could do to stop it, Davis said.Bringing back jobs through accessOne of the communities that would be served by a new Chicago L station is Roseland, a once-thriving, predominantly Black business district that has fallen victim to the loss of manufacturing and a spike in crime.Jervon Hicks, who spent many years in and out of jail on gun charges, turned his life around and ended up becoming a mentor for at-risk youth. The new station could help quicken the same transition for others, he said.Roseland needs a makeover, Hicks said. We lack a pet store. We used to have a theater. Take some of these abandoned buildings and turn them into job opportunities.Unlike the busy Magnificent Mile shopping district on Michigan Avenue in the downtown Chicago Loop, the business district on South Michigan Avenue in Roseland has fallen from more than 90% occupancy decades ago to around 10% now.Among the surviving businesses is Edwards Fashions. Owner Ledall Edwards hopes transportation will spur more to return.I dont think itll get to the level it was back in the 1970s, but I think the environment is going to improve because of the accessibility, he said. Youre going to be able to get people here in this area much faster.Rogers Jones, who for 30 years has run the Youth Peace Center next to the future train station, said he cant wait for the transformation.The community is going to change, Jones said. Its going to be a vibrant community, and people are excited. I know Im excited.A 55-year-old promiseFormer Chicago Mayor Richard J. Daley told residents of Roseland and surrounding areas in 1969 that the L would eventually expand there.Tammy Chase, a spokesperson for the Chicago Transit Authority, said the cost then would have been $114 million compared to around $5.7 billion now, a figure that would keep rising the longer construction is delayed.The agency has hired a construction firm, opened a Roseland office in a former paint store and begun boarding up homes that will be demolished for the tracks to run through. Ground is expected to be broken in late 2025, Chase said.U.S. Rep. Mike Quigley of Illinois, the top Democrat on the subcommittee that oversees transportation spending, points out Chicagos transit system survived wars and depression. It surely also can withstand a pandemic and a presidential administration with different priorities, he said.The big infrastructure projects stand the test of time, Quigley said. These ups and downs, you have to adjust to them, but you recognize transit always comes back. If transit doesnt come back, it stymies opportunities going forward.Jeff McMurray, Associated Press0 Comentários 0 Compartilhamentos -
 WWW.YANKODESIGN.COMThis Apollo Moon Mission inspired calculator wristwatch is for every space enthusiastTheres something about watches and lunar elements that makes both an attractive combo. LUNAR1,622 and the LUNAR 1969 watches by Sebastien Colen, or the more contemporary Swatch x Omega Moonphase watch are a testament to the fact. Now theres yet another timepiece carrying a piece of history thatll pique the interest of astronomy and space lovers. The Apollo Instruments DSKY Moonwatch by British startup Apollo Instruments is a retro-futuristic wristwatch straight out of the Cyberpunk universe.This piece carrying the Apollo Missions revered history is a reminder of how all the advanced computing started with the Apollo Guidance Computer. The timepiece was the first ever device to have silicon microchips developed for the Moon Mission. Fast forward to current times and all our gadgets, automobiles, and everyday consumer electronics can attribute their existence to this iconic computing machine.Designer: Apollo InstrumentsNow after 55 years the computer that made possible Neil Armstrong and Buzz Aldrins first footsteps on the lunar surface, reincarnates in a working miniature form as a cool wristwatch. DSKY (Display and Keyboard) Moonwatch is a true remake of the briefcase-sized computing machine as the maker got the original design blueprints from MIT Instrumentation Laboratory. The 4:6:1 scaled recreation of the watch with digital display has a working GPS waypoint navigation system, a working keyboard, and can be programmed to include your custom modules if you are into Arduino or Python coding. Targeted towards the nerdy audience it even comes with a 8-channel digital I/O port to interact with robotic devices or breadboard interfaces.According to Mark Clayton, Apollo Instruments Fonder, Moving forward I would like to see Apollo Instruments become a focal point for space enthusiasts with authentic quality products that not only allow our customers to immerse themselves into the narrative of mankinds greatest journey but also offer an engaging experience that will inspire creativity and a continued thirst for knowledge. On the functionality front, the watch will get future updates, so that developers can come up with useful features and users can install them on the device right away. For now, it comes with functions including time/date, configurable time zones, calculator stopwatch, alarm, and V35 lights function.Apollo Instruments DSKY Moonwatch is a cool piece of technology that is a reminder of how tech advancements came to be, and how the lunar mission became a possibility. If you also want to be a part of this cool piece of history, the watch can be pre-ordered for $311.The post This Apollo Moon Mission inspired calculator wristwatch is for every space enthusiast first appeared on Yanko Design.0 Comentários 0 Compartilhamentos
WWW.YANKODESIGN.COMThis Apollo Moon Mission inspired calculator wristwatch is for every space enthusiastTheres something about watches and lunar elements that makes both an attractive combo. LUNAR1,622 and the LUNAR 1969 watches by Sebastien Colen, or the more contemporary Swatch x Omega Moonphase watch are a testament to the fact. Now theres yet another timepiece carrying a piece of history thatll pique the interest of astronomy and space lovers. The Apollo Instruments DSKY Moonwatch by British startup Apollo Instruments is a retro-futuristic wristwatch straight out of the Cyberpunk universe.This piece carrying the Apollo Missions revered history is a reminder of how all the advanced computing started with the Apollo Guidance Computer. The timepiece was the first ever device to have silicon microchips developed for the Moon Mission. Fast forward to current times and all our gadgets, automobiles, and everyday consumer electronics can attribute their existence to this iconic computing machine.Designer: Apollo InstrumentsNow after 55 years the computer that made possible Neil Armstrong and Buzz Aldrins first footsteps on the lunar surface, reincarnates in a working miniature form as a cool wristwatch. DSKY (Display and Keyboard) Moonwatch is a true remake of the briefcase-sized computing machine as the maker got the original design blueprints from MIT Instrumentation Laboratory. The 4:6:1 scaled recreation of the watch with digital display has a working GPS waypoint navigation system, a working keyboard, and can be programmed to include your custom modules if you are into Arduino or Python coding. Targeted towards the nerdy audience it even comes with a 8-channel digital I/O port to interact with robotic devices or breadboard interfaces.According to Mark Clayton, Apollo Instruments Fonder, Moving forward I would like to see Apollo Instruments become a focal point for space enthusiasts with authentic quality products that not only allow our customers to immerse themselves into the narrative of mankinds greatest journey but also offer an engaging experience that will inspire creativity and a continued thirst for knowledge. On the functionality front, the watch will get future updates, so that developers can come up with useful features and users can install them on the device right away. For now, it comes with functions including time/date, configurable time zones, calculator stopwatch, alarm, and V35 lights function.Apollo Instruments DSKY Moonwatch is a cool piece of technology that is a reminder of how tech advancements came to be, and how the lunar mission became a possibility. If you also want to be a part of this cool piece of history, the watch can be pre-ordered for $311.The post This Apollo Moon Mission inspired calculator wristwatch is for every space enthusiast first appeared on Yanko Design.0 Comentários 0 Compartilhamentos





