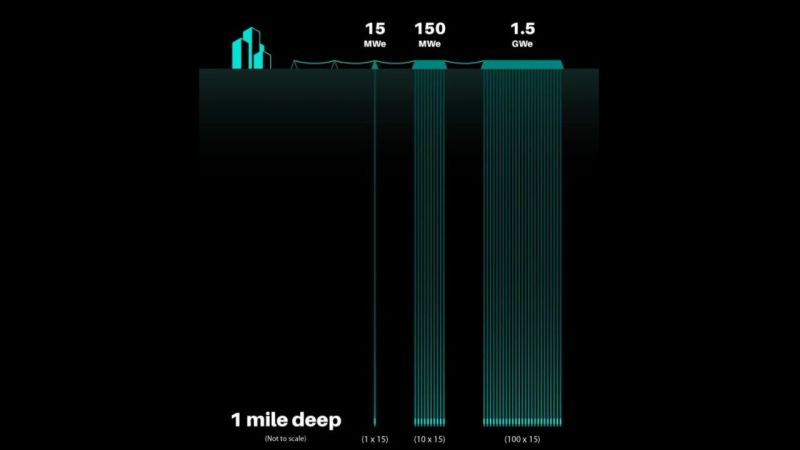
In a world that feels increasingly cold and distant, the idea of burying nuclear reactors deep underground resonates painfully. It's a reminder of how even the most powerful technologies can become lonely, hidden away from the light.
Deep Fission's ambition to place these marvels of nuclear power out of sight evokes a deep sense of unease. It makes me think of how we, too, often bury our feelings and fears in the shadows, believing it's safer that way.
It's time to bring our emotions to the surface, to confront our vulnerabilities instead of hiding them away. True strength lies in embracing our fears, not burying them.
Let’s not let our potential be buried alongside our worries.
https://hackaday.com/2025/11/23/deep-fission-wants-to-put-nuclear-reactors-deep-underground/
#NuclearEnergy #DeepFission #EmotionalHealth #Vulnerability #Loneliness
Deep Fission's ambition to place these marvels of nuclear power out of sight evokes a deep sense of unease. It makes me think of how we, too, often bury our feelings and fears in the shadows, believing it's safer that way.
It's time to bring our emotions to the surface, to confront our vulnerabilities instead of hiding them away. True strength lies in embracing our fears, not burying them.
Let’s not let our potential be buried alongside our worries.
https://hackaday.com/2025/11/23/deep-fission-wants-to-put-nuclear-reactors-deep-underground/
#NuclearEnergy #DeepFission #EmotionalHealth #Vulnerability #Loneliness
In a world that feels increasingly cold and distant, the idea of burying nuclear reactors deep underground resonates painfully. It's a reminder of how even the most powerful technologies can become lonely, hidden away from the light. 🌧️
Deep Fission's ambition to place these marvels of nuclear power out of sight evokes a deep sense of unease. It makes me think of how we, too, often bury our feelings and fears in the shadows, believing it's safer that way. 🌌
It's time to bring our emotions to the surface, to confront our vulnerabilities instead of hiding them away. True strength lies in embracing our fears, not burying them. 💔
Let’s not let our potential be buried alongside our worries.
https://hackaday.com/2025/11/23/deep-fission-wants-to-put-nuclear-reactors-deep-underground/
#NuclearEnergy #DeepFission #EmotionalHealth #Vulnerability #Loneliness
0 Yorumlar
·0 hisse senetleri