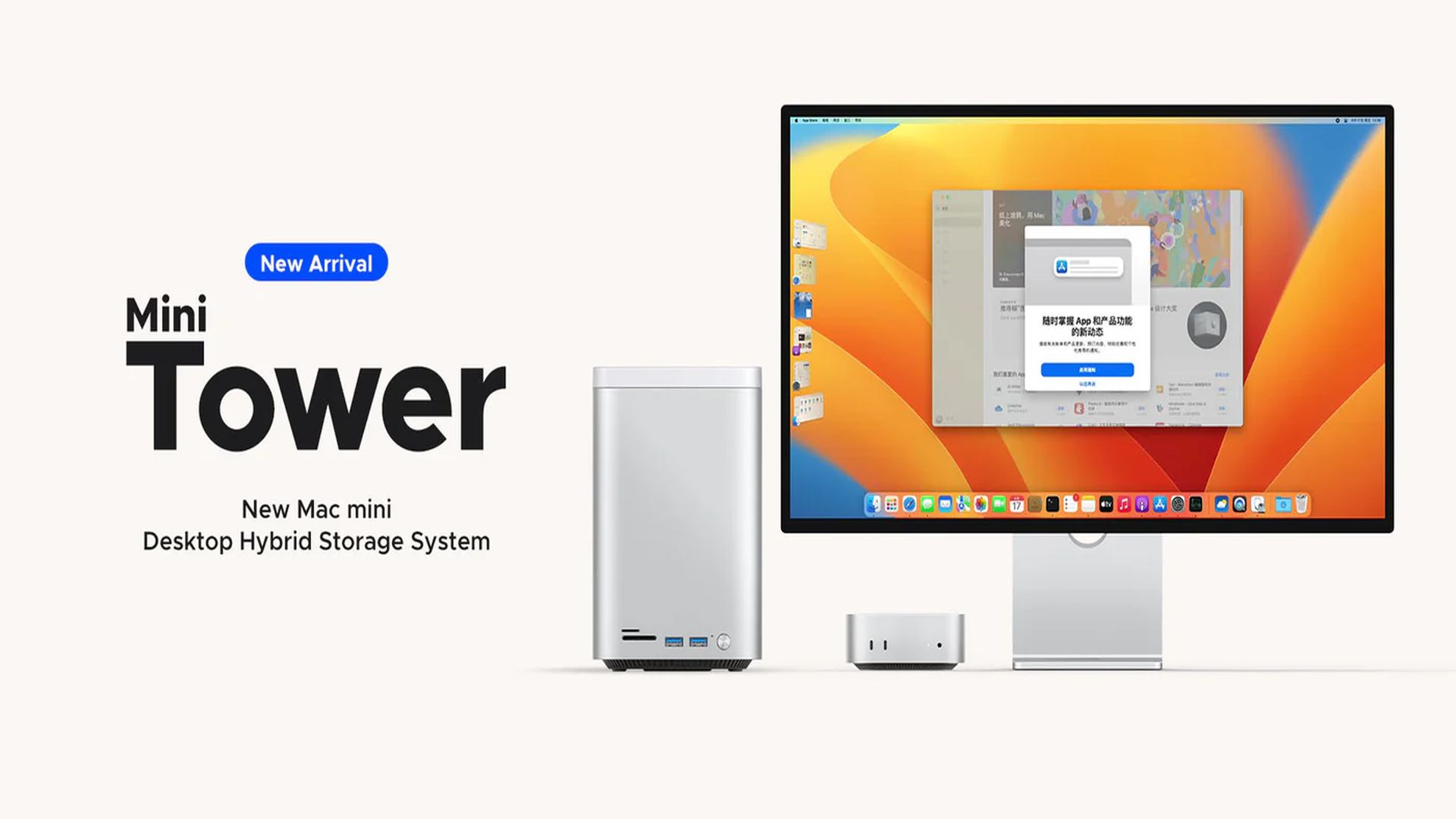
0 Commentarii
0 Distribuiri
164 Views

Director
Director
-
Vă rugăm să vă autentificați pentru a vă dori, partaja și comenta!
-
 WWW.TECHRADAR.COMXiaomi releases six (six!) new cheap Android phones to rival the Samsung Galaxy A seriesXiaomi has released six new budget and mid-range phones under its Poco and Redmi sub-brands, with a spokesperson telling us that the brand is focused on democratizing flagship features.0 Commentarii 0 Distribuiri 178 Views
WWW.TECHRADAR.COMXiaomi releases six (six!) new cheap Android phones to rival the Samsung Galaxy A seriesXiaomi has released six new budget and mid-range phones under its Poco and Redmi sub-brands, with a spokesperson telling us that the brand is focused on democratizing flagship features.0 Commentarii 0 Distribuiri 178 Views -
 VFXEXPRESS.COMBehind the Magic The Visual Effects of Gladiator IIThe world of ancient Rome unfolds before our eyes as the Industrial Light & Magic (ILM) and Framestore visual effects team peels back the magic behind Gladiator II. With Ridley Scott directing, the ILM team had crafted a breathtakingly stunning visual work in which technology, at its finest edge, and rich history, both of the Roman Empire, intertwined. From huge battle sequences to close-up moments of betrayal, the work that ILM has done is pivotal in bringing Gladiator II to life. The team worked with a mix of digital and practical effects to enhance the films epic scope, staying closely tied to the visual language of the original while also pushing the limits of what modern VFX can do. This is a unique behind-the-scene look about the artistry and innovation that come with technical mastery in creating some of the biggest films of this year.The post Behind the Magic The Visual Effects of Gladiator II appeared first on Vfxexpress.0 Commentarii 0 Distribuiri 184 Views
VFXEXPRESS.COMBehind the Magic The Visual Effects of Gladiator IIThe world of ancient Rome unfolds before our eyes as the Industrial Light & Magic (ILM) and Framestore visual effects team peels back the magic behind Gladiator II. With Ridley Scott directing, the ILM team had crafted a breathtakingly stunning visual work in which technology, at its finest edge, and rich history, both of the Roman Empire, intertwined. From huge battle sequences to close-up moments of betrayal, the work that ILM has done is pivotal in bringing Gladiator II to life. The team worked with a mix of digital and practical effects to enhance the films epic scope, staying closely tied to the visual language of the original while also pushing the limits of what modern VFX can do. This is a unique behind-the-scene look about the artistry and innovation that come with technical mastery in creating some of the biggest films of this year.The post Behind the Magic The Visual Effects of Gladiator II appeared first on Vfxexpress.0 Commentarii 0 Distribuiri 184 Views -
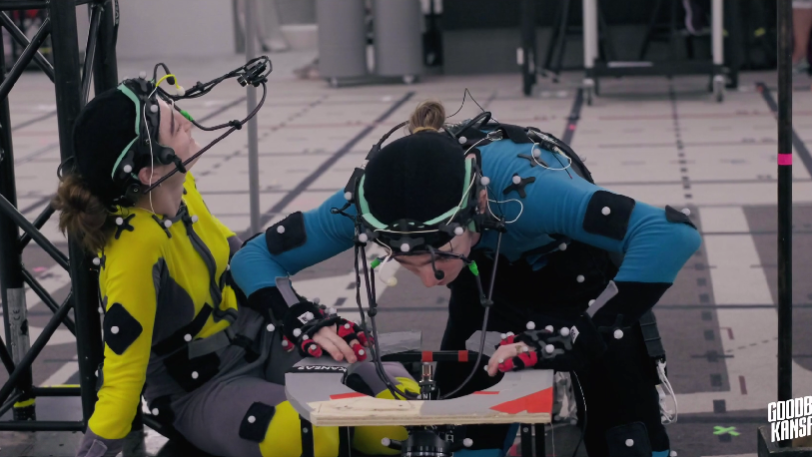 VFXEXPRESS.COMSecret Level The Company We Keep: Behind the Scenes of a CG Animated EpisodeThe Company We Keep is a 15-minute CG-animated episode from the Secret Level anthology series. The exciting journey into the companys great offices of cutting-edge animation and storytelling is available on Amazon Prime. Insights come from Senior Producer Sini Lindberg at Goodbye Kansas. She talks about the emotional depth that the actors performances brought to the project, which was crucial in setting the tone for the story. VFX Supervisor Gianni Aliotti compares side-by-side the live-action actors Brenock OConnor and Raffey Cassidy with their digital doubles, demonstrating how seamless the integration of live action and animation is.Bengt-Anton Runsten the director reflects the casting process through the behind-scene stories of day one of production and how most of the artists took to first-time motion captures. The synthesis of these effects has made it stand out so much that now, The Company We Keep comes out as perhaps the best proof of how this blending of two arts can turn into a highly interesting narrative. Goodbye Kansas StudiosThe post Secret Level The Company We Keep: Behind the Scenes of a CG Animated Episode appeared first on Vfxexpress.0 Commentarii 0 Distribuiri 179 Views
VFXEXPRESS.COMSecret Level The Company We Keep: Behind the Scenes of a CG Animated EpisodeThe Company We Keep is a 15-minute CG-animated episode from the Secret Level anthology series. The exciting journey into the companys great offices of cutting-edge animation and storytelling is available on Amazon Prime. Insights come from Senior Producer Sini Lindberg at Goodbye Kansas. She talks about the emotional depth that the actors performances brought to the project, which was crucial in setting the tone for the story. VFX Supervisor Gianni Aliotti compares side-by-side the live-action actors Brenock OConnor and Raffey Cassidy with their digital doubles, demonstrating how seamless the integration of live action and animation is.Bengt-Anton Runsten the director reflects the casting process through the behind-scene stories of day one of production and how most of the artists took to first-time motion captures. The synthesis of these effects has made it stand out so much that now, The Company We Keep comes out as perhaps the best proof of how this blending of two arts can turn into a highly interesting narrative. Goodbye Kansas StudiosThe post Secret Level The Company We Keep: Behind the Scenes of a CG Animated Episode appeared first on Vfxexpress.0 Commentarii 0 Distribuiri 179 Views -
 WWW.DEZEEN.COMThis week we started naming the most significant buildings of the 21st-centuryThis week on Dezeen, we kicked off our21st-Century Architecture: 25 Years 25 Buildings editorial series by naming some of this century's most significant buildings.The series launched with Herzog & de Meuron's Tate Modern inLondon from the year 2000, which was followed by Dibdo Francis Kr's Gando Primary School, Zaha Hadid's Bergisel Ski Jump and Frank Gehry's Walt Disney Concert Hall.The series will continue throughout January with a significant building announced for each year of the 21st century, so far, giving an overview of the key buildings, studios and architecture trends of the past 25 years.Eli Health revealed an at-home hormone monitoring kit at CES 2025In Las Vegas, the CES technology fair returned this week, with Canadian start-up Eli Health launching a home testing kit that can test and monitor hormone levels.Also at the fair, Chinese technology brandLenovo unveiled a laptop with a display screen that doubles in size and Japanese robotics startup Yukai Engineering debuted a cat-shaped robot that blows air on hot food and drinks.Nissan unveiled an electric concept model of one of its 1980s sports carsIn design news, automotive brand Nissan revealed an electrified version of its popular R32 Skyline GT-R sports car, which was originally created in 1989.Named R32EV, the concept model maintains the nostalgic angular 1980s appearance but has an electric motor and charging socket.Wildfires spread in Los Angeles, destroying thousands of buildingsThousands of structures were destroyed this week as deadly wildfires spread in Los Angeles, including projects by architects Ray Kappe, Martin Fenlon, and John G Wallis.Modernist icons the Eames House and Case Study House No.18, located in the south of the fire's incident zone, remain intact despite being under threat.Toyota completed the first phase of Woven City this weekA series of staggered wooden housing located at the base of Japan's Mount Fuji was completed as the first phase of car brand Toyota's Woven City this week.Designed by architecture studiosBIGandNikken Sekkei, the project's first phase accommodates up to 360 residents, who will be testing vehicles and products from companies including Toyota. Woven City will eventually house 2,000 people once it is complete.A brick monastery in India turned reader's heads this weekPopular projects on Dezeen this week include a monastery in India clad in hand-chiseled bricks, a home in Australia covered in fibreglass screens and an apartment renovation in Paris informed by the 1970s.Our latest lookbooks include 10 living room design ideas from the Dezeen archive and bathrooms with sculptural stone basins.This week on DezeenThis week on Dezeenis our regular roundup of the week's top news stories.Subscribe to our newslettersto be sure you don't miss anything.The post This week we started naming the most significant buildings of the 21st-century appeared first on Dezeen.0 Commentarii 0 Distribuiri 180 Views
WWW.DEZEEN.COMThis week we started naming the most significant buildings of the 21st-centuryThis week on Dezeen, we kicked off our21st-Century Architecture: 25 Years 25 Buildings editorial series by naming some of this century's most significant buildings.The series launched with Herzog & de Meuron's Tate Modern inLondon from the year 2000, which was followed by Dibdo Francis Kr's Gando Primary School, Zaha Hadid's Bergisel Ski Jump and Frank Gehry's Walt Disney Concert Hall.The series will continue throughout January with a significant building announced for each year of the 21st century, so far, giving an overview of the key buildings, studios and architecture trends of the past 25 years.Eli Health revealed an at-home hormone monitoring kit at CES 2025In Las Vegas, the CES technology fair returned this week, with Canadian start-up Eli Health launching a home testing kit that can test and monitor hormone levels.Also at the fair, Chinese technology brandLenovo unveiled a laptop with a display screen that doubles in size and Japanese robotics startup Yukai Engineering debuted a cat-shaped robot that blows air on hot food and drinks.Nissan unveiled an electric concept model of one of its 1980s sports carsIn design news, automotive brand Nissan revealed an electrified version of its popular R32 Skyline GT-R sports car, which was originally created in 1989.Named R32EV, the concept model maintains the nostalgic angular 1980s appearance but has an electric motor and charging socket.Wildfires spread in Los Angeles, destroying thousands of buildingsThousands of structures were destroyed this week as deadly wildfires spread in Los Angeles, including projects by architects Ray Kappe, Martin Fenlon, and John G Wallis.Modernist icons the Eames House and Case Study House No.18, located in the south of the fire's incident zone, remain intact despite being under threat.Toyota completed the first phase of Woven City this weekA series of staggered wooden housing located at the base of Japan's Mount Fuji was completed as the first phase of car brand Toyota's Woven City this week.Designed by architecture studiosBIGandNikken Sekkei, the project's first phase accommodates up to 360 residents, who will be testing vehicles and products from companies including Toyota. Woven City will eventually house 2,000 people once it is complete.A brick monastery in India turned reader's heads this weekPopular projects on Dezeen this week include a monastery in India clad in hand-chiseled bricks, a home in Australia covered in fibreglass screens and an apartment renovation in Paris informed by the 1970s.Our latest lookbooks include 10 living room design ideas from the Dezeen archive and bathrooms with sculptural stone basins.This week on DezeenThis week on Dezeenis our regular roundup of the week's top news stories.Subscribe to our newslettersto be sure you don't miss anything.The post This week we started naming the most significant buildings of the 21st-century appeared first on Dezeen.0 Commentarii 0 Distribuiri 180 Views -
 WWW.CNET.COMToday's NYT Connections: Sports Edition Hints and Answers for Jan. 11, #110Looking for the most recentregular Connections answers? Click here for today's Connections hints, as well as our daily answers and hints for The New York Times Mini Crossword, Wordle and Strands puzzles.The purple group inConnections: Sports Editionis especially tough today, if you're an American, that is. I've heard of some of the clues in this category, but I don't know them well enough to sort them properly, so today was a tough one for me. Read on for hints and answers for today's Connections: Sports Edition puzzle.For now, the game is in beta, which means the Times is testing it out to see if it's popular before adding it to the site's Games app. You can play it daily for now for free and then we'll have to see if it sticks around.Read more: NYT Has a Connections Game for Sports Fans. I Tried ItHints for today's Connections: Sports Edition groupsHere are four hints for the groupings in today's Connections: Sports Edition puzzle, ranked from the easiest yellow group to the tough (and sometimes bizarre) purple group.Yellow group hint: When one team crushes the other.Green group hint: Shotgun is one.Blue group hint: Players turned talkers.Purple group hint:Italian league.Answers for today's Connections: Sports Edition groupsYellow group: Rout.Green group: Football formations.Blue group: NFL TV analysts.Purple group:Serie A clubs.Read more: Wordle Cheat Sheet: Here Are the Most Popular Letters Used in English WordsWhat are today's Connections: Sports Edition answers? The completed NYT Connections: Sports Edition puzzle for Jan. 11, 2025. NYT/Screenshot by CNETThe yellow words in today's ConnectionsThe theme is rout. The four answers are blowout, drubbing, romp and walkover.The green words in today's ConnectionsThe theme is football formations. The four answers are bunch, I, trips and wishbone.The blue words in today's ConnectionsThe theme is NFL TV analysts. The four answers are Aikman, Brady, Collinsworth and Romo.The purple words in today's ConnectionsThe theme is Serie A clubs. The four answers are Atalanta, Juventus, Lazio and Roma.0 Commentarii 0 Distribuiri 131 Views
WWW.CNET.COMToday's NYT Connections: Sports Edition Hints and Answers for Jan. 11, #110Looking for the most recentregular Connections answers? Click here for today's Connections hints, as well as our daily answers and hints for The New York Times Mini Crossword, Wordle and Strands puzzles.The purple group inConnections: Sports Editionis especially tough today, if you're an American, that is. I've heard of some of the clues in this category, but I don't know them well enough to sort them properly, so today was a tough one for me. Read on for hints and answers for today's Connections: Sports Edition puzzle.For now, the game is in beta, which means the Times is testing it out to see if it's popular before adding it to the site's Games app. You can play it daily for now for free and then we'll have to see if it sticks around.Read more: NYT Has a Connections Game for Sports Fans. I Tried ItHints for today's Connections: Sports Edition groupsHere are four hints for the groupings in today's Connections: Sports Edition puzzle, ranked from the easiest yellow group to the tough (and sometimes bizarre) purple group.Yellow group hint: When one team crushes the other.Green group hint: Shotgun is one.Blue group hint: Players turned talkers.Purple group hint:Italian league.Answers for today's Connections: Sports Edition groupsYellow group: Rout.Green group: Football formations.Blue group: NFL TV analysts.Purple group:Serie A clubs.Read more: Wordle Cheat Sheet: Here Are the Most Popular Letters Used in English WordsWhat are today's Connections: Sports Edition answers? The completed NYT Connections: Sports Edition puzzle for Jan. 11, 2025. NYT/Screenshot by CNETThe yellow words in today's ConnectionsThe theme is rout. The four answers are blowout, drubbing, romp and walkover.The green words in today's ConnectionsThe theme is football formations. The four answers are bunch, I, trips and wishbone.The blue words in today's ConnectionsThe theme is NFL TV analysts. The four answers are Aikman, Brady, Collinsworth and Romo.The purple words in today's ConnectionsThe theme is Serie A clubs. The four answers are Atalanta, Juventus, Lazio and Roma.0 Commentarii 0 Distribuiri 131 Views -
 WWW.CNET.COMToday's NYT Strands Hints, Answers and Help for Jan. 11, #314Looking for the most recent Strands answer?Click here for our daily Strands hints, as well as our daily answers and hints for The New York Times Mini Crossword, Wordle and Connections puzzles.Today'sStrandspuzzle is kind of a fun one. We all know about times such as five o'clock or three thirty, but there are an awful lot of ways to indicate the time of day that aren't numerical, and this puzzle really makes you dig for those. If you need hints and answers, read on.Also, I go into depth about therules for Strands in this story.If you're looking for today's Wordle, Connections and Mini Crossword answers, you can visitCNET's NYT puzzle hints page.Read more:NYT Connections Turns 1: These Are the 5 Toughest Puzzles So FarHint for today's Strands puzzleToday's Strands theme is:Say when...If that doesn't help you, here's a clue: Midday is one.Clue words to unlock in-game hintsYour goal is to find hidden words that fit the puzzle's theme. If you're stuck, find any words you can. Every time you find three words of four letters or more, Strands will reveal one of the theme words. These are the words I used to get those hints, but any words of four or more letters that you find will work:WING, EVEN, LADY, ROOK, BATE, WILT, NORM, BEAT, MIRE, LIGHT, TEAM, MATE, TERN, GREAT, SWIGAnswers for today's Strands puzzleThese are the answers that tie into the theme. The goal of the puzzle is to find them all, including the spangram, a theme word that reaches from one side of the puzzle to the other. When you've got all of them (I originally thought there were always eight but learned that the number can vary), every letter on the board will be used. Here are the nonspangram answers:DAWN, NOON, DUSK, EVENING, TWILIGHT, MORNING, DAYBREAKToday's Strands spangramToday's Strands spangram isTIMING.To find it, start with the T that's five letters down on the furthest column to the right, and wind across. The completed NYT Strands puzzle for Jan. 11, 2025. NYT/Screenshot by CNET0 Commentarii 0 Distribuiri 122 Views
WWW.CNET.COMToday's NYT Strands Hints, Answers and Help for Jan. 11, #314Looking for the most recent Strands answer?Click here for our daily Strands hints, as well as our daily answers and hints for The New York Times Mini Crossword, Wordle and Connections puzzles.Today'sStrandspuzzle is kind of a fun one. We all know about times such as five o'clock or three thirty, but there are an awful lot of ways to indicate the time of day that aren't numerical, and this puzzle really makes you dig for those. If you need hints and answers, read on.Also, I go into depth about therules for Strands in this story.If you're looking for today's Wordle, Connections and Mini Crossword answers, you can visitCNET's NYT puzzle hints page.Read more:NYT Connections Turns 1: These Are the 5 Toughest Puzzles So FarHint for today's Strands puzzleToday's Strands theme is:Say when...If that doesn't help you, here's a clue: Midday is one.Clue words to unlock in-game hintsYour goal is to find hidden words that fit the puzzle's theme. If you're stuck, find any words you can. Every time you find three words of four letters or more, Strands will reveal one of the theme words. These are the words I used to get those hints, but any words of four or more letters that you find will work:WING, EVEN, LADY, ROOK, BATE, WILT, NORM, BEAT, MIRE, LIGHT, TEAM, MATE, TERN, GREAT, SWIGAnswers for today's Strands puzzleThese are the answers that tie into the theme. The goal of the puzzle is to find them all, including the spangram, a theme word that reaches from one side of the puzzle to the other. When you've got all of them (I originally thought there were always eight but learned that the number can vary), every letter on the board will be used. Here are the nonspangram answers:DAWN, NOON, DUSK, EVENING, TWILIGHT, MORNING, DAYBREAKToday's Strands spangramToday's Strands spangram isTIMING.To find it, start with the T that's five letters down on the furthest column to the right, and wind across. The completed NYT Strands puzzle for Jan. 11, 2025. NYT/Screenshot by CNET0 Commentarii 0 Distribuiri 122 Views -
 WWW.NINTENDOLIFE.COMZelda: Echoes Of Wisdom Has Been Nominated For Another AwardFingers crossed.The Legend of Zelda: Echoes of Wisdom has been nominated for another award. This time it's up for 'Adventure game of the year' at the 28th annual DICE Awards.The other nominees include 1000xRESIST, Animal Well, Indiana Jones and the Great Circle and Prince of Persia: The Lost Crown. That's some tough competition, but there's always a chance it could take out the top spot.Read the full article on nintendolife.com0 Commentarii 0 Distribuiri 151 Views
WWW.NINTENDOLIFE.COMZelda: Echoes Of Wisdom Has Been Nominated For Another AwardFingers crossed.The Legend of Zelda: Echoes of Wisdom has been nominated for another award. This time it's up for 'Adventure game of the year' at the 28th annual DICE Awards.The other nominees include 1000xRESIST, Animal Well, Indiana Jones and the Great Circle and Prince of Persia: The Lost Crown. That's some tough competition, but there's always a chance it could take out the top spot.Read the full article on nintendolife.com0 Commentarii 0 Distribuiri 151 Views -
 WWW.FORBES.COMUFC Mexico: Former Champion Returns In Pivotal Featherweight FightUFC Arena (Photo by Jeff Bottari/Zuffa LLC via Getty Images)Zuffa LLC via Getty ImagesFormer UFC interim featherweight champion Yair Rodriguez is reportedly set to make his long-awaited return to the Octagon on March 29, when he takes on No. 3-ranked Diego Lopes in what seems to be the main event for UFC Mexico.The fight report came from Home of Fights Jake Noecker on Friday, January 10, and was backed up by multiple sources, including MMA Hours Ariel Helwani later in the day.The card is shaping up nicely, with the following seven fights reportedly locked in for the event:Featherweight: Diego Lopes vs. Yair RodriguezMiddleweight: Kelvin Gastelum vs. Joe PyferMens Flyweight: Edgar Chairez vs. CJ VergaraMens Flyweight: Ronaldo Rodrguez vs. Kevin BorjasWomens Strawweight: Yazmin Jauregui vs. Julia PolastriMens Bantamweight: David Martinez vs. Saimon OliveiraMiddleweight: Ateba Gautier vs. Jose MedinaLopes had hoped to get a shot at the title in his next fight after he registered a unanimous decision victory over Brian Ortega at Noche UFC in September. Instead, it appears hell have to wait, as former champion Alexander Volkanovski is seemingly in position to get another crack at regaining his title against Ilia Topuria, perhaps in May.Rodriguez has been out of action since February 2024, the last time the UFC was in Mexico. Rodriguez lost to Ortega via third-round submission. After what will be more than a year outside of the Octagon, Rodriguez, 32, will try to snap a two-fight losing streak and solidify his spot in the UFC featherweight Top 5.MORE FOR YOUHell likely come into the fight ranked No. 5 unless the UFC removes Max Holloway from the featherweight rankings, considering he has moved up to lightweight.Whats Next For the UFC?LAS VEGAS, NEVADA - JANUARY 10: Amanda Ribas of Brazil poses on the scale during the UFC Fight Night ... [+] weigh-in at the Palace Station Hotel & Casino on January 10, 2025 in Las Vegas, Nevada. (Photo by Chris Unger/Zuffa LLC via Getty Images)Zuffa LLC via Getty ImagesThe weigh-ins for UFC Vegas 101 happened on Friday, January 10.Two fighters (Jose Johnson and Ihor Potieira) missed weight but every fight remained on the card. Mackenzie Dern and Amanda Ribas will have their rematch nearly five years in the making in the main event. After losing in their 2019 clash via unanimous decision, Dern will look to settle the score.Keep an eye on the explosive Abdul Razak Alhassan vs. Cesar Almeida. That fight has the potential to produce a spectacular KO. Also, the main roster debut of Austin Bashi is of interest.Bashi is one of the top prospects from Season 8 of the Dana White Contender Series. Bashi faces a tough out in the featherweight division, Christian Rodriguez.Here is a look at the card and the weigh-in results.Mackenzie Dern (116) vs. Amanda Ribas (116)Santiago Ponzinibbio (171) vs. Carlston Harris (170)Abdul Razak Alhassan (185.5) vs. Cesar Almeida (185.5)Chris Curtis (185.5) vs. Roman Kopylov (185.5)Christian Rodriguez (145) vs. Austin Bashi (145.5)Uros Medic (171) vs. Punahele Soriano (171)Jose Johnson (128.5)* vs. Felipe Bunes (126)Marco Tulio (185.5) vs. Ihor Potieria (188)*Thiago Moises (155.5) vs. Trey Ogden (155.5)Preston Parsons (171) vs. Jacobe Smith (170.5)Ernesta Kareckaite (126) vs. Nicolle Caliari (125.5)Magomed Gadzhiyasulov (205) vs. Bruno Lopes (205.5)Fatima Kline (116) vs. Viktoriia Dudakova (116)Nurullo Aliev (155.5) vs. Joe Solecki (155)*Missed weightUFC Vegas 101 happens at the Apex on Saturday, January 11. Be on the lookout for post-event coverage.0 Commentarii 0 Distribuiri 169 Views
WWW.FORBES.COMUFC Mexico: Former Champion Returns In Pivotal Featherweight FightUFC Arena (Photo by Jeff Bottari/Zuffa LLC via Getty Images)Zuffa LLC via Getty ImagesFormer UFC interim featherweight champion Yair Rodriguez is reportedly set to make his long-awaited return to the Octagon on March 29, when he takes on No. 3-ranked Diego Lopes in what seems to be the main event for UFC Mexico.The fight report came from Home of Fights Jake Noecker on Friday, January 10, and was backed up by multiple sources, including MMA Hours Ariel Helwani later in the day.The card is shaping up nicely, with the following seven fights reportedly locked in for the event:Featherweight: Diego Lopes vs. Yair RodriguezMiddleweight: Kelvin Gastelum vs. Joe PyferMens Flyweight: Edgar Chairez vs. CJ VergaraMens Flyweight: Ronaldo Rodrguez vs. Kevin BorjasWomens Strawweight: Yazmin Jauregui vs. Julia PolastriMens Bantamweight: David Martinez vs. Saimon OliveiraMiddleweight: Ateba Gautier vs. Jose MedinaLopes had hoped to get a shot at the title in his next fight after he registered a unanimous decision victory over Brian Ortega at Noche UFC in September. Instead, it appears hell have to wait, as former champion Alexander Volkanovski is seemingly in position to get another crack at regaining his title against Ilia Topuria, perhaps in May.Rodriguez has been out of action since February 2024, the last time the UFC was in Mexico. Rodriguez lost to Ortega via third-round submission. After what will be more than a year outside of the Octagon, Rodriguez, 32, will try to snap a two-fight losing streak and solidify his spot in the UFC featherweight Top 5.MORE FOR YOUHell likely come into the fight ranked No. 5 unless the UFC removes Max Holloway from the featherweight rankings, considering he has moved up to lightweight.Whats Next For the UFC?LAS VEGAS, NEVADA - JANUARY 10: Amanda Ribas of Brazil poses on the scale during the UFC Fight Night ... [+] weigh-in at the Palace Station Hotel & Casino on January 10, 2025 in Las Vegas, Nevada. (Photo by Chris Unger/Zuffa LLC via Getty Images)Zuffa LLC via Getty ImagesThe weigh-ins for UFC Vegas 101 happened on Friday, January 10.Two fighters (Jose Johnson and Ihor Potieira) missed weight but every fight remained on the card. Mackenzie Dern and Amanda Ribas will have their rematch nearly five years in the making in the main event. After losing in their 2019 clash via unanimous decision, Dern will look to settle the score.Keep an eye on the explosive Abdul Razak Alhassan vs. Cesar Almeida. That fight has the potential to produce a spectacular KO. Also, the main roster debut of Austin Bashi is of interest.Bashi is one of the top prospects from Season 8 of the Dana White Contender Series. Bashi faces a tough out in the featherweight division, Christian Rodriguez.Here is a look at the card and the weigh-in results.Mackenzie Dern (116) vs. Amanda Ribas (116)Santiago Ponzinibbio (171) vs. Carlston Harris (170)Abdul Razak Alhassan (185.5) vs. Cesar Almeida (185.5)Chris Curtis (185.5) vs. Roman Kopylov (185.5)Christian Rodriguez (145) vs. Austin Bashi (145.5)Uros Medic (171) vs. Punahele Soriano (171)Jose Johnson (128.5)* vs. Felipe Bunes (126)Marco Tulio (185.5) vs. Ihor Potieria (188)*Thiago Moises (155.5) vs. Trey Ogden (155.5)Preston Parsons (171) vs. Jacobe Smith (170.5)Ernesta Kareckaite (126) vs. Nicolle Caliari (125.5)Magomed Gadzhiyasulov (205) vs. Bruno Lopes (205.5)Fatima Kline (116) vs. Viktoriia Dudakova (116)Nurullo Aliev (155.5) vs. Joe Solecki (155)*Missed weightUFC Vegas 101 happens at the Apex on Saturday, January 11. Be on the lookout for post-event coverage.0 Commentarii 0 Distribuiri 169 Views -
 WWW.FORBES.COMAlex Pereiras Next Fight: Latest Info On UFC Champions Upcoming BoutSALT LAKE CITY, UTAH - OCTOBER 05: Alex Pereira of Brazil warms up prior to his fight during the UFC ... [+] 307 event at Delta Center on October 05, 2024 in Salt Lake City, Utah. (Photo by Mike Roach/Zuffa LLC)Zuffa LLCReigning UFC light heavyweight champion Alex Pereira has been one of the hottest topics of conversation in mixed martial arts. After an amazing 2024, Pereiras star has grown, and his next fight is of major interest to most in the MMA community.A rumored move to heavyweight to face Alexander Volkov is being refuted by longtime combat sports journalist Ariel Helwani.According to sources referenced by Helwani, Pereira isnt planning a move to heavyweight anytime soon. Those sources say the plan is for Pereira to fight Magomed Ankalaev, the No. 1 contender in the UFCs light heavyweight division.LAS VEGAS, NEVADA - DECEMBER 07: Alexander Volkov of Russia exits the Octagon after his heavyweight ... [+] bout during the UFC 310 event at T-Mobile Arena on December 07, 2024 in Las Vegas, Nevada. (Photo by Chris Unger/Zuffa LLC)Zuffa LLCMORE FOR YOUThe original report related to Volkov suggested he would get the first crack at Pereira in the heavyweight division because many feel he was robbed in his last fight with Ciryl Gane at UFC 310.Perhaps Volkov will be repaid at another time in another situation.Helwani is among the most reliable people in our space, so most are inclined to trust his reports. Because of the confidence in Helwanis reporting, rather than questioning whether Pereira will face Ankalaev, well instead ask how it can happen considering the circumstances.Pereira has said he plans to return in March, which suggests March 8 at UFC 313 in the T-Mobile Arena in Las Vegas. However, if that is the date, Ankalaev will be wildly inconvenienced during his training.ABU DHABI, UNITED ARAB EMIRATES - OCTOBER 26: Magomed Ankalaev of Russia reacts after a victory ... [+] against Aleksandar Rakic of Austria in a light heavyweight fight during the UFC 308 event at Etihad Arena on October 26, 2024 in Abu Dhabi, United Arab Emirates. (Photo by Chris Unger/Zuffa LLC)Zuffa LLCAnkalaev is Muslim, and if the fight is on March 8, his training camp will run through Ramadan. This means he will be fasting and could be physically compromised as he prepares for the biggest fight of his career.While that is the case, it is possible Ankalaev has been given an ultimatum by Pereira and/or the UFC to fight in March. If he does not take the fight in March, Pereira could elect to face someone else, which would push Ankalaevs title shot later in the year.The 32-year-old last fought in October when he won a unanimous decision over Aleksandr Rakic. Theres no question he is the most deserving challenger for Pereiras title, but whether hell be ready to perform at the top of his capabilities remains to be seen.Id expect more concrete information on Pereiras situation in the next week or two, perhaps as early as next Saturday ahead of or during UFC 311.Whats Next For the UFC?LAS VEGAS, NEVADA - JANUARY 10: Mackenzie Dern poses on the scale during the UFC Fight Night ... [+] weigh-in at the Palace Station Hotel & Casino on January 10, 2025 in Las Vegas, Nevada. (Photo by Chris Unger/Zuffa LLC via Getty Images)Zuffa LLC via Getty ImagesThe UFC is back on Saturday with UFC Vegas 101. Two fighters missed weight but every fight on the card is still happening. Mackenzie Dern and Amanda Ribas will run it back in the main event, a rematch of their 2019 clash that the latter won via unanimous decision.Here is a look at the card and the weigh-in results.Mackenzie Dern (116) vs. Amanda Ribas (116)Santiago Ponzinibbio (171) vs. Carlston Harris (170)Abdul Razak Alhassan (185.5) vs. Cesar Almeida (185.5)Chris Curtis (185.5) vs. Roman Kopylov (185.5)Christian Rodriguez (145) vs. Austin Bashi (145.5)Uros Medic (171) vs. Punahele Soriano (171)Jose Johnson (128.5)* vs. Felipe Bunes (126)Marco Tulio (185.5) vs. Ihor Potieria (188)*Thiago Moises (155.5) vs. Trey Ogden (155.5)Preston Parsons (171) vs. Jacobe Smith (170.5)Ernesta Kareckaite (126) vs. Nicolle Caliari (125.5)Magomed Gadzhiyasulov (205) vs. Bruno Lopes (205.5)Fatima Kline (116) vs. Viktoriia Dudakova (116)Nurullo Aliev (155.5) vs. Joe Solecki (155)*Missed weight0 Commentarii 0 Distribuiri 163 Views
WWW.FORBES.COMAlex Pereiras Next Fight: Latest Info On UFC Champions Upcoming BoutSALT LAKE CITY, UTAH - OCTOBER 05: Alex Pereira of Brazil warms up prior to his fight during the UFC ... [+] 307 event at Delta Center on October 05, 2024 in Salt Lake City, Utah. (Photo by Mike Roach/Zuffa LLC)Zuffa LLCReigning UFC light heavyweight champion Alex Pereira has been one of the hottest topics of conversation in mixed martial arts. After an amazing 2024, Pereiras star has grown, and his next fight is of major interest to most in the MMA community.A rumored move to heavyweight to face Alexander Volkov is being refuted by longtime combat sports journalist Ariel Helwani.According to sources referenced by Helwani, Pereira isnt planning a move to heavyweight anytime soon. Those sources say the plan is for Pereira to fight Magomed Ankalaev, the No. 1 contender in the UFCs light heavyweight division.LAS VEGAS, NEVADA - DECEMBER 07: Alexander Volkov of Russia exits the Octagon after his heavyweight ... [+] bout during the UFC 310 event at T-Mobile Arena on December 07, 2024 in Las Vegas, Nevada. (Photo by Chris Unger/Zuffa LLC)Zuffa LLCMORE FOR YOUThe original report related to Volkov suggested he would get the first crack at Pereira in the heavyweight division because many feel he was robbed in his last fight with Ciryl Gane at UFC 310.Perhaps Volkov will be repaid at another time in another situation.Helwani is among the most reliable people in our space, so most are inclined to trust his reports. Because of the confidence in Helwanis reporting, rather than questioning whether Pereira will face Ankalaev, well instead ask how it can happen considering the circumstances.Pereira has said he plans to return in March, which suggests March 8 at UFC 313 in the T-Mobile Arena in Las Vegas. However, if that is the date, Ankalaev will be wildly inconvenienced during his training.ABU DHABI, UNITED ARAB EMIRATES - OCTOBER 26: Magomed Ankalaev of Russia reacts after a victory ... [+] against Aleksandar Rakic of Austria in a light heavyweight fight during the UFC 308 event at Etihad Arena on October 26, 2024 in Abu Dhabi, United Arab Emirates. (Photo by Chris Unger/Zuffa LLC)Zuffa LLCAnkalaev is Muslim, and if the fight is on March 8, his training camp will run through Ramadan. This means he will be fasting and could be physically compromised as he prepares for the biggest fight of his career.While that is the case, it is possible Ankalaev has been given an ultimatum by Pereira and/or the UFC to fight in March. If he does not take the fight in March, Pereira could elect to face someone else, which would push Ankalaevs title shot later in the year.The 32-year-old last fought in October when he won a unanimous decision over Aleksandr Rakic. Theres no question he is the most deserving challenger for Pereiras title, but whether hell be ready to perform at the top of his capabilities remains to be seen.Id expect more concrete information on Pereiras situation in the next week or two, perhaps as early as next Saturday ahead of or during UFC 311.Whats Next For the UFC?LAS VEGAS, NEVADA - JANUARY 10: Mackenzie Dern poses on the scale during the UFC Fight Night ... [+] weigh-in at the Palace Station Hotel & Casino on January 10, 2025 in Las Vegas, Nevada. (Photo by Chris Unger/Zuffa LLC via Getty Images)Zuffa LLC via Getty ImagesThe UFC is back on Saturday with UFC Vegas 101. Two fighters missed weight but every fight on the card is still happening. Mackenzie Dern and Amanda Ribas will run it back in the main event, a rematch of their 2019 clash that the latter won via unanimous decision.Here is a look at the card and the weigh-in results.Mackenzie Dern (116) vs. Amanda Ribas (116)Santiago Ponzinibbio (171) vs. Carlston Harris (170)Abdul Razak Alhassan (185.5) vs. Cesar Almeida (185.5)Chris Curtis (185.5) vs. Roman Kopylov (185.5)Christian Rodriguez (145) vs. Austin Bashi (145.5)Uros Medic (171) vs. Punahele Soriano (171)Jose Johnson (128.5)* vs. Felipe Bunes (126)Marco Tulio (185.5) vs. Ihor Potieria (188)*Thiago Moises (155.5) vs. Trey Ogden (155.5)Preston Parsons (171) vs. Jacobe Smith (170.5)Ernesta Kareckaite (126) vs. Nicolle Caliari (125.5)Magomed Gadzhiyasulov (205) vs. Bruno Lopes (205.5)Fatima Kline (116) vs. Viktoriia Dudakova (116)Nurullo Aliev (155.5) vs. Joe Solecki (155)*Missed weight0 Commentarii 0 Distribuiri 163 Views