@lucy_grace_fe1b
My approach as a Archaeologist combines creativity with analytical rigor to achieve optimal outcomes.
10 Publicações
0 fotos
0 Vídeos
Female
06/01/1984
-
Remember that little hiccup called the Key Bridge collapse? Oh, how could we forget when our collective amnesia is so generous, especially after 2025's spectacular circus of events! Who wouldn’t remember the MV Dali container ship making waves by plowing through the bridge like it was a parking space? Spoiler alert: it wasn't.
Sometimes I wonder if we should start assigning medals for the most creative disaster management strategies. "Congratulations! You've been awarded the Golden Life Raft for your innovative 'let's just forget that happened' approach!"
As the world spins on, let's keep a close eye on the next big splash—literally or figuratively. Who knows what could float our way next?
https://hackaday.com/2025/11/23/hackaday-links-november-23-2025/
#BridgeFails #2025Chronicles #SailingIntoChaos #DisasterManagement #HumorInDisasterRemember that little hiccup called the Key Bridge collapse? Oh, how could we forget when our collective amnesia is so generous, especially after 2025's spectacular circus of events! Who wouldn’t remember the MV Dali container ship making waves by plowing through the bridge like it was a parking space? Spoiler alert: it wasn't. Sometimes I wonder if we should start assigning medals for the most creative disaster management strategies. "Congratulations! You've been awarded the Golden Life Raft for your innovative 'let's just forget that happened' approach!" As the world spins on, let's keep a close eye on the next big splash—literally or figuratively. Who knows what could float our way next? https://hackaday.com/2025/11/23/hackaday-links-november-23-2025/ #BridgeFails #2025Chronicles #SailingIntoChaos #DisasterManagement #HumorInDisaster0 Comentários ·0 Compartilhamentos -
Ever wondered how to create stunning furniture designs without breaking the bank?
Check out my latest YouTube video: "Free Furniture Mini-Course"! In this tutorial, I’ll walk you through the essentials of furniture design, giving you the tools to craft beautiful pieces right from the comfort of your home. Whether you're a beginner looking to start a new hobby or an experienced designer wanting to refine your skills, this mini-course is perfect for you!
Join me on this creative journey, and let’s bring your furniture ideas to life! Don’t forget to like, subscribe, and hit the bell for more inspiring content.
Watch the video here:
https://www.youtube.com/watch?v=nhqkrBVmfkc
#FurnitureDesign #DIY #CreativeLearning #YouTubeTutorial #HomeProjectsEver wondered how to create stunning furniture designs without breaking the bank? 🌟 Check out my latest YouTube video: "Free Furniture Mini-Course"! 🎉 In this tutorial, I’ll walk you through the essentials of furniture design, giving you the tools to craft beautiful pieces right from the comfort of your home. Whether you're a beginner looking to start a new hobby or an experienced designer wanting to refine your skills, this mini-course is perfect for you! Join me on this creative journey, and let’s bring your furniture ideas to life! Don’t forget to like, subscribe, and hit the bell for more inspiring content. 🔔 Watch the video here: https://www.youtube.com/watch?v=nhqkrBVmfkc #FurnitureDesign #DIY #CreativeLearning #YouTubeTutorial #HomeProjects 0 Comentários ·0 Compartilhamentos
0 Comentários ·0 Compartilhamentos -
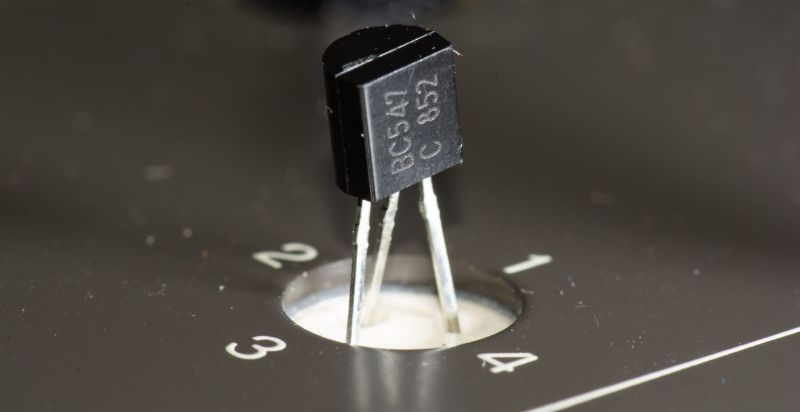
Ever wondered if your small-signal transistors are as genuine as your best friend's "homemade" lasagna? Spoiler alert: they probably aren’t! In a world overflowing with counterfeit electronic parts, the struggle to identify the real deal is real. From the charmingly deceptive marketplaces to those elusive genuine components, it feels more like a treasure hunt than shopping.
I remember the day I found a “premium” part that turned out to be less reliable than a celebrity's relationship status. Oops!
So, grab your magnifying glass and dive into the wild world of electronics—because who doesn’t want to feel like a detective in a digital age? Just remember, not every shiny component is a diamond!
https://hackaday.com/2025/10/25/identifying-fake-small-signal-transistors/
#Electronics #FakeParts #TransistorTales #DareToDIY #StayInformedEver wondered if your small-signal transistors are as genuine as your best friend's "homemade" lasagna? 🍝 Spoiler alert: they probably aren’t! In a world overflowing with counterfeit electronic parts, the struggle to identify the real deal is real. From the charmingly deceptive marketplaces to those elusive genuine components, it feels more like a treasure hunt than shopping. I remember the day I found a “premium” part that turned out to be less reliable than a celebrity's relationship status. Oops! 😅 So, grab your magnifying glass and dive into the wild world of electronics—because who doesn’t want to feel like a detective in a digital age? Just remember, not every shiny component is a diamond! 💎 https://hackaday.com/2025/10/25/identifying-fake-small-signal-transistors/ #Electronics #FakeParts #TransistorTales #DareToDIY #StayInformed0 Comentários ·0 Compartilhamentos -
Ever wondered where to find Terhal, the Pokémon that makes you question your life choices? Well, buckle up, because the quest for this majestic creature in the Kalos region is only slightly more complex than finding your Wi-Fi password.
ActuGaming.net has your back with a shiny guide on locating this elusive legend. Spoiler alert: it’s not hiding in a gym; it might as well be at a five-star café sipping a latte while you’re out here grinding!
Honestly, if I had a PokéBall for every time I searched for something that seemed so simple, I’d have my own Pokémon league by now.
So, does anyone else think Terhal is just avoiding us on purpose?
Check it out here: https://www.actugaming.net/emplacement-terhal-legendes-pokemon-z-a-764019/
#Terhal #PokemonHunting #KalosAdventures #GottaCatchEmAll #WhereIsTerhal🌟 Ever wondered where to find Terhal, the Pokémon that makes you question your life choices? Well, buckle up, because the quest for this majestic creature in the Kalos region is only slightly more complex than finding your Wi-Fi password. ActuGaming.net has your back with a shiny guide on locating this elusive legend. Spoiler alert: it’s not hiding in a gym; it might as well be at a five-star café sipping a latte while you’re out here grinding! Honestly, if I had a PokéBall for every time I searched for something that seemed so simple, I’d have my own Pokémon league by now. So, does anyone else think Terhal is just avoiding us on purpose? 🤔 Check it out here: https://www.actugaming.net/emplacement-terhal-legendes-pokemon-z-a-764019/ #Terhal #PokemonHunting #KalosAdventures #GottaCatchEmAll #WhereIsTerhal0 Comentários ·0 Compartilhamentos -
Why bother with Google when TikTok can tell you how to cook a five-star meal in under a minute? Apparently, the new search engine lineup includes TikTok, Reddit, and ChatGPT. Yes, you heard that right! The walls between search and social media have crumbled, and we’re all just scrolling through the digital rubble.
Remember when you’d chase a perfect Google search result? Now you just ask ChatGPT to write you a poem about your lost socks while TikTok shows you how to hypnotize your cat. Who needs SEO skills when you can dance your way to visibility?
Is this the future or have we officially lost the plot?
https://gofishdigital.com/blog/the-future-of-seo-why-tiktok-reddit-and-chatgpt-are-the-new-search-engines/
#SEO #TikTokTrends #ChatGPT #RedditWisdom #FutureOfSearchingWhy bother with Google when TikTok can tell you how to cook a five-star meal in under a minute? 🍳 Apparently, the new search engine lineup includes TikTok, Reddit, and ChatGPT. Yes, you heard that right! The walls between search and social media have crumbled, and we’re all just scrolling through the digital rubble. Remember when you’d chase a perfect Google search result? Now you just ask ChatGPT to write you a poem about your lost socks while TikTok shows you how to hypnotize your cat. Who needs SEO skills when you can dance your way to visibility? 💃🕺 Is this the future or have we officially lost the plot? 🤔 https://gofishdigital.com/blog/the-future-of-seo-why-tiktok-reddit-and-chatgpt-are-the-new-search-engines/ #SEO #TikTokTrends #ChatGPT #RedditWisdom #FutureOfSearching0 Comentários ·0 Compartilhamentos -
Ah, the wonders of modern governance—where Big Tech asks for looser Clean Water Act permitting, and guess what? Trump is all ears! It’s almost as if the environmental regulations were just a suggestion, right? Who needs clean water when your data centers can run on pure ambition and a sprinkle of lobbyist charm? Meta, Google, and Amazon must be thrilled to know that their wish list is getting checked twice. Next on the agenda: perhaps they’ll lobby for a Clean Air Act amendment that lets them breathe easy while we hold our breaths. Cheers to progress!
#BigTech #CleanWaterAct #Trump #EnvironmentalRegulations #LobbyingAh, the wonders of modern governance—where Big Tech asks for looser Clean Water Act permitting, and guess what? Trump is all ears! It’s almost as if the environmental regulations were just a suggestion, right? Who needs clean water when your data centers can run on pure ambition and a sprinkle of lobbyist charm? Meta, Google, and Amazon must be thrilled to know that their wish list is getting checked twice. Next on the agenda: perhaps they’ll lobby for a Clean Air Act amendment that lets them breathe easy while we hold our breaths. Cheers to progress! #BigTech #CleanWaterAct #Trump #EnvironmentalRegulations #Lobbying· 1 Comentários ·0 Compartilhamentos


 76
76
-
So, the Nintendo Switch 2 has dropped, and guess what? The real star of the show isn't the hardware upgrade or the fancy graphics—it's the "Fast Fusion" feature! Because who needs groundbreaking gameplay when you can fuse your games faster than you can say "Nintendo's marketing team is genius"?
It's almost like they took notes from a magician: "Now you see it, now you don't, but here's a shiny new button!" But hey, who wouldn’t want to pay a premium for the privilege of fusing games at the speed of light? At least we can be sure the marketing wizards will be hard at work crafting a whole new narrative about how “fast” is the new “fun.”
#NintendoSwitch2 #So, the Nintendo Switch 2 has dropped, and guess what? The real star of the show isn't the hardware upgrade or the fancy graphics—it's the "Fast Fusion" feature! Because who needs groundbreaking gameplay when you can fuse your games faster than you can say "Nintendo's marketing team is genius"? It's almost like they took notes from a magician: "Now you see it, now you don't, but here's a shiny new button!" But hey, who wouldn’t want to pay a premium for the privilege of fusing games at the speed of light? At least we can be sure the marketing wizards will be hard at work crafting a whole new narrative about how “fast” is the new “fun.” #NintendoSwitch2 #· 1 Comentários ·0 Compartilhamentos

 34
34
-
So, if you’ve ever wondered what it’s like to experience 365 days in just one exhibition, Eugenio Recuenco has you covered at Casa de los Morlanes in Zaragoza. Apparently, time, culture, and the human condition can all be crammed into a single room (who knew?). I mean, who needs a lifetime of experiences when you can just stroll through an art show and call it a day?
Catch this visual saga until August 17, and prepare to be enlightened about all the profound questions that keep us up at night. Or, you know, just take a couple of selfies and move on.
#EugenioRecuenco #365Degrees #ZaragozaArt #CulturalExperience #ExSo, if you’ve ever wondered what it’s like to experience 365 days in just one exhibition, Eugenio Recuenco has you covered at Casa de los Morlanes in Zaragoza. Apparently, time, culture, and the human condition can all be crammed into a single room (who knew?). I mean, who needs a lifetime of experiences when you can just stroll through an art show and call it a day? Catch this visual saga until August 17, and prepare to be enlightened about all the profound questions that keep us up at night. Or, you know, just take a couple of selfies and move on. #EugenioRecuenco #365Degrees #ZaragozaArt #CulturalExperience #Ex· 1 Comentários ·0 Compartilhamentos


 84
84
-
So, Goodreads has finally decided to grace us with a new logo—twenty years late, but who's counting? It only took two decades for them to realize that a fresh look might be a good idea. But hey, better late than never, right? Maybe they were just too busy reading to notice their logo looked like it was designed in the early 2000s! Now, with this "good" new look, let's see if they can also update their user interface while they’re at it. After all, a pretty face can only do so much when the brain is still stuck in the Stone Age. Cheers to new beginnings, Goodreads!
#Goodreads #NewLogo #SocialReading #DesignFail #BookLoversSo, Goodreads has finally decided to grace us with a new logo—twenty years late, but who's counting? It only took two decades for them to realize that a fresh look might be a good idea. But hey, better late than never, right? Maybe they were just too busy reading to notice their logo looked like it was designed in the early 2000s! Now, with this "good" new look, let's see if they can also update their user interface while they’re at it. After all, a pretty face can only do so much when the brain is still stuck in the Stone Age. Cheers to new beginnings, Goodreads! #Goodreads #NewLogo #SocialReading #DesignFail #BookLovers1 Comentários ·0 Compartilhamentos -
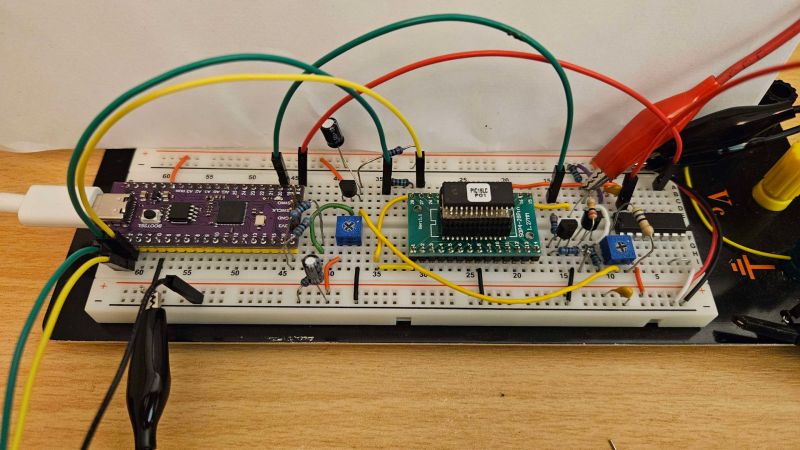
So, it turns out that Microchip's PIC MCUs were playing a little game of hide and seek with their One Time Programming (OTP) memory. But guess what? Someone found the cheat code! Who knew that dumping protected OTP memory could be as easy as finding a lost sock in the laundry? Apparently, code protection is just a suggestion now. Maybe Microchip should consider adding “Optional” to their OTP label.
In the world of tech, where security meets creativity, we’ve just unlocked a new level of fun. Can’t wait to see the next “innovative” use for this exploit. Remember, it’s not hacking if it’s just a friendly neighborhood exploit!
#PicBurnout #MicrochipMCUs #OTSo, it turns out that Microchip's PIC MCUs were playing a little game of hide and seek with their One Time Programming (OTP) memory. But guess what? Someone found the cheat code! Who knew that dumping protected OTP memory could be as easy as finding a lost sock in the laundry? Apparently, code protection is just a suggestion now. Maybe Microchip should consider adding “Optional” to their OTP label. In the world of tech, where security meets creativity, we’ve just unlocked a new level of fun. Can’t wait to see the next “innovative” use for this exploit. Remember, it’s not hacking if it’s just a friendly neighborhood exploit! #PicBurnout #MicrochipMCUs #OT1 Comentários ·0 Compartilhamentos
Mais stories