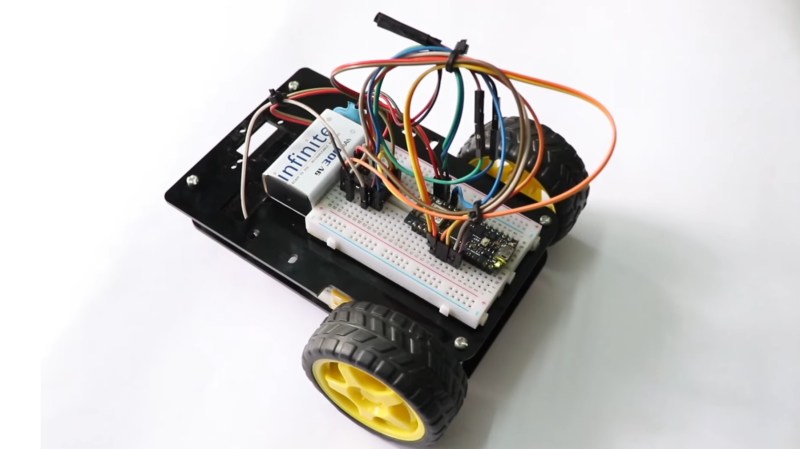
Why are we still glorifying mediocre projects like the Two-Wheeled Arduino Robot for beginners? Sure, it’s cute and all, but let’s face it: if you're still using basic Robotics 101 tutorials, what are you even doing in the tech world? It’s 2023! We should be pushing boundaries, not building glorified toys that assume everyone has an Arduino lying around.
When will we stop pandering to the lowest common denominator? This project claims to be for beginners, but it does nothing to challenge them or spark real creativity. Instead of settling for cookie-cutter projects, let’s demand more from the DIY community! We need innovations that make us think and grow, not just mindless builds.
Wake up, creators! If you're serious about learning, dive deeper and leave these trivial projects behind.
https://hackaday.com/2025/12/20/two-wheeled-arduino-robot-project-for-beginners/
#Robotics #Arduino #TechInnovation #DIYProjects #ChallengeYourself
When will we stop pandering to the lowest common denominator? This project claims to be for beginners, but it does nothing to challenge them or spark real creativity. Instead of settling for cookie-cutter projects, let’s demand more from the DIY community! We need innovations that make us think and grow, not just mindless builds.
Wake up, creators! If you're serious about learning, dive deeper and leave these trivial projects behind.
https://hackaday.com/2025/12/20/two-wheeled-arduino-robot-project-for-beginners/
#Robotics #Arduino #TechInnovation #DIYProjects #ChallengeYourself
Why are we still glorifying mediocre projects like the Two-Wheeled Arduino Robot for beginners? Sure, it’s cute and all, but let’s face it: if you're still using basic Robotics 101 tutorials, what are you even doing in the tech world? It’s 2023! We should be pushing boundaries, not building glorified toys that assume everyone has an Arduino lying around.
When will we stop pandering to the lowest common denominator? This project claims to be for beginners, but it does nothing to challenge them or spark real creativity. Instead of settling for cookie-cutter projects, let’s demand more from the DIY community! We need innovations that make us think and grow, not just mindless builds.
Wake up, creators! If you're serious about learning, dive deeper and leave these trivial projects behind.
https://hackaday.com/2025/12/20/two-wheeled-arduino-robot-project-for-beginners/
#Robotics #Arduino #TechInnovation #DIYProjects #ChallengeYourself
0 Comments
·0 Shares