0 Commentaires
0 Parts
114 Vue

Annuaire
Annuaire
-
Connectez-vous pour aimer, partager et commenter!
-
 WWW.FOXNEWS.COM5 mobile privacy terms you need to know to protect yourselfclose Expert recommends smartphone alternatives for kids and teens this holiday season Ethics and Public Policy fellow Clare Morell explains how parents can choose smartphone alternatives for their children this holiday season on ‘Fox & Friends Weekend.’ Your smartphone might be your closest companion, tracking your steps, saving your passwords and remembering your favorite takeout. But how much do you know about how it protects (or exposes) your privacy?We’re breaking down five key mobile privacy terms that could make all the difference when it comes to keeping your personal info safe. Whether you’re team iPhone or Android, understanding these concepts can help you take control of your digital footprint — right from the palm of your hand.Stay tuned for more in this series as we dive deeper into privacy-related tech terms and other essential concepts, answering the top questions we get from readers like you. STAY PROTECTED & INFORMED! GET SECURITY ALERTS & EXPERT TECH TIPS — SIGN UP FOR KURT’S THE CYBERGUY REPORT NOW A woman working on her laptop (Kurt "CyberGuy" Knutsson)1. Location trackingYour phone’s GPS isn’t just for directionsEvery time you check the weather, tag your location on Instagram or ask Google Maps for the quickest route, you’re sharing your whereabouts. That’s thanks to Location Tracking, a feature built into most apps and devices that uses GPS, Wi-Fi, Bluetooth or cell towers to pinpoint your location.Here’s the catch: Many apps track you even when you’re not using them. Some use this data to serve local content or ads, while others collect and sell it to third parties.How to protect yourself:Check which apps have location access in your settingsSwitch from "Always" to "While Using the App"Consider turning off location services entirely when you don’t need themKnowing when and how you’re being tracked is the first step to stopping it.More: Top 20 apps tracking you every day2. App permissionsWhat your apps know about you (and maybe shouldn't)Before you can use that new photo editor or budgeting tool, it probably asked for a few things — access to your camera, contacts, microphone, maybe even your calendar. These are called App Permissions, and they determine what parts of your phone an app can interact with.WHAT IS ARTIFICIAL INTELLIGENCE (AI)?While some requests are necessary (e.g., a video app needs camera access), others can be excessive or even suspicious. For example, why does a flashlight app need your location or call logs?Tips for staying in control:Review permissions when installing appsRegularly audit your app settingsDelete apps you no longer useYour data shouldn’t be the price of convenience. Set boundaries.More: Did you say ‘yes’ to allowing apps permission to your Google account? A woman looking at her phone while working on her laptop (Kurt "CyberGuy" Knutsson)3. Two-factor authentication (2FA)A second lock on your digital front doorPasswords aren’t perfect. That’s where two-factor authentication (2FA) comes in. It adds an extra layer of protection by requiring two forms of identification before granting access to your account, typically something you know (a password) and something you have (a text code or authentication app).Many major apps and platforms now support 2FA, and enabling it can help block hackers, even if they steal your password.GET FOX BUSINESS ON THE GO BY CLICKING HEREMost common types of 2FA:Text or email codesAuthenticator apps like Google Authenticator or AuthyBiometric verification (fingerprint or face ID)Activate 2FA where you can. It's one of the simplest ways to level up your mobile security.4. Mobile ad IDThe invisible label that tracks your habitsBehind the scenes, your phone is assigned a unique string of numbers and letters called a mobile advertising identifier (Mobile Ad ID). It helps advertisers track your behavior across apps and websites to build a profile of your interests.While it doesn’t include your name, it can be linked to your device and used to serve targeted ads. Think of it as a digital name tag for marketing purposes.Want to opt out? You can:iPhone: Go to Settings > Privacy & Security > TrackingAndroid: Settings > Privacy > Ads, and reset or delete your Ad IDYou’re not obligated to let your phone advertise you.More: How to escape Facebook’s creepy ad tracking A laptop and external storage devices on a desk (Kurt "CyberGuy" Knutsson)5. VPN (virtual private network)Your personal privacy tunnelA VPN is like a secret tunnel for your internet connection. It hides your online activities and helps keep your personal information safe when you’re using the internet, especially on public Wi-Fi.In addition to protecting your information from prying eyes, a VPN also hides your real location. It allows you to connect to the internet through a server in another part of the world, which makes it appear as though you’re browsing from a different location. This is useful for security (protecting your privacy) and for accessing content that might be restricted in certain areas.When you connect to public Wi-Fi at a coffee shop or airport, your data can be exposed to hackers and snoops. That’s where a VPN (virtual private network) comes in. It encrypts your internet traffic and routes it through a secure server, hiding your IP address and protecting your activity.Think of it as a private tunnel for your internet usage, shielding your data from prying eyes.What VPNs are great for:Protecting your connection on public Wi-FiAccessing region-locked contentHiding your online activity from advertisers or your internet providerJust make sure to choose a trustworthy VPN. Some free VPNs may log your data or slow your phone down. A reliable VPN is essential for protecting your online privacy and ensuring a secure, high-speed connection. Kurt’s key takeawaysYour mobile device is powerful, but so are the privacy risks associated with it. By understanding these five mobile privacy terms, you can take simple yet impactful steps to protect your digital life. From turning off unnecessary app permissions to enabling two-factor authentication, these small tweaks can help you stay in control and keep your information safe.CLICK HERE TO GET THE FOX NEWS APPConfused by a mobile tech term or want help tightening up your privacy settings? Drop your questions below. We’ve got more tips coming your way. Let us know by writing us atCyberguy.com/ContactFor more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/NewsletterAsk Kurt a question or let us know what stories you'd like us to coverFollow Kurt on his social channelsAnswers to the most asked CyberGuy questions:New from Kurt:Copyright 2025 CyberGuy.com. All rights reserved. Kurt "CyberGuy" Knutsson is an award-winning tech journalist who has a deep love of technology, gear and gadgets that make life better with his contributions for Fox News & FOX Business beginning mornings on "FOX & Friends." Got a tech question? Get Kurt’s free CyberGuy Newsletter, share your voice, a story idea or comment at CyberGuy.com.0 Commentaires 0 Parts 128 Vue
WWW.FOXNEWS.COM5 mobile privacy terms you need to know to protect yourselfclose Expert recommends smartphone alternatives for kids and teens this holiday season Ethics and Public Policy fellow Clare Morell explains how parents can choose smartphone alternatives for their children this holiday season on ‘Fox & Friends Weekend.’ Your smartphone might be your closest companion, tracking your steps, saving your passwords and remembering your favorite takeout. But how much do you know about how it protects (or exposes) your privacy?We’re breaking down five key mobile privacy terms that could make all the difference when it comes to keeping your personal info safe. Whether you’re team iPhone or Android, understanding these concepts can help you take control of your digital footprint — right from the palm of your hand.Stay tuned for more in this series as we dive deeper into privacy-related tech terms and other essential concepts, answering the top questions we get from readers like you. STAY PROTECTED & INFORMED! GET SECURITY ALERTS & EXPERT TECH TIPS — SIGN UP FOR KURT’S THE CYBERGUY REPORT NOW A woman working on her laptop (Kurt "CyberGuy" Knutsson)1. Location trackingYour phone’s GPS isn’t just for directionsEvery time you check the weather, tag your location on Instagram or ask Google Maps for the quickest route, you’re sharing your whereabouts. That’s thanks to Location Tracking, a feature built into most apps and devices that uses GPS, Wi-Fi, Bluetooth or cell towers to pinpoint your location.Here’s the catch: Many apps track you even when you’re not using them. Some use this data to serve local content or ads, while others collect and sell it to third parties.How to protect yourself:Check which apps have location access in your settingsSwitch from "Always" to "While Using the App"Consider turning off location services entirely when you don’t need themKnowing when and how you’re being tracked is the first step to stopping it.More: Top 20 apps tracking you every day2. App permissionsWhat your apps know about you (and maybe shouldn't)Before you can use that new photo editor or budgeting tool, it probably asked for a few things — access to your camera, contacts, microphone, maybe even your calendar. These are called App Permissions, and they determine what parts of your phone an app can interact with.WHAT IS ARTIFICIAL INTELLIGENCE (AI)?While some requests are necessary (e.g., a video app needs camera access), others can be excessive or even suspicious. For example, why does a flashlight app need your location or call logs?Tips for staying in control:Review permissions when installing appsRegularly audit your app settingsDelete apps you no longer useYour data shouldn’t be the price of convenience. Set boundaries.More: Did you say ‘yes’ to allowing apps permission to your Google account? A woman looking at her phone while working on her laptop (Kurt "CyberGuy" Knutsson)3. Two-factor authentication (2FA)A second lock on your digital front doorPasswords aren’t perfect. That’s where two-factor authentication (2FA) comes in. It adds an extra layer of protection by requiring two forms of identification before granting access to your account, typically something you know (a password) and something you have (a text code or authentication app).Many major apps and platforms now support 2FA, and enabling it can help block hackers, even if they steal your password.GET FOX BUSINESS ON THE GO BY CLICKING HEREMost common types of 2FA:Text or email codesAuthenticator apps like Google Authenticator or AuthyBiometric verification (fingerprint or face ID)Activate 2FA where you can. It's one of the simplest ways to level up your mobile security.4. Mobile ad IDThe invisible label that tracks your habitsBehind the scenes, your phone is assigned a unique string of numbers and letters called a mobile advertising identifier (Mobile Ad ID). It helps advertisers track your behavior across apps and websites to build a profile of your interests.While it doesn’t include your name, it can be linked to your device and used to serve targeted ads. Think of it as a digital name tag for marketing purposes.Want to opt out? You can:iPhone: Go to Settings > Privacy & Security > TrackingAndroid: Settings > Privacy > Ads, and reset or delete your Ad IDYou’re not obligated to let your phone advertise you.More: How to escape Facebook’s creepy ad tracking A laptop and external storage devices on a desk (Kurt "CyberGuy" Knutsson)5. VPN (virtual private network)Your personal privacy tunnelA VPN is like a secret tunnel for your internet connection. It hides your online activities and helps keep your personal information safe when you’re using the internet, especially on public Wi-Fi.In addition to protecting your information from prying eyes, a VPN also hides your real location. It allows you to connect to the internet through a server in another part of the world, which makes it appear as though you’re browsing from a different location. This is useful for security (protecting your privacy) and for accessing content that might be restricted in certain areas.When you connect to public Wi-Fi at a coffee shop or airport, your data can be exposed to hackers and snoops. That’s where a VPN (virtual private network) comes in. It encrypts your internet traffic and routes it through a secure server, hiding your IP address and protecting your activity.Think of it as a private tunnel for your internet usage, shielding your data from prying eyes.What VPNs are great for:Protecting your connection on public Wi-FiAccessing region-locked contentHiding your online activity from advertisers or your internet providerJust make sure to choose a trustworthy VPN. Some free VPNs may log your data or slow your phone down. A reliable VPN is essential for protecting your online privacy and ensuring a secure, high-speed connection. Kurt’s key takeawaysYour mobile device is powerful, but so are the privacy risks associated with it. By understanding these five mobile privacy terms, you can take simple yet impactful steps to protect your digital life. From turning off unnecessary app permissions to enabling two-factor authentication, these small tweaks can help you stay in control and keep your information safe.CLICK HERE TO GET THE FOX NEWS APPConfused by a mobile tech term or want help tightening up your privacy settings? Drop your questions below. We’ve got more tips coming your way. Let us know by writing us atCyberguy.com/ContactFor more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/NewsletterAsk Kurt a question or let us know what stories you'd like us to coverFollow Kurt on his social channelsAnswers to the most asked CyberGuy questions:New from Kurt:Copyright 2025 CyberGuy.com. All rights reserved. Kurt "CyberGuy" Knutsson is an award-winning tech journalist who has a deep love of technology, gear and gadgets that make life better with his contributions for Fox News & FOX Business beginning mornings on "FOX & Friends." Got a tech question? Get Kurt’s free CyberGuy Newsletter, share your voice, a story idea or comment at CyberGuy.com.0 Commentaires 0 Parts 128 Vue -
 WWW.ZDNET.COMThis is the most customizable smart home accessory I didn't know I neededGovee's new Neon Rope Light 2 makes it easy to decorate your home and has quickly become a staple in my household.0 Commentaires 0 Parts 105 Vue
WWW.ZDNET.COMThis is the most customizable smart home accessory I didn't know I neededGovee's new Neon Rope Light 2 makes it easy to decorate your home and has quickly become a staple in my household.0 Commentaires 0 Parts 105 Vue -
 WWW.FORBES.COMRenewing The Mandate To Safeguard The Energy GridAbstract network wave and a glowing blue and orange particle data on dark background.getty Protection of the energy grid, or "the Grid," will be an issue of significant interest during the second Trump Administration. According to President Trump, he intends to prioritize national security concerns while investing in modernizing and enhancing America’s energy infrastructure. He also understood the significance of safeguarding vital infrastructure against electromagnetic pulses (EMPs) and other dangers during his first term in office. Three main regions constitute the U.S. energy grid: the Texas Interconnected System, the Western Interconnection, which spans the Pacific Ocean to the Rocky Mountain states, and the Eastern Interconnection, which serves states east of the mountains. The Grid, an essential piece of infrastructure, consists of a network of over 7,000 power plants connected by hundreds of thousands of miles of high-voltage transmission lines. According to estimates, there are thousands of power-generating units and 70,000 transformer power substations. Even with the addition of automation and emerging technologies recently, the grid still relies heavily on older tech. 60% of circuit breakers are older than 30 years, while 70% of transmission lines are at least 30 years old, meaning they are nearing the end of their useful lifespans. As a result of the aging infrastructure and rising power consumption, the Grid is now more vulnerable to cascading failures, in which the failure of one component triggers a chain reaction of failures. The growth and expansion of data centers in itself is straining the Grid. Research by the Lawrence Berkeley National Laboratory for the Department of Energy shows that data centers’ power consumption has tripled in the last ten years and may triple again by 2028. John Moura, Director of Reliability Assessment and System Analysis for the North American Electricity Reliability Corporation (NERC) told Reuters that the grid is not built to handle the loss of 1,500-megawatt data centers as they get larger and use more electricity. "Unless we add additional grid resources, it will eventually grow too big to handle." The fundamental truth is that the infrastructure of the US power grid is too outdated to handle the new era of data and growing computational needs. It is also highly susceptible to cyberattacks, EMP, natural disasters, and physical threats, all of which could have disastrous results. The reality of the ecosystem is that the Grid is essential for medical care, food and agriculture, water, data centers, telecommunications, stock exchanges, satellite ground systems, and other important infrastructure. RISKS TO THE GRIDhigh voltage post.High-voltage tower sky background.getty The power grid faces a wide range of risks. EMPs from geomagnetic solar flares, short-range missiles fired by terrorists or nation-states, cyberattacks, or physical attacks on utilities or power facilities are all examples of the risk landscape.Solar flares, which originate from storms on the Sun, constitute a persistent menace. Earth is believed to have experienced more than 100 solar storms in the last 150 years. Strong flares release particles of electromagnetic radiation that are aimed toward Earth and other planets in the solar system. The size of the flare, the scale of the coronal mass ejection, and the speed at which it moves from the Sun to Earth all affect how severe a solar storm is. The electrical grid can sustain serious damage from a type of flare known as an X-class flare. It is impossible to overlook the risk. An EMP attack could also be directed. An EMP strike could be carried out by a terrorist organization or rogue state that detonated a nuclear bomb far above the atmosphere, destroying electronics and the electrical grid. Former CIA Director James Woolsey testified before a House committee and said that if the US received an EMP attack, “two-thirds of the US population would likely perish from starvation, disease, and societal breakdown.” "Natural EMP from a geomagnetic superstorm, like the 1859 Carrington Event or 1921 Railroad Storm, and nuclear EMP attack from terrorists or rogue states, as practiced by North Korea during the nuclear crisis of 2013, are both existential threats that could kill 9 of 10 Americans through starvation, disease, and societal collapse," said the late Dr. Peter Pry, executive director of the Task Force on National and Homeland Security and a member of the Congressional EMP Commission. The Department of Homeland Security (DHS), which acknowledges that hackers have targeted US public utilities control systems, partially protects The Grid. Many of the Supervisory Control and Data Acquisition (SCADA) networks used by power companies to manage their industrial systems need to be updated and strengthened to withstand the increasing dangers of cybersecurity. The Russian cyberattack against Ukraine's power grid, which left 700,000 people without power, served as a reminder of the vulnerabilities in the electric grid. Countries need to step up their efforts to prevent cyberattacks on nuclear and other energy systems, according to the World Energy Council. They observe that the frequency, complexity, and expenses of data breaches are rising. The whole U.S. power system and other vital infrastructure might be taken down by a cyberattack launched by multiple nations, according to retired Admiral Mike Rodgers, a former leader of the National Security Agency (NSA) and U.S. Cyber Command. A successful ransomware attack on the Colonial Pipeline in 2021 offered insight into that vulnerability and the numerous attack points. In addition to disrupting the oil supply of the US East Coast, the attackers showed that there was no cybersecurity structure in place for event response and preparation. The majority of the vital infrastructure components of the U.S. energy grid now function in an internet-accessible digital environment. The trends of hardware and software integration, along with the expansion of networked sensors, are redefining hackers’ opportunities for surface attacks. Both industry and the government have identified the vulnerabilities for cyberattacks. The U.S. energy grid is susceptible to cyberattacks, according to the General Accounting Office (GAO). The grid distribution systems, which transport power from transmission systems to customers, have become increasingly vulnerable, according to the GAO, partly because of the growing capabilities of technologies that enable remote access and linkages to business networks. Threat actors might be able to access those systems as a result, thereby interfering with operations.The reality is that artificial intelligence tools are enabling increasingly sophisticated cyberattacks. Criminal groups, state actors, and other entities are also targeting energy-critical infrastructure. The use of operational technology and the industrial internet of things has increased the attack surface. To combat cyber risks, energy infrastructure operators should use "security by design." Building agile systems with operational cyber-fusion is required by design for cybersecurity to monitor, identify, and react to new threats. Ultimately, we need to enhance the cybersecurity of the U.S. energy grid. Another worry is the physical threat posed to the Grid by malevolent acts, particularly by terrorists. A bomb and an incendiary device placed atop a 50,000-gallon fuel tank were used to target and assault a power facility in Nogales, Arizona, a decade ago. Fortunately, the endeavor was unsuccessful. Recently, other terrorist acts by extremist groups have targeted utilities with gunfire and bomb threats. Strategies To Help Protect the GridWire mesh security shield showing up from a huge wave pattern network.getty There are various ways to lessen threats to the energy infrastructure from physical, existential, and cyber sources. These include spreading out energy sources and using smaller, independent networks; systems to stabilize voltage and devices to manage energy flow; setting better security rules, training, and emergency plans; protecting the grid from power surges and voltage issues; and creating ways to share information about weaknesses and threats. To restore power for various emergencies, systematic resilience planning is also essential. For instance, we should upgrade and replace outdated infrastructure with cutting-edge technology like automation systems, smart meters, and sensors to improve grid efficiency and dependability. Additionally, we should set up independent microgrids on a smaller scale, which can function independently or in tandem with the main grid, to supply localized electricity during emergencies or outages. Cyberattacks are becoming increasingly sophisticated thanks to artificial intelligence tools. Additionally, governmental actors, criminal gangs, and other assailants are targeting vital infrastructure related to energy. Operators of energy infrastructure should use "security by design" to combat cyber threats since connectivity brought about by the introduction of operational technology and the industrial internet of things has further increased the attack surface. For cybersecurity to be able to monitor, identify, and react to new threats, it is necessary to construct agile systems with operational cyber-fusion. Ultimately, we need to significantly improve the cybersecurity of the U.S. energy grid to withstand growing threats.Illustration of a coronal mass ejection impacting the Earth s atmosphere. These events, CMEs for ... More short, are powerful releases of solar charged particles (plasma) and magnetic field, travelling on the solar wind. When a CME hits Earth, it can cause a geomagnetic storm which disrupts the planet s magnetosphere, our radio transmissions and electrical power lines. They can damage artificial satellites and cause long-lasting power outages. Humans in orbit are also very vulnerable to these events, whose high-energy particles are not shield by typical spacecraft.getty The threat of an EMP is existential and will require more planning and resilience. President Trump signed Executive Order (E.O.) 13865, “Coordinating National Resilience to Electromagnetic Pulses,” on March 26, 2019, making it a national priority program to set resilience and security standards for vital infrastructure in the United States. E.O. 13865 states, “An electromagnetic pulse (EMP) has the potential to disrupt, degrade, and damage technology and critical infrastructure systems. Human-made or naturally occurring EMPs can affect large geographic areas, disrupting elements critical to the nation’s security and economic prosperity, and could adversely affect global commerce and stability. The federal government must foster sustainable, efficient, and cost-effective approaches to improving the nation’s resilience to the effects of EMPs.” Electromagnetic Pulse (EMP) Programs Status Report In an article, “Cost Analysis: Protecting The Grid and Electronics from EMP,” the authors proposed that a National Resilience Task Force, supported by the U.S. Department of Defense (Northern Command and the National Guard), the Department of Homeland Security, and the Department of Energy, could undertake a mitigation strategy to protect the U.S. critical infrastructure from the effects of an EMP. This effort could include the following actions: Protect electronic equipment by enclosing sensitive electronics in grounded conductive housings and by adding EMP surge arresters to generators, transformers, motors, and critical electronic equipment. Install neutral ground blockers on transformers in substations to prevent ground-induced currents from entering the transformers. Install EMP-protected microgrids with on-site power generation at critical infrastructure facilities. Develop EMP-resistant electronics, such as optical computing and carbon nanotube memory, that are less susceptible to an EMP attack. Include EMP-attack planning scenarios in emergency preparedness training. By planning for the consequences of an EMP attack, communities could develop plans and measures to maintain essential services. Source: Cost Analysis: Protecting the Grid and Electronics from an EMP - Domestic Preparedness To restore power for various emergencies, comprehensive resilience planning is essential. Current technologies can protect the Grid, requiring only leadership and investment to reduce vulnerabilities. The leadership for resolving the electric grid problem is going to come from the incoming administration. Since the majority of the country’s vital infrastructure—such as the banking, healthcare, transportation, and communications systems—is owned by the private sector, it is reliant on the Grid. Co-investment, solid public-private sector partnerships, and cooperation in research, development, and prototyping will all be necessary to find answers.Such collaboration must involve a faster effort to finance and develop innovative technologies that can shield utilities from man-made or natural electromagnetic surges, further secure SCADA network hardware and software from cyberattacks, and improve the Grid's physical security. The investment in preserving civilization is worth it, even though estimates of costs vary. As more people become conscious of the precarious threat landscape and the consequences of inaction, there has been an increasing need for safeguarding The Grid. This heightened consciousness implies a need to act quickly and a mandate to support the incoming administration.0 Commentaires 0 Parts 106 Vue
WWW.FORBES.COMRenewing The Mandate To Safeguard The Energy GridAbstract network wave and a glowing blue and orange particle data on dark background.getty Protection of the energy grid, or "the Grid," will be an issue of significant interest during the second Trump Administration. According to President Trump, he intends to prioritize national security concerns while investing in modernizing and enhancing America’s energy infrastructure. He also understood the significance of safeguarding vital infrastructure against electromagnetic pulses (EMPs) and other dangers during his first term in office. Three main regions constitute the U.S. energy grid: the Texas Interconnected System, the Western Interconnection, which spans the Pacific Ocean to the Rocky Mountain states, and the Eastern Interconnection, which serves states east of the mountains. The Grid, an essential piece of infrastructure, consists of a network of over 7,000 power plants connected by hundreds of thousands of miles of high-voltage transmission lines. According to estimates, there are thousands of power-generating units and 70,000 transformer power substations. Even with the addition of automation and emerging technologies recently, the grid still relies heavily on older tech. 60% of circuit breakers are older than 30 years, while 70% of transmission lines are at least 30 years old, meaning they are nearing the end of their useful lifespans. As a result of the aging infrastructure and rising power consumption, the Grid is now more vulnerable to cascading failures, in which the failure of one component triggers a chain reaction of failures. The growth and expansion of data centers in itself is straining the Grid. Research by the Lawrence Berkeley National Laboratory for the Department of Energy shows that data centers’ power consumption has tripled in the last ten years and may triple again by 2028. John Moura, Director of Reliability Assessment and System Analysis for the North American Electricity Reliability Corporation (NERC) told Reuters that the grid is not built to handle the loss of 1,500-megawatt data centers as they get larger and use more electricity. "Unless we add additional grid resources, it will eventually grow too big to handle." The fundamental truth is that the infrastructure of the US power grid is too outdated to handle the new era of data and growing computational needs. It is also highly susceptible to cyberattacks, EMP, natural disasters, and physical threats, all of which could have disastrous results. The reality of the ecosystem is that the Grid is essential for medical care, food and agriculture, water, data centers, telecommunications, stock exchanges, satellite ground systems, and other important infrastructure. RISKS TO THE GRIDhigh voltage post.High-voltage tower sky background.getty The power grid faces a wide range of risks. EMPs from geomagnetic solar flares, short-range missiles fired by terrorists or nation-states, cyberattacks, or physical attacks on utilities or power facilities are all examples of the risk landscape.Solar flares, which originate from storms on the Sun, constitute a persistent menace. Earth is believed to have experienced more than 100 solar storms in the last 150 years. Strong flares release particles of electromagnetic radiation that are aimed toward Earth and other planets in the solar system. The size of the flare, the scale of the coronal mass ejection, and the speed at which it moves from the Sun to Earth all affect how severe a solar storm is. The electrical grid can sustain serious damage from a type of flare known as an X-class flare. It is impossible to overlook the risk. An EMP attack could also be directed. An EMP strike could be carried out by a terrorist organization or rogue state that detonated a nuclear bomb far above the atmosphere, destroying electronics and the electrical grid. Former CIA Director James Woolsey testified before a House committee and said that if the US received an EMP attack, “two-thirds of the US population would likely perish from starvation, disease, and societal breakdown.” "Natural EMP from a geomagnetic superstorm, like the 1859 Carrington Event or 1921 Railroad Storm, and nuclear EMP attack from terrorists or rogue states, as practiced by North Korea during the nuclear crisis of 2013, are both existential threats that could kill 9 of 10 Americans through starvation, disease, and societal collapse," said the late Dr. Peter Pry, executive director of the Task Force on National and Homeland Security and a member of the Congressional EMP Commission. The Department of Homeland Security (DHS), which acknowledges that hackers have targeted US public utilities control systems, partially protects The Grid. Many of the Supervisory Control and Data Acquisition (SCADA) networks used by power companies to manage their industrial systems need to be updated and strengthened to withstand the increasing dangers of cybersecurity. The Russian cyberattack against Ukraine's power grid, which left 700,000 people without power, served as a reminder of the vulnerabilities in the electric grid. Countries need to step up their efforts to prevent cyberattacks on nuclear and other energy systems, according to the World Energy Council. They observe that the frequency, complexity, and expenses of data breaches are rising. The whole U.S. power system and other vital infrastructure might be taken down by a cyberattack launched by multiple nations, according to retired Admiral Mike Rodgers, a former leader of the National Security Agency (NSA) and U.S. Cyber Command. A successful ransomware attack on the Colonial Pipeline in 2021 offered insight into that vulnerability and the numerous attack points. In addition to disrupting the oil supply of the US East Coast, the attackers showed that there was no cybersecurity structure in place for event response and preparation. The majority of the vital infrastructure components of the U.S. energy grid now function in an internet-accessible digital environment. The trends of hardware and software integration, along with the expansion of networked sensors, are redefining hackers’ opportunities for surface attacks. Both industry and the government have identified the vulnerabilities for cyberattacks. The U.S. energy grid is susceptible to cyberattacks, according to the General Accounting Office (GAO). The grid distribution systems, which transport power from transmission systems to customers, have become increasingly vulnerable, according to the GAO, partly because of the growing capabilities of technologies that enable remote access and linkages to business networks. Threat actors might be able to access those systems as a result, thereby interfering with operations.The reality is that artificial intelligence tools are enabling increasingly sophisticated cyberattacks. Criminal groups, state actors, and other entities are also targeting energy-critical infrastructure. The use of operational technology and the industrial internet of things has increased the attack surface. To combat cyber risks, energy infrastructure operators should use "security by design." Building agile systems with operational cyber-fusion is required by design for cybersecurity to monitor, identify, and react to new threats. Ultimately, we need to enhance the cybersecurity of the U.S. energy grid. Another worry is the physical threat posed to the Grid by malevolent acts, particularly by terrorists. A bomb and an incendiary device placed atop a 50,000-gallon fuel tank were used to target and assault a power facility in Nogales, Arizona, a decade ago. Fortunately, the endeavor was unsuccessful. Recently, other terrorist acts by extremist groups have targeted utilities with gunfire and bomb threats. Strategies To Help Protect the GridWire mesh security shield showing up from a huge wave pattern network.getty There are various ways to lessen threats to the energy infrastructure from physical, existential, and cyber sources. These include spreading out energy sources and using smaller, independent networks; systems to stabilize voltage and devices to manage energy flow; setting better security rules, training, and emergency plans; protecting the grid from power surges and voltage issues; and creating ways to share information about weaknesses and threats. To restore power for various emergencies, systematic resilience planning is also essential. For instance, we should upgrade and replace outdated infrastructure with cutting-edge technology like automation systems, smart meters, and sensors to improve grid efficiency and dependability. Additionally, we should set up independent microgrids on a smaller scale, which can function independently or in tandem with the main grid, to supply localized electricity during emergencies or outages. Cyberattacks are becoming increasingly sophisticated thanks to artificial intelligence tools. Additionally, governmental actors, criminal gangs, and other assailants are targeting vital infrastructure related to energy. Operators of energy infrastructure should use "security by design" to combat cyber threats since connectivity brought about by the introduction of operational technology and the industrial internet of things has further increased the attack surface. For cybersecurity to be able to monitor, identify, and react to new threats, it is necessary to construct agile systems with operational cyber-fusion. Ultimately, we need to significantly improve the cybersecurity of the U.S. energy grid to withstand growing threats.Illustration of a coronal mass ejection impacting the Earth s atmosphere. These events, CMEs for ... More short, are powerful releases of solar charged particles (plasma) and magnetic field, travelling on the solar wind. When a CME hits Earth, it can cause a geomagnetic storm which disrupts the planet s magnetosphere, our radio transmissions and electrical power lines. They can damage artificial satellites and cause long-lasting power outages. Humans in orbit are also very vulnerable to these events, whose high-energy particles are not shield by typical spacecraft.getty The threat of an EMP is existential and will require more planning and resilience. President Trump signed Executive Order (E.O.) 13865, “Coordinating National Resilience to Electromagnetic Pulses,” on March 26, 2019, making it a national priority program to set resilience and security standards for vital infrastructure in the United States. E.O. 13865 states, “An electromagnetic pulse (EMP) has the potential to disrupt, degrade, and damage technology and critical infrastructure systems. Human-made or naturally occurring EMPs can affect large geographic areas, disrupting elements critical to the nation’s security and economic prosperity, and could adversely affect global commerce and stability. The federal government must foster sustainable, efficient, and cost-effective approaches to improving the nation’s resilience to the effects of EMPs.” Electromagnetic Pulse (EMP) Programs Status Report In an article, “Cost Analysis: Protecting The Grid and Electronics from EMP,” the authors proposed that a National Resilience Task Force, supported by the U.S. Department of Defense (Northern Command and the National Guard), the Department of Homeland Security, and the Department of Energy, could undertake a mitigation strategy to protect the U.S. critical infrastructure from the effects of an EMP. This effort could include the following actions: Protect electronic equipment by enclosing sensitive electronics in grounded conductive housings and by adding EMP surge arresters to generators, transformers, motors, and critical electronic equipment. Install neutral ground blockers on transformers in substations to prevent ground-induced currents from entering the transformers. Install EMP-protected microgrids with on-site power generation at critical infrastructure facilities. Develop EMP-resistant electronics, such as optical computing and carbon nanotube memory, that are less susceptible to an EMP attack. Include EMP-attack planning scenarios in emergency preparedness training. By planning for the consequences of an EMP attack, communities could develop plans and measures to maintain essential services. Source: Cost Analysis: Protecting the Grid and Electronics from an EMP - Domestic Preparedness To restore power for various emergencies, comprehensive resilience planning is essential. Current technologies can protect the Grid, requiring only leadership and investment to reduce vulnerabilities. The leadership for resolving the electric grid problem is going to come from the incoming administration. Since the majority of the country’s vital infrastructure—such as the banking, healthcare, transportation, and communications systems—is owned by the private sector, it is reliant on the Grid. Co-investment, solid public-private sector partnerships, and cooperation in research, development, and prototyping will all be necessary to find answers.Such collaboration must involve a faster effort to finance and develop innovative technologies that can shield utilities from man-made or natural electromagnetic surges, further secure SCADA network hardware and software from cyberattacks, and improve the Grid's physical security. The investment in preserving civilization is worth it, even though estimates of costs vary. As more people become conscious of the precarious threat landscape and the consequences of inaction, there has been an increasing need for safeguarding The Grid. This heightened consciousness implies a need to act quickly and a mandate to support the incoming administration.0 Commentaires 0 Parts 106 Vue -
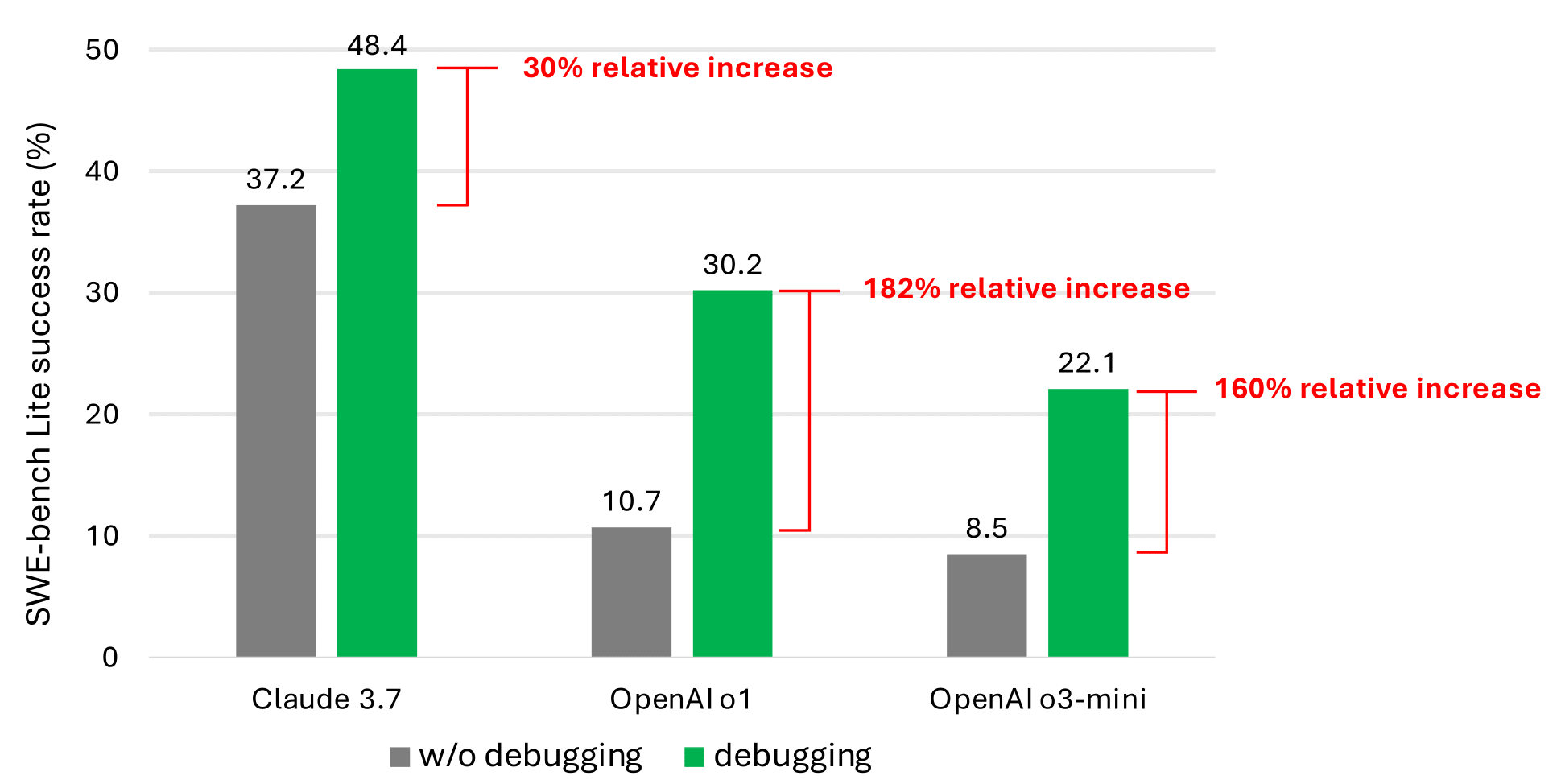 WWW.TECHSPOT.COMMicrosoft research shows AI coding tools fall short in key debugging tasksIn context: Some industry experts boldly claim that generative AI will soon replace human software developers. With tools like GitHub Copilot and AI-driven "vibe" coding startups, it may seem that AI has already significantly impacted software engineering. However, a new study suggests that AI still has a long way to go before replacing human programmers. The Microsoft Research study acknowledges that while today's AI coding tools can boost productivity by suggesting examples, they are limited in actively seeking new information or interacting with code execution when these solutions fail. However, human developers routinely perform these tasks when debugging, highlighting a significant gap in AI's capabilities. Microsoft introduced a new environment called debug-gym to explore and address these challenges. This platform allows AI models to debug real-world codebases using tools similar to those developers use, enabling the information-seeking behavior essential for effective debugging. Microsoft tested how well a simple AI agent, built with existing language models, could debug real-world code using debug-gym. While the results were promising, they were still limited. Despite having access to interactive debugging tools, the prompt-based agents rarely solved more than half of the tasks in benchmarks. That's far from the level of competence needed to replace human engineers. The research identifies two key issues at play. First, the training data for today's LLMs lacks sufficient examples of the decision-making behavior typical in real debugging sessions. Second, these models are not yet fully capable of utilizing debugging tools to their full potential. "We believe this is due to the scarcity of data representing sequential decision-making behavior (e.g., debugging traces) in the current LLM training corpus," the researchers said. // Related Stories Of course, artificial intelligence is advancing rapidly. Microsoft believes that language models can become much more capable debuggers with the right focused training approaches over time. One approach the researchers suggest is creating specialized training data focused on debugging processes and trajectories. For example, they propose developing an "info-seeking" model that gathers relevant debugging context and passes it on to a larger code generation model. The broader findings align with previous studies, showing that while artificial intelligence can occasionally generate seemingly functional applications for specific tasks, the resulting code often contains bugs and security vulnerabilities. Until artificial intelligence can handle this core function of software development, it will remain an assistant – not a replacement.0 Commentaires 0 Parts 122 Vue
WWW.TECHSPOT.COMMicrosoft research shows AI coding tools fall short in key debugging tasksIn context: Some industry experts boldly claim that generative AI will soon replace human software developers. With tools like GitHub Copilot and AI-driven "vibe" coding startups, it may seem that AI has already significantly impacted software engineering. However, a new study suggests that AI still has a long way to go before replacing human programmers. The Microsoft Research study acknowledges that while today's AI coding tools can boost productivity by suggesting examples, they are limited in actively seeking new information or interacting with code execution when these solutions fail. However, human developers routinely perform these tasks when debugging, highlighting a significant gap in AI's capabilities. Microsoft introduced a new environment called debug-gym to explore and address these challenges. This platform allows AI models to debug real-world codebases using tools similar to those developers use, enabling the information-seeking behavior essential for effective debugging. Microsoft tested how well a simple AI agent, built with existing language models, could debug real-world code using debug-gym. While the results were promising, they were still limited. Despite having access to interactive debugging tools, the prompt-based agents rarely solved more than half of the tasks in benchmarks. That's far from the level of competence needed to replace human engineers. The research identifies two key issues at play. First, the training data for today's LLMs lacks sufficient examples of the decision-making behavior typical in real debugging sessions. Second, these models are not yet fully capable of utilizing debugging tools to their full potential. "We believe this is due to the scarcity of data representing sequential decision-making behavior (e.g., debugging traces) in the current LLM training corpus," the researchers said. // Related Stories Of course, artificial intelligence is advancing rapidly. Microsoft believes that language models can become much more capable debuggers with the right focused training approaches over time. One approach the researchers suggest is creating specialized training data focused on debugging processes and trajectories. For example, they propose developing an "info-seeking" model that gathers relevant debugging context and passes it on to a larger code generation model. The broader findings align with previous studies, showing that while artificial intelligence can occasionally generate seemingly functional applications for specific tasks, the resulting code often contains bugs and security vulnerabilities. Until artificial intelligence can handle this core function of software development, it will remain an assistant – not a replacement.0 Commentaires 0 Parts 122 Vue -
 WWW.DIGITALTRENDS.COMThe Microsoft Surface Pro 11 is almost $400 off — down to $830If you’re thinking about buying a new device for the primary purpose of accessing Microsoft’s Copilot, we can’t recommend the Microsoft Surface Pro 11 enough. It’s an even more tempting purchase right now because it’s available from Walmart for just $830, for savings of $369 on its original price of $1,199. We’re not entirely sure how much longer stock will be available, but since past Surface Pro deals expired pretty quickly, we recommend completing your transaction as soon as you can to make sure you don’t miss out. The “spectacular” Microsoft Surface Pro 11 received 4.5 stars out of 5 in our review, where we also described it as “the best Surface Pro ever made.” It all begins with its great performance, powered by the Qualcomm Snapdragon X Elite processor and 16GB of RAM. With these specifications and Windows 11 Home pre-installed, the Microsoft Surface Pro 11 is a designated Copilot+ PC that’s built to take advantage of the capabilities of Microsoft’s Copilot. You’ll be able to access the AI assistant on the go, as the device’s battery can last up to 14 hours on a single charge. The Microsoft Surface Pro 11 features a gorgeous 13-inch OLED touchscreen with 2880 x 1920 resolution, and it has a 180-degree kickstand at the back for when you need to prop it up while using it. It’s also our top pick among the best 2-in-1 laptops, but in order to transform the Microsoft Surface Pro 11 from a tablet to a laptop, you’ll have to buy the Surface Pro keyboard, which is sold separately. Related The Microsoft Surface Pro 11 is a powerful device with Microsoft’s Copilot, and it’s currently on sale from Walmart at $369 off. From a sticker price of $1,199, it’s down to only $830, but probably not for long. There’s a chance that it’s back to its regular price as soon as tomorrow, so if you want to pocket the savings when buying the Microsoft Surface Pro 11, you’re going to have to push through with your purchase immediately. Editors’ Recommendations0 Commentaires 0 Parts 111 Vue
WWW.DIGITALTRENDS.COMThe Microsoft Surface Pro 11 is almost $400 off — down to $830If you’re thinking about buying a new device for the primary purpose of accessing Microsoft’s Copilot, we can’t recommend the Microsoft Surface Pro 11 enough. It’s an even more tempting purchase right now because it’s available from Walmart for just $830, for savings of $369 on its original price of $1,199. We’re not entirely sure how much longer stock will be available, but since past Surface Pro deals expired pretty quickly, we recommend completing your transaction as soon as you can to make sure you don’t miss out. The “spectacular” Microsoft Surface Pro 11 received 4.5 stars out of 5 in our review, where we also described it as “the best Surface Pro ever made.” It all begins with its great performance, powered by the Qualcomm Snapdragon X Elite processor and 16GB of RAM. With these specifications and Windows 11 Home pre-installed, the Microsoft Surface Pro 11 is a designated Copilot+ PC that’s built to take advantage of the capabilities of Microsoft’s Copilot. You’ll be able to access the AI assistant on the go, as the device’s battery can last up to 14 hours on a single charge. The Microsoft Surface Pro 11 features a gorgeous 13-inch OLED touchscreen with 2880 x 1920 resolution, and it has a 180-degree kickstand at the back for when you need to prop it up while using it. It’s also our top pick among the best 2-in-1 laptops, but in order to transform the Microsoft Surface Pro 11 from a tablet to a laptop, you’ll have to buy the Surface Pro keyboard, which is sold separately. Related The Microsoft Surface Pro 11 is a powerful device with Microsoft’s Copilot, and it’s currently on sale from Walmart at $369 off. From a sticker price of $1,199, it’s down to only $830, but probably not for long. There’s a chance that it’s back to its regular price as soon as tomorrow, so if you want to pocket the savings when buying the Microsoft Surface Pro 11, you’re going to have to push through with your purchase immediately. Editors’ Recommendations0 Commentaires 0 Parts 111 Vue -
WWW.WSJ.COM‘Enough Is Enuf’ Review: A Dream of Simpler SpellingGeorge Bernard Shaw, Theodore Roosevelt, Andrew Carnegie and others have lobbied to reform English spelling. The language has been resistant.0 Commentaires 0 Parts 113 Vue
-
WWW.BUSINESSINSIDER.COMMy husband thought he'd hate Disney World — but I won him over by planning the perfect adults-only tripI work as the editor for a magazine about Disney World, so I'm at the parks at least four or five times a year (for work, I swear!).Every time I've gone, I've asked my husband, Trent, to join me, but he's always said no.He'd say Disney isn't for him as he's not a huge fan of the movies, he gets severe motion sickness on the tamest of rides, and he hates big crowds. However, I was convinced I could plan a trip to win him over if only he'd give me a chance.Earlier this year, we finally went together — and he loved it. Here's the adults-only trip that sealed the deal. I made sure we had a sit-down meal at a nice restaurant at least once a day. We watched animals roam by Animal Kingdom Lodge after our meal at Sanaa. Timothy Moore When I travel to Disney World for work, I'm always on the go, chasing stories and trying to cram in as many experiences as possible. That means my meals are usually quick Dole Whips and pretzels while standing in line.However, to win Trent over, I decided to slow down and indulge in some of Disney World's best dining.We visited at least one sit-down restaurant a day and stayed far away from character dining and buffets, where the food is usually an afterthought.One of our favorite meals was at Sanaa, where we got the world-famous bread service and then watched animals roaming the safari at Animal Kingdom Lodge.We also got a fancy dinner at Toledo, a steakhouse at the top of Gran Destino Tower, and a massive brunch at Chef Art Smith's Homecomin'. We geeked out on a behind-the-scenes tour of Epcot's greenhouses. The Behind the Seeds tour was fairly affordable and relaxing. Timothy Moore Disney offers a lot of cool backstage tours, but one of the nerdiest (and cheapest at under $50 a person) is the Behind the Seeds Tour at Epcot's Land Pavilion.For about an hour, a knowledgeable scientist took us on a small group tour of all the greenhouses, and we learned about the innovative ways Disney grows food and manages pests.Although the tour isn't adults-only, the subject matter might be a little dry for little ones — and we didn't see many kids here when we went.If you're on an adults-only trip, this tour could be a great way to get a break from the screaming toddlers around the parks. World Showcase was a great place to spend our time. We had fun walking around World Showcase and its many pavilions. Timothy Moore It's no secret that World Showcase is the best place for 21-and-over fun at Disney World, and Trent and I definitely ordered a few drinks from the different pavilions.However, as history buffs, we also enjoyed touring World Showcase beyondWe stopped by each country pavilion's museum and enjoyed live entertainment from the Voices of Liberty at the American Adventure Pavilion and the taiko drummers at the Japan Pavilion. Our itinerary had plenty of room for naps and downtime. We'd rest for a bit before heading back to the parks at night. Timothy Moore When I do Disney alone, I'm a rope-drop-to-kiss-goodnight kinda guy, with no breaks in between. I love being at the parks from open to close, but I knew Trent would get burned out if we attempted that.So I followed the advice I usually give parents with little kids: Take a midday break back at the hotel.We'd nap, grab drinks at the pool bar, and even read in a hammock. Then, refreshed, we'd head back to the parks in the evening. We took a sangria class and went bar-hopping with friends. The sangria class was fun. Timothy Moore Coronado Springs Resort has a sangria class on weekends where you get to sample different types of sangria and concoct your own. This was a huge hit with Trent.We also bar-hopped around Disney Springs with friends and went to the BoardWalk area's dueling piano bar, Jellyrolls, with some of my coworkers. (Jellyrolls is set to close later this month, unfortunately). Plus, we made sure to stop at some of my favorite quiet spots at Disney World. Tom Sawyer Island may not be around for much longer. Timothy Moore I get overwhelmed by large groups and loud noises, so I have a few favorite spots around the parks where I go to cool off and decompress.I really liked sharing my favorite secret spots in Disney with Trent, who also doesn't do well in crowds. My favorite is Tom Sawyer Island, which is unfortunately set to be replaced with "Cars" attractions this year.I also took him to the koi pond in Epcot's Japan Pavilion to decompress, the patio of BaseLine Tap House to people watch with beers, and the Discovery Island Trail at Animal Kingdom to go on a quiet walk.Having some spaces all to ourselves at Disney World made the experience more magical. Lastly, we focused on shows instead of big attractions. We saw "Festival of the Lion King" with friends Timothy Moore Because Trent experiences severe motion sickness, we couldn't do too many rides. Haunted Mansion and Spaceship Earth were OK, but even something like Soarin' or Rise of the Resistance would've been too much for him.Fortunately, this meant we weren't stressed about waiting in long lines to get on rides or managing Lightning Lane passes to try to skip them. Instead, we simply walked around and enjoyed the theming of each park.We also spent a lot of time watching shows — and there are a lot of good ones at Disney. Our favorites included the "Indiana Jones Epic Stunt Spectacular," "Festival of the Lion King," and, of course, "Fantasmic."0 Commentaires 0 Parts 108 Vue
-
 WWW.VOX.COMThe far-reaching effects of Trump’s tariffs on low-income people, explainedPresident Donald Trump’s tariff plan has rattled Wall Street, alarmed the United States’ trading partners, and made Americans afraid of checking their retirement accounts. It’s also been extremely confusing: After announcing that he would implement steep tariffs across the board (for reasons that didn’t make much sense), Trump walked back some of the tariffs before they were set to go into effect. However, he is still waging a trade war with China, and the tariff rates on many other countries remain much higher than they were before this whole saga began.Throughout this, Trump and his allies have suggested that while the tariffs are hurting Wall Street, they’re going to have a positive effect for small businesses on “Main Street.” The logic is that it’s only the wealthy who own stocks and have 401(k)s, and are therefore feeling the pain of the plunging market. But that’s not true, and it’s not just Wall Street that will suffer from these tariffs. That’s not because tariffs are always bad. As I wrote last week, tariffs can be used for good if implemented narrowly and strategically to help prop up certain industries, which is why some unions support the idea of harsher tariffs. But Trump’s plan is far too broad, and it’s unclear what he even hopes to achieve with them. In reality, the people who will be most affected by Trump’s tariffs are poor people. That’s true for low-wage workers who might lose jobs in developing countries around the world as factories downsize or close because of the negative effect of tariffs on trade. It’s also true for low-income families in the United States, for at least two reasons.How Trump’s tariffs will hurt low-income AmericansThere are two ways the tariffs will hurt people with low incomes:The first and most obvious impact of Trump’s tariffs is that they will raise prices on everyday goods. Tariffs act as a consumption tax — a levy that people ultimately pay at the checkout counter because businesses will likely raise their prices to offset their tariff bills. Unlike income taxes, which are adjusted based on how much a household makes, everyone will pay the same rate on the same good. According to the Budget Lab at Yale University, which analyzed the impact of the original tariffs Trump announced over a week ago, the average American household would be levied about $3,800. For the lowest income households, the tariff-imposed cost-of-living increase is lower — about $1,700 — in part because their overall spending is lower.But they will still pay a larger share of their income toward the price hikes. The bottom 10 percent of households by income, for example, would spend 4 percent of their disposable income on tariffs, while the top 10 percent will only pay 1.6 percent. (If Trump fully reverses some of his tariffs, the impact will be smaller but the overall trend will be the same: Lower-income people will carry the biggest burden.)The second potential impact of the tariffs is on the health of the broader economy. When Trump announced his original tariff plan on what he called “Liberation Day,” economic forecasts immediately showed an increase in the likelihood of a recession. Economists also worried that the new tariffs might cause stagflation — a combination of high inflation, rising unemployment, and stagnant economic growth. When Trump put a pause on implementing some of his tariffs, Goldman Sachs pulled back its recession forecast. But given the high tariffs still in place — and the instability of global financial markets — a recession is still on the table. And if a recession does materialize, then low-income families will bear the brunt of it. During recessions, the number of people in poverty rises; between 2007 and 2009, during the Great Recession, the number of people living below the poverty line increased by nearly 5 million. The job market can also be a greater challenge for low-income people. Not only can job loss sometimes lead to long-term unemployment, workers without college degrees — who tend to earn less than college-educated workers to begin with — are more likely to find new jobs that have lower wages than before.Is there a fix?The good news is that all of this is reversible. The bad news is that it largely relies on Trump changing his mind, though as we saw this week, that’s always a possibility.There are two other avenues for change. The first is Congress: Before Trump walked back his “Liberation Day” promises, at least seven Republican senators signed onto a bipartisan bill to put limits on the president’s authority to impose tariffs. That’s unlikely to work, in part because the bill still falls short of the 60 votes it would need to pass the Senate, and because Trump’s abrupt U-turn has softened some of the pushback that his original tariff plan received. The second is the courts: Federal courts could potentially strike down Trump’s tariffs, which are unpopular even in some right-wing circles. A libertarian group, for example, has already filed a lawsuit against Trump, claiming that he is misusing his emergency powers. But the quickest and likeliest change can only come from Trump himself, and it’s hard to predict what he’ll do next. In the meantime, his latest tariff policy shows exactly where Trump’s priorities are: tax hikes for the poor, and tax cuts for the rich.This story was featured in the Within Our Means newsletter. Sign up here.See More:0 Commentaires 0 Parts 103 Vue
WWW.VOX.COMThe far-reaching effects of Trump’s tariffs on low-income people, explainedPresident Donald Trump’s tariff plan has rattled Wall Street, alarmed the United States’ trading partners, and made Americans afraid of checking their retirement accounts. It’s also been extremely confusing: After announcing that he would implement steep tariffs across the board (for reasons that didn’t make much sense), Trump walked back some of the tariffs before they were set to go into effect. However, he is still waging a trade war with China, and the tariff rates on many other countries remain much higher than they were before this whole saga began.Throughout this, Trump and his allies have suggested that while the tariffs are hurting Wall Street, they’re going to have a positive effect for small businesses on “Main Street.” The logic is that it’s only the wealthy who own stocks and have 401(k)s, and are therefore feeling the pain of the plunging market. But that’s not true, and it’s not just Wall Street that will suffer from these tariffs. That’s not because tariffs are always bad. As I wrote last week, tariffs can be used for good if implemented narrowly and strategically to help prop up certain industries, which is why some unions support the idea of harsher tariffs. But Trump’s plan is far too broad, and it’s unclear what he even hopes to achieve with them. In reality, the people who will be most affected by Trump’s tariffs are poor people. That’s true for low-wage workers who might lose jobs in developing countries around the world as factories downsize or close because of the negative effect of tariffs on trade. It’s also true for low-income families in the United States, for at least two reasons.How Trump’s tariffs will hurt low-income AmericansThere are two ways the tariffs will hurt people with low incomes:The first and most obvious impact of Trump’s tariffs is that they will raise prices on everyday goods. Tariffs act as a consumption tax — a levy that people ultimately pay at the checkout counter because businesses will likely raise their prices to offset their tariff bills. Unlike income taxes, which are adjusted based on how much a household makes, everyone will pay the same rate on the same good. According to the Budget Lab at Yale University, which analyzed the impact of the original tariffs Trump announced over a week ago, the average American household would be levied about $3,800. For the lowest income households, the tariff-imposed cost-of-living increase is lower — about $1,700 — in part because their overall spending is lower.But they will still pay a larger share of their income toward the price hikes. The bottom 10 percent of households by income, for example, would spend 4 percent of their disposable income on tariffs, while the top 10 percent will only pay 1.6 percent. (If Trump fully reverses some of his tariffs, the impact will be smaller but the overall trend will be the same: Lower-income people will carry the biggest burden.)The second potential impact of the tariffs is on the health of the broader economy. When Trump announced his original tariff plan on what he called “Liberation Day,” economic forecasts immediately showed an increase in the likelihood of a recession. Economists also worried that the new tariffs might cause stagflation — a combination of high inflation, rising unemployment, and stagnant economic growth. When Trump put a pause on implementing some of his tariffs, Goldman Sachs pulled back its recession forecast. But given the high tariffs still in place — and the instability of global financial markets — a recession is still on the table. And if a recession does materialize, then low-income families will bear the brunt of it. During recessions, the number of people in poverty rises; between 2007 and 2009, during the Great Recession, the number of people living below the poverty line increased by nearly 5 million. The job market can also be a greater challenge for low-income people. Not only can job loss sometimes lead to long-term unemployment, workers without college degrees — who tend to earn less than college-educated workers to begin with — are more likely to find new jobs that have lower wages than before.Is there a fix?The good news is that all of this is reversible. The bad news is that it largely relies on Trump changing his mind, though as we saw this week, that’s always a possibility.There are two other avenues for change. The first is Congress: Before Trump walked back his “Liberation Day” promises, at least seven Republican senators signed onto a bipartisan bill to put limits on the president’s authority to impose tariffs. That’s unlikely to work, in part because the bill still falls short of the 60 votes it would need to pass the Senate, and because Trump’s abrupt U-turn has softened some of the pushback that his original tariff plan received. The second is the courts: Federal courts could potentially strike down Trump’s tariffs, which are unpopular even in some right-wing circles. A libertarian group, for example, has already filed a lawsuit against Trump, claiming that he is misusing his emergency powers. But the quickest and likeliest change can only come from Trump himself, and it’s hard to predict what he’ll do next. In the meantime, his latest tariff policy shows exactly where Trump’s priorities are: tax hikes for the poor, and tax cuts for the rich.This story was featured in the Within Our Means newsletter. Sign up here.See More:0 Commentaires 0 Parts 103 Vue -
 GIZMODO.COMBungie’s New Marathon Game Has an Amazing Short FilmAfter a decade focusing solely on its ongoing shared world shooter Destiny, Bungie is reviving its old sci-fi shooter series Marathon. As part of the game’s official unveiling on Saturday, the developer released a cinematic short that may be one of the coolest videos of 2025. Written and directed by Spanish animator Alberto Mielgo—best known for Love, Death, & Robots and art director for Spider-Man: Into the Spider-Verse—the eight-minute video lays out the intriguing, violent, and more than a little unsettling sci-fi world of this new Marathon. As it opens, something…weird happens on the planet Tau Ceti IV. Some colonists are crushed by satellite debris from a meteor shower, others die where they stand in gruesome fashion. Even creepier is that we see these deaths span across several decades, from 2794 to 2812 and 2827. We then jump ahead to 2893, where cybernetic beings—former humans who have machine bodies crafted by cybernetic silkworms—are looting the colony for anything they can get their hands on to sell to various factions still stationed on the planet. This second part of the cinematic, which features narration from Final Fantasy XVI’s Ben Starr, is meant to show you Marathon’s gameplay loop. Since this is a multiplayer extraction shooter, players will take on the role of cybernetic mercenaries called Runners to steal data, research, and the like for Tau Ceti’s various factions, and shoot each other (or the planet’s wildlife or security bots) to get loot and escape safely. But the main point of this cinematic is take you into Bungie’s new sci-fi world and offer glimpses of what you’ll see as you shoot each other into scrap. Vibes and atmosphere have always been one of Bungie’s strong suits, and what’s really interesting about this short is seeing Runners like Glitch (Erica Lindbeck) and Void (Elias Toufexis) be aware that something about Tau Ceti and their being there is wrong, but unable to fully vocalize why. Whatever’s drawn them there has its hooks in them deep, and not even getting shot to bits will keep them from keeping on after they’ve been rebuilt. Fancy cinematics are nothing new for games at this point in the medium’s life. But for Bungie, Marathon feels like a massive step forward from what the studio’s previously done with Halo and Destiny. The game’s aesthetic is pretty striking and distinct from anything seen in major sci-fi games in quite some time. As cold as everything looks—this is, after all, a world shaken by its inhabitants mysteriously vanishing, possibly because of some thing roaming the hallways—there’s a vibrancy to the colors that don’t clash as much as you’d think. It’s also just shot differently than any Bungie cutscene to date; the camera being so close to the Runners provides intimatcy they’re not getting (or ignoring) from each other and makes the scenes where they die hit that much harder. For many, this short will be enough to sell them on Marathon alone, and it’s likely Sony plans to use snippets of it to promote the game on TV. For others, the short has done everything right in terms of getting them hooked…but it’s a strictly multiplayer game with no single-player offering to speak of. That’s a real shame, since at their best, Bungie’s story campaigns were memorable and have stayed with players for years. It’s easy to imagine this being so engrossing if we were able to just be on Tau Ceti and investigate its secrets in an engaging narrative with tight gunplay and some sweet music. Ah, well—for the multiplayer heads, Marathon will run to PlayStation 5, Xbox Series X|S, and PC on September 23. Want more io9 news? Check out when to expect the latest Marvel, Star Wars, and Star Trek releases, what’s next for the DC Universe on film and TV, and everything you need to know about the future of Doctor Who.0 Commentaires 0 Parts 100 Vue
GIZMODO.COMBungie’s New Marathon Game Has an Amazing Short FilmAfter a decade focusing solely on its ongoing shared world shooter Destiny, Bungie is reviving its old sci-fi shooter series Marathon. As part of the game’s official unveiling on Saturday, the developer released a cinematic short that may be one of the coolest videos of 2025. Written and directed by Spanish animator Alberto Mielgo—best known for Love, Death, & Robots and art director for Spider-Man: Into the Spider-Verse—the eight-minute video lays out the intriguing, violent, and more than a little unsettling sci-fi world of this new Marathon. As it opens, something…weird happens on the planet Tau Ceti IV. Some colonists are crushed by satellite debris from a meteor shower, others die where they stand in gruesome fashion. Even creepier is that we see these deaths span across several decades, from 2794 to 2812 and 2827. We then jump ahead to 2893, where cybernetic beings—former humans who have machine bodies crafted by cybernetic silkworms—are looting the colony for anything they can get their hands on to sell to various factions still stationed on the planet. This second part of the cinematic, which features narration from Final Fantasy XVI’s Ben Starr, is meant to show you Marathon’s gameplay loop. Since this is a multiplayer extraction shooter, players will take on the role of cybernetic mercenaries called Runners to steal data, research, and the like for Tau Ceti’s various factions, and shoot each other (or the planet’s wildlife or security bots) to get loot and escape safely. But the main point of this cinematic is take you into Bungie’s new sci-fi world and offer glimpses of what you’ll see as you shoot each other into scrap. Vibes and atmosphere have always been one of Bungie’s strong suits, and what’s really interesting about this short is seeing Runners like Glitch (Erica Lindbeck) and Void (Elias Toufexis) be aware that something about Tau Ceti and their being there is wrong, but unable to fully vocalize why. Whatever’s drawn them there has its hooks in them deep, and not even getting shot to bits will keep them from keeping on after they’ve been rebuilt. Fancy cinematics are nothing new for games at this point in the medium’s life. But for Bungie, Marathon feels like a massive step forward from what the studio’s previously done with Halo and Destiny. The game’s aesthetic is pretty striking and distinct from anything seen in major sci-fi games in quite some time. As cold as everything looks—this is, after all, a world shaken by its inhabitants mysteriously vanishing, possibly because of some thing roaming the hallways—there’s a vibrancy to the colors that don’t clash as much as you’d think. It’s also just shot differently than any Bungie cutscene to date; the camera being so close to the Runners provides intimatcy they’re not getting (or ignoring) from each other and makes the scenes where they die hit that much harder. For many, this short will be enough to sell them on Marathon alone, and it’s likely Sony plans to use snippets of it to promote the game on TV. For others, the short has done everything right in terms of getting them hooked…but it’s a strictly multiplayer game with no single-player offering to speak of. That’s a real shame, since at their best, Bungie’s story campaigns were memorable and have stayed with players for years. It’s easy to imagine this being so engrossing if we were able to just be on Tau Ceti and investigate its secrets in an engaging narrative with tight gunplay and some sweet music. Ah, well—for the multiplayer heads, Marathon will run to PlayStation 5, Xbox Series X|S, and PC on September 23. Want more io9 news? Check out when to expect the latest Marvel, Star Wars, and Star Trek releases, what’s next for the DC Universe on film and TV, and everything you need to know about the future of Doctor Who.0 Commentaires 0 Parts 100 Vue


