0 Commentarii
0 Distribuiri
162 Views

Director
Director
-
Vă rugăm să vă autentificați pentru a vă dori, partaja și comenta!
-
WWW.ENGADGET.COMApples next AirPods Pro could offer heart rate and temperature monitoringApple is working on the next generation of AirPods Pro, and they may come packing some new health features, according to Bloombergs Mark Gurman. In the Power On newsletter this weekend, Gurman reports that Apple has been testing features including temperature sensing and heart rate monitoring for the earbuds. So far, Apple has found that the Apple Watch still does the latter better, but the AirPods arent terribly far off in their readings, he writes.The company has also reportedly revived its idea of putting cameras into AirPods, a rumor weve heard a few times over the last year. According to Gurman, Apple now considers it a priority as it works to bolster its AI services. But, itd likely be years before any camera-equipped AirPods make their debut. As for heart rate monitoring, that may appear much sooner. Gurman writes, The capability could be ready for the next-generation AirPods Pro, which are in early development.This article originally appeared on Engadget at https://www.engadget.com/audio/headphones/apples-next-airpods-pro-could-offer-heart-rate-and-temperature-monitoring-175757188.html?src=rss0 Commentarii 0 Distribuiri 158 Views
-
WWW.ENGADGET.COMApple is reportedly working on a smart doorbell system that could unlock your door with Face IDApple is developing a smart doorbell and lock system that would use Face ID to unlock the door for known residents, Mark Gurman reports in the Power On newsletter. The face-scanning doorbell would connect to a smart deadbolt, which could include existing HomeKit-compatible third-party locks, according to Gurman. Or, Apple may [team] up with a specific lock maker to offer a complete system on day one.Itll likely still be a while before we see the doorbell-lock system hit the market, though, if we see it at all. Gurman reports that its in the early stages of development and wouldnt be ready until at least the end of next year. The doorbell would help Apple compete with the likes of Amazon's Ring and Google Nest, and it's just one of several smart home products Apple is working on, according to Gurman. The company is reportedly also developing a security camera for inside the home, which would work with its rumored smart home hub thats expected to make its debut as soon as next year.This article originally appeared on Engadget at https://www.engadget.com/home/smart-home/apple-is-reportedly-working-on-a-smart-doorbell-system-that-could-unlock-your-door-with-face-id-161504513.html?src=rss0 Commentarii 0 Distribuiri 148 Views
-
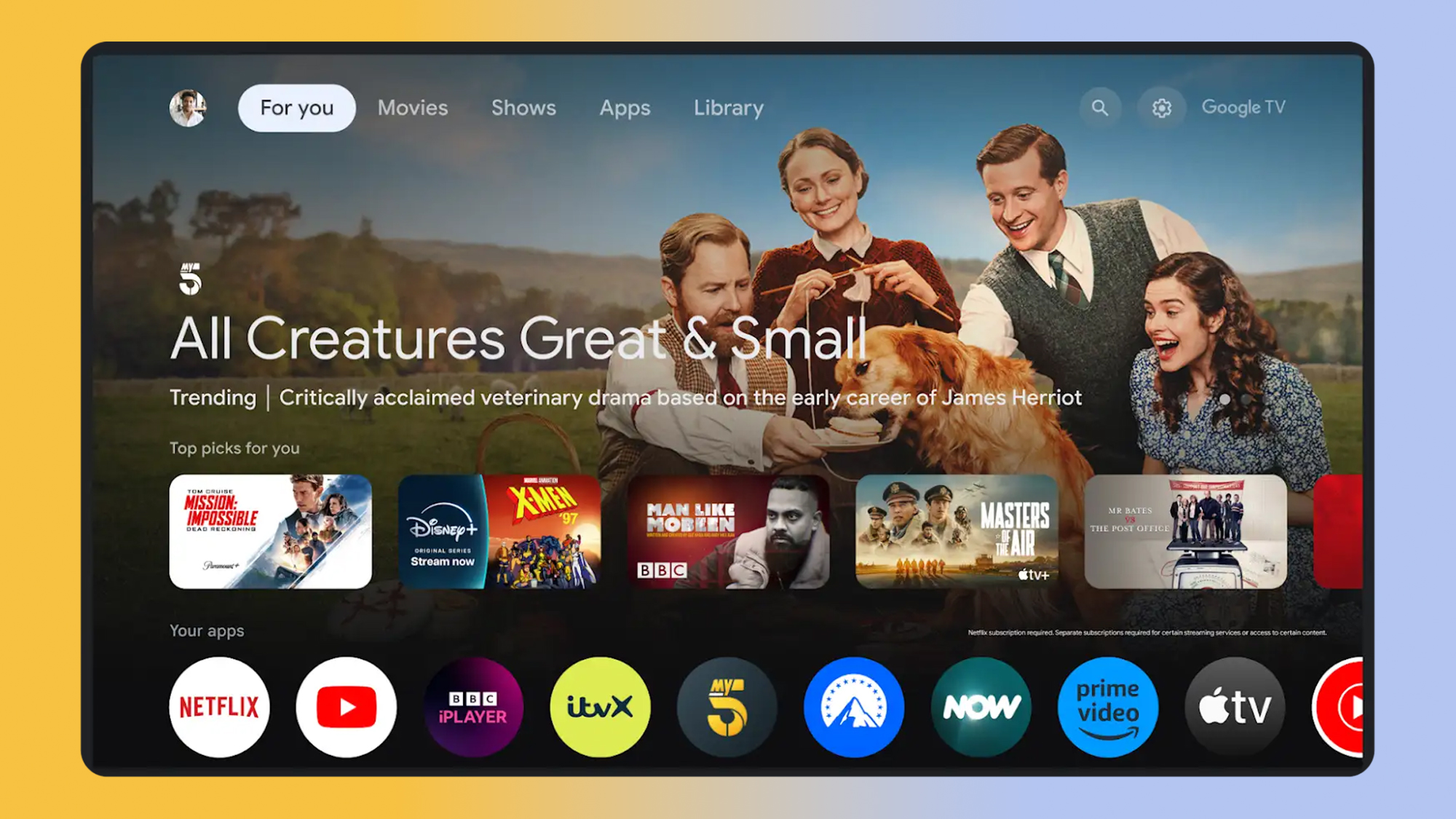 WWW.TECHRADAR.COMGoogle TV users are getting even more free channels in time for the holidaysIf you're in the US, you now have a total of 171 channels to watch through the Google TV Freeplay app.0 Commentarii 0 Distribuiri 160 Views
WWW.TECHRADAR.COMGoogle TV users are getting even more free channels in time for the holidaysIf you're in the US, you now have a total of 171 channels to watch through the Google TV Freeplay app.0 Commentarii 0 Distribuiri 160 Views -
 WWW.CNBC.COMWhat Googles quantum computing breakthrough Willow means for the future of bitcoin and other cryptosGoogle's new chip Willow made a big statement that quantum computing is coming to the real world. That could also mean a future of cryptocurrency hacking.0 Commentarii 0 Distribuiri 177 Views
WWW.CNBC.COMWhat Googles quantum computing breakthrough Willow means for the future of bitcoin and other cryptosGoogle's new chip Willow made a big statement that quantum computing is coming to the real world. That could also mean a future of cryptocurrency hacking.0 Commentarii 0 Distribuiri 177 Views -
 VFXEXPRESS.COMNick & Merlin Discuss the Making of Wallace & Gromit | NetflixWallace & Gromit was founded by visionary Nick Park, as well as Merlin Crossingham, Director of Vengeance Most Fowl, who talks about how this work came to be. Through this exclusive Netflix feature, they share how inventive storytelling by Nick brought the iconic Wallace & Gromit to life, appealing to many generations with their unique and quirky humor and charm.The two also discuss their work on the new adventure, Vengeance Most Fowl, bringing the lovable duo back for another fun-filled journey. Packed with humor and heart, the new story continues to showcase the timeless appeal and creativity that have made Wallace & Gromit cultural icons.This is an interesting conversation that provides fans with a rare glimpse into the creative process behind the claymation classics and celebrates their ongoing impact on audiences around the world. Dont miss this nostalgic and inspiring behind-the-scenes look!The post Nick & Merlin Discuss the Making of Wallace & Gromit | Netflix appeared first on Vfxexpress.0 Commentarii 0 Distribuiri 178 Views
VFXEXPRESS.COMNick & Merlin Discuss the Making of Wallace & Gromit | NetflixWallace & Gromit was founded by visionary Nick Park, as well as Merlin Crossingham, Director of Vengeance Most Fowl, who talks about how this work came to be. Through this exclusive Netflix feature, they share how inventive storytelling by Nick brought the iconic Wallace & Gromit to life, appealing to many generations with their unique and quirky humor and charm.The two also discuss their work on the new adventure, Vengeance Most Fowl, bringing the lovable duo back for another fun-filled journey. Packed with humor and heart, the new story continues to showcase the timeless appeal and creativity that have made Wallace & Gromit cultural icons.This is an interesting conversation that provides fans with a rare glimpse into the creative process behind the claymation classics and celebrates their ongoing impact on audiences around the world. Dont miss this nostalgic and inspiring behind-the-scenes look!The post Nick & Merlin Discuss the Making of Wallace & Gromit | Netflix appeared first on Vfxexpress.0 Commentarii 0 Distribuiri 178 Views -
 WWW.FASTCOMPANY.COMJob search 2025: 3 key ways AI will make an impact on recruitmentLogging onto LinkedIn, your feed is likely full of Open to Work profiles and posts about the struggle of finding a job in todays market. Your LinkedIn inbox is probably a lot quieter with fewer recruiters reaching out with job opportunities than at the height of the Great Resignation just two years ago.Whether you are a new graduate navigating a career pivot or just looking for greener pastures, the common sentiment of job seekers is that its becoming exceedingly difficult to land an interview, let alone an offer. With applications up 6% from October 2023, competition remains stiff. To make matters more difficult, how hiring teams review applications has also changed.Application tracking systems (ATS) are now the status quo for companies to manage job openings and vet potential candidates. While not a new development, they are continuing to shake up the job application process and transform how talent is evaluated, engaged, and hired.Fueled by AI, these systems are now aiding hiring teams in ways that would have been unimaginable just a decade ago, through matching candidates to open roles, providing recommendations and explainable rankings, parsing rsums, and more. With these systems, recruiters are empowered to be more streamlined and efficient in managing applications, scheduling interviews, and connecting with potential candidates.So, if the way recruiters approach their candidate search evolved, why havent job seekers strategies? As recruiters rethink their processes with AI, applicants should, too. Job seekers must figure out how to navigate a transforming landscape where AI shapes how we approach and think about the hiring system.Lets dive into three key changes to the recruitment process and how candidates can respond and stand apart from their peers.Skills over experienceOver the past several years, skills-matching technology has been the most notable advancement in recruitment to come out of the AI revolution. Recruiters have turned a growing focus towards skills-based hiring, ensuring a candidate is the best fit for a role based on the capabilities they have on hand. Gone are the days when an expensive degree or a specific internship on your rsum sealed the deal. If AI cant see the skills theyre looking for in your rsum, it is likely moving on to the next applicant. With skills-matching AI in their toolbox, recruiters spend less time scanning through rsums and more time engaging with prospective candidates.What this means for you: Its time for a rsum revamp. The experience-forward rsums of the past will not help you stand out to a large language model scanning for a specific skill. Dont get me wrong: job experience is still valuable. But instead of just listing past job duties, focus on the how: what skills you used, and how they made an impact. This shift democratizes the playing field, making way for those from nontraditional backgrounds. If you can demonstrate the skills, youre in the game.The automation of candidate communication and engagementWaiting to hear back from a potential employer can be stressful for job seekers. In fact, almost a quarter (23%) of candidates find the most frustrating aspect of the application process is feeling like their application is going into a digital black hole, per research from iCIMS. But that wait is not just about hearing if their application has been accepted or if they landed the job. A lot of the waiting is the result of scheduling interviews, asking clarifying questions on company culture, etc. Chatbots are becoming the go-to option to help streamline candidate communication so job seekers can get answers fast, schedule interviews more quickly, and leverage their recruiter contact strategically to understand what the hiring manager is looking for in the role.What this means for you: Dont just dismiss the ping of a chatbot on a career pageuse it to supercharge both your application and interview process. Chatbots are a safe space to ask the questions you want answered about company culture or an open position that you might be too nervous to ask a recruiter about. For example, you can ask chatbots about benefits, company offerings, the job description, and more. Use this knowledge to discern if the role is the right fit for you before applying and help prepare for your interviews once you progress in the application process.AI leveraged at every part of the recruitment processAccording to 500 TA pros, AI tools save them 2.39 hours a week on average, and 64% of those TA pros want to see more AI in their workflows. So, where is AI coming into play today? Thirty percent use GenAI specifically to write job descriptions and another 36% to draft interview questions.What this means for you: Use AI in your job search. There is a double standard with AI usage in todays labor market. iCIMS research has found that 87% of recruiters say its adoption in the application process has raised red flags. As technology becomes more ubiquitous in culture and the workplace, AI will be seen as a tooljust like a search engineto help fuel ones job search. For now, use AI as more of a yellow flag. It will never be okay to blindly copy and paste AI-generated rsums or cover letters. Your unique insight and human touch will always be necessary and what recruiters truly want to see.Instead, use GenAI to prep for your interviews by feeding it the job description and asking what questions a hiring manager would ask, so you can come to an interview fully prepared. You can also use it to review your rsum and help streamline and identify the skills you want to highlight most for the job you are applying for. Just remember, when it comes to using AI in your job search, no one knows you or your work experience better than you do.Adapting to an AI-enhanced job marketAs the recruitment process continues to be infused with more technology, job seekers must move away from the mentality of gaming the system or beating the AI and instead see the new status quo of hiring and evolve their strategies to meet recruiters where they are at.With every instance of automation in the recruitment process, the goal has been to make life easier for candidates and their potential employers. However, this cannot be true without some adaptations and tweaks. Trying to go about the application process in the same ways we always have doesnt make sense in a world where the entire recruitment journey has been AI-enhanced. The right opportunity is out there, and these small adjustments can make a big difference in helping you land your next role.0 Commentarii 0 Distribuiri 163 Views
WWW.FASTCOMPANY.COMJob search 2025: 3 key ways AI will make an impact on recruitmentLogging onto LinkedIn, your feed is likely full of Open to Work profiles and posts about the struggle of finding a job in todays market. Your LinkedIn inbox is probably a lot quieter with fewer recruiters reaching out with job opportunities than at the height of the Great Resignation just two years ago.Whether you are a new graduate navigating a career pivot or just looking for greener pastures, the common sentiment of job seekers is that its becoming exceedingly difficult to land an interview, let alone an offer. With applications up 6% from October 2023, competition remains stiff. To make matters more difficult, how hiring teams review applications has also changed.Application tracking systems (ATS) are now the status quo for companies to manage job openings and vet potential candidates. While not a new development, they are continuing to shake up the job application process and transform how talent is evaluated, engaged, and hired.Fueled by AI, these systems are now aiding hiring teams in ways that would have been unimaginable just a decade ago, through matching candidates to open roles, providing recommendations and explainable rankings, parsing rsums, and more. With these systems, recruiters are empowered to be more streamlined and efficient in managing applications, scheduling interviews, and connecting with potential candidates.So, if the way recruiters approach their candidate search evolved, why havent job seekers strategies? As recruiters rethink their processes with AI, applicants should, too. Job seekers must figure out how to navigate a transforming landscape where AI shapes how we approach and think about the hiring system.Lets dive into three key changes to the recruitment process and how candidates can respond and stand apart from their peers.Skills over experienceOver the past several years, skills-matching technology has been the most notable advancement in recruitment to come out of the AI revolution. Recruiters have turned a growing focus towards skills-based hiring, ensuring a candidate is the best fit for a role based on the capabilities they have on hand. Gone are the days when an expensive degree or a specific internship on your rsum sealed the deal. If AI cant see the skills theyre looking for in your rsum, it is likely moving on to the next applicant. With skills-matching AI in their toolbox, recruiters spend less time scanning through rsums and more time engaging with prospective candidates.What this means for you: Its time for a rsum revamp. The experience-forward rsums of the past will not help you stand out to a large language model scanning for a specific skill. Dont get me wrong: job experience is still valuable. But instead of just listing past job duties, focus on the how: what skills you used, and how they made an impact. This shift democratizes the playing field, making way for those from nontraditional backgrounds. If you can demonstrate the skills, youre in the game.The automation of candidate communication and engagementWaiting to hear back from a potential employer can be stressful for job seekers. In fact, almost a quarter (23%) of candidates find the most frustrating aspect of the application process is feeling like their application is going into a digital black hole, per research from iCIMS. But that wait is not just about hearing if their application has been accepted or if they landed the job. A lot of the waiting is the result of scheduling interviews, asking clarifying questions on company culture, etc. Chatbots are becoming the go-to option to help streamline candidate communication so job seekers can get answers fast, schedule interviews more quickly, and leverage their recruiter contact strategically to understand what the hiring manager is looking for in the role.What this means for you: Dont just dismiss the ping of a chatbot on a career pageuse it to supercharge both your application and interview process. Chatbots are a safe space to ask the questions you want answered about company culture or an open position that you might be too nervous to ask a recruiter about. For example, you can ask chatbots about benefits, company offerings, the job description, and more. Use this knowledge to discern if the role is the right fit for you before applying and help prepare for your interviews once you progress in the application process.AI leveraged at every part of the recruitment processAccording to 500 TA pros, AI tools save them 2.39 hours a week on average, and 64% of those TA pros want to see more AI in their workflows. So, where is AI coming into play today? Thirty percent use GenAI specifically to write job descriptions and another 36% to draft interview questions.What this means for you: Use AI in your job search. There is a double standard with AI usage in todays labor market. iCIMS research has found that 87% of recruiters say its adoption in the application process has raised red flags. As technology becomes more ubiquitous in culture and the workplace, AI will be seen as a tooljust like a search engineto help fuel ones job search. For now, use AI as more of a yellow flag. It will never be okay to blindly copy and paste AI-generated rsums or cover letters. Your unique insight and human touch will always be necessary and what recruiters truly want to see.Instead, use GenAI to prep for your interviews by feeding it the job description and asking what questions a hiring manager would ask, so you can come to an interview fully prepared. You can also use it to review your rsum and help streamline and identify the skills you want to highlight most for the job you are applying for. Just remember, when it comes to using AI in your job search, no one knows you or your work experience better than you do.Adapting to an AI-enhanced job marketAs the recruitment process continues to be infused with more technology, job seekers must move away from the mentality of gaming the system or beating the AI and instead see the new status quo of hiring and evolve their strategies to meet recruiters where they are at.With every instance of automation in the recruitment process, the goal has been to make life easier for candidates and their potential employers. However, this cannot be true without some adaptations and tweaks. Trying to go about the application process in the same ways we always have doesnt make sense in a world where the entire recruitment journey has been AI-enhanced. The right opportunity is out there, and these small adjustments can make a big difference in helping you land your next role.0 Commentarii 0 Distribuiri 163 Views -
 WWW.FASTCOMPANY.COMPublic-private partnerships are shifting to be more community-centered. Here are 4 lessonsCities tackle a vast array of responsibilitiesfrom building transit networks to running schoolsand sometimes they can use a little help. Thats why local governments have long teamed up with businesses in so-called public-private partnerships. Historically, these arrangements have helped cities fund big infrastructure projects such as bridges and hospitals.However, our analysis and research show an emerging trend with local governments engaged in private-sector collaborationswhat we have come to describe as community-centered, public-private partnerships, or CP3s. Unlike traditional public-private partnerships, CP3s arent just about financial investments; they leverage relationships and trust. And theyre about more than just building infrastructure; theyre about building resilient and inclusive communities.As the founding executive director of the Partnership for Inclusive Innovation, based out of the Georgia Institute of Technology, Im fascinated with CP3s. And while not all CP3s are successful, when done right they offer local governments a powerful tool to navigate the complexities of modern urban life.Together with international climate finance expert Andrea Fernndez of the urban climate leadership group C40, we analyzed community-centered, public-private partnerships across the world and put together eight case studies. Together, they offer valuable insights into how cities can harness the power of CP3s.4 keys to successAlthough we looked at partnerships forged in different countries and contexts, we saw several elements emerge as critical to success over and over again. 1. Clear mission and vision: Its essential to have a mission that resonates with everyone involved. Ruta N in Medelln, Colombia, for example, transformed the city into a hub of innovation, attracting 471 technology companies and creating 22,500 jobs.This vision wasnt static. It evolved in response to changing local dynamics, including leadership priorities and broader global trends. However, the core mission of entrepreneurship, investment and innovation remained clear and was embraced by all key stakeholders, driving the partnership forward. 2. Diverse and engaged partners: Successful CP3s rely on the active involvement of a wide range of partners, each bringing their unique expertise and resources to the table. In the U.K., for example, the Hull net-zero climate initiative featured a partnership that included more than 150 companies, many small and medium-size. This diversity of partners was crucial to the initiatives success because they could leverage resources and share risks, enabling it to address complex challenges from multiple angles.Similarly, Malaysias Think City engaged community-based organizations and vulnerable populations in its Penang climate adaptation program. This ensured that the partnership was inclusive and responsive to the needs of all citizens. 3. Robust governance structure: Effective governance is key to ensuring that CP3s operate smoothly and achieve their objectives. For example, in Melbourne, Australia, the City Professorial Chair in Urban Resilience and Innovation includes representatives from the city and a university. It has a formal communication structure where research informs policy and vice versa. It aims to harness the research to better inform and guide policymaking and in turn advance research by putting it into city practice.In South Africa, the Gauteng City-Region Observatory bridges academia and government to drive urban development. Its governance structure, which includes a diverse board appointed by the provinces premier, ensures that the partnership remains focused and effective. It means that it goes beyond any one organizations evolving agendas and leadership for longer-term community gains. 4. Commitment to innovation and growth: While we found that securing funding and in-kind support is important, demonstrating economic impact is crucial for the sustainability of CP3s.Dublins Smart Docklands initiative is a prime example of this. By leveraging technology to address community needs, the partnership attracted over 3 million euros (US$3.2 billion) in investments and quadrupled the projects funding.The initiative not only boosted Dublins connectivity and tech infrastructure but also addressed public safety through solutions such as smart ring buoys. The buoys are life preservers with sensors to alert the city when its buoys are tampered with or stolen.The case studies show that CP3s can be a globally applicable model for urban development, not merely a passing trend. By fostering collective action, sharing risks and leveraging multiple sources of funding, CP3s can be a powerful tool for cities navigating the challenges and opportunities of the 21st century.Debra Lam is a founding director of the Partnership for Inclusive Innovation at the Enterprise Innovation Institute at Georgia Institute of Technology.This article is republished from The Conversation under a Creative Commons license. Read the original article.0 Commentarii 0 Distribuiri 164 Views
WWW.FASTCOMPANY.COMPublic-private partnerships are shifting to be more community-centered. Here are 4 lessonsCities tackle a vast array of responsibilitiesfrom building transit networks to running schoolsand sometimes they can use a little help. Thats why local governments have long teamed up with businesses in so-called public-private partnerships. Historically, these arrangements have helped cities fund big infrastructure projects such as bridges and hospitals.However, our analysis and research show an emerging trend with local governments engaged in private-sector collaborationswhat we have come to describe as community-centered, public-private partnerships, or CP3s. Unlike traditional public-private partnerships, CP3s arent just about financial investments; they leverage relationships and trust. And theyre about more than just building infrastructure; theyre about building resilient and inclusive communities.As the founding executive director of the Partnership for Inclusive Innovation, based out of the Georgia Institute of Technology, Im fascinated with CP3s. And while not all CP3s are successful, when done right they offer local governments a powerful tool to navigate the complexities of modern urban life.Together with international climate finance expert Andrea Fernndez of the urban climate leadership group C40, we analyzed community-centered, public-private partnerships across the world and put together eight case studies. Together, they offer valuable insights into how cities can harness the power of CP3s.4 keys to successAlthough we looked at partnerships forged in different countries and contexts, we saw several elements emerge as critical to success over and over again. 1. Clear mission and vision: Its essential to have a mission that resonates with everyone involved. Ruta N in Medelln, Colombia, for example, transformed the city into a hub of innovation, attracting 471 technology companies and creating 22,500 jobs.This vision wasnt static. It evolved in response to changing local dynamics, including leadership priorities and broader global trends. However, the core mission of entrepreneurship, investment and innovation remained clear and was embraced by all key stakeholders, driving the partnership forward. 2. Diverse and engaged partners: Successful CP3s rely on the active involvement of a wide range of partners, each bringing their unique expertise and resources to the table. In the U.K., for example, the Hull net-zero climate initiative featured a partnership that included more than 150 companies, many small and medium-size. This diversity of partners was crucial to the initiatives success because they could leverage resources and share risks, enabling it to address complex challenges from multiple angles.Similarly, Malaysias Think City engaged community-based organizations and vulnerable populations in its Penang climate adaptation program. This ensured that the partnership was inclusive and responsive to the needs of all citizens. 3. Robust governance structure: Effective governance is key to ensuring that CP3s operate smoothly and achieve their objectives. For example, in Melbourne, Australia, the City Professorial Chair in Urban Resilience and Innovation includes representatives from the city and a university. It has a formal communication structure where research informs policy and vice versa. It aims to harness the research to better inform and guide policymaking and in turn advance research by putting it into city practice.In South Africa, the Gauteng City-Region Observatory bridges academia and government to drive urban development. Its governance structure, which includes a diverse board appointed by the provinces premier, ensures that the partnership remains focused and effective. It means that it goes beyond any one organizations evolving agendas and leadership for longer-term community gains. 4. Commitment to innovation and growth: While we found that securing funding and in-kind support is important, demonstrating economic impact is crucial for the sustainability of CP3s.Dublins Smart Docklands initiative is a prime example of this. By leveraging technology to address community needs, the partnership attracted over 3 million euros (US$3.2 billion) in investments and quadrupled the projects funding.The initiative not only boosted Dublins connectivity and tech infrastructure but also addressed public safety through solutions such as smart ring buoys. The buoys are life preservers with sensors to alert the city when its buoys are tampered with or stolen.The case studies show that CP3s can be a globally applicable model for urban development, not merely a passing trend. By fostering collective action, sharing risks and leveraging multiple sources of funding, CP3s can be a powerful tool for cities navigating the challenges and opportunities of the 21st century.Debra Lam is a founding director of the Partnership for Inclusive Innovation at the Enterprise Innovation Institute at Georgia Institute of Technology.This article is republished from The Conversation under a Creative Commons license. Read the original article.0 Commentarii 0 Distribuiri 164 Views -
 WWW.DEZEEN.COMMorris Adjmi Architects mixes soft and industrial materials inside Brooklyn towersNew York-based Morris Adjmi Architects has used pink leather, herringbone flooring and green hand-glazed tiles across the interiors of a residential complex the studio designed on the waterfront of Greenpoint, Brooklyn.The Huron comprises two interconnected glass and steel towers, for which Morris Adjmi Architects served as the architect, interior designer and art consultant.In the lobby at The Huron, the reception desk is wrapped in pink leather and sits against a backdrop of green tiles"Inspired by the Brooklyn waterfront and artist Edward Hopper's urbanscapes, The Huron reflects Greenpoint's past and present, paying homage to the neighborhood's golden age of industrialism," said the studio.Industrial hints in the form of exposed concrete columns, large loft-style windows and metal-framed glass partitions are found throughout the public areas.A soft neutral palette juxtaposes industrial loft-style windowsThese are paired with a soft colour palette in the lobby, where warm-toned, wood-panelled walls flank a custom reception desk in pink leather and with an onyx top.Behind are hand-glazed tiles in vivid shades of green, while to one side, a selection of art objects is displayed on a set of shelves wrapped in the same leather as the counter.Exposed concrete columns and brown oak herringbone floors contrast one another in the private dining roomCurved furniture is used in the lobby "to balance out the building's linear shape", and forms seating areas at either end of the space.Pieces include Giulio Marelli sofas, Gubi chairs, an Egg Collective table with cylindrical legs, a neutral-toned Marc Phillips rug, a Bludot floor lamp and Erica Shamrock drapery.Kitchens in the residences feature Greek marble backsplashes and waterfall islandsThe 171 residences range from studio to four-bedroom units, and a third of these have private outdoor space.Light-toned Greek marble forms the backsplashes and waterfall islands in the kitchens, contrasting walnut millwork and black hardware.Read: Skyscraper by Jason Long and OMA reaches full height in BrooklynBoth towers are topped with an outdoor terrace, while the west tower includes a 50-foot (15-metre) indoor saltwater pool with a view of the East River.In this space, textured limestone tile runs up to the ceiling between each column, while porcelain tiles that cover the floor transition into blue mosaic tiles that form a letter H in the pool.A swimming pool in the complex's west tower overlooks the East RiverOther amenity spaces within the complex include a lounge with brown herringbone oak flooring that carries into the private dining room.There's also a communal workspace and a fitness centre on the first floor, as well as a kids' room, a lounge for teenagers, and a playground on the second floor.The Huron's pair of towers (right) join a spate of newly developed buildings on the Greenpoint waterfrontDevelopment along the Greenpoint waterfront has transformed the area over the past few years, with residential towers by firms including OMA popping up along the East River.Located in the northwest of Brooklyn, the neighbourhood is home to many design-forward eateries including a bar with a time-worn feel and a restaurant informed by Usonian architecture.The interior photography is by David Mitchell and the exterior photography is by Field Condition.Project credits:Design: Morris Adjmi ArchitectsLandscape: Scape Landscape ArchitectureDevelopment: Quadrum GlobalBrand development: Seventh ArtThe post Morris Adjmi Architects mixes soft and industrial materials inside Brooklyn towers appeared first on Dezeen.0 Commentarii 0 Distribuiri 192 Views
WWW.DEZEEN.COMMorris Adjmi Architects mixes soft and industrial materials inside Brooklyn towersNew York-based Morris Adjmi Architects has used pink leather, herringbone flooring and green hand-glazed tiles across the interiors of a residential complex the studio designed on the waterfront of Greenpoint, Brooklyn.The Huron comprises two interconnected glass and steel towers, for which Morris Adjmi Architects served as the architect, interior designer and art consultant.In the lobby at The Huron, the reception desk is wrapped in pink leather and sits against a backdrop of green tiles"Inspired by the Brooklyn waterfront and artist Edward Hopper's urbanscapes, The Huron reflects Greenpoint's past and present, paying homage to the neighborhood's golden age of industrialism," said the studio.Industrial hints in the form of exposed concrete columns, large loft-style windows and metal-framed glass partitions are found throughout the public areas.A soft neutral palette juxtaposes industrial loft-style windowsThese are paired with a soft colour palette in the lobby, where warm-toned, wood-panelled walls flank a custom reception desk in pink leather and with an onyx top.Behind are hand-glazed tiles in vivid shades of green, while to one side, a selection of art objects is displayed on a set of shelves wrapped in the same leather as the counter.Exposed concrete columns and brown oak herringbone floors contrast one another in the private dining roomCurved furniture is used in the lobby "to balance out the building's linear shape", and forms seating areas at either end of the space.Pieces include Giulio Marelli sofas, Gubi chairs, an Egg Collective table with cylindrical legs, a neutral-toned Marc Phillips rug, a Bludot floor lamp and Erica Shamrock drapery.Kitchens in the residences feature Greek marble backsplashes and waterfall islandsThe 171 residences range from studio to four-bedroom units, and a third of these have private outdoor space.Light-toned Greek marble forms the backsplashes and waterfall islands in the kitchens, contrasting walnut millwork and black hardware.Read: Skyscraper by Jason Long and OMA reaches full height in BrooklynBoth towers are topped with an outdoor terrace, while the west tower includes a 50-foot (15-metre) indoor saltwater pool with a view of the East River.In this space, textured limestone tile runs up to the ceiling between each column, while porcelain tiles that cover the floor transition into blue mosaic tiles that form a letter H in the pool.A swimming pool in the complex's west tower overlooks the East RiverOther amenity spaces within the complex include a lounge with brown herringbone oak flooring that carries into the private dining room.There's also a communal workspace and a fitness centre on the first floor, as well as a kids' room, a lounge for teenagers, and a playground on the second floor.The Huron's pair of towers (right) join a spate of newly developed buildings on the Greenpoint waterfrontDevelopment along the Greenpoint waterfront has transformed the area over the past few years, with residential towers by firms including OMA popping up along the East River.Located in the northwest of Brooklyn, the neighbourhood is home to many design-forward eateries including a bar with a time-worn feel and a restaurant informed by Usonian architecture.The interior photography is by David Mitchell and the exterior photography is by Field Condition.Project credits:Design: Morris Adjmi ArchitectsLandscape: Scape Landscape ArchitectureDevelopment: Quadrum GlobalBrand development: Seventh ArtThe post Morris Adjmi Architects mixes soft and industrial materials inside Brooklyn towers appeared first on Dezeen.0 Commentarii 0 Distribuiri 192 Views -
 ARCHINECT.COMStandout sports architecture and stadiums in 2024In 2024, there was no shortage of exciting news in the world of sports architecture and design. Developments in this space included the completion of long-awaited projects, groundbreakings, and renovations. Other notable stories featured first-of-its-kind and record-breaking projects that could signal what the future of sports architecture could look like.Greener approaches to stadium design, along with a prioritization to integrate mixed-use schemes that, aside from sports, include public space, greater accessibility offerings, and even housing were common across projects this year.As part of Archinect's2024 Year In Review, take a look at some of the best sports architecture and stadium projects in our news this year.Previously on Archinect: New photos of Populous' modular Cricket World Cup stadium ahead of June gamesPopulous designs modular Cricket World Cup stadium on Long IslandIn January, Populous released designs for a modular, 34,000-seat cricket stadium for the Men's T2...0 Commentarii 0 Distribuiri 152 Views
ARCHINECT.COMStandout sports architecture and stadiums in 2024In 2024, there was no shortage of exciting news in the world of sports architecture and design. Developments in this space included the completion of long-awaited projects, groundbreakings, and renovations. Other notable stories featured first-of-its-kind and record-breaking projects that could signal what the future of sports architecture could look like.Greener approaches to stadium design, along with a prioritization to integrate mixed-use schemes that, aside from sports, include public space, greater accessibility offerings, and even housing were common across projects this year.As part of Archinect's2024 Year In Review, take a look at some of the best sports architecture and stadium projects in our news this year.Previously on Archinect: New photos of Populous' modular Cricket World Cup stadium ahead of June gamesPopulous designs modular Cricket World Cup stadium on Long IslandIn January, Populous released designs for a modular, 34,000-seat cricket stadium for the Men's T2...0 Commentarii 0 Distribuiri 152 Views





