0 Commentarios
0 Acciones
130 Views

Directorio
Directorio
-
Please log in to like, share and comment!
-
 WWW.GAMESPOT.COM28th Annual DICE Awards Nominees RevealedThe 28th annual DICE Awards has revealed the categories and nominees for this year's show. The show will be livestreamed on February 13 at 8 PM PT / 11 PM ET.For the coveted Game of the Year category this year, there are five games being considered--Astro Bot, Balatro, Black Myth: Wukong, Helldivers 2, and Indiana Jones and the Great Circle. The inclusion of Indiana Jones is notable since it wasn't considered at The Game Awards 2024 due to its December release date. Without further ado, here are the categories and their nominees. Outstanding Achievement in AnimationAstro BotCall of Duty: Black Ops 6Final Fantasy VII RebirthNevaWarhammer 40,000: Space Marine 2 Outstanding Achievement in Art DirectionBlack Myth: WukongIndiana Jones and the Great CircleLego Horizon AdventuresThe Plucky SquireSenua's Saga: Hellblade II Outstanding Achievement in Character1000xResist - WatcherFinal Fantasy VII Rebirth - Yuffie KisaragiIndiana Jones and the Great Circle - Dr. Henry "Indiana" JonesIndika - IndikaSenua's Saga: Hellblade II - Senua Outstanding Achievement in Original Music CompositionAstro BotHelldivers 2Monument Valley 3Senua's Saga: Hellblade IIStar Wars Outlaws Outstanding Achievement in Audio DesignFrostpunk 2Helldivers 2Monument Valley 3Senua's Saga: Hellblade IIStill Wakes the Deep Outstanding Achievement in Story1000xResistIndiana Jones and the Great CircleMetaphor: ReFantazioStill Wakes the DeepThank Goodness You're Here! Outstanding Technical AchievementAstro BotBatman: Arkham ShadowIndiana Jones and the Great CircleSenua's Saga: Hellblade IIWarhammer 40,000: Space Marine 2 Action Game of the YearBatman: Arkham ShadowBlack Myth: WukongCall of Duty: Black Ops 6Helldivers 2Stellar Blade Adventure Game of the Year1000xResistAnimal WellIndiana Jones and the Great CircleThe Legend of Zelda: Echoes of WisdomPrince of Persia: The Lost Crown Family Game of the YearAstro BotCat Quest IIILittle Kitty, Big CityThe Plucky SquireSuper Mario Party Jamboree Fighting Game of the YearBlazing StrikeDragon Ball: Sparking! ZeroMortal Kombat 1: Khaos ReignsTekke 8Underdogs Racing Game of the YearF1 24MotoGP 24Night-Runners Prologue Role-Playing Game of the YearFinal Fantasy VII RebirthDragon Age: The VeilguardElden Ring: Shadow of the ErdtreeLike a Dragon: Infinite WealthMetaphor: ReFantazio Sports Game of the YearEA Sports College Football 25EA Sports FC 25MLB The Show 24NBA 2K25 Strategy/Simulation Game of the YearBalatroCaves of QudFrostpunk 2Tactical Breach WizardsSatisfactory Immersive Reality Technical AchievementAlien: Rogue IncursionBatman: Arkham ShadowSkydance's BehemothStarship HomeUnderdogs Immersive Reality Game of the YearAlien: Rogue IncursionBatman: Arkham ShadowEscaping WonderlandSkydance's BehemothUnderdogs Outstanding Achievement for an Independent GameAnimal WellBalatroGrunnIndikaMouthwashing Mobile Game of the YearBalatroHalls of TormentMonument Valley 3Paper TrailWuthering Waves Online Game of the YearCall of Duty: Black Ops 6Diablo IV: Vessel of HatredHelldivers 2Marvel RivalsWarhammer 40,000: Space Marine 2 Outstanding Achievement in Game DesignAnimal WellAstro BotBalatroHelldivers 2UFO 50 Outstanding Achievement in Game Direction1000xResistAnimal WellLorelei and the Laser EyesRivenThank Goodness You're Here! Game of the YearAstro BotBalatroBlack Myth: WukongHelldivers 2Indiana Jones and the Great Circle0 Commentarios 0 Acciones 115 Views
WWW.GAMESPOT.COM28th Annual DICE Awards Nominees RevealedThe 28th annual DICE Awards has revealed the categories and nominees for this year's show. The show will be livestreamed on February 13 at 8 PM PT / 11 PM ET.For the coveted Game of the Year category this year, there are five games being considered--Astro Bot, Balatro, Black Myth: Wukong, Helldivers 2, and Indiana Jones and the Great Circle. The inclusion of Indiana Jones is notable since it wasn't considered at The Game Awards 2024 due to its December release date. Without further ado, here are the categories and their nominees. Outstanding Achievement in AnimationAstro BotCall of Duty: Black Ops 6Final Fantasy VII RebirthNevaWarhammer 40,000: Space Marine 2 Outstanding Achievement in Art DirectionBlack Myth: WukongIndiana Jones and the Great CircleLego Horizon AdventuresThe Plucky SquireSenua's Saga: Hellblade II Outstanding Achievement in Character1000xResist - WatcherFinal Fantasy VII Rebirth - Yuffie KisaragiIndiana Jones and the Great Circle - Dr. Henry "Indiana" JonesIndika - IndikaSenua's Saga: Hellblade II - Senua Outstanding Achievement in Original Music CompositionAstro BotHelldivers 2Monument Valley 3Senua's Saga: Hellblade IIStar Wars Outlaws Outstanding Achievement in Audio DesignFrostpunk 2Helldivers 2Monument Valley 3Senua's Saga: Hellblade IIStill Wakes the Deep Outstanding Achievement in Story1000xResistIndiana Jones and the Great CircleMetaphor: ReFantazioStill Wakes the DeepThank Goodness You're Here! Outstanding Technical AchievementAstro BotBatman: Arkham ShadowIndiana Jones and the Great CircleSenua's Saga: Hellblade IIWarhammer 40,000: Space Marine 2 Action Game of the YearBatman: Arkham ShadowBlack Myth: WukongCall of Duty: Black Ops 6Helldivers 2Stellar Blade Adventure Game of the Year1000xResistAnimal WellIndiana Jones and the Great CircleThe Legend of Zelda: Echoes of WisdomPrince of Persia: The Lost Crown Family Game of the YearAstro BotCat Quest IIILittle Kitty, Big CityThe Plucky SquireSuper Mario Party Jamboree Fighting Game of the YearBlazing StrikeDragon Ball: Sparking! ZeroMortal Kombat 1: Khaos ReignsTekke 8Underdogs Racing Game of the YearF1 24MotoGP 24Night-Runners Prologue Role-Playing Game of the YearFinal Fantasy VII RebirthDragon Age: The VeilguardElden Ring: Shadow of the ErdtreeLike a Dragon: Infinite WealthMetaphor: ReFantazio Sports Game of the YearEA Sports College Football 25EA Sports FC 25MLB The Show 24NBA 2K25 Strategy/Simulation Game of the YearBalatroCaves of QudFrostpunk 2Tactical Breach WizardsSatisfactory Immersive Reality Technical AchievementAlien: Rogue IncursionBatman: Arkham ShadowSkydance's BehemothStarship HomeUnderdogs Immersive Reality Game of the YearAlien: Rogue IncursionBatman: Arkham ShadowEscaping WonderlandSkydance's BehemothUnderdogs Outstanding Achievement for an Independent GameAnimal WellBalatroGrunnIndikaMouthwashing Mobile Game of the YearBalatroHalls of TormentMonument Valley 3Paper TrailWuthering Waves Online Game of the YearCall of Duty: Black Ops 6Diablo IV: Vessel of HatredHelldivers 2Marvel RivalsWarhammer 40,000: Space Marine 2 Outstanding Achievement in Game DesignAnimal WellAstro BotBalatroHelldivers 2UFO 50 Outstanding Achievement in Game Direction1000xResistAnimal WellLorelei and the Laser EyesRivenThank Goodness You're Here! Game of the YearAstro BotBalatroBlack Myth: WukongHelldivers 2Indiana Jones and the Great Circle0 Commentarios 0 Acciones 115 Views -
 WWW.GAMESPOT.COMFive Nights At Freddys: Into The Pit And Help Wanted 2 Are Getting Physical Editions Later This YearFive Nights at Freddys has become wildly popular in recent years, earning itself a movie adaptation in 2023 and boasting a catalog filled with over a dozen horror games. Later this year, two of its most recent games, Into the Pit and Help Wanted 2, are getting physical editions after previously only launching in digital formats (or making physical formats only available on select platforms). Both titles earned positive reviews, and if youre a fan of the series, theyre an easy recommendation. Best of all, Into the Pit comes with a nice bonus when you purchase the physical edition.Into the Pits physical edition is expected to arrive on June 20, while Help Wanted 2 will get physical editions for Switch and Xbox Series X around March 31 (though that date is likely to change). Preorders are now open ahead of their release, so consider reservering a copy if you plan on playing them later this year. Five Nights at Freddys: Into the Pit $30 | Releases June 20 The physical edition of Into the Pit will eventually launch for PS5, Xbox, and PS4, though only the Switch version is currently available to preorder. Into the Pit is a big departure for the series, featuring 2D side-scrolling gameplay that sees you solving various puzzles as you attempt to save your friends and family from a mysterious horror. As a bonus, the physical edition includes a download code for the games official soundtrack.If you want to dive deeper into the games lore, check out Fazbear Frights 4-Book Box Set. The first book in the collection is titled Into the Pit, and it's a great companion to the game. Since the box set is now just $22 (was $40), its the ideal time to check it out. Want even more frights? The Five Nights at Freddys 12-Book Box Set is $83 (was $150). Preorder at Amazon Five Nights at Freddys: Help Wanted 2 $40 | Releases March 31 A physical version of Help Wanted 2 is already available for PS5, but its coming to Switch and Xbox Series X later this year. Youll play as a new Fazbear employee as you try to prove to management that you have what it takes to handle all aspects of the job. The March 31 date listed on Amazon is likely a placeholder, so expect to learn more about a release date in the coming weeks.Preorders are open for Switch and Xbox, and the PS5 version is currently discounted to just $32 (was $40). You could also check out Security Breach on PS5, as its physical edition is also on sale for $33 (was $40). This survival horror game places you in the shoes of a boy trapped overnight in Freddy Fazbears Mega Pizzaplex, and youll need to overcome numerous horrors to escape at dawn. Preorder at Amazon (Switch) Preorder at Amazon (Xbox) Preorder at Best Buy More Gaming, Tech, and Entertainment Deals & Preorders Grab 3 Movies On 4K Blu-Ray For Only $33 At Amazon While You Can Final Fantasy 7 Remake Physical Edition Gets PS5 Reprint - Snag It While You Can The 2,500-Piece Legend Of Zelda Lego Set Is Now Available At Amazon + Show More More Gaming, Tech, and Entertainment Deals & Preorders Links (5) Mario Kart Lego Sets Are Available Now - Check Out All Six In The Launch Lineup Fortnite Lego Sets Launch At Major Retailers, Including Amazon And Walmart Backbone One iPhone And Android Controller Is 50% Off The Lord Of The Rings: The War Of The Rohirrim 4K Blu-Ray Steelbook Up For Preorder At Amazon Metaphor: ReFantazio Is Getting A Nearly 600-Page Official Strategy Guide0 Commentarios 0 Acciones 128 Views
WWW.GAMESPOT.COMFive Nights At Freddys: Into The Pit And Help Wanted 2 Are Getting Physical Editions Later This YearFive Nights at Freddys has become wildly popular in recent years, earning itself a movie adaptation in 2023 and boasting a catalog filled with over a dozen horror games. Later this year, two of its most recent games, Into the Pit and Help Wanted 2, are getting physical editions after previously only launching in digital formats (or making physical formats only available on select platforms). Both titles earned positive reviews, and if youre a fan of the series, theyre an easy recommendation. Best of all, Into the Pit comes with a nice bonus when you purchase the physical edition.Into the Pits physical edition is expected to arrive on June 20, while Help Wanted 2 will get physical editions for Switch and Xbox Series X around March 31 (though that date is likely to change). Preorders are now open ahead of their release, so consider reservering a copy if you plan on playing them later this year. Five Nights at Freddys: Into the Pit $30 | Releases June 20 The physical edition of Into the Pit will eventually launch for PS5, Xbox, and PS4, though only the Switch version is currently available to preorder. Into the Pit is a big departure for the series, featuring 2D side-scrolling gameplay that sees you solving various puzzles as you attempt to save your friends and family from a mysterious horror. As a bonus, the physical edition includes a download code for the games official soundtrack.If you want to dive deeper into the games lore, check out Fazbear Frights 4-Book Box Set. The first book in the collection is titled Into the Pit, and it's a great companion to the game. Since the box set is now just $22 (was $40), its the ideal time to check it out. Want even more frights? The Five Nights at Freddys 12-Book Box Set is $83 (was $150). Preorder at Amazon Five Nights at Freddys: Help Wanted 2 $40 | Releases March 31 A physical version of Help Wanted 2 is already available for PS5, but its coming to Switch and Xbox Series X later this year. Youll play as a new Fazbear employee as you try to prove to management that you have what it takes to handle all aspects of the job. The March 31 date listed on Amazon is likely a placeholder, so expect to learn more about a release date in the coming weeks.Preorders are open for Switch and Xbox, and the PS5 version is currently discounted to just $32 (was $40). You could also check out Security Breach on PS5, as its physical edition is also on sale for $33 (was $40). This survival horror game places you in the shoes of a boy trapped overnight in Freddy Fazbears Mega Pizzaplex, and youll need to overcome numerous horrors to escape at dawn. Preorder at Amazon (Switch) Preorder at Amazon (Xbox) Preorder at Best Buy More Gaming, Tech, and Entertainment Deals & Preorders Grab 3 Movies On 4K Blu-Ray For Only $33 At Amazon While You Can Final Fantasy 7 Remake Physical Edition Gets PS5 Reprint - Snag It While You Can The 2,500-Piece Legend Of Zelda Lego Set Is Now Available At Amazon + Show More More Gaming, Tech, and Entertainment Deals & Preorders Links (5) Mario Kart Lego Sets Are Available Now - Check Out All Six In The Launch Lineup Fortnite Lego Sets Launch At Major Retailers, Including Amazon And Walmart Backbone One iPhone And Android Controller Is 50% Off The Lord Of The Rings: The War Of The Rohirrim 4K Blu-Ray Steelbook Up For Preorder At Amazon Metaphor: ReFantazio Is Getting A Nearly 600-Page Official Strategy Guide0 Commentarios 0 Acciones 128 Views -
 GAMERANT.COMAll Stelae Locations (Belongs In A Museum) In Indiana Jones And The Great CircleThe sands of Gizeh hide many secrets in Indiana Jones and the Great Circle. As part of Gizeh's main adventure called 'The Idol of Ra' and related fieldwork quest 'Sanctuary of the Guardians,' you'll find one of several missing mysterious stone tablets called Stelae that Voss is hunting. However, a second Stelae List helps you track down all 10 missing Stelae in a Discovery quest called 'Belongs in a Museum.' If you're huffing and puffing your way across the desert trying to find all Stelae locations in Gizeh, this guide details how to complete 'Belongs in a Museum' and where to find all Stelae with less trouble.0 Commentarios 0 Acciones 113 Views
GAMERANT.COMAll Stelae Locations (Belongs In A Museum) In Indiana Jones And The Great CircleThe sands of Gizeh hide many secrets in Indiana Jones and the Great Circle. As part of Gizeh's main adventure called 'The Idol of Ra' and related fieldwork quest 'Sanctuary of the Guardians,' you'll find one of several missing mysterious stone tablets called Stelae that Voss is hunting. However, a second Stelae List helps you track down all 10 missing Stelae in a Discovery quest called 'Belongs in a Museum.' If you're huffing and puffing your way across the desert trying to find all Stelae locations in Gizeh, this guide details how to complete 'Belongs in a Museum' and where to find all Stelae with less trouble.0 Commentarios 0 Acciones 113 Views -
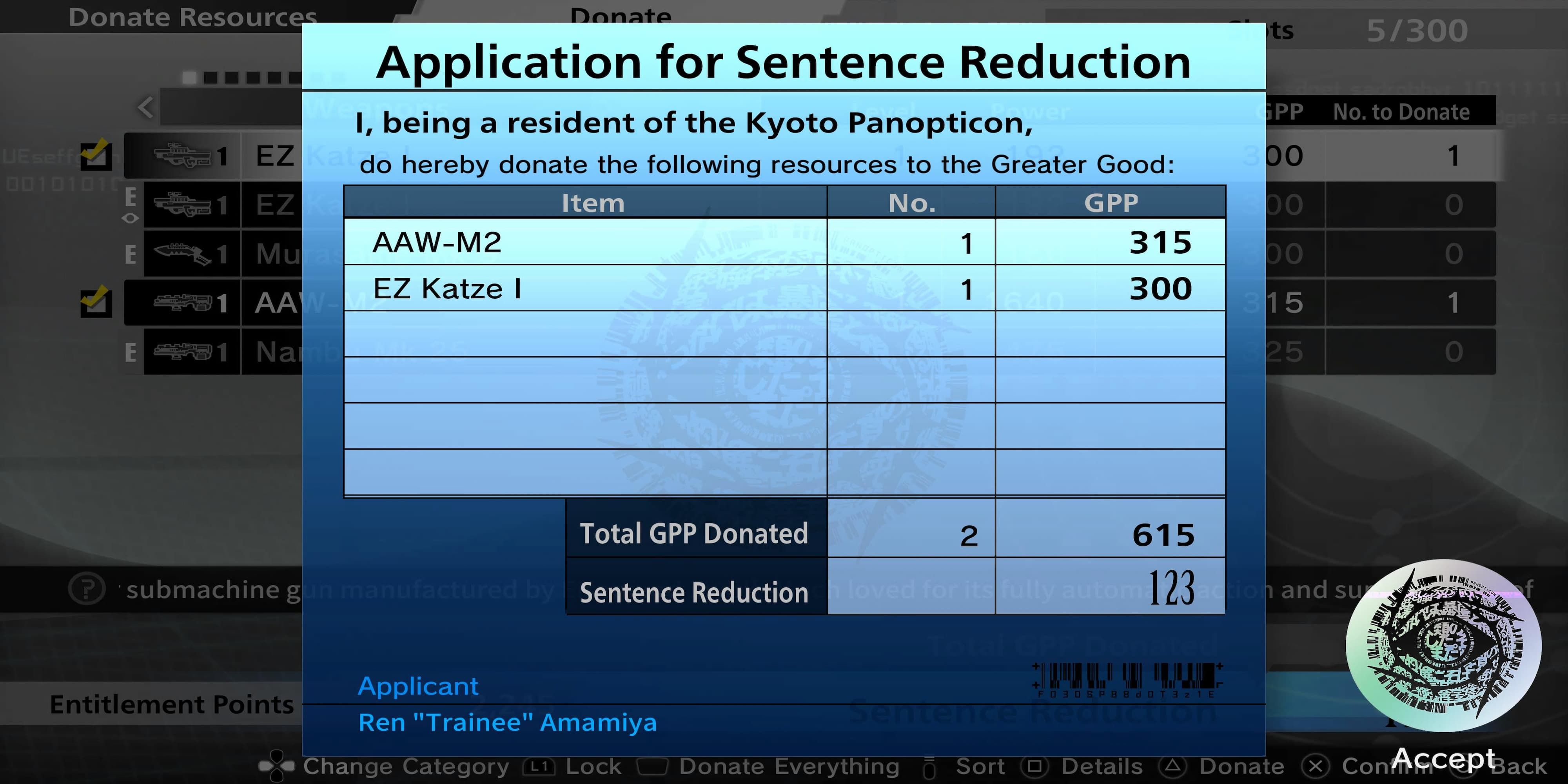 GAMERANT.COMShould You Donate Resources In Freedom Wars Remastered?A lot of the mechanics in Freedom Wars Remastered revolve around the general atmosphere of the world you're in, really making you feel like you're in prison working against impossible odds to earn your freedom. One way to knock years off your sentence is by donating items picked up from Operations.0 Commentarios 0 Acciones 119 Views
GAMERANT.COMShould You Donate Resources In Freedom Wars Remastered?A lot of the mechanics in Freedom Wars Remastered revolve around the general atmosphere of the world you're in, really making you feel like you're in prison working against impossible odds to earn your freedom. One way to knock years off your sentence is by donating items picked up from Operations.0 Commentarios 0 Acciones 119 Views -
 GAMERANT.COMBest Books That Inspired Popular Video GamesWith video games slowly evolving to become a complex medium full of everything from cathartic gameplay experiences to enrapturing stories, it's easy to see why some games take inspiration from real-life literature to become as captivating as possible. These books go a long way in helping establish a diverse world full of unique things and occurrences to keep in mind.0 Commentarios 0 Acciones 123 Views
GAMERANT.COMBest Books That Inspired Popular Video GamesWith video games slowly evolving to become a complex medium full of everything from cathartic gameplay experiences to enrapturing stories, it's easy to see why some games take inspiration from real-life literature to become as captivating as possible. These books go a long way in helping establish a diverse world full of unique things and occurrences to keep in mind.0 Commentarios 0 Acciones 123 Views -
 LIFEHACKER.COMThis 77-Inch OLED Smart TV Is $1,700 Off Right NowWe may earn a commission from links on this page. Deal pricing and availability subject to change after time of publication.If youve been holding out for a deal on a big-screen OLED TV, the Samsung 77-inch S84D might be worth a look. Its currently marked down to $1,599.99 at Best Buythats less than half its usual $3,299 price tag. The S84D benefits from OLEDs self-lit pixel technology, meaning its contrast is virtually unbeatable. Bright highlights pop against pitch-black backgrounds, perfect for dimly lit rooms or late-night movie marathons. And thanks to its lack of local dimming, theres no annoying blooming effect where bright spots bleed into dark areas. That said, while its HDR brightness is decent, its not the most dazzling OLED out there. Large bright scenes can look dimmer due to its aggressive Automatic Brightness Limiter (ABL), and HDR gaming takes a hit in Game Mode because of this.Still, for gamers, theres a lot to like. With support for 4K at 120Hz, VRR (Variable Refresh Rate), and super-low input lag, its great for the PS5, Xbox Series, or a high-end gaming PC. The lack of Dolby Vision support might disappoint some, but its performance with other HDR formats holds up. If youre into fast-paced games, its near-instantaneous response time promises clear motion with almost no blur. For everyday use, the TV excels in upscaling lower-resolution content like older DVDs or streams and its excellent viewing angles make it great for group watch parties. Additionally, the S84Ds reflection handling is said to really minimize glare (even in well-lit rooms).This smart TV features the 2024 version of Tizen OS, known for being quick and user-friendly. It offers a wide range of apps, making it simple to find your go-to streaming services. You can also cast content directly from your phone or play videos via a USB stick. The TV supports Bixby and Alexa voice assistants, with a remote that includes a built-in microphone for easy voice commandswhether youre launching apps, switching inputs, checking the weather, or adjusting brightness. However, when it comes to sound, the S84D reportedly falls short. While dialogue is clear at moderate volumes, the audio quality diminishes as you turn it up, and the lack of meaningful bass leaves action scenes or music sounding a bit flat.0 Commentarios 0 Acciones 95 Views
LIFEHACKER.COMThis 77-Inch OLED Smart TV Is $1,700 Off Right NowWe may earn a commission from links on this page. Deal pricing and availability subject to change after time of publication.If youve been holding out for a deal on a big-screen OLED TV, the Samsung 77-inch S84D might be worth a look. Its currently marked down to $1,599.99 at Best Buythats less than half its usual $3,299 price tag. The S84D benefits from OLEDs self-lit pixel technology, meaning its contrast is virtually unbeatable. Bright highlights pop against pitch-black backgrounds, perfect for dimly lit rooms or late-night movie marathons. And thanks to its lack of local dimming, theres no annoying blooming effect where bright spots bleed into dark areas. That said, while its HDR brightness is decent, its not the most dazzling OLED out there. Large bright scenes can look dimmer due to its aggressive Automatic Brightness Limiter (ABL), and HDR gaming takes a hit in Game Mode because of this.Still, for gamers, theres a lot to like. With support for 4K at 120Hz, VRR (Variable Refresh Rate), and super-low input lag, its great for the PS5, Xbox Series, or a high-end gaming PC. The lack of Dolby Vision support might disappoint some, but its performance with other HDR formats holds up. If youre into fast-paced games, its near-instantaneous response time promises clear motion with almost no blur. For everyday use, the TV excels in upscaling lower-resolution content like older DVDs or streams and its excellent viewing angles make it great for group watch parties. Additionally, the S84Ds reflection handling is said to really minimize glare (even in well-lit rooms).This smart TV features the 2024 version of Tizen OS, known for being quick and user-friendly. It offers a wide range of apps, making it simple to find your go-to streaming services. You can also cast content directly from your phone or play videos via a USB stick. The TV supports Bixby and Alexa voice assistants, with a remote that includes a built-in microphone for easy voice commandswhether youre launching apps, switching inputs, checking the weather, or adjusting brightness. However, when it comes to sound, the S84D reportedly falls short. While dialogue is clear at moderate volumes, the audio quality diminishes as you turn it up, and the lack of meaningful bass leaves action scenes or music sounding a bit flat.0 Commentarios 0 Acciones 95 Views -
 LIFEHACKER.COMOne of the Best Premium Soundbars of 2024 Is 50% Off Right NowWe may earn a commission from links on this page. Deal pricing and availability subject to change after time of publication.Most people buying TVs focus on the visuals, looking for words like 4K and OLED, meaning the audio aspect often takes a back seat. If you want to understand dialogue and not rely on subtitles, getting a soundbar is a must and will take your TV-watching experience to the next level. The best deal of the year so far on a quality soundbar is upon us: The Samsung Q990D 11.1.4ch Soundbar is on sale for $997.99 (originally $1,997.99) on Woot, a 50% discount. This is the lowest price this soundbar has been, according to price tracking tools. Samsung HW-Q990D Q-series 11.1.4ch Soundbar Wireless Subwoofer (2), Wireless Surround Speaker (Left/Right), HDMI Cable, Wall Mountable. $997.99 at Woot $1,997.99 Save $1,000.00 Get Deal Get Deal $997.99 at Woot $1,997.99 Save $1,000.00 The Samsung HW-Q990D Q-series 11.1.4ch soundbar is considered one of the best premium soundbars, even a year after its release. You get a wall-mountable soundbar with the wall-mount kit included, a wireless subwoofer, two wireless surround rear speakers (one left and one right), a remote control, and an HDMI 2.1 cable. The HDMI 2.1 is great for gamers since it allows 4K at 120Hz passthrough. There is also an eARC input, which is separate from the two HDMI 2.1 inputs, making it ideal to have two gaming consoles connected at the same time while able to switch to watch movies on your TV seamlessly. Of course, there's also wifi and Bluetooth connectivity, Dolby Atmos, DTS:X, Dolby 5.1, Dolby Digital Plus, and Dolby TrueHD for an immersive and dimensional audio experience. If you want to quickly connect to your sound system, you can connect your iPhone with AirPlay 2 or your Android with Chromecast or Alexa. Another cool feature is the Adaptive Sound, which auto-adjusts audio levels to optimize it depending on what you're watching (an action movie will have a different sound EQ to a drama). The SpaceFit Sound Pro tunes the audio depending on your room layout to also optimize the sound. There's also a Game Mode Pro feature for gamers that enhances directional sound, making full use of the surround sound. At 50% off, this soundbar system is the best value you can get for those looking for a premium audio experience.0 Commentarios 0 Acciones 128 Views
LIFEHACKER.COMOne of the Best Premium Soundbars of 2024 Is 50% Off Right NowWe may earn a commission from links on this page. Deal pricing and availability subject to change after time of publication.Most people buying TVs focus on the visuals, looking for words like 4K and OLED, meaning the audio aspect often takes a back seat. If you want to understand dialogue and not rely on subtitles, getting a soundbar is a must and will take your TV-watching experience to the next level. The best deal of the year so far on a quality soundbar is upon us: The Samsung Q990D 11.1.4ch Soundbar is on sale for $997.99 (originally $1,997.99) on Woot, a 50% discount. This is the lowest price this soundbar has been, according to price tracking tools. Samsung HW-Q990D Q-series 11.1.4ch Soundbar Wireless Subwoofer (2), Wireless Surround Speaker (Left/Right), HDMI Cable, Wall Mountable. $997.99 at Woot $1,997.99 Save $1,000.00 Get Deal Get Deal $997.99 at Woot $1,997.99 Save $1,000.00 The Samsung HW-Q990D Q-series 11.1.4ch soundbar is considered one of the best premium soundbars, even a year after its release. You get a wall-mountable soundbar with the wall-mount kit included, a wireless subwoofer, two wireless surround rear speakers (one left and one right), a remote control, and an HDMI 2.1 cable. The HDMI 2.1 is great for gamers since it allows 4K at 120Hz passthrough. There is also an eARC input, which is separate from the two HDMI 2.1 inputs, making it ideal to have two gaming consoles connected at the same time while able to switch to watch movies on your TV seamlessly. Of course, there's also wifi and Bluetooth connectivity, Dolby Atmos, DTS:X, Dolby 5.1, Dolby Digital Plus, and Dolby TrueHD for an immersive and dimensional audio experience. If you want to quickly connect to your sound system, you can connect your iPhone with AirPlay 2 or your Android with Chromecast or Alexa. Another cool feature is the Adaptive Sound, which auto-adjusts audio levels to optimize it depending on what you're watching (an action movie will have a different sound EQ to a drama). The SpaceFit Sound Pro tunes the audio depending on your room layout to also optimize the sound. There's also a Game Mode Pro feature for gamers that enhances directional sound, making full use of the surround sound. At 50% off, this soundbar system is the best value you can get for those looking for a premium audio experience.0 Commentarios 0 Acciones 128 Views -
 LIFEHACKER.COMFive Unexpected Things You Can Do With Windows Snipping ToolThe Windows Snipping Tool is best known for its screenshot-taking capabilitiesafter all, when you launch it from the Start menu, that's what it invites you to do. But Microsoft has packed a number of other unexpected, useful functions into this program.These extra features aren't particularly well-advertised nor easy to access, so you'll be forgiven if you've never come across them before. Open it via the Win+Shift+S keyboard shortcut or through the Start menu, and check out what it can do.Run an image searchIf you want to know more about an image you've capturedor any image on your system that you open up in the Snipping Toolyou can use it to run an image search on the internet. It's helpful for everything from shopping for products to looking up info about landmarks.To try it, open an image in Snipping Tool, click the three dots in the top right corner, then choose Visual Search with Bing. You'll be directed to Microsoft's search engine in your default browser, and from there you can click through on any result to see more.Extract text from images Extracting text from an image. Credit: Lifehacker The Snipping Tool also works well as an OCR (Optical Character Recognition) program. With a picture loaded up on screen, click the Text actions button at the top (the horizontal lines inside a frame) to identify text in an image and make it available to highlight.From there you can copy some or all of the text to the Windows clipboard and other programsvery handy if you need to pull text out of receipts or documents, for example. Click Quick redact to ignore any text containing email addresses and phone numbers.Scan QR codesLifehacker has written before about how the Snipping Tool can turn itself into a QR code reader, though this is limited to QR codes embedded in images; you can't scan a QR code that you've pointing your laptop's webcam at (which is probably for the best anyway).The process is the same as it is for text extraction: Open the image in the Snipping Tool, then click Text actions (the button with horizontal lines in a frame), and as long as the image you're dealing with has a QR code inside it, you'll see a clickable link appear on top.Record video and audio Switch to movie mode to record clips. Credit: Lifehacker This perhaps counts as a screenshot feature, but it's still worth mentioning: The Snipping Tool is a capable video and audio recorder, so you can use it to record whatever's going on your screen. Just click the movie camera button then the + New button (both top right).You have the option of recording the entirety of the screen, or just a particular section of it (by dragging the edges of the selection window). When the recording is in progress, a control bar appears at the top with options for including system and microphone audio.Editing images to add annotations or emojiThe Snipping Tool can also be a handy way to add highlights and annotations to your picturesremember, you can open any image in the app, not just screenshots. Maybe you want to highlight the key message in a text conversation, for example.With an image open inside the Snipping Tool, you'll see four buttons on the top toolbar: the pen, the highlighter, the eraser, and the shapes tool (which also lets you drop in emojis). Click once to select a tool, then click the button again to bring up its options.0 Commentarios 0 Acciones 133 Views
LIFEHACKER.COMFive Unexpected Things You Can Do With Windows Snipping ToolThe Windows Snipping Tool is best known for its screenshot-taking capabilitiesafter all, when you launch it from the Start menu, that's what it invites you to do. But Microsoft has packed a number of other unexpected, useful functions into this program.These extra features aren't particularly well-advertised nor easy to access, so you'll be forgiven if you've never come across them before. Open it via the Win+Shift+S keyboard shortcut or through the Start menu, and check out what it can do.Run an image searchIf you want to know more about an image you've capturedor any image on your system that you open up in the Snipping Toolyou can use it to run an image search on the internet. It's helpful for everything from shopping for products to looking up info about landmarks.To try it, open an image in Snipping Tool, click the three dots in the top right corner, then choose Visual Search with Bing. You'll be directed to Microsoft's search engine in your default browser, and from there you can click through on any result to see more.Extract text from images Extracting text from an image. Credit: Lifehacker The Snipping Tool also works well as an OCR (Optical Character Recognition) program. With a picture loaded up on screen, click the Text actions button at the top (the horizontal lines inside a frame) to identify text in an image and make it available to highlight.From there you can copy some or all of the text to the Windows clipboard and other programsvery handy if you need to pull text out of receipts or documents, for example. Click Quick redact to ignore any text containing email addresses and phone numbers.Scan QR codesLifehacker has written before about how the Snipping Tool can turn itself into a QR code reader, though this is limited to QR codes embedded in images; you can't scan a QR code that you've pointing your laptop's webcam at (which is probably for the best anyway).The process is the same as it is for text extraction: Open the image in the Snipping Tool, then click Text actions (the button with horizontal lines in a frame), and as long as the image you're dealing with has a QR code inside it, you'll see a clickable link appear on top.Record video and audio Switch to movie mode to record clips. Credit: Lifehacker This perhaps counts as a screenshot feature, but it's still worth mentioning: The Snipping Tool is a capable video and audio recorder, so you can use it to record whatever's going on your screen. Just click the movie camera button then the + New button (both top right).You have the option of recording the entirety of the screen, or just a particular section of it (by dragging the edges of the selection window). When the recording is in progress, a control bar appears at the top with options for including system and microphone audio.Editing images to add annotations or emojiThe Snipping Tool can also be a handy way to add highlights and annotations to your picturesremember, you can open any image in the app, not just screenshots. Maybe you want to highlight the key message in a text conversation, for example.With an image open inside the Snipping Tool, you'll see four buttons on the top toolbar: the pen, the highlighter, the eraser, and the shapes tool (which also lets you drop in emojis). Click once to select a tool, then click the button again to bring up its options.0 Commentarios 0 Acciones 133 Views -
WWW.ENGADGET.COMCES's Pebble Flow EV trailer gets some tweaks ahead of its spring shipping dateIt's always gratifying when something promised at CES actually comes to market. That's the case with the Pebble Flow electric trailer that my colleague Sam Rutherford checked out last year's CES. I was able to see the final draft on the show floor this week and was adequately impressed. Like the (four!) other sustainable, electrified tiny homes we saw this year, it was shiny and luxe and decked out in wood tones, glass, metal and white polymers. The main features that drew us to the Flow last year remain intact: sleeping for four, a 45 kWh battery and a 1.1 kW solar panel, full kitchen and bath, a queen-size Murphy bed that transforms into a shared working space and a convertible dinette at the other end. The kitchen faucet even spins 180-degrees and out the window to let you do some washing up outside. The option for the Magic Pack add-on is still here. For an upcharge, it allows the Flow to self-park, automatically hitch itself and provide it's own propulsion from dual motors so it's not such a drag (literally) on the vehicle that's towing it. One of the coolest features is still the glass separating the bathroom from the rest of the cabin. At the push of a button it goes from clear to opaque so you can have some privacy without having to kick your entire family out of the trailer. Amy Skorheim for Engadget As for what's new, those changes were partly sourced from prospective customers. One directive was "more windows," so a skylight was added, along with a larger window at the back. The cupboards are now easier to access by flipping up instead of down. And the overall shape was refined to be more aerodynamic. Walking around in the Flow, everything felt soothing and clean. The bed was so plush I wanted to melt into it. The seating area was inviting and spacious. It was tough to leave this homey pod (especially considering how stupendously hard it is to just find a place to sit down at CES). I don't have a vehicle that can pull a trailer, but I would love to park one of these in my backyard. Even if I never took it on the road, I'd happily hang out in its well-appointed comfort and even (reluctantly) give it up to guests when they visited. Production on the Flow will begin early this year and shipping is scheduled for spring. The option without the motor assist and self-parking features will go for $109,500. If you want the Magic Pack package, that brings your price to $135,500. There's also a "Founders Edition" with a limited-edition color scheme and a few more upgrades going for $175,000. This article originally appeared on Engadget at https://www.engadget.com/transportation/evs/cess-pebble-flow-ev-trailer-gets-some-tweaks-ahead-of-its-spring-shipping-date-161502791.html?src=rss0 Commentarios 0 Acciones 124 Views




