0 Commentarios
0 Acciones
129 Views

Directorio
Directorio
-
Please log in to like, share and comment!
-
WWW.BUSINESSINSIDER.COMThe wildfires have a Hollywood producer wondering: Should I even stay in LA?Los Angeles' fires threaten to hamper the entertainment industry's recovery.LA's share of film and TV jobs has declined, and some are thinking anew about leaving.One producer and director said he felt he could improve his financial situation by leaving LA.The fires tearing through Los Angeles are a new threat to an entertainment industry that has been trying to rebound from a studio spending slowdown and twin labor strikes."Survive till '25" was the mantra in Hollywood for much of 2024. Now, some in the entertainment industry are wondering whether they should stick around."If there's no longer a need to be in LA, the question arises: Do I stay here?" asked Adam Wood, a producer and director in North Hollywood. He said the shift during COVID to remote work had made it easier to build an entertainment career outside LA. Wood hasn't had to evacuate yet, but helped a friend leave and is monitoring conditions."I could improve my lot financially by not being here," he said. "LA is the spiritual home of the industry, but at the same time, it's not loving me back."Like many in entertainment, Wood works on a freelance basis. While he feels tied to the entertainment mecca, he said he's also counting the days of work lost to the fire. Producer and director Adam Wood. Adam Wood Productions and premieres have largely been pausedThe fires have paused production on shows including Amazon's "Fallout" and CBS Studios' "NCIS," while studios from Paramount to Universal canceled premieres.Stars, including Paris Hilton and Billy Crystal, havelost their homesin the tony Pacific Palisades neighborhood, which is favored for its proximity to the studios. Countless others have lost or fled their homes.FilmLA, the city's film permitting office, issued a statement Thursday warning that permits in or near evacuation zones could be canceled, while new applications to film in or near these areas would be denied.It previously said the LA County Fire Department ordered film permits to be revoked for the communities of Altadena, La Crescenta, La Canada/Flintridge, and Unincorporated Pasadena.Hollywood was already hurting before the firesBefore the fires, the entertainment spending slowdown had already hit the industry's biggest market hard.LA has also been hobbled by an exodus of productions and workers to other entertainment hubs in lower-cost places like Atlanta and Miami. Greater Los Angeles' share of US-produced TV and film projects declined from 23% in 2021 to 18% in 2023, according to FilmLA.LA accounted for 22% of US film and TV jobs in August, down from 33% two years earlier, according to an analysis of Bureau of Labor Statistics figures by Patrick Adler and Taner Osman of Westwood Economics & Planning Associates.Despite the downturn, producer Adam Fratto said he had been feeling pretty good about the state of the industry before the fires started."I was taking some projects out, and who knows if they're going to sell, but the fact that TV folks were open to pitches, that's good," he said. "Before a couple days ago, I felt a little upbeat about 2025."While it's still early to say how far the destruction could spread, Fratto said he expected the fires to cause some people to reassess their commitment to the area and industry."I think there will be folks who just decide to take their chips off the table and do something else or relocate," he said.Still, Adler, the economic researcher, said he doubted LA would lose its position at the top of the entertainment industry."In the likes of film, television, content creation, and video games, LA has been the place where major decisions have been made, where talented people collaborate, and where deals get done," he said. "This has remained true as the city has persevered through multiple earthquakes and riots, not to mention periodic industry downturns."0 Commentarios 0 Acciones 126 Views
-
WWW.BUSINESSINSIDER.COM2025 TV shows we're most excited about, from the return of 'Stranger Things' to the new 'Game of Thrones' prequel"Severance," season 2Adam Scott stars in "Severance." Apple TV Plus Release date: January 17 on Apple TV+Watching the first season of "Severance" in early 2022 felt a bit like getting in on an extraordinary secret. This bizarre, endearing, and incredibly stylistic take on the soul-crushing office grind quickly yet quietly became one of the best genre series on television. Three years later, the show blessedly is not a hidden gem anymore, and "Severance" season two is coming in hotly anticipated.The series stars Adam Scott as Mark, a man who decides to take a "severed" job after the death of his wife. The severance procedure bifurcates his personality into two discrete people: one who works his job at the inscrutable Lumon Industries, and one who lives life on the outside. In season one, he and his coworkers work to expose their plight as severed workers to the world, while simultaneously unraveling the myriad secrets of their workplace. Palmer Haasch "Paradise"Sterling K. Brown in "Paradise." Brian Roedel/Disney Release date: January 28 on Hulu"This Is Us" creator Dan Fogelman and star Sterling K. Brown reunite on a new Hulu series. The mystery thriller focuses on Xavier Collins (Brown), the head of security to James Marsden's President Cal Bradford. Xavier finds Cal dead and is said to be the last person who saw the president alive, thrusting him into the middle of an apparent conspiracy.The trailer is light on specific details, but according to the streamer the show is set "in a serene, wealthy community inhabited by some of the world's most prominent individuals," who are rattled by the president's murder and the ensuing investigation.Brown was always a highlight of "This Is Us," so it's exciting to see him step into another lead role that appears to be very different from Randall Pearson. "Yellowjackets," season 3Tawny Cypress as Taissa and Lauren Ambrose as Van in "Yellowjackets" season 3. Colin Bentley/Paramount+ with SHOWTIME Release date: February 14 on Paramount+ with Showtime (and February 16 on Showtime)"Yellowjackets" is a mish-mash of genres: part coming-of-age story, part survival drama, part black comedy, part mystery.When it first premiered in 2021, it wasn't an instant hit. Rather, it steadily grew a passionate fan base as more and more viewers became invested in this tale of a group of teenage girls who became stranded in the Canadian wilderness in the 1990s and the repercussions of that traumatic experience on the surviving women 25 years later.Creators Ashley Lyle and Bart Nickerson managed to craft a wildly compelling story that drew equal interest to both halves of its cast: the talented rising stars who play the '90s versions of the girls (including breakouts like Ella Purnell and Sophie Thatcher), and the established powerhouse actors like Juliette Lewis, Melanie Lynskey, and Christina Ricci in the modern-day setting.Season two answered a lot of questions (including arguably the biggest: Did they eat each other??) but ended on an unexpected death that left fans clamoring to know what would happen next. Luckily, there are still plenty of mysteries waiting to be solved. CM "The White Lotus," season 3Blackpink member Lisa on season three of "The White Lotus." HBO Release date: February 16 on HBO and MaxThere's little information about season three of "The White Lotus." But Mike White's hit HBO anthology series, which racked up a total of 43 Emmy nominations from the first two seasons, has generated enough hype all on its own for the next installment.Season three will focus on wealthy guests visiting the fictional White Lotus resort chain's Thailand location. And for the first time ever, the new season will feature a returning cast member: Natasha Rothwell, who played spa manager Belinda in season one. The star-studded cast also includes Blackpink member Lisa in her acting debut, "Fallout" star Walton Goggins, and "Gen V" actor Patrick Schwarzenegger who told Business Insider that season three is "Absolutely fucking insane." Olivia Singh "Zero Day"Robert DeNiro and Angela Bassett star in "Zero Day." Netflix Release date: February 20 on NetflixRobert De Niro on a Netflix drama? OK, sure, we're in."Zero Day" is a political thriller focusing on a global cyberattack, where De Niro plays a former president who comes out of retirement to help mitigate the crisis. The impressive ensemble cast also includes Lizzy Caplan as his daughter, Angela Bassett as the current president, and Dan Stevens as a loudmouth political TV host who antagonizes De Niro. "Suits: LA"Stephen Amell stars in "Suits LA." David Astorga/NBC Release date: February 23 on NBC and Peacock"Suits" mania very suddenly and randomly swept over the nation when the 2010s USA Network drama saw a resurgence of interest on Netflix. Why? Who knows chalk it up to one of the great mysteries of the algorithm.In any event, it prompted the greenlighting of a spinoff series that shifts the action from a corporate firm in New York to an entertainment firm in Los Angeles. The new series centers on Stephen Amell's Ted Black, a former New York prosecutor who has reinvented himself out west. Don't expect Meghan Markle to show up on it, but we can still hold out hope for other fan-favorite characters: Gabriel Macht's Harvey Specter is reportedly set for a three-episode arc, which hopefully means Donna Paulsen (Sarah Rafferty) isn't far behind. CM "Daredevil: Born Again"Charlie Cox in "Daredevil." Netflix/Marvel Entertainment Release date: March 4 on Disney+The Marvel series will see Charlie Cox reprise his role as Matt Murdock, a blind lawyer by day, and a vicious vigilante by night. Because it's a continuation of the "Daredevil" Netflix series (which is exciting in itself) it'll also reunite Cox with Vincent D'Onofrio as Wilson Fisk, the criminal mastermind, Kingpin. Not only that but "Daredevil: Born Again" will add a harder, violent edge to the Marvel Cinematic Universe.Hopefully Marvel chief Kevin Feige and the gang let the show stand on its own two bloody feet without forcing needless cameos for the sake of it. After all, a street-level story with relatable stakes is what the franchise needs right now amid all the chatter of future "Avengers" movies. Eammon Jacobs "Deli Boys"Saagar Shaikh and Asif Ali in "Deli Boys." Elizabeth Sisson/Disney Release date: March 6 on Hulu"Deli Boys" (created by former Vice journalist Abdullah Saeed) follows the two wealthy Pakistani American sons of a convenience store magnate who learn after his death that he was secretly involved in a life of crime.The polar opposite brothers are forced into that world, promising a unique take on the fish-out-of-water story coming to Hulu. CM "The Residence"Uzo Aduba and Randall Park in "The Residence." Erin Simkin/Netflix Release date: March 20 on NetflixMarket your series as a "Shondaland White House whodunnit," and you don't have to do too much more to convince me. After a murder at a state dinner, Detective Cordelia Cupp, played by Uzo Aduba, must attempt to solve the case. On-screen, she's joined by Giancarlo Esposito, Randall Park, Ken Marino, Edwina Findley, and a slate of others including Kylie Minogue."Scandal" writer Paul William Davies serves as showrunner, with Shonda Rhimes and Betsy Beers executive producing. "The Residence" is based on the book of the same name by Kate Andersen Brower. PH "The Last of Us," season 2Bella Ramsey as Ellie in "The Last of Us" season two. HBO Release date: April on HBO and Max"The Last of Us" season one turned prestige gaming into prestige television, adapting Naughty Dog's fungal apocalypse thriller into an acclaimed series starring Pedro Pascal and Bella Ramsey. Season one ended on a tenuous high note: Joel (Pascal) chose to save Ellie (Ramsey), who is immune to the cordyceps fungus that turns people into violent infected, rather than allowing her death in pursuit of a cure."The Last of Us" season two will adapt at least part of "The Last of Us Part II," the sequel to the original video game. Without getting too much into spoilers, it's likely to be even more heartbreaking than season one. This season will also feature newcomers including Kaitlyn Dever, who will play a significant character named Abby, "Beef" star Young Mazino, and Jeffrey Wright, who will reprise his role from the game, Isaac. PH "Your Friends and Neighbors"Jon Hamm leads a new TV show. Apple TV+ Release date: April 11 on Apple TV+Apple TV+ has had no shortage of prestige drama attempts, from the Cate Blanchett series "Disclaimer" to Natalie Portman's "Lady in the Lake." Not all of them are very good (and a lot of them appear to come and go with little to no fanfare), and yet I still have enough faith in Jon Hamm and his ability to play complex antiheroes that I'm compelled to tune into "Your Friends & Neighbors."Hamm plays Andrew "Coop" Cooper (Hamm), a recently divorced former hedge fund manager who's fired in disgrace. According to Apple, Coop, who lives in the wealthy Vestment Village, begins stealing from his neighbors' homes but ends up uncovering more secrets (and danger) than he bargained for.The show also stars Amanda Peet and Olivia Munn, among others. And the streamer clearly has a lot of faith in it: They've already renewed it for a second season, months ahead of its premiere. CM "Hacks," season 4Jean Smart and Hannah Einbinder return in "Hacks" season 4. HBO Release date: (rumored) May on MaxThe Emmy Award-winning "Hacks" is a series that only gets better with age, and its excellent third season set a high bar for whatever will come next. The series stars Jean Smart as Deborah Vance, a comedian who turns around her stale Vegas stand-up career into a true artistic reinvention with the help of young writer Ava Daniels, played by Hannah Einbinder.Deborah and Ava's relationship has always been defined by an ever-growing co-dependence, the capacity to mutually wound each other, and somewhere in the mix, love and grudging respect. The season three finale put them at odds once again, setting up for what's sure to be a thrilling and of course, extremely funny fourth season. PH "Chad Powers"Glen Powell returns to TV in "Chad Powers." Daniel Delgado/Disney Release date: Fall 2025 on HuluGlen Powell has been all over our movie screens for the last three years, and now he'll be all over our small screens.Powell, one of the biggest male rising actors in Hollywood today, is on a movie star trajectory akin to his mentor (and "Top Gun: Maverick" costar) Tom Cruise. He has roots in TV, though ("Scream Queens," I will never forget you). The upcoming Hulu comedy, about a hotshot quarterback who torpedoes his college football career and disguises himself as Chad Powers to walk onto a Southern university's team, is a great venue for flexing his funny chops.At the absolute least, the visual of Powell in those prosthetics and wig is already a hoot. CM "Stranger Things," season 5The cast of "Stranger Things" season five with Matt and Ross Duffer. Atsushi Nishijima/Netflix Release date: TBD on NetflixThese days, it's hard to fathom that "Stranger Things" was one of the relatively early hits of the streaming age when it premiered in 2016. Close to a decade later, it's a cultural juggernaut that elevated the profile of its entire cast, from veteran actors to young stars. With one season left, it's finally time to close this chapter of life in Hawkins, Indiana."Stranger Things" season five will bring an end to Eleven's (Millie Bobby Brown) story, but past that, it will represent the true end of an era at Netflix. "Stranger Things" is one of the biggest series the streamer has ever released, but even if the show is ending, some talent like showrunners Matt and Ross Duffer and Brown, now a leading lady, are sticking around with other projects. PH "Wednesday," season 2Jenna Ortega returns in "Wednesday" season 2. Netflix Release date: TBD on Netflix"Wednesday" was a smash hit when it premiered on Netflix in 2022. Over two years later, it's still holding strong atop the streamer's list of its most-watched shows ever, with over 252 million views to date.The supernatural teen dramedy's success is due in large part to the performance of Jenna Ortega as the titular Wednesday Addams, the sardonic, psychic teen who finds herself thrust into the center of a murder mystery when she's shipped off to a new boarding school.The first season ended with a twist about one of Wednesday's two love interests, but Ortega has promised that "Wednesday" season two will lean more into horror and focus less on her character's romantic life. That's a very welcome tweak. CM "Black Mirror," season 7Cristin Milloti as Nanette Cole in the "Black Mirror" episode "USS Callister." Jonathan Prime / Netflix Release date: TBD on NetflixThe long-running dystopian anthology series where each episode is a stand-alone story of speculative fiction, with most set in a near-future world with advanced, often ethically troublesome technology returns for its seventh outing later this year.As with recent seasons, there are some big names lined up for the "Black Mirror" season seven cast, including Awkwafina, Issa Rae, Paul Giamatti, Billy Magnussen, and Tracee Ellis Ross. But perhaps most excitingly, for the first time in the series' history, there's going to be a story continuation: One of the six new episodes will be a sequel to "USS Callister," the Emmy-winning season four episode starring Cristin Milioti as a programmer who gets trapped in her incel boss' video game world. CM "You," season 5"You" will return for its fifth and final season. Netflix Release date: TBD on NetflixObsessive stalker Joe Goldberg has somehow managed to evade capture or consequences in his yearslong killing spree that's spanned four seasons of television and multiple cities across the globe. He seemed to finally be at the end of the line in "You" season four, only to miraculously make it out with a seemingly clean slate yet again. The finale brought Joe full circle back to New York, and partnered with a woman who may or may not see him for who he truly is.The fifth and final season of "You" will hopefully bring a satisfying conclusion to the drama that's managed to keep reinventing itself and finding ways to creatively continue the story long past where many assumed it'd surely end. CM "Squid Game," season 3Lee Jung-jae returns to the death game in "Squid Game" season two. JuHan Noh / Netflix Release date: TBD on Netflix"Squid Game" isn't only Netflix's biggest non-English-language series it's also one of its biggest properties, period. The Korean-language series, created by showrunner Hwang Dong-hyuk, is a deeply tragic thriller with an instantly recognizable visual identity. Both of those factors helped it become not only a hit series, but also a true cultural phenomenon. "Squid Game" season two, which premiered in December, broke viewership records to become Netflix's biggest debut ever.Even if you didn't watch "Squid Game," you know "Squid Game" and with the show's third and final season on the way in 2025, you definitely should be catching up. PH "A Knight of the Seven Kingdoms""A Knight of the Seven Kingdoms" is an adaptation of G.R.R. Martin's novella "The Hedge Knight." Steffan Hill/HBO Release date: TBD on HBO and MaxGiven the wild success of "Game of Thrones," it makes sense that HBO would go all-in on the "Thrones" brand through a series of spinoffs. The first of those, "House of the Dragon," focuses on a bloody Targaryen succession war. The second, "A Knight of the Seven Kingdoms," is about a knight and his young squire Dunk and Egg, colloquially. Dunk is Ser Duncan the Tall, and Egg is Aegon Targaryen, a young member of the ruling family.The series is based on the first installation of George R. R. Martin's "Tales of Dunk and Egg" novella series, titled "The Hedge Knight." HBO drama headDeadline in 2023 that the show would ideally span three seasons, one for each existing novella. PH "Alien: Earth""Alien: Earth." FX Release date: TBD on FX and HuluFX is expanding the "Alien" franchise with a new TV series that finally brings the unimaginable horrors of the Xenomorphs to Earth in the aptly titled "Alien: Earth."The first teaser trailer didn't reveal much about the series, but it's helmed by "Legion" and "Fargo" creator Noah Hawley, which hopefully means that the series will have more to say than just sci-fi scares. It features the likes of "Justified" and "The Mandalorian" star Timothy Olyphant, "Andor" and "Black Mirror" actor Alex Lawther, and "Fargo" alumni David Rysdahl. Also in the cast are Essie Davis, Sydney Chandler, and Samuel Blenkin. EJ Untitled Rachel Sennott projectRachel Sennott wrote, executive produced, and stars in her upcoming show. HBO Release date: TBD on HBO and MaxRachel Sennott has been a standout part of some of the best comedies of the last few years, including "Bottoms," "Shiva Baby," and the horror comedy "Bodies Bodies Bodies." The comedian is stepping up as HBO's new Lena Dunham (non-derogatory), helming a series that she's writing, executive producing, and starring in.No details about its plot have been made available, but Sennott has proven herself to be imminently watchable, so we're certainly tuning in to see what she's got in store. CM "Good American Family"Ellen Pompeo stars in "Good American Family." Hulu Release date: TBD on HuluIt's a tale as old as time: Where there's a viral true-crime story, a scripted dramatization (or five) is sure to follow. That's the case with "Good American Family" (not to be confused with the similarly named faith-based TV network Great American Family), which is loosely inspired by Natalia Grace Mans' story.Natalia's saga is long and complex (enough to fill three seasons of the Investigation Discovery docuseries "The Curious Case of Natalia Grace" over the course of three years). The gist of it is that Natalia, a Ukrainian orphan with dwarfism, was adopted by Kristine and Michael Barnett, who eventually came to believe that their new daughter was actually a psychopathic adult posing as a child. (Yes, that is also generally the plot of the horror movie "Orphan," which wasn't based on Natalia's story).Ellen Pompeo, in her first major starring role since stepping back from "Grey's Anatomy" as a series regular, stars as the girl's adoptive mother. It'll be interesting to see whether the scripted drama is more sympathetic to the Barnetts' side or Natalia's. CM "It: Welcome to Derry""It: Welcome to Derry" is a prequel to the Stephen King story. Brooke Palmer/Photo: Brooke Palmer Release date: TBD on HBO and Max"It Chapter 1" and "It Chapter 2," based on the Stephen King novel of the same name, were mega-hits at the box office when they came out in 2017 and 2019 respectively. Pennywise the Clown had previously terrorized audiences in the form of Tim Curry in a 1990 miniseries before Bill Skarsgard scarred a new generation when he took over the role. "Welcome to Derry" is the first time the story is getting the prequel treatment.The show jumps back in time to explore an earlier community in Derry who came face to face with the monstrous creature. It features new characters not seen in the films, with only Skarsgard returning. CM "Outlander: Blood of My Blood"Sam Heughan as Jamie Fraser and Caitriona Balfe as Claire Fraser in "Outlander" season seven. Starz Release date: TBD on StarzThe smash hit historical drama "Outlander" has captivated audiences (both readers of the book series it's based on and show-only fans) for over a decade since premiering in 2014.Claire and Jamie Fraser's epic love story will come to an end with an eighth and final season. But the "Outlander" universe will live on with "Blood of My Blood," a prequel that rewinds the clock to show how Jamie's parents, and Claire's, wound up together.If the prequel's cast has even a fraction of the chemistry "Outlander" leads Sam Heughan and Caitrona Balfe do, it'll be must-see TV for romance lovers. CM "Dying for Sex"Michelle Williams in "Dying for Sex." Sarah Shatz/FX Release date: TBD on FX and HuluMichelle Williams, who previously won an Emmy and Golden Globe for her role in the FX limited series "Fosse/Verdon," returns to the network with "Dying For Sex." She plays Molly, an unhappily married woman who decides to leave her husband in order to explore her sexuality after being diagnosed with cancer.Billed as a comedy-drama, it's based on the podcast of the same name by Nikki Boyer. Boyer, who's also an executive producer on the FX show, co-created her podcast with her friend the real Molly, who actually did leave her own marriage after a breast cancer diagnosis. Jenny Slate plays Boyer on the show; Rob Delaney and Jay Duplass also star.Beyond the compelling true story and excitement over the talented Williams' return to TV, "New Girl" creator Liz Meriwether also serves as a showrunner, promising whip-smart writing. CM "The Terror: Devil in Silver"Dan Stevens is producing and starring in "The Terror: Devil in Silver." Emma McIntyre/Getty Images; Random House Publishing Release date: TBD on AMC and AMC+The criminally underrated supernatural horror anthology series gathered a small but devoted fan base after the first season, based on Dan Simmons' 2007 novel of the same name, premiered in 2018.That season told an extremely spooky fictionalized account of Captain Sir John Franklin's doomed Arctic expedition and featured a who's-who of British actors like Jared Harris and Tobias Menzies. The next season, subtitled "Infamy," debuted a year later and moved the horror to a Japanese internment camp in America during World War II, where the camp's inhabitants believe they're being tormented by an evil force.AMC stayed mum on whether the show would continue for almost five years, until the February 2024 announcement that "The Terror: Devil in Silver" was coming. The upcoming six-episode season, based on Victor LaValle's novel of the same name, will star Dan Stevens (who's also an EP) as a working-class man wrongfully committed to a psychiatric hospital where he has to contend not only with the other patients and the doctors but a seemingly malevolent force that appears to live within the hospital's walls.Stevens is a great choice for this brand of psychological horror. See also: "Legion." CM "All's Fair"Kim Kardashian, Naomi Watts, and Sarah Paulson are all reuniting with Ryan Murphy on "All's Fair." Karwai Tang/Getty Images; Jon Kopaloff/Getty Images; John Nacion/FilmMagic via Getty Images Release date: TBD on HuluRyan Murphy regulars, assemble!The prolific TV creator is fresh off a busy 2024 that included the premieres of four separate shows he produced, including "Grotesquerie" and the controversial "Monsters: The Lyle and Erik Menendez Story." He doesn't appear to be taking it easy in 2025 either.It's unclear whether he'll again match the sheer number of projects he debuted in 2024, but he definitely has at least one coming out: "All's Fair," a legal drama about an all-female law firm of divorce attorneys coming to Hulu. The cast includes a bunch of Murphy's go-tos, including his frequent collaborator Sarah Paulson, "Feud: Capote vs. the Swans" star Naomi Watts, "Grotesquerie" star Niecy Nash, and his most recent addition to the crew, aspiring real-life lawyer Kim Kardashian, who starred in "American Horror Story" season 12.Kardashian was surprisingly good in "AHS," so it's intriguing to see what she'll do in "All's Fair," where she's reportedly playing the protagonist. CM "Unspeakable: The Murder of JonBent Ramsey"Clive Owen and Melissa McCarthy will play JonBent Ramsey's parents. Michael Tullberg/Getty Images; Helen H. Richardson/The Denver Post/Getty Images; Alberto E. Rodriguez/Getty Images Release date: TBD on Paramount+Few true crime cases have captivated the public as intensely and for as long as JonBent Ramsey's unsolved murder. The six-year-old beauty queen was found dead in her family home the day after Christmas 1996, and her killer was never identified.The long-cold case was recently covered in a Netflix docuseries, which led to a resurgence of interest (though plenty of true-crime enthusiasts have been carefully following the case for years). The story has been dramatized before, in a 2000 miniseries and multiple TV movies, but this is the first time it's getting what appears to be the prestige TV treatment.Most intriguingly, the series will star Melissa McCarthy as Patsy Ramsey, JonBent's mother. This will mark an interesting pivot for McCarthy, who's chiefly known for far more light-hearted roles in comedies like "Bridesmaids" and "Tammy." CM0 Commentarios 0 Acciones 127 Views
-
WWW.BUSINESSINSIDER.COMThe Kremlin said Greenland is in Russia's sphere of 'national and strategic interests' — and it's got its eye on Trump's claims on the territoryThe Kremlin is closely watching Greenland after Trump expressed interest in the US acquiring it.The Kremlin's press secretary said the Arctic is a zone of national interest for Russia.Trump said earlier this week that he would not rule out using military force to seize Greenland.Russia is keeping a close eye on President-elect Donald Trump's interest in acquiring Greenland.The Kremlin's press secretary, Dmitry Peskov, said that Russia is "watching the rather dramatic development of the situation very closely," according to areportby Reuters."The Arctic is a zone of our national interests, our strategic interests," Peskov said. "We are interested in preserving the atmosphere of peace and stability in the Arctic zone."Russia has ramped up its military presence in the Arctic in recent years. For example, it has deployed a substantially larger fleet of icebreaker ships which break up ice in strategic waterways and increase maneuverability for other ships to the Arctic than the US.Trump, who expressed interestin buying Greenland as early as 2019,resurfacedhis proposition in December and has since doubled down on his stance.In a press conference on Tuesday, Trump said that he would not rule out using force to secure Greenland, which is an autonomous Danish territory, and regain control of the Panama Canal, a critical waterway for trade.When asked for assurance that he would not resort to "military or economic coercion" to seize the two, he said, "I can't assure you.""I'm not going to commit to that," he added."People really don't even know if Denmark has any legal right to it, but if they do, they should give it up because we need it for National Security," he said of Greenland in the press conference.He then threatened to impose tariffs on Denmark "at a very high level" if the Scandinavian country resisted giving up control of the Arctic territory.Russia's statement comes after Trump's son, Donald Trump Jr., landed in Greenland on Tuesday and met with locals in Nuuk, the capital city, according to his X posts.A Tuesday video on his X showed the president-elect calling his son to talk to Nuuk locals.In response to Trump's comments, Denmark's Prime Minister Mette Frederiksen said to a local news outlet on Tuesday that Greenland is "not for sale."Greenland's Prime Minister, Mte Egede, said in a December Facebook statement, "We are not for sale and will never be for sale."Trump, meanwhile, has also talked about seizing control of the Panama Canal, a roughly 50-mile canal built in 1914 to link the Pacific and Atlantic oceans. It was under US control until it was given to the Panama Canal Authority (PCA) in 1999.Trump called for the canal's control to bereturned to the US, slamming "exorbitant" fees for US ships passing through it.Representatives of Trump and the Kremlin did not respond to requests for comment from Business Insider, sent outside regular business hours.0 Commentarios 0 Acciones 129 Views
-
 WWW.DAILYSTAR.CO.UKIs Marvel Rivals down? Season 1 release information and server downtime scheduleMarvel Rivals servers are down today as NetEase preps to launch Season 1, which is set to introduce a ton of new features from new maps and heroes, to ranked changes and a new Doom Match game mode.News07:07, 10 Jan 2025Updated 07:10, 10 Jan 2025Marvel Rivals serves are down for the Season 1 update that's rolling out today and introduces the first two members of the Fantastic Four(Image: netease)With the initial Season 0 wrapped up, NetEase is rolling out Marvel Rivals Season 1 today, accompanied by update v20250110. This update primarily focuses on hero adjustments rather than team-up abilities for now.As NetEase prepares to launch Season 1, Marvel Rivals servers are offline today. The new season promises a plethora of new features including new maps and heroes, ranked changes, and a fresh Doom Match game mode.Alongside these additions, players can anticipate numerous balancing tweaks, with NetEase providing more specific details in the early Marvel Rivals patch notes. The much-anticipated arrival of the Fantastic Four is a highlight for many players, with Mister Fantastic and the Invisible Woman making their debut today, once the Marvel Rivals servers are back online.Marvel Rivals could be adding more characters very soonSeason 0 was brief, lasting only five weeks, but it appears that NetEase is planning to go bigger and adopt the mid-season update approach used by games like Warzone and Diablo 4. In line with this, Marvel Rivals Season 1 will be a double season, featuring a second update at the mid-point introducing the Human Torch and The Thing, thus completing Marvel's First Family in the game.Marvel Rivals fans, brace yourselves for a big shake-up as the servers spark back into action with some hefty changes one hotly requested tweak sees Jeff the Land Shark getting put on a leash with a major nerf. If you've been caught up in the whirlwind of this hero shooter's craze, today's update is set to crank up the excitement even more; and if you're just dipping your toes into Marvel Rivals waters, now couldn't be a better time with all the fresh content dropping in today, reports the Mirror.The Marvel Rivals servers are powering down today at the crack of dawn, at 7am GMT / 2am EST, which translates to yesterday night, 11pm PST, for the US west coast night owls. And heres a heads up you might get the boot a tad early, much like Fortnite players do when they're ousted 30 minutes pre-scheduled maintenance.According to the game's official Twitter page, we're looking at servers being back in business by 9.10am GMT / 4.10am EST / 1.10am PST so just sit tight for a bit more than a two-hour break. But hey, take it with a pinch of salt, as those folks over at NetEase have hinted that "Server return times may vary based on progress" which could mean an earlier comeback... or not.Article continues belowLet's keep our hopes high, although given that the planned downtime already spills 10 minutes over the anticipated season start, I reckon the team isn't banking on any extra delays.We'll be monitoring the status of the Marvel Rivals server and will keep you updated when it's back up and running.For the latest breaking news and stories from across the globe from the Daily Star, sign up for our newsletters.RECOMMENDED0 Commentarios 0 Acciones 155 Views
WWW.DAILYSTAR.CO.UKIs Marvel Rivals down? Season 1 release information and server downtime scheduleMarvel Rivals servers are down today as NetEase preps to launch Season 1, which is set to introduce a ton of new features from new maps and heroes, to ranked changes and a new Doom Match game mode.News07:07, 10 Jan 2025Updated 07:10, 10 Jan 2025Marvel Rivals serves are down for the Season 1 update that's rolling out today and introduces the first two members of the Fantastic Four(Image: netease)With the initial Season 0 wrapped up, NetEase is rolling out Marvel Rivals Season 1 today, accompanied by update v20250110. This update primarily focuses on hero adjustments rather than team-up abilities for now.As NetEase prepares to launch Season 1, Marvel Rivals servers are offline today. The new season promises a plethora of new features including new maps and heroes, ranked changes, and a fresh Doom Match game mode.Alongside these additions, players can anticipate numerous balancing tweaks, with NetEase providing more specific details in the early Marvel Rivals patch notes. The much-anticipated arrival of the Fantastic Four is a highlight for many players, with Mister Fantastic and the Invisible Woman making their debut today, once the Marvel Rivals servers are back online.Marvel Rivals could be adding more characters very soonSeason 0 was brief, lasting only five weeks, but it appears that NetEase is planning to go bigger and adopt the mid-season update approach used by games like Warzone and Diablo 4. In line with this, Marvel Rivals Season 1 will be a double season, featuring a second update at the mid-point introducing the Human Torch and The Thing, thus completing Marvel's First Family in the game.Marvel Rivals fans, brace yourselves for a big shake-up as the servers spark back into action with some hefty changes one hotly requested tweak sees Jeff the Land Shark getting put on a leash with a major nerf. If you've been caught up in the whirlwind of this hero shooter's craze, today's update is set to crank up the excitement even more; and if you're just dipping your toes into Marvel Rivals waters, now couldn't be a better time with all the fresh content dropping in today, reports the Mirror.The Marvel Rivals servers are powering down today at the crack of dawn, at 7am GMT / 2am EST, which translates to yesterday night, 11pm PST, for the US west coast night owls. And heres a heads up you might get the boot a tad early, much like Fortnite players do when they're ousted 30 minutes pre-scheduled maintenance.According to the game's official Twitter page, we're looking at servers being back in business by 9.10am GMT / 4.10am EST / 1.10am PST so just sit tight for a bit more than a two-hour break. But hey, take it with a pinch of salt, as those folks over at NetEase have hinted that "Server return times may vary based on progress" which could mean an earlier comeback... or not.Article continues belowLet's keep our hopes high, although given that the planned downtime already spills 10 minutes over the anticipated season start, I reckon the team isn't banking on any extra delays.We'll be monitoring the status of the Marvel Rivals server and will keep you updated when it's back up and running.For the latest breaking news and stories from across the globe from the Daily Star, sign up for our newsletters.RECOMMENDED0 Commentarios 0 Acciones 155 Views -
 WWW.ARCHDAILY.COMHouse Among Trees and Houses / BAILORULLHouse Among Trees and Houses / BAILORULLSave this picture! Jos HeviaHousesArchitects: BAILORULLAreaArea of this architecture projectArea:230 mYearCompletion year of this architecture project Year: 2021 PhotographsPhotographs:Jos Hevia Lead Architects: Manuel Bailo Esteve, Rosa Rull Bertran More SpecsLess SpecsSave this picture!Text description provided by the architects. The project for this expansion and renovation of a 1930s summer house located next to the Sant Cugat golf club has been conceived with two key elements in mind that define the site.Save this picture!The urban rhythm of the street.Save this picture!Save this picture!Save this picture!The trees and the golf course. The house has a unique location characterized by having both an urban character, due to its continuity with the city, and a natural character, as it is adjacent to the Sant Cugat golf club. The presence of large, centuries-old trees from the golf club transforms this part of the established city into a continuous and built environment that is also green and natural.Save this picture!The project. Never demolish. The expansion is conceived from occupying the original free space, the threshold, that remains between the summer house and the golf club house. Occupying this empty space allows the preservation of the porous and narrow urban rhythm that defines this part of Vill street. A small, lightweight wooden house that follows the morphology of the neighboring houses is situated among the centuries-old trees on a permeable concrete structure.Save this picture!Save this picture!The renovation proposes the basic principle of sustainability: Never demolish. Maintaining the existing house and renovating it has allowed for the construction of a generous dialogue between two structures of similar forms, but not identical. On one hand, an old summer house without insulation with a load-bearing brick wall structure has been rehabilitated, while next to it, an expansion has been constructed that features a permeable structure formed by a single column. This column, which starts from the basement, supports the weight of the house located on the first floor with its branches. On the ground floor, the unique concrete column helps to organize the space and circulation, while freeing the facade of load and allowing for the construction of a completely transparent enclosure. The unique structure formed by a single column of the expansion allows the ground floor to easily integrate with the garden, while the first floor dialogues with and complements the urban rhythm of the neighboring houses.Save this picture!Project gallerySee allShow lessAbout this officePublished on January 10, 2025Cite: "House Among Trees and Houses / BAILORULL" [Casa entre rboles y casas / BAILORULL] 10 Jan 2025. ArchDaily. Accessed . <https://www.archdaily.com/1025333/house-among-trees-and-houses-bailorull&gt ISSN 0719-8884Save!ArchDaily?You've started following your first account!Did you know?You'll now receive updates based on what you follow! Personalize your stream and start following your favorite authors, offices and users.Go to my stream0 Commentarios 0 Acciones 135 Views
WWW.ARCHDAILY.COMHouse Among Trees and Houses / BAILORULLHouse Among Trees and Houses / BAILORULLSave this picture! Jos HeviaHousesArchitects: BAILORULLAreaArea of this architecture projectArea:230 mYearCompletion year of this architecture project Year: 2021 PhotographsPhotographs:Jos Hevia Lead Architects: Manuel Bailo Esteve, Rosa Rull Bertran More SpecsLess SpecsSave this picture!Text description provided by the architects. The project for this expansion and renovation of a 1930s summer house located next to the Sant Cugat golf club has been conceived with two key elements in mind that define the site.Save this picture!The urban rhythm of the street.Save this picture!Save this picture!Save this picture!The trees and the golf course. The house has a unique location characterized by having both an urban character, due to its continuity with the city, and a natural character, as it is adjacent to the Sant Cugat golf club. The presence of large, centuries-old trees from the golf club transforms this part of the established city into a continuous and built environment that is also green and natural.Save this picture!The project. Never demolish. The expansion is conceived from occupying the original free space, the threshold, that remains between the summer house and the golf club house. Occupying this empty space allows the preservation of the porous and narrow urban rhythm that defines this part of Vill street. A small, lightweight wooden house that follows the morphology of the neighboring houses is situated among the centuries-old trees on a permeable concrete structure.Save this picture!Save this picture!The renovation proposes the basic principle of sustainability: Never demolish. Maintaining the existing house and renovating it has allowed for the construction of a generous dialogue between two structures of similar forms, but not identical. On one hand, an old summer house without insulation with a load-bearing brick wall structure has been rehabilitated, while next to it, an expansion has been constructed that features a permeable structure formed by a single column. This column, which starts from the basement, supports the weight of the house located on the first floor with its branches. On the ground floor, the unique concrete column helps to organize the space and circulation, while freeing the facade of load and allowing for the construction of a completely transparent enclosure. The unique structure formed by a single column of the expansion allows the ground floor to easily integrate with the garden, while the first floor dialogues with and complements the urban rhythm of the neighboring houses.Save this picture!Project gallerySee allShow lessAbout this officePublished on January 10, 2025Cite: "House Among Trees and Houses / BAILORULL" [Casa entre rboles y casas / BAILORULL] 10 Jan 2025. ArchDaily. Accessed . <https://www.archdaily.com/1025333/house-among-trees-and-houses-bailorull&gt ISSN 0719-8884Save!ArchDaily?You've started following your first account!Did you know?You'll now receive updates based on what you follow! Personalize your stream and start following your favorite authors, offices and users.Go to my stream0 Commentarios 0 Acciones 135 Views -
 WWW.ARCHDAILY.COMThe Desert Relics / Karim+EliasThe Desert Relics / Karim+EliasSave this picture! Elias El HageArchitects: Karim+EliasAreaArea of this architecture projectArea:3850 mYearCompletion year of this architecture project Year: 2024 PhotographsPhotographs:Elias El Hage Lead Architects: Karim Tamerji, Elias El Hage More SpecsLess SpecsSave this picture!Text description provided by the architects. Our latest piece celebrates the craft of Mleiha's artifacts through a grand land art installation, made of and from desert sand.Save this picture!Renowned for its archaeological significance within the Arab region, Mleiha fosters a broad collection of the region's artefactual heritage. 'The Desert Relics' draw inspiration from a selection of Mleiha's ancient relics, visually expressing the "unearthing of an artifact" through a variety of vessel-like geometries.Save this picture!Twelve modular totems rise to monumental heights against the mountain backdrop in the symbolic form of stacked vessel vases, a grand bejeweled necklace, or a set of ancient stones.Save this picture!Each piece is unique in color and form, and like all ancient crafts, is fully handmade of and from the earth.Save this picture!The permanent installation was unveiled at the 2024 Tanweer Festival, and designed as a contribution to Sheikha Bodour Al Qasimi's inspiring vision to timelessly celebrate Mleiha's cultural heritage and rich desertscapes.Save this picture!Project gallerySee allShow lessProject locationAddress:Milehah, United Arab EmiratesLocation to be used only as a reference. It could indicate city/country but not exact address.About this officeKarim+EliasOfficePublished on January 10, 2025Cite: "The Desert Relics / Karim+Elias" 10 Jan 2025. ArchDaily. Accessed . <https://www.archdaily.com/1025437/the-desert-relics-karim-plus-elias&gt ISSN 0719-8884Save!ArchDaily?You've started following your first account!Did you know?You'll now receive updates based on what you follow! Personalize your stream and start following your favorite authors, offices and users.Go to my stream0 Commentarios 0 Acciones 144 Views
WWW.ARCHDAILY.COMThe Desert Relics / Karim+EliasThe Desert Relics / Karim+EliasSave this picture! Elias El HageArchitects: Karim+EliasAreaArea of this architecture projectArea:3850 mYearCompletion year of this architecture project Year: 2024 PhotographsPhotographs:Elias El Hage Lead Architects: Karim Tamerji, Elias El Hage More SpecsLess SpecsSave this picture!Text description provided by the architects. Our latest piece celebrates the craft of Mleiha's artifacts through a grand land art installation, made of and from desert sand.Save this picture!Renowned for its archaeological significance within the Arab region, Mleiha fosters a broad collection of the region's artefactual heritage. 'The Desert Relics' draw inspiration from a selection of Mleiha's ancient relics, visually expressing the "unearthing of an artifact" through a variety of vessel-like geometries.Save this picture!Twelve modular totems rise to monumental heights against the mountain backdrop in the symbolic form of stacked vessel vases, a grand bejeweled necklace, or a set of ancient stones.Save this picture!Each piece is unique in color and form, and like all ancient crafts, is fully handmade of and from the earth.Save this picture!The permanent installation was unveiled at the 2024 Tanweer Festival, and designed as a contribution to Sheikha Bodour Al Qasimi's inspiring vision to timelessly celebrate Mleiha's cultural heritage and rich desertscapes.Save this picture!Project gallerySee allShow lessProject locationAddress:Milehah, United Arab EmiratesLocation to be used only as a reference. It could indicate city/country but not exact address.About this officeKarim+EliasOfficePublished on January 10, 2025Cite: "The Desert Relics / Karim+Elias" 10 Jan 2025. ArchDaily. Accessed . <https://www.archdaily.com/1025437/the-desert-relics-karim-plus-elias&gt ISSN 0719-8884Save!ArchDaily?You've started following your first account!Did you know?You'll now receive updates based on what you follow! Personalize your stream and start following your favorite authors, offices and users.Go to my stream0 Commentarios 0 Acciones 144 Views -
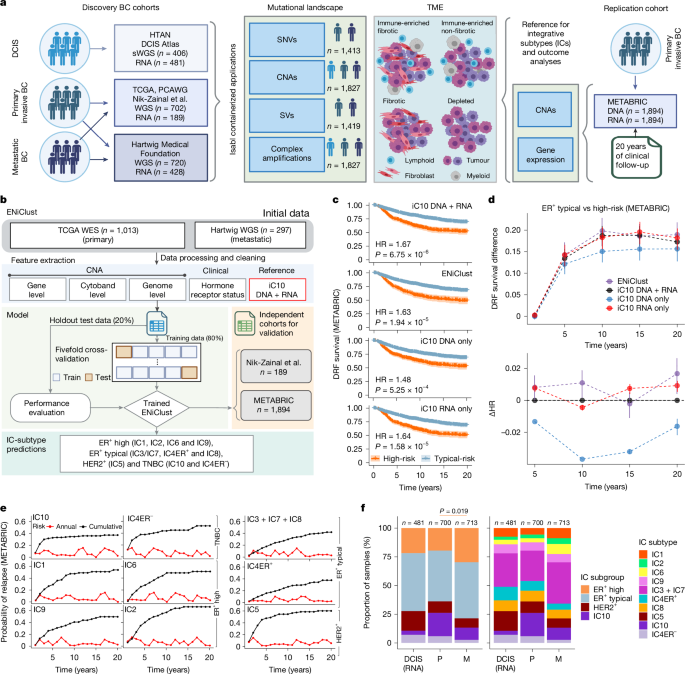 WWW.NATURE.COMComplex rearrangements fuel ER<sup>+</sup> and HER2<sup>+</sup> breast tumoursNature, Published online: 08 January 2025; doi:10.1038/s41586-024-08377-xA study identifies three dominant genomic archetypes of breast cancer induced by discrete mutational processes, describing a continuum of genomic profiles and detailing the mechanisms underlying the progression of breast cancer.0 Commentarios 0 Acciones 142 Views
WWW.NATURE.COMComplex rearrangements fuel ER<sup>+</sup> and HER2<sup>+</sup> breast tumoursNature, Published online: 08 January 2025; doi:10.1038/s41586-024-08377-xA study identifies three dominant genomic archetypes of breast cancer induced by discrete mutational processes, describing a continuum of genomic profiles and detailing the mechanisms underlying the progression of breast cancer.0 Commentarios 0 Acciones 142 Views -
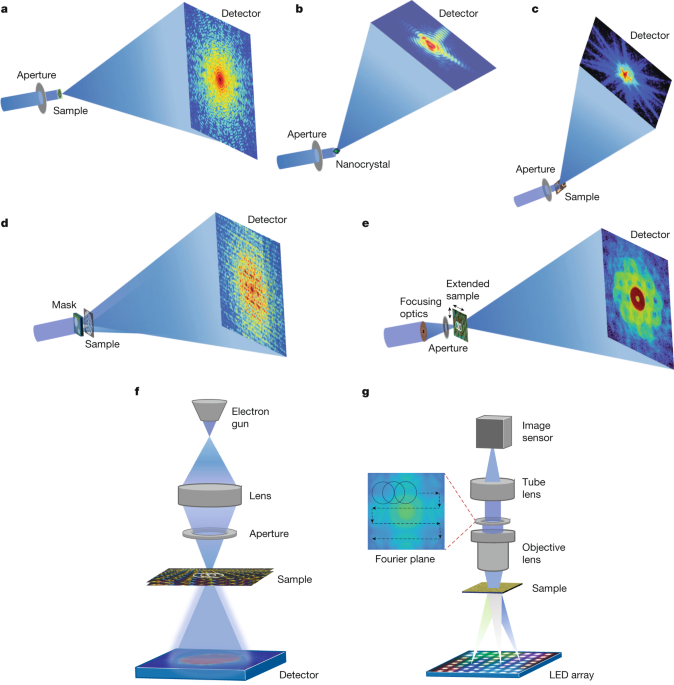 WWW.NATURE.COMComputational microscopy with coherent diffractive imaging and ptychographyNature, Published online: 08 January 2025; doi:10.1038/s41586-024-08278-zThis review highlights transformative advancements in computational microscopy, encompassing coherent diffractive imaging and ptychography, which unify microscopy and crystallography to achieve unparalleled resolution, precision, and large fields of view, enabling diverse applications and driving breakthroughs across multidisciplinary sciences.0 Commentarios 0 Acciones 146 Views
WWW.NATURE.COMComputational microscopy with coherent diffractive imaging and ptychographyNature, Published online: 08 January 2025; doi:10.1038/s41586-024-08278-zThis review highlights transformative advancements in computational microscopy, encompassing coherent diffractive imaging and ptychography, which unify microscopy and crystallography to achieve unparalleled resolution, precision, and large fields of view, enabling diverse applications and driving breakthroughs across multidisciplinary sciences.0 Commentarios 0 Acciones 146 Views -
 WWW.GAMESPOT.COMTwin Peaks: From Z To A Collection Reprint Preorder Is 20% Off At AmazonTwin Peaks: From Z to A Blu-ray (Repackage) $55 (was $70) | Releases February 3 Preorder at Amazon Twin Peaks: A Limited Event Series Collector's Edition Blu-ray $38 (was $40) | Releases February 11 Preorder at Amazon Twin Peaks fans can save on the upcoming reprint of the superb show's comprehensive Blu-ray collection at Amazon. Twin Peaks: From Z to A is discounted to $55.29, down from $70, ahead of its February 3 release. This Twin Peaks box set originally released in 2019 and has been sold out for quite some time, but the new repackaged release offers a budget-friendly way to add the complete series to your collection. Twin Peaks: From Z to A Blu-ray (Repackage) $55 (was $70) | Releases February 3 Twin Peaks: From Z to A compiles the entire Twin Peaks series, including Seasons 1 and 2 of the original series, the Fire Walk With Me prequel movie, and Twin Peaks: A Limited Event Series (Season 3) that aired in 2017. You'll also get a long list of special features, including 4K versions of the original series Pilot episode and Twin Peaks: A Limited Event Series Episode 8.Here's a look at the special features included in Twin Peaks: From Z to A:The Missing Pieces: Fire Walk With Me deleted scenesBehind The Curtain: Making of Footage From Twin Peaks: A Limited Event SeriesFull-length versions of all Roadhouse Bar music performancesA Talk with Kyle MacLachlan and Sheryl LeeOn the Couch with Kimmy and Harry4K versions of the Original Series Pilot and Twin Peaks: A Limited Event Series Episode 8Additional special features from previously released Twin Peaks home video releasesIn total, that's over 20 hours of additional Twin Peaks content. It's worth noting that the packaging for this Twin Peaks: From Z to A reprinting differs from the original 2019 version. The new run uses a plastic case rather than the premium fold-out box of the original, and it lacks the collectible art prints. This cost-saving measure probably makes producing the sets easier, which hopefully means this reprint run will have better availability, but it's less of a collector's item. Nevertheless, this should be your best option if you want an all-in-one Twin Peak set. Preorder at Amazon Twin Peaks: A Limited Event Series Collector's Edition Blu-ray $38 (was $40) | Releases February 11 Twin Peaks Season 3 is also getting a standalone Blu-ray re-release on February 11. It's launching for $40--which is a bit steep considering the 18-episode season is also included in the $70 Twin Peaks: Z to A box set, not to mention other Twin Peaks collections that are currently available. Still, this new Collector's Edition is worth considering if you only need to add the final set of episodes to your collection. Along with the full season, you also get a selection of special features (most of which, again, are also included in the Z to A box set).Twin Peaks: A Limited Event Series Collector's Edition special features:FeaturettesBehind-the-Scenes Photo GalleryComic-Con Twin Peaks Panel Preorder at Amazon In case the Twin Peaks: From Z to A box set set sells out, or you're looking to get your hands on a Blu-ray version of the full show sooner than February, you can also grab the Twin Peaks: The Television Collection, which includes the two original seasons and Twin Peaks: A Limited Event Series in one Blu-ray box set for $55.72 (was $77). A DVD edition is also available for $36.73 (was $51). While you'll be missing out on the exclusive special features and Fire Walk With Me film included in The Z to A collection, the Twin Peaks: The Television Collection is still a solid choice.Continue Reading at GameSpot0 Commentarios 0 Acciones 106 Views
WWW.GAMESPOT.COMTwin Peaks: From Z To A Collection Reprint Preorder Is 20% Off At AmazonTwin Peaks: From Z to A Blu-ray (Repackage) $55 (was $70) | Releases February 3 Preorder at Amazon Twin Peaks: A Limited Event Series Collector's Edition Blu-ray $38 (was $40) | Releases February 11 Preorder at Amazon Twin Peaks fans can save on the upcoming reprint of the superb show's comprehensive Blu-ray collection at Amazon. Twin Peaks: From Z to A is discounted to $55.29, down from $70, ahead of its February 3 release. This Twin Peaks box set originally released in 2019 and has been sold out for quite some time, but the new repackaged release offers a budget-friendly way to add the complete series to your collection. Twin Peaks: From Z to A Blu-ray (Repackage) $55 (was $70) | Releases February 3 Twin Peaks: From Z to A compiles the entire Twin Peaks series, including Seasons 1 and 2 of the original series, the Fire Walk With Me prequel movie, and Twin Peaks: A Limited Event Series (Season 3) that aired in 2017. You'll also get a long list of special features, including 4K versions of the original series Pilot episode and Twin Peaks: A Limited Event Series Episode 8.Here's a look at the special features included in Twin Peaks: From Z to A:The Missing Pieces: Fire Walk With Me deleted scenesBehind The Curtain: Making of Footage From Twin Peaks: A Limited Event SeriesFull-length versions of all Roadhouse Bar music performancesA Talk with Kyle MacLachlan and Sheryl LeeOn the Couch with Kimmy and Harry4K versions of the Original Series Pilot and Twin Peaks: A Limited Event Series Episode 8Additional special features from previously released Twin Peaks home video releasesIn total, that's over 20 hours of additional Twin Peaks content. It's worth noting that the packaging for this Twin Peaks: From Z to A reprinting differs from the original 2019 version. The new run uses a plastic case rather than the premium fold-out box of the original, and it lacks the collectible art prints. This cost-saving measure probably makes producing the sets easier, which hopefully means this reprint run will have better availability, but it's less of a collector's item. Nevertheless, this should be your best option if you want an all-in-one Twin Peak set. Preorder at Amazon Twin Peaks: A Limited Event Series Collector's Edition Blu-ray $38 (was $40) | Releases February 11 Twin Peaks Season 3 is also getting a standalone Blu-ray re-release on February 11. It's launching for $40--which is a bit steep considering the 18-episode season is also included in the $70 Twin Peaks: Z to A box set, not to mention other Twin Peaks collections that are currently available. Still, this new Collector's Edition is worth considering if you only need to add the final set of episodes to your collection. Along with the full season, you also get a selection of special features (most of which, again, are also included in the Z to A box set).Twin Peaks: A Limited Event Series Collector's Edition special features:FeaturettesBehind-the-Scenes Photo GalleryComic-Con Twin Peaks Panel Preorder at Amazon In case the Twin Peaks: From Z to A box set set sells out, or you're looking to get your hands on a Blu-ray version of the full show sooner than February, you can also grab the Twin Peaks: The Television Collection, which includes the two original seasons and Twin Peaks: A Limited Event Series in one Blu-ray box set for $55.72 (was $77). A DVD edition is also available for $36.73 (was $51). While you'll be missing out on the exclusive special features and Fire Walk With Me film included in The Z to A collection, the Twin Peaks: The Television Collection is still a solid choice.Continue Reading at GameSpot0 Commentarios 0 Acciones 106 Views



