0 Yorumlar
0 hisse senetleri
39 Views

Rehber
Rehber
-
Please log in to like, share and comment!
-
 FUTURISM.COMCalifornia Nuclear Power Plant Deploys Generative AI Safety SystemAmerica's first nuclear power plant to use artificial intelligence is, ironically, the last operational one in California.As CalMatters reports, the Diablo Canyon power plant is slated to be decommissioned by the end of this decade. In the interim, the plant's owner, Pacific Gas & Electric (PG&E), claims that it's deploying its "Neutron Enterprise" tool — which will be the first nuclear plant in the nation to use AI — in a series of escalating stages.Less than 18 months ago, Diablo Canyon was hurtling headlong toward a decommissioning that would have begun in 2024 and ended this year. In late 2023, however, the California Public Utility Commission voted to stay its execution for five years, kicking the can on the inevitable to 2029 and 2030, respectively.Just under a year after that vote, PG&E announced that it was teaming up with a startup called Atomic Canyon, which was founded with the plant in mind and is also based in the coastal Central California town of San Luis Obispo. That partnership, and the first "stage" of the tool's deployment, brought some of Nvidia's high-powered H100 AI chips to the dying nuclear plant, and with them the compute power needed for generative artificial intelligence.Running on an internal server without cloud access, Neutron Enterprise's biggest use case, much like so-called AI "search engines," is summarizing a massive trove of millions of regulatory documents that have been fed into it. According to Atomic Canyon CEO and cofounder Trey Lauderdale, this isn't risky — though anyone who has used AI to summarize information knows better, because the tech still often makes factual mistakes.Speaking to CalMatters, PG&E executive Maureen Zalawick insisted that the AI program will be more of a "copilot" than a "decision-maker," meant to assist flesh-and-blood employees rather than replace them."We probably spend about 15,000 hours a year searching through our multiple databases and records and procedures," Zalawick explained. "And that’s going to shrink that time way down."Lauderdale put it in even simpler terms."You can put this on the record," he told CalMatters. "The AI guy in nuclear says there is no way in hell I want AI running my nuclear power plant right now."If that "right now" caveat gives you pause, you're not alone. Given the shifting timelines for the closure of Diablo Canyon in a state that has been painstakingly phasing out its nuclear facilities since the 1970s over concerns about toxic waste — and the fact that Lauderdale claims to be talking to other plants in other states — there's ample cause for concern."The idea that you could just use generative AI for one specific kind of task at the nuclear power plant and then call it a day," cautioned Tamara Kneese of the tech watchdog Data & Society, "I don’t really trust that it would stop there."As head of Data & Society's Climate, Technology, and Justice program, Kneese said that while using AI to help sift through tomes of documents is worthwhile, "trusting PG&E to safely use generative AI in a nuclear setting is something that is deserving of more scrutiny." This is the same company whose polluting propensities were exposed by the real-life Erin Brokovich in the 1990s, after all.California lawmakers, meanwhile, were impressed by the tailored usage Atomic Canyon and PG&E propose for the program — but it remains to be seen whether or not that narrow functionality will remain that way.Share This Article0 Yorumlar 0 hisse senetleri 61 Views
FUTURISM.COMCalifornia Nuclear Power Plant Deploys Generative AI Safety SystemAmerica's first nuclear power plant to use artificial intelligence is, ironically, the last operational one in California.As CalMatters reports, the Diablo Canyon power plant is slated to be decommissioned by the end of this decade. In the interim, the plant's owner, Pacific Gas & Electric (PG&E), claims that it's deploying its "Neutron Enterprise" tool — which will be the first nuclear plant in the nation to use AI — in a series of escalating stages.Less than 18 months ago, Diablo Canyon was hurtling headlong toward a decommissioning that would have begun in 2024 and ended this year. In late 2023, however, the California Public Utility Commission voted to stay its execution for five years, kicking the can on the inevitable to 2029 and 2030, respectively.Just under a year after that vote, PG&E announced that it was teaming up with a startup called Atomic Canyon, which was founded with the plant in mind and is also based in the coastal Central California town of San Luis Obispo. That partnership, and the first "stage" of the tool's deployment, brought some of Nvidia's high-powered H100 AI chips to the dying nuclear plant, and with them the compute power needed for generative artificial intelligence.Running on an internal server without cloud access, Neutron Enterprise's biggest use case, much like so-called AI "search engines," is summarizing a massive trove of millions of regulatory documents that have been fed into it. According to Atomic Canyon CEO and cofounder Trey Lauderdale, this isn't risky — though anyone who has used AI to summarize information knows better, because the tech still often makes factual mistakes.Speaking to CalMatters, PG&E executive Maureen Zalawick insisted that the AI program will be more of a "copilot" than a "decision-maker," meant to assist flesh-and-blood employees rather than replace them."We probably spend about 15,000 hours a year searching through our multiple databases and records and procedures," Zalawick explained. "And that’s going to shrink that time way down."Lauderdale put it in even simpler terms."You can put this on the record," he told CalMatters. "The AI guy in nuclear says there is no way in hell I want AI running my nuclear power plant right now."If that "right now" caveat gives you pause, you're not alone. Given the shifting timelines for the closure of Diablo Canyon in a state that has been painstakingly phasing out its nuclear facilities since the 1970s over concerns about toxic waste — and the fact that Lauderdale claims to be talking to other plants in other states — there's ample cause for concern."The idea that you could just use generative AI for one specific kind of task at the nuclear power plant and then call it a day," cautioned Tamara Kneese of the tech watchdog Data & Society, "I don’t really trust that it would stop there."As head of Data & Society's Climate, Technology, and Justice program, Kneese said that while using AI to help sift through tomes of documents is worthwhile, "trusting PG&E to safely use generative AI in a nuclear setting is something that is deserving of more scrutiny." This is the same company whose polluting propensities were exposed by the real-life Erin Brokovich in the 1990s, after all.California lawmakers, meanwhile, were impressed by the tailored usage Atomic Canyon and PG&E propose for the program — but it remains to be seen whether or not that narrow functionality will remain that way.Share This Article0 Yorumlar 0 hisse senetleri 61 Views -
 THEHACKERNEWS.COMChinese Hackers Target Linux Systems Using SNOWLIGHT Malware and VShell ToolApr 15, 2025Ravie LakshmananLinux / Malware The China-linked threat actor known as UNC5174 has been attributed to a new campaign that leverages a variant of a known malware dubbed SNOWLIGHT and a new open-source tool called VShell to infect Linux systems. "Threat actors are increasingly using open source tools in their arsenals for cost-effectiveness and obfuscation to save money and, in this case, plausibly blend in with the pool of non-state-sponsored and often less technical adversaries (e.g., script kiddies), thereby making attribution even more difficult," Sysdig researcher Alessandra Rizzo said in a report shared with The Hacker News. "This seems to hold especially true for this particular threat actor, who has been under the radar for the last year since being affiliated with the Chinese government." UNC5174, also referred to as Uteus (or Uetus), was previously documented by Google-owned Mandiant as exploiting security flaws in Connectwise ScreenConnect and F5 BIG-IP software to deliver a C-based ELF downloader named SNOWLIGHT, which is designed to fetch a Golang tunneler dubbed GOHEAVY from infrastructure tied to a publicly available command-and-control (C2) framework known as SUPERSHELL. Also deployed in the attacks was GOREVERSE, a publicly available reverse shell backdoor written in Golang that operates over Secure Shell (SSH). The French National Agency for the Security of Information Systems (ANSSI), in its Cyber Threat Overview report for 2024 published last month, said it observed an attacker employing similar tradecraft as that of UNC5174 to weaponize security flaws in Ivanti Cloud Service Appliance (CSA) such as CVE-2024-8963, CVE-2024-9380, and CVE-2024-8190 to gain control and execute arbitrary code. "Moderately sophisticated and discreet, this intrusion set is characterized by the use of intrusion tools largely available as open source and by the – already publicly reported – use of a rootkit code," the ANSSI said. It's worth noting that both SNOWLIGHT and VShell are capable of targeting Apple macOS systems, with the latter distributed as a fake Cloudflare authenticator application as part of an as-yet-undetermined attack chain, according to an analysis of artifacts uploaded to VirusTotal from China in October 2024. In the attack chain observed by Sysdig in late January 2025, the SNOWLIGHT malware acts as a dropper for a fileless, in-memory payload called VShell, a remote access trojan (RAT) widely used by Chinese-speaking cybercriminals. The initial access vector used for the attack is presently unknown. Specifically, the initial access is used to execute a malicious bash script ("download_backd.sh") that deploys two binaries associated with SNOWLIGHT (dnsloger) and Sliver (system_worker), both of which are used to set up persistence and establish communications with a C2 server. The final stage of the attack delivers VShell via SNOWLIGHT by means of a specially crafted request to the C2 server, thereby enabling remote control and further post-compromise exploitation. "[VShell] acts as a RAT (Remote Access Trojan), allowing its abusers to execute arbitrary commands and download or upload files," Rizzo said. "SNOWLIGHT and VShell pose a significant risk to organizations due to their stealthy and sophisticated techniques," Sysdig said. "This is evidenced by the employment of WebSockets for command-and-control, as well as the fileless VShell payload." The disclosure comes as TeamT5 revealed that a China-nexus hacking group likely exploited security flaws in Ivanti appliances (CVE-2025-0282 and CVE-2025-22457) to gain initial access and deploy the SPAWNCHIMERA malware. The attacks, the Taiwanese cybersecurity company said, targeted a multitude of sectors spanning nearly 20 different countries such as Austria, Australia, France, Spain, Japan, South Korea, Netherlands, Singapore, Taiwan, the United Arab Emirates, the United Kingdom, and the United States. The findings also dovetail with accusations from China that the U.S. National Security Agency (NSA) launched "advanced" cyber attacks during the Asian Winter Games in February, pointing fingers at three NSA agents for repeated attacks on China's critical information infrastructure as well as against Huawei. "At the ninth Asian Winter Games, the U.S. government conducted cyberattacks on the information systems of the Games and the critical information infrastructure in Heilongjiang," Foreign Ministry Spokesperson Lin Jian said. "This move is egregious for it severely endangers the security of China's critical information infrastructure, national defense, finance, society, and production as well as its citizens' personal information." Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post. SHARE 0 Yorumlar 0 hisse senetleri 55 Views
THEHACKERNEWS.COMChinese Hackers Target Linux Systems Using SNOWLIGHT Malware and VShell ToolApr 15, 2025Ravie LakshmananLinux / Malware The China-linked threat actor known as UNC5174 has been attributed to a new campaign that leverages a variant of a known malware dubbed SNOWLIGHT and a new open-source tool called VShell to infect Linux systems. "Threat actors are increasingly using open source tools in their arsenals for cost-effectiveness and obfuscation to save money and, in this case, plausibly blend in with the pool of non-state-sponsored and often less technical adversaries (e.g., script kiddies), thereby making attribution even more difficult," Sysdig researcher Alessandra Rizzo said in a report shared with The Hacker News. "This seems to hold especially true for this particular threat actor, who has been under the radar for the last year since being affiliated with the Chinese government." UNC5174, also referred to as Uteus (or Uetus), was previously documented by Google-owned Mandiant as exploiting security flaws in Connectwise ScreenConnect and F5 BIG-IP software to deliver a C-based ELF downloader named SNOWLIGHT, which is designed to fetch a Golang tunneler dubbed GOHEAVY from infrastructure tied to a publicly available command-and-control (C2) framework known as SUPERSHELL. Also deployed in the attacks was GOREVERSE, a publicly available reverse shell backdoor written in Golang that operates over Secure Shell (SSH). The French National Agency for the Security of Information Systems (ANSSI), in its Cyber Threat Overview report for 2024 published last month, said it observed an attacker employing similar tradecraft as that of UNC5174 to weaponize security flaws in Ivanti Cloud Service Appliance (CSA) such as CVE-2024-8963, CVE-2024-9380, and CVE-2024-8190 to gain control and execute arbitrary code. "Moderately sophisticated and discreet, this intrusion set is characterized by the use of intrusion tools largely available as open source and by the – already publicly reported – use of a rootkit code," the ANSSI said. It's worth noting that both SNOWLIGHT and VShell are capable of targeting Apple macOS systems, with the latter distributed as a fake Cloudflare authenticator application as part of an as-yet-undetermined attack chain, according to an analysis of artifacts uploaded to VirusTotal from China in October 2024. In the attack chain observed by Sysdig in late January 2025, the SNOWLIGHT malware acts as a dropper for a fileless, in-memory payload called VShell, a remote access trojan (RAT) widely used by Chinese-speaking cybercriminals. The initial access vector used for the attack is presently unknown. Specifically, the initial access is used to execute a malicious bash script ("download_backd.sh") that deploys two binaries associated with SNOWLIGHT (dnsloger) and Sliver (system_worker), both of which are used to set up persistence and establish communications with a C2 server. The final stage of the attack delivers VShell via SNOWLIGHT by means of a specially crafted request to the C2 server, thereby enabling remote control and further post-compromise exploitation. "[VShell] acts as a RAT (Remote Access Trojan), allowing its abusers to execute arbitrary commands and download or upload files," Rizzo said. "SNOWLIGHT and VShell pose a significant risk to organizations due to their stealthy and sophisticated techniques," Sysdig said. "This is evidenced by the employment of WebSockets for command-and-control, as well as the fileless VShell payload." The disclosure comes as TeamT5 revealed that a China-nexus hacking group likely exploited security flaws in Ivanti appliances (CVE-2025-0282 and CVE-2025-22457) to gain initial access and deploy the SPAWNCHIMERA malware. The attacks, the Taiwanese cybersecurity company said, targeted a multitude of sectors spanning nearly 20 different countries such as Austria, Australia, France, Spain, Japan, South Korea, Netherlands, Singapore, Taiwan, the United Arab Emirates, the United Kingdom, and the United States. The findings also dovetail with accusations from China that the U.S. National Security Agency (NSA) launched "advanced" cyber attacks during the Asian Winter Games in February, pointing fingers at three NSA agents for repeated attacks on China's critical information infrastructure as well as against Huawei. "At the ninth Asian Winter Games, the U.S. government conducted cyberattacks on the information systems of the Games and the critical information infrastructure in Heilongjiang," Foreign Ministry Spokesperson Lin Jian said. "This move is egregious for it severely endangers the security of China's critical information infrastructure, national defense, finance, society, and production as well as its citizens' personal information." Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post. SHARE 0 Yorumlar 0 hisse senetleri 55 Views -
 WWW.INFORMATIONWEEK.COMLate to AI? Here's How CIOs Can Catch Up QuicklyJohn Edwards, Technology Journalist & AuthorApril 15, 20255 Min Readeverything possible via Alamy Stock PhotoFew IT leaders dispute the fact that AI is this decade's breakthrough technology. Yet this wasn't always the case. In fact, until relatively recently, many AI cynics failed to recognize the technology's potential and, therefore, fell behind more astute competitors. As they begin to make up for lost time, business and technology leaders should focus on key readiness areas: data infrastructure, governance, regulatory compliance, risk management, and workforce training, says Jim Rowan, head of AI at Deloitte Consulting. "These foundational steps are essential for success in an AI-driven future," he notes in an email interview. Rowan cites Deloitte's most recent State of Generative AI in the Enterprise report, in which 78% of respondents stated they expect to increase their overall AI spending in the next fiscal year. However, the majority of organizations anticipate it will take at least a year to overcome adoption challenges. "These findings underscore the importance of a deliberate yet agile approach to AI readiness that addresses both regulation and talent challenges to AI adoption." Getting Ready The key to getting up to speed in AI lies in hiring the best advisor you can find, someone who has expertise in your company's area, advises Melissa Ruzzi, AI director at SaaS security firm AppOmni. "Some companies think the best way is to hire grad students fresh out of college," she notes via email. Yet nothing beats domain expertise and implementation experience. "This is the fastest way to catch up." Related:Many organizations underestimate the amount of cultural change needed to help team members adopt and effectively use AI technologies, Rowan says. Workforce training and education early in the AI journey is essential. To foster familiarity and innovation, team members need access to AI tools as well as hands-on experience. "Talent and training gaps can't be overlooked if organizations aim to achieve sustained growth and maximize ROI," he says. Every company has multiple projects that can benefit from AI, Ruzzi says. "It's best to have an in-house AI expert who understands the technology and its applications," she advises. "If not, hire consultants and contractors with domain experience to help decide where to get started." Many new AI adopters begin by focusing on internal projects tied to customer delivery timelines, Ruzzi says. Others decide to start with a small customer-facing project so they can prove AI's added value. The decision depends very much on the ROI goal, she notes. "Small projects of short duration can be a good starting point, so the success can be more quickly measured." Related:Security Matters AI security must always be addressed and ensured, regardless of the project's size or scope, Ruzzi advises. View developing an initial AI project as being similar to installing a new SaaS application, she suggests. "It's crucial to make sure that configurations, such as accessibility and access to data aren't posing a risk of public data exposure or, worse yet, are vulnerable to data injection that could poison your models." To minimize the security risk created by novice AI teams, start with simple implementations and proofs of concepts, such as internal chatbots, recommends David Brauchler, technical director and head of AI and ML security at cybersecurity consulting firm NCC Group. "Starting slow enables application architects and developers to consider the intricacies AI introduces to application threat models," he explains in an email interview. AI also creates new data risk concerns, including the technology's inability to reliably distinguish between trusted and untrusted content. "Application designers need to consider risks that they might not be used to addressing in traditional software stacks," Brauchler says. Related:Organizations should already be training their employees on the risks associated with AI as part of their standard security training, Brauchler advises. "Training programs help address common pitfalls organizations encounter that lead to shadow AI and data leakage," he says. Organizations that aren't already providing guidance on security issues should incorporate these risks into their training programs as quickly as they can. "For employees who contribute to the software development lifecycle, technical training should begin before developing AI applications." Final Thoughts As organizations gain experience with GenAI, they will begin to understand both the rewards and challenges of deploying the technology at scale, Rowan says. "The need for disciplined action has grown," he observes. As technical preparedness has improved, regulatory uncertainty and risk management have emerged as significant barriers to AI progress, particularly for newcomers, Rowan says. "Talent and workforce issues remain important, yet access to specialized technical talent no longer seems to be a dire emergency." Although tempting, Brauchler warns against rushing into AI. "AI will still be here in a few years [and] taking a thoughtful, measured approach to AI business strategy and security is the best way to avoid unnecessary risks," he concludes.About the AuthorJohn EdwardsTechnology Journalist & AuthorJohn Edwards is a veteran business technology journalist. His work has appeared in The New York Times, The Washington Post, and numerous business and technology publications, including Computerworld, CFO Magazine, IBM Data Management Magazine, RFID Journal, and Electronic Design. He has also written columns for The Economist's Business Intelligence Unit and PricewaterhouseCoopers' Communications Direct. John has authored several books on business technology topics. His work began appearing online as early as 1983. Throughout the 1980s and 90s, he wrote daily news and feature articles for both the CompuServe and Prodigy online services. His "Behind the Screens" commentaries made him the world's first known professional blogger.See more from John EdwardsWebinarsMore WebinarsReportsMore ReportsNever Miss a Beat: Get a snapshot of the issues affecting the IT industry straight to your inbox.SIGN-UPYou May Also Like0 Yorumlar 0 hisse senetleri 65 Views
WWW.INFORMATIONWEEK.COMLate to AI? Here's How CIOs Can Catch Up QuicklyJohn Edwards, Technology Journalist & AuthorApril 15, 20255 Min Readeverything possible via Alamy Stock PhotoFew IT leaders dispute the fact that AI is this decade's breakthrough technology. Yet this wasn't always the case. In fact, until relatively recently, many AI cynics failed to recognize the technology's potential and, therefore, fell behind more astute competitors. As they begin to make up for lost time, business and technology leaders should focus on key readiness areas: data infrastructure, governance, regulatory compliance, risk management, and workforce training, says Jim Rowan, head of AI at Deloitte Consulting. "These foundational steps are essential for success in an AI-driven future," he notes in an email interview. Rowan cites Deloitte's most recent State of Generative AI in the Enterprise report, in which 78% of respondents stated they expect to increase their overall AI spending in the next fiscal year. However, the majority of organizations anticipate it will take at least a year to overcome adoption challenges. "These findings underscore the importance of a deliberate yet agile approach to AI readiness that addresses both regulation and talent challenges to AI adoption." Getting Ready The key to getting up to speed in AI lies in hiring the best advisor you can find, someone who has expertise in your company's area, advises Melissa Ruzzi, AI director at SaaS security firm AppOmni. "Some companies think the best way is to hire grad students fresh out of college," she notes via email. Yet nothing beats domain expertise and implementation experience. "This is the fastest way to catch up." Related:Many organizations underestimate the amount of cultural change needed to help team members adopt and effectively use AI technologies, Rowan says. Workforce training and education early in the AI journey is essential. To foster familiarity and innovation, team members need access to AI tools as well as hands-on experience. "Talent and training gaps can't be overlooked if organizations aim to achieve sustained growth and maximize ROI," he says. Every company has multiple projects that can benefit from AI, Ruzzi says. "It's best to have an in-house AI expert who understands the technology and its applications," she advises. "If not, hire consultants and contractors with domain experience to help decide where to get started." Many new AI adopters begin by focusing on internal projects tied to customer delivery timelines, Ruzzi says. Others decide to start with a small customer-facing project so they can prove AI's added value. The decision depends very much on the ROI goal, she notes. "Small projects of short duration can be a good starting point, so the success can be more quickly measured." Related:Security Matters AI security must always be addressed and ensured, regardless of the project's size or scope, Ruzzi advises. View developing an initial AI project as being similar to installing a new SaaS application, she suggests. "It's crucial to make sure that configurations, such as accessibility and access to data aren't posing a risk of public data exposure or, worse yet, are vulnerable to data injection that could poison your models." To minimize the security risk created by novice AI teams, start with simple implementations and proofs of concepts, such as internal chatbots, recommends David Brauchler, technical director and head of AI and ML security at cybersecurity consulting firm NCC Group. "Starting slow enables application architects and developers to consider the intricacies AI introduces to application threat models," he explains in an email interview. AI also creates new data risk concerns, including the technology's inability to reliably distinguish between trusted and untrusted content. "Application designers need to consider risks that they might not be used to addressing in traditional software stacks," Brauchler says. Related:Organizations should already be training their employees on the risks associated with AI as part of their standard security training, Brauchler advises. "Training programs help address common pitfalls organizations encounter that lead to shadow AI and data leakage," he says. Organizations that aren't already providing guidance on security issues should incorporate these risks into their training programs as quickly as they can. "For employees who contribute to the software development lifecycle, technical training should begin before developing AI applications." Final Thoughts As organizations gain experience with GenAI, they will begin to understand both the rewards and challenges of deploying the technology at scale, Rowan says. "The need for disciplined action has grown," he observes. As technical preparedness has improved, regulatory uncertainty and risk management have emerged as significant barriers to AI progress, particularly for newcomers, Rowan says. "Talent and workforce issues remain important, yet access to specialized technical talent no longer seems to be a dire emergency." Although tempting, Brauchler warns against rushing into AI. "AI will still be here in a few years [and] taking a thoughtful, measured approach to AI business strategy and security is the best way to avoid unnecessary risks," he concludes.About the AuthorJohn EdwardsTechnology Journalist & AuthorJohn Edwards is a veteran business technology journalist. His work has appeared in The New York Times, The Washington Post, and numerous business and technology publications, including Computerworld, CFO Magazine, IBM Data Management Magazine, RFID Journal, and Electronic Design. He has also written columns for The Economist's Business Intelligence Unit and PricewaterhouseCoopers' Communications Direct. John has authored several books on business technology topics. His work began appearing online as early as 1983. Throughout the 1980s and 90s, he wrote daily news and feature articles for both the CompuServe and Prodigy online services. His "Behind the Screens" commentaries made him the world's first known professional blogger.See more from John EdwardsWebinarsMore WebinarsReportsMore ReportsNever Miss a Beat: Get a snapshot of the issues affecting the IT industry straight to your inbox.SIGN-UPYou May Also Like0 Yorumlar 0 hisse senetleri 65 Views -
 SCREENCRUSH.COM‘Aladdin’ Is Latest Disney Classic to Get Horror Movie TreatmentAladdin is getting the horror treatment with a “dark, supernatural reimagining.”The classic story, which was famously made into an animated musical by Disney in 1992, which in turn got a live action adaptation in 2019, is the latest family film to be given a terrifying twist.As reported by Deadline, the synopsis for Aladdin: The Monkey’s Paw reads: “A modern-day Londoner, Aladdin, inherits an ancient monkey’s paw believed to grant wishes, only to discover that every desire comes at a soul-crushing price.”“As those around him fall victim to its curse, he must confront a growing evil — and the demonic force that feeds on every wish made.”The movie, which comes from Empire Studios, Every Entertainment and 8th Law Pictures, is set to start filming next month in the U.K.DisneyDisneyloading...READ MORE: Disney Live-Action Remakes Ranked From Worst to BestThe cast will include Queen of the South star Nick Sagar, former EastEnders actor Ricky Norwood, and Tell Me Everything’s Montana Manning.Terrifier 3 star Bradley Stryker is also part of the cast, and will direct the film from a screenplay by Charley McDougall.McDougall said in a statement: “We always wanted to explore horror through a personal lens — not just the scares, but the human cost of wishes. “This story’s been haunting us for a while, and it’s time to let it loose. The best horror films haunt you long after the credits roll. That’s what this story does.”“It’s sharp, emotional, and full of dread in all the right ways. We’re not just making another horror film — we’re building a world around a truly iconic concept. The paw, the mythology, the characters — it’s all there.”Meanwhile, Stryker insisted the film will carry “diabolical and entertaining” stakes as film fans are taken on a journey.It's not the first time a character associated with Disney has been given the horror treatment, after the likes of Winnie-the-Pooh: Blood and Honey and Mickey's Mouse Trap.The latter was announced at the beginning of 2024 after “Steamboat Willie,” the earliest iteration of Disney's iconic mouse mascot, entered public domain.The slasher, which was released on demand in the U.S., focused on a killer wearing a mouse mask targeting college kids at a local arcade.Get our free mobile app25 Actors Who Turned Down Huge Movie RolesSome of the most famous actors in history turned down the chance to play cinema’s most iconic roles.Filed Under: Aladdin, DisneyCategories: Movie News0 Yorumlar 0 hisse senetleri 61 Views
SCREENCRUSH.COM‘Aladdin’ Is Latest Disney Classic to Get Horror Movie TreatmentAladdin is getting the horror treatment with a “dark, supernatural reimagining.”The classic story, which was famously made into an animated musical by Disney in 1992, which in turn got a live action adaptation in 2019, is the latest family film to be given a terrifying twist.As reported by Deadline, the synopsis for Aladdin: The Monkey’s Paw reads: “A modern-day Londoner, Aladdin, inherits an ancient monkey’s paw believed to grant wishes, only to discover that every desire comes at a soul-crushing price.”“As those around him fall victim to its curse, he must confront a growing evil — and the demonic force that feeds on every wish made.”The movie, which comes from Empire Studios, Every Entertainment and 8th Law Pictures, is set to start filming next month in the U.K.DisneyDisneyloading...READ MORE: Disney Live-Action Remakes Ranked From Worst to BestThe cast will include Queen of the South star Nick Sagar, former EastEnders actor Ricky Norwood, and Tell Me Everything’s Montana Manning.Terrifier 3 star Bradley Stryker is also part of the cast, and will direct the film from a screenplay by Charley McDougall.McDougall said in a statement: “We always wanted to explore horror through a personal lens — not just the scares, but the human cost of wishes. “This story’s been haunting us for a while, and it’s time to let it loose. The best horror films haunt you long after the credits roll. That’s what this story does.”“It’s sharp, emotional, and full of dread in all the right ways. We’re not just making another horror film — we’re building a world around a truly iconic concept. The paw, the mythology, the characters — it’s all there.”Meanwhile, Stryker insisted the film will carry “diabolical and entertaining” stakes as film fans are taken on a journey.It's not the first time a character associated with Disney has been given the horror treatment, after the likes of Winnie-the-Pooh: Blood and Honey and Mickey's Mouse Trap.The latter was announced at the beginning of 2024 after “Steamboat Willie,” the earliest iteration of Disney's iconic mouse mascot, entered public domain.The slasher, which was released on demand in the U.S., focused on a killer wearing a mouse mask targeting college kids at a local arcade.Get our free mobile app25 Actors Who Turned Down Huge Movie RolesSome of the most famous actors in history turned down the chance to play cinema’s most iconic roles.Filed Under: Aladdin, DisneyCategories: Movie News0 Yorumlar 0 hisse senetleri 61 Views -
 WWW.TECHNOLOGYREVIEW.COMThe Download: tracking the evolution of street drugs, and the next wave of military AIThis is today's edition of The Download, our weekday newsletter that provides a daily dose of what's going on in the world of technology. How the federal government is tracking changes in the supply of street drugs In 2021, the Maryland Department of Health and the state police were confronting a crisis: Fatal drug overdoses in the state were at an all-time high, and authorities didn’t know why. Seeking answers, Maryland officials turned to scientists at the National Institute of Standards and Technology, the national metrology institute for the United States, which defines and maintains standards of measurement essential to a wide range of industrial sectors and health and security applications.There, a research chemist named Ed Sisco and his team had developed methods for detecting trace amounts of drugs, explosives, and other dangerous materials—techniques that could protect law enforcement officials and others who had to collect these samples. And a pilot uncovered new, critical information almost immediately. Read the full story.—Adam Bluestein This story is from the next edition of our print magazine. Subscribe now to read it and get a copy of the magazine when it lands! Phase two of military AI has arrived —James O’Donnell Last week, I spoke with two US Marines who spent much of last year deployed in the Pacific, conducting training exercises from South Korea to the Philippines. Both were responsible for analyzing surveillance to warn their superiors about possible threats to the unit. But this deployment was unique: For the first time, they were using generative AI to scour intelligence, through a chatbot interface similar to ChatGPT. As I wrote in my new story, this experiment is the latest evidence of the Pentagon’s push to use generative AI—tools that can engage in humanlike conversation—throughout its ranks, for tasks including surveillance. This push raises alarms from some AI safety experts about whether large language models are fit to analyze subtle pieces of intelligence in situations with high geopolitical stakes. Here are three open questions to keep your eye on as the US military, and others around the world, bring generative AI to more parts of the so-called “kill chain.” Read the full story. This story originally appeared in The Algorithm, our weekly newsletter on AI. To get stories like this in your inbox first, sign up here. The must-reads I’ve combed the internet to find you today’s most fun/important/scary/fascinating stories about technology. 1 The FCC wants Europe to choose between US and Chinese technology Trump official Brendan Carr has urged Western allies to pick Elon Musk’s Starlink over rival Chinese satellite firms. (FT $)+ China may look like a less erratic choice right now. (NY Mag $)2 Nvidia wants to build its AI supercomputers entirely in the US It’s a decision the Trump administration has claimed credit for. (WP $)+ That said, Nvidia hasn’t said how much gear it plans to make in America. (WSJ $)+ Production of its latest chip has already begun in Arizona. (Bloomberg $) 3 Mark Zuckerberg defended Meta in the first day of its antitrust trialHe downplayed the company’s decision to purchase Instagram and WhatsApp. (Politico)+ The government claims he bought the firms to stifle competition. (The Verge)+ Zuckerberg has previously denied that his purchases had hurt competition. (NYT $)4 OpenAI’s new models are designed to excel at coding The three models have been optimized to follow complex instructions. (Wired $)+ We’re still waiting for confirmation of GPT-5. (The Verge)+ The second wave of AI coding is here. (MIT Technology Review) 5 Apple has increased its iPhone shipments by 10%It’s part of a pre-emptive plan to mitigate tariff disruptions. (Bloomberg $) + The tariff chaos has played havoc with Apple stocks. (Insider $)6 We’re learning more about the link between long covid and cognitive impairment Studies suggest that a patient’s age when they contracted covid may be a key factor. (WSJ $)7 Can’t be bothered to call your elderly parents? Get AI to do it 📞404 Media) 8 This video app hopes to capitalize on TikTok’s uncertain futureBut unlike TikTok, Neptune allows creators to hide their likes. (TechCrunch) 9 Meet the tech bros who want to live underwaterColonizing the sea is one of the final frontiers. (NYT $) + Meet the divers trying to figure out how deep humans can go. (MIT Technology Review)10 Google’s new AI model can decipher dolphin sounds🐬 If they’re squawking, back away. (Ars Technica)+ The way whales communicate is closer to human language than we realized. (MIT Technology Review) Quote of the day "If you don't like an ad, you scroll past it. It takes about a second." —Mark Hansen, Meta’s lead lawyer, makes light of the Federal Trade Commission’s assertion that users of its platforms are inundated with ads during the first day of Meta’s monopoly trial, Ars Technica reports. The big story Recapturing early internet whimsy with HTML Websites weren’t always slick digital experiences. There was a time when surfing the web involved opening tabs that played music against your will and sifting through walls of text on a colored background. In the 2000s, before Squarespace and social media, websites were manifestations of individuality—built from scratch using HTML, by users who had some knowledge of code.Scattered across the web are communities of programmers working to revive this seemingly outdated approach. And the movement is anything but a superficial appeal to retro aesthetics—it’s about celebrating the human touch in digital experiences. Read the full story. —Tiffany Ng We can still have nice things A place for comfort, fun and distraction to brighten up your day. (Got any ideas? Drop me a line or skeet 'em at me.) + Who doesn’t love a good stroll?+ All hail Shenmue, the recently-crowned most influential game of all time.+ This Wikipedia-powered museum is really quite something (thanks Amy!)+ This spring’s hottest accessory is a conical princess crown. No, really.0 Yorumlar 0 hisse senetleri 34 Views
WWW.TECHNOLOGYREVIEW.COMThe Download: tracking the evolution of street drugs, and the next wave of military AIThis is today's edition of The Download, our weekday newsletter that provides a daily dose of what's going on in the world of technology. How the federal government is tracking changes in the supply of street drugs In 2021, the Maryland Department of Health and the state police were confronting a crisis: Fatal drug overdoses in the state were at an all-time high, and authorities didn’t know why. Seeking answers, Maryland officials turned to scientists at the National Institute of Standards and Technology, the national metrology institute for the United States, which defines and maintains standards of measurement essential to a wide range of industrial sectors and health and security applications.There, a research chemist named Ed Sisco and his team had developed methods for detecting trace amounts of drugs, explosives, and other dangerous materials—techniques that could protect law enforcement officials and others who had to collect these samples. And a pilot uncovered new, critical information almost immediately. Read the full story.—Adam Bluestein This story is from the next edition of our print magazine. Subscribe now to read it and get a copy of the magazine when it lands! Phase two of military AI has arrived —James O’Donnell Last week, I spoke with two US Marines who spent much of last year deployed in the Pacific, conducting training exercises from South Korea to the Philippines. Both were responsible for analyzing surveillance to warn their superiors about possible threats to the unit. But this deployment was unique: For the first time, they were using generative AI to scour intelligence, through a chatbot interface similar to ChatGPT. As I wrote in my new story, this experiment is the latest evidence of the Pentagon’s push to use generative AI—tools that can engage in humanlike conversation—throughout its ranks, for tasks including surveillance. This push raises alarms from some AI safety experts about whether large language models are fit to analyze subtle pieces of intelligence in situations with high geopolitical stakes. Here are three open questions to keep your eye on as the US military, and others around the world, bring generative AI to more parts of the so-called “kill chain.” Read the full story. This story originally appeared in The Algorithm, our weekly newsletter on AI. To get stories like this in your inbox first, sign up here. The must-reads I’ve combed the internet to find you today’s most fun/important/scary/fascinating stories about technology. 1 The FCC wants Europe to choose between US and Chinese technology Trump official Brendan Carr has urged Western allies to pick Elon Musk’s Starlink over rival Chinese satellite firms. (FT $)+ China may look like a less erratic choice right now. (NY Mag $)2 Nvidia wants to build its AI supercomputers entirely in the US It’s a decision the Trump administration has claimed credit for. (WP $)+ That said, Nvidia hasn’t said how much gear it plans to make in America. (WSJ $)+ Production of its latest chip has already begun in Arizona. (Bloomberg $) 3 Mark Zuckerberg defended Meta in the first day of its antitrust trialHe downplayed the company’s decision to purchase Instagram and WhatsApp. (Politico)+ The government claims he bought the firms to stifle competition. (The Verge)+ Zuckerberg has previously denied that his purchases had hurt competition. (NYT $)4 OpenAI’s new models are designed to excel at coding The three models have been optimized to follow complex instructions. (Wired $)+ We’re still waiting for confirmation of GPT-5. (The Verge)+ The second wave of AI coding is here. (MIT Technology Review) 5 Apple has increased its iPhone shipments by 10%It’s part of a pre-emptive plan to mitigate tariff disruptions. (Bloomberg $) + The tariff chaos has played havoc with Apple stocks. (Insider $)6 We’re learning more about the link between long covid and cognitive impairment Studies suggest that a patient’s age when they contracted covid may be a key factor. (WSJ $)7 Can’t be bothered to call your elderly parents? Get AI to do it 📞404 Media) 8 This video app hopes to capitalize on TikTok’s uncertain futureBut unlike TikTok, Neptune allows creators to hide their likes. (TechCrunch) 9 Meet the tech bros who want to live underwaterColonizing the sea is one of the final frontiers. (NYT $) + Meet the divers trying to figure out how deep humans can go. (MIT Technology Review)10 Google’s new AI model can decipher dolphin sounds🐬 If they’re squawking, back away. (Ars Technica)+ The way whales communicate is closer to human language than we realized. (MIT Technology Review) Quote of the day "If you don't like an ad, you scroll past it. It takes about a second." —Mark Hansen, Meta’s lead lawyer, makes light of the Federal Trade Commission’s assertion that users of its platforms are inundated with ads during the first day of Meta’s monopoly trial, Ars Technica reports. The big story Recapturing early internet whimsy with HTML Websites weren’t always slick digital experiences. There was a time when surfing the web involved opening tabs that played music against your will and sifting through walls of text on a colored background. In the 2000s, before Squarespace and social media, websites were manifestations of individuality—built from scratch using HTML, by users who had some knowledge of code.Scattered across the web are communities of programmers working to revive this seemingly outdated approach. And the movement is anything but a superficial appeal to retro aesthetics—it’s about celebrating the human touch in digital experiences. Read the full story. —Tiffany Ng We can still have nice things A place for comfort, fun and distraction to brighten up your day. (Got any ideas? Drop me a line or skeet 'em at me.) + Who doesn’t love a good stroll?+ All hail Shenmue, the recently-crowned most influential game of all time.+ This Wikipedia-powered museum is really quite something (thanks Amy!)+ This spring’s hottest accessory is a conical princess crown. No, really.0 Yorumlar 0 hisse senetleri 34 Views -
 WWW.BDONLINE.CO.UKSheppard Robson’s Salford University acoustics facility approvedBuilding to contain advanced acoustics testing chambers for industrial and commercial research Exterior view of the approved scheme Sheppard Robson has been given the go ahead for an advanced acoustics research facility for the University of Salford. The 1,300sq m building is being billed by the university as an investment into acoustics research on an “international scale”. The scheme, which is expected to take around 18 months to build, will contain a series of acoustic testing chambers for researchers and specialist technical staff to measure sounds for a range of commercial and industrial uses. It is part of Salford University’s six-decade long work with some of the world’s biggest manufacturing brands to ensure products emit acceptable levels of noise. CGI showing the building’s internal research spaces Most recently Salford’s experts have worked on projects to manage drone noise, develop e-scooter alarm noises and make forklift trucks safer in a work environment. The new centre is aiming to increase the research, innovation and development that the university’s acoustics team is able to offer. Contractor Morgan Sindall is set to start work on scheme this summer. Director of the National Institute of Airborne Acoustic Metrology at the University of Salford, Claire Lomax said: “The whole acoustics team at Salford are thrilled planning consent has been granted for this globally unique building. Every person on earth is affected by what they can or cannot hear, which is why acoustics as a science is so significant. “To have this facility in Salford shows the University’s commitment to innovation to enrich lives – in this case through pioneering research, impacting policy and industry standards, and shaping products sold worldwide.” The project team also includes client project manager Gleeds, acoustics consultant Arup, MEP engineer Buro Happold, structural engineer Renaissance, landscape architect Planit and sustainability consultant BDP. It will sit within the wider £2.5bn, 240 acre Crescent Salford masterplan which is being delivered by the Crescent Partnership, the university, Salford city council and ECF in a joint partnership with Homes England, L&G and Muse.0 Yorumlar 0 hisse senetleri 54 Views
WWW.BDONLINE.CO.UKSheppard Robson’s Salford University acoustics facility approvedBuilding to contain advanced acoustics testing chambers for industrial and commercial research Exterior view of the approved scheme Sheppard Robson has been given the go ahead for an advanced acoustics research facility for the University of Salford. The 1,300sq m building is being billed by the university as an investment into acoustics research on an “international scale”. The scheme, which is expected to take around 18 months to build, will contain a series of acoustic testing chambers for researchers and specialist technical staff to measure sounds for a range of commercial and industrial uses. It is part of Salford University’s six-decade long work with some of the world’s biggest manufacturing brands to ensure products emit acceptable levels of noise. CGI showing the building’s internal research spaces Most recently Salford’s experts have worked on projects to manage drone noise, develop e-scooter alarm noises and make forklift trucks safer in a work environment. The new centre is aiming to increase the research, innovation and development that the university’s acoustics team is able to offer. Contractor Morgan Sindall is set to start work on scheme this summer. Director of the National Institute of Airborne Acoustic Metrology at the University of Salford, Claire Lomax said: “The whole acoustics team at Salford are thrilled planning consent has been granted for this globally unique building. Every person on earth is affected by what they can or cannot hear, which is why acoustics as a science is so significant. “To have this facility in Salford shows the University’s commitment to innovation to enrich lives – in this case through pioneering research, impacting policy and industry standards, and shaping products sold worldwide.” The project team also includes client project manager Gleeds, acoustics consultant Arup, MEP engineer Buro Happold, structural engineer Renaissance, landscape architect Planit and sustainability consultant BDP. It will sit within the wider £2.5bn, 240 acre Crescent Salford masterplan which is being delivered by the Crescent Partnership, the university, Salford city council and ECF in a joint partnership with Homes England, L&G and Muse.0 Yorumlar 0 hisse senetleri 54 Views -
 WWW.ARCHITECTSJOURNAL.CO.UKCase study: Hanham Hall by HTA DesignBuilt using Modern Methods of Construction (MMC), Hanham Hall was the first large-scale volume housebuilder scheme in England to meet the 2016 zero-carbon standard. The Barratt Homes development created 185 new homes on a 3.8ha site formerly occupied by a psychiatric hospital on the outskirts of Bristol. HTA Design’s project included the renovation of the Grade II*-listed Hanham Hall itself, which has been repurposed for community use. The extensive grounds have been regenerated to increase biodiversity as well as providing playspaces, greenhouses and allotments. Architect's voice Our first challenge was achieving the zero-carbon standard for all homes. Leading with fabric-first construction, structural insulated panels (SIPs) formed walls and roofs, providing excellent thermal performance, airtightness and speed of construction. Utilising SIPs led to considerable benefits compared with a standard onsite masonry approach. Combined with photovoltaic panels and mechanical ventilation with heat recovery (MVHR) systems, the homes minimise energy use and cost. Simple passive design solutions support comfort and usability year-round. All homes meet Lifetime Homes and Building for Life standards. The development had to carefully respond to, and even enhance, the surrounding green belt fields. New biodiverse meadows and orchards were designed around existing mature hedgerows, waterways and retained mature trees, embedded as part of a site-wide sustainable urban drainage system. Simon Toplis, partner and head of architecture, HTA Design Project data Location Whittucks Road, Hanham, Bristol Type New build Context Suburban Planning permission date November 2009 Completion 2013 Construction cost £42 million Construction cost per m² £3,700 Construction cost per home £215,000 Number of homes 185 Housing type Houses and flats Mix of homes Percentage of 1B2P: 19%, Percentage of 2B3P: 26%, Percentage of 2B4P: 9%, Percentage of 3B5P: 10%, Percentage of 4B6P: 33%, Percentage of 5B8P: 3% Site area 3.8ha Density 51.3 homes per hectare Development area 18,994m² (total), 17,006m² (residential) Height 2-3 storeys Tenure mix 65% private sale, 35% affordable Percentage of affordable housing 35% Aspect 100% dual-aspect homes Client Barratt Homes Client type Housebuilder Architectural appointment Direct appointment Procurement Design and build Design or Quality Review Panel review No Design team novation Yes Lead contractor Barratt Homes Main structural system Composite timber frameAdvertisement Environmental data Annual carbon emissions 10.62 kgCO2/m² Operational energy use 58 kWh/m²/yr Onsite energy generation 21% Average energy bill per home Unknown All-electric No Post-occupancy evaluation undertaken Yes U-values 0.14 W/m²K (walls, roofs and floors, area-weighted) Airtightness at 50Pa 1.50 m³/h.m² Residents' voices I love that Hanham Hall is surrounded by the wildlife-rich Avon Woods, expansive fields, and has its own wildflower meadow, allotments, orchard and beehives. Anonymous resident After a neighbour lent us a garden bed in their allotment for us to trial, gardening has become an integral part of my creative and wellbeing practice. It has also been a big part of getting to know people – and a big part of the whole ethos here of getting in touch with nature. Anonymous resident Living here feeds my fascination with nature and seasonality, allowing me to imbue my creative practice, artworks and workshops with this same curiosity and reverence. Holly0 Yorumlar 0 hisse senetleri 26 Views
WWW.ARCHITECTSJOURNAL.CO.UKCase study: Hanham Hall by HTA DesignBuilt using Modern Methods of Construction (MMC), Hanham Hall was the first large-scale volume housebuilder scheme in England to meet the 2016 zero-carbon standard. The Barratt Homes development created 185 new homes on a 3.8ha site formerly occupied by a psychiatric hospital on the outskirts of Bristol. HTA Design’s project included the renovation of the Grade II*-listed Hanham Hall itself, which has been repurposed for community use. The extensive grounds have been regenerated to increase biodiversity as well as providing playspaces, greenhouses and allotments. Architect's voice Our first challenge was achieving the zero-carbon standard for all homes. Leading with fabric-first construction, structural insulated panels (SIPs) formed walls and roofs, providing excellent thermal performance, airtightness and speed of construction. Utilising SIPs led to considerable benefits compared with a standard onsite masonry approach. Combined with photovoltaic panels and mechanical ventilation with heat recovery (MVHR) systems, the homes minimise energy use and cost. Simple passive design solutions support comfort and usability year-round. All homes meet Lifetime Homes and Building for Life standards. The development had to carefully respond to, and even enhance, the surrounding green belt fields. New biodiverse meadows and orchards were designed around existing mature hedgerows, waterways and retained mature trees, embedded as part of a site-wide sustainable urban drainage system. Simon Toplis, partner and head of architecture, HTA Design Project data Location Whittucks Road, Hanham, Bristol Type New build Context Suburban Planning permission date November 2009 Completion 2013 Construction cost £42 million Construction cost per m² £3,700 Construction cost per home £215,000 Number of homes 185 Housing type Houses and flats Mix of homes Percentage of 1B2P: 19%, Percentage of 2B3P: 26%, Percentage of 2B4P: 9%, Percentage of 3B5P: 10%, Percentage of 4B6P: 33%, Percentage of 5B8P: 3% Site area 3.8ha Density 51.3 homes per hectare Development area 18,994m² (total), 17,006m² (residential) Height 2-3 storeys Tenure mix 65% private sale, 35% affordable Percentage of affordable housing 35% Aspect 100% dual-aspect homes Client Barratt Homes Client type Housebuilder Architectural appointment Direct appointment Procurement Design and build Design or Quality Review Panel review No Design team novation Yes Lead contractor Barratt Homes Main structural system Composite timber frameAdvertisement Environmental data Annual carbon emissions 10.62 kgCO2/m² Operational energy use 58 kWh/m²/yr Onsite energy generation 21% Average energy bill per home Unknown All-electric No Post-occupancy evaluation undertaken Yes U-values 0.14 W/m²K (walls, roofs and floors, area-weighted) Airtightness at 50Pa 1.50 m³/h.m² Residents' voices I love that Hanham Hall is surrounded by the wildlife-rich Avon Woods, expansive fields, and has its own wildflower meadow, allotments, orchard and beehives. Anonymous resident After a neighbour lent us a garden bed in their allotment for us to trial, gardening has become an integral part of my creative and wellbeing practice. It has also been a big part of getting to know people – and a big part of the whole ethos here of getting in touch with nature. Anonymous resident Living here feeds my fascination with nature and seasonality, allowing me to imbue my creative practice, artworks and workshops with this same curiosity and reverence. Holly0 Yorumlar 0 hisse senetleri 26 Views -
 WWW.CNET.COMAndroid Phones Will Now Automatically Restart After 3 Days if Untouched. Here's WhyThe new feature is designed to better secure your data.0 Yorumlar 0 hisse senetleri 25 Views
WWW.CNET.COMAndroid Phones Will Now Automatically Restart After 3 Days if Untouched. Here's WhyThe new feature is designed to better secure your data.0 Yorumlar 0 hisse senetleri 25 Views -
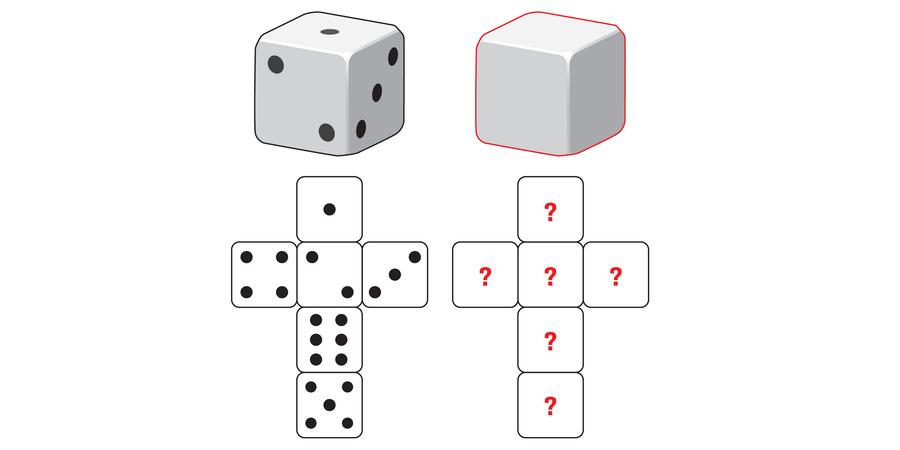 WWW.SCIENTIFICAMERICAN.COMMath Puzzle: Construct the DiceMarie has one regular die labeled with the numbers 1, 2, 3, 4, 5 and 6 and a second cube that is completely blank. She labels this cube in a special way. If you roll both dice, you can get the following totals: 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11 and 12. The special part: all 12 total values are equally likely to be rolled. How did Marie label the cube?Amanda MontañezThe sides of the die must be labeled 0, 0, 0, 6, 6 and 6.There are 36 possible totals when rolling two dice. If the 12 sum values are all to have the same probability, then each value must occur exactly three times.Amanda MontañezThe total value of 12 can be achieved with two dice only if both dice show a 6. Because the value 12 must appear three times in the table, the cube Marie labels must have three sides with a 6. The rest of the needed results are possible only if the other three sides are labeled with a 0.For each sum value from 1 to 12, the probability p isp = 3 / 36 = 1 / 12 ≈ 8.3%We’d love to hear from you! E-mail us at games@sciam.com to share your experience.This puzzle originally appeared in Spektrum der Wissenschaft and was reproduced with permission.0 Yorumlar 0 hisse senetleri 25 Views
WWW.SCIENTIFICAMERICAN.COMMath Puzzle: Construct the DiceMarie has one regular die labeled with the numbers 1, 2, 3, 4, 5 and 6 and a second cube that is completely blank. She labels this cube in a special way. If you roll both dice, you can get the following totals: 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11 and 12. The special part: all 12 total values are equally likely to be rolled. How did Marie label the cube?Amanda MontañezThe sides of the die must be labeled 0, 0, 0, 6, 6 and 6.There are 36 possible totals when rolling two dice. If the 12 sum values are all to have the same probability, then each value must occur exactly three times.Amanda MontañezThe total value of 12 can be achieved with two dice only if both dice show a 6. Because the value 12 must appear three times in the table, the cube Marie labels must have three sides with a 6. The rest of the needed results are possible only if the other three sides are labeled with a 0.For each sum value from 1 to 12, the probability p isp = 3 / 36 = 1 / 12 ≈ 8.3%We’d love to hear from you! E-mail us at games@sciam.com to share your experience.This puzzle originally appeared in Spektrum der Wissenschaft and was reproduced with permission.0 Yorumlar 0 hisse senetleri 25 Views



