0 Commentarios
0 Acciones
157 Views

Directorio
Directorio
-
Please log in to like, share and comment!
-
 BLOGS.NVIDIA.COMKeeping an AI on Diabetes Risk: Gen AI Model Predicts Blood Sugar Levels Four Years OutDiabetics or others monitoring their sugar intake may look at a cookie and wonder, How will eating this affect my glucose levels? A generative AI model can now predict the answer.Researchers from the Weizmann Institute of Science, Tel Aviv-based startup Pheno.AI and NVIDIA led the development of GluFormer, an AI model that can predict an individuals future glucose levels and other health metrics based on past glucose monitoring data.Data from continuous glucose monitoring could help more quickly diagnose patients with prediabetes or diabetes, according to Harvard Health Publishing and NYU Langone Health. GluFormers AI capabilities can further enhance the value of this data, helping clinicians and patients spot anomalies, predict clinical trial outcomes and forecast health outcomes up to four years in advance.The researchers showed that, after adding dietary intake data into the model, GluFormer can also predict how a persons glucose levels will respond to specific foods and dietary changes, enabling precision nutrition.Accurate predictions of glucose levels for those at high risk of developing diabetes could enable doctors and patients to adopt preventative care strategies sooner, improving patient outcomes and reducing the economic impact of diabetes, which could reach $2.5 trillion globally by 2030.AI tools like GluFormer have the potential to help the hundreds of millions of adults with diabetes. The condition currently affects around 10% of the worlds adults a figure that could potentially double by 2050 to impact over 1.3 billion people. Its one of the 10 leading causes of death globally, with side effects including kidney damage, vision loss and heart problems.GluFormer is a transformer model, a kind of neural network architecture that tracks relationships in sequential data. Its the same architecture as OpenAIs GPT models in this case generating glucose levels instead of text.Medical data, and continuous glucose monitoring in particular, can be viewed as sequences of diagnostic tests that trace biological processes throughout life, said Gal Chechik, senior director of AI research at NVIDIA. We found that the transformer architecture, developed for long text sequences, can take a sequence of medical tests and predict the results of the next test. In doing so, it learns something about how the diagnostic measurements develop over time.The model was trained on 14 days of glucose monitoring data from over 10,000 non-diabetic study participants, with data collected every 15 minutes through a wearable monitoring device. The data was collected as part of the Human Phenotype Project, an initiative by Pheno.AI, a startup that aims to improve human health through data collection and analysis.Two important factors converged at the same time to enable this research: the maturing of generative AI technology powered by NVIDIA and the collection of large-scale health data by the Weizmann Institute, said the papers lead author, Guy Lutsker, an NVIDIA researcher and Ph.D. student at the Weizmann Institute of Science. It put us in the unique position to extract interesting medical insights from the data.The research team validated GluFormer across 15 other datasets and found it generalizes well to predict health outcomes for other groups, including those with prediabetes, type 1 and type 2 diabetes, gestational diabetes and obesity.They used a cluster of NVIDIA Tensor Core GPUs to accelerate model training and inference.Beyond glucose levels, GluFormer can predict medical values including visceral adipose tissue, a measure of the amount of body fat around organs like the liver and pancreas; systolic blood pressure, which is associated with diabetes risk; and apnea-hypopnea index, a measurement for sleep apnea, which is linked to type 2 diabetes.Read the GluFormer research paper on Arxiv.0 Commentarios 0 Acciones 150 Views
BLOGS.NVIDIA.COMKeeping an AI on Diabetes Risk: Gen AI Model Predicts Blood Sugar Levels Four Years OutDiabetics or others monitoring their sugar intake may look at a cookie and wonder, How will eating this affect my glucose levels? A generative AI model can now predict the answer.Researchers from the Weizmann Institute of Science, Tel Aviv-based startup Pheno.AI and NVIDIA led the development of GluFormer, an AI model that can predict an individuals future glucose levels and other health metrics based on past glucose monitoring data.Data from continuous glucose monitoring could help more quickly diagnose patients with prediabetes or diabetes, according to Harvard Health Publishing and NYU Langone Health. GluFormers AI capabilities can further enhance the value of this data, helping clinicians and patients spot anomalies, predict clinical trial outcomes and forecast health outcomes up to four years in advance.The researchers showed that, after adding dietary intake data into the model, GluFormer can also predict how a persons glucose levels will respond to specific foods and dietary changes, enabling precision nutrition.Accurate predictions of glucose levels for those at high risk of developing diabetes could enable doctors and patients to adopt preventative care strategies sooner, improving patient outcomes and reducing the economic impact of diabetes, which could reach $2.5 trillion globally by 2030.AI tools like GluFormer have the potential to help the hundreds of millions of adults with diabetes. The condition currently affects around 10% of the worlds adults a figure that could potentially double by 2050 to impact over 1.3 billion people. Its one of the 10 leading causes of death globally, with side effects including kidney damage, vision loss and heart problems.GluFormer is a transformer model, a kind of neural network architecture that tracks relationships in sequential data. Its the same architecture as OpenAIs GPT models in this case generating glucose levels instead of text.Medical data, and continuous glucose monitoring in particular, can be viewed as sequences of diagnostic tests that trace biological processes throughout life, said Gal Chechik, senior director of AI research at NVIDIA. We found that the transformer architecture, developed for long text sequences, can take a sequence of medical tests and predict the results of the next test. In doing so, it learns something about how the diagnostic measurements develop over time.The model was trained on 14 days of glucose monitoring data from over 10,000 non-diabetic study participants, with data collected every 15 minutes through a wearable monitoring device. The data was collected as part of the Human Phenotype Project, an initiative by Pheno.AI, a startup that aims to improve human health through data collection and analysis.Two important factors converged at the same time to enable this research: the maturing of generative AI technology powered by NVIDIA and the collection of large-scale health data by the Weizmann Institute, said the papers lead author, Guy Lutsker, an NVIDIA researcher and Ph.D. student at the Weizmann Institute of Science. It put us in the unique position to extract interesting medical insights from the data.The research team validated GluFormer across 15 other datasets and found it generalizes well to predict health outcomes for other groups, including those with prediabetes, type 1 and type 2 diabetes, gestational diabetes and obesity.They used a cluster of NVIDIA Tensor Core GPUs to accelerate model training and inference.Beyond glucose levels, GluFormer can predict medical values including visceral adipose tissue, a measure of the amount of body fat around organs like the liver and pancreas; systolic blood pressure, which is associated with diabetes risk; and apnea-hypopnea index, a measurement for sleep apnea, which is linked to type 2 diabetes.Read the GluFormer research paper on Arxiv.0 Commentarios 0 Acciones 150 Views -
 BLOGS.NVIDIA.COMNVIDIA Ranks No. 1 as Forbes Debuts List of Americas Best Companies 2025NVIDIA ranked No. 1 on Forbes magazines new list Americas Best Companies based on more than 60 measures in nearly a dozen categories that cover financial performance, customer and employee satisfaction, sustainability, remote work policies and more.Forbes stated that the company thrived in numerous areas, particularly employee satisfaction, earning high ratings in career opportunities, company benefits and culture, as well as financial strength.About 2,000 of the largest public companies in the U.S. were eligible, with 300 making the list.Beau Davidson, vice president of employee experience at NVIDIA, told Forbes that the company has created systemic opportunities to listen to its staff (such as quarterly surveys, CEO Q&As and a virtual suggestion box) and then takes action on concerns ranging from benefits to cafe snacks.NVIDIA has also championed Free Days two days each quarter where the entire company closes. It allows us to take a break as a company, Davidson told Forbes. NVIDIA provides counselors onsite and a careers week that provides programs and training for workers to pursue internal job opportunities.NVIDIA enjoys a low rate of employee turnover widely viewed as a sign of employee happiness, according to People Data Labs, Forbes data provider on workforce stability.For a full list of rankings, view Forbes Americas Best Companies 2025 list.Check out the NVIDIA Careers page and learn more about NVIDIA Life.0 Commentarios 0 Acciones 170 Views
BLOGS.NVIDIA.COMNVIDIA Ranks No. 1 as Forbes Debuts List of Americas Best Companies 2025NVIDIA ranked No. 1 on Forbes magazines new list Americas Best Companies based on more than 60 measures in nearly a dozen categories that cover financial performance, customer and employee satisfaction, sustainability, remote work policies and more.Forbes stated that the company thrived in numerous areas, particularly employee satisfaction, earning high ratings in career opportunities, company benefits and culture, as well as financial strength.About 2,000 of the largest public companies in the U.S. were eligible, with 300 making the list.Beau Davidson, vice president of employee experience at NVIDIA, told Forbes that the company has created systemic opportunities to listen to its staff (such as quarterly surveys, CEO Q&As and a virtual suggestion box) and then takes action on concerns ranging from benefits to cafe snacks.NVIDIA has also championed Free Days two days each quarter where the entire company closes. It allows us to take a break as a company, Davidson told Forbes. NVIDIA provides counselors onsite and a careers week that provides programs and training for workers to pursue internal job opportunities.NVIDIA enjoys a low rate of employee turnover widely viewed as a sign of employee happiness, according to People Data Labs, Forbes data provider on workforce stability.For a full list of rankings, view Forbes Americas Best Companies 2025 list.Check out the NVIDIA Careers page and learn more about NVIDIA Life.0 Commentarios 0 Acciones 170 Views -
BLOG.PLAYSTATION.COMOfficial PlayStation Podcast Episode 500: Celebrating 30 Years of PlayStation (Part 1)Email us at PSPodcast@sony.com!Subscribe via Apple Podcasts, Spotify, or download hereHey yall, Episode 500 is finally here! Thank you to all the loyal listeners for making this momentous episode possible. Can you believe the show started back in 2011? Whether youve been with us for the entire run or are a new listener, we appreciate you.This week, the crew hears from listeners and developers about some of their favorite PlayStation games and memories. The podcast crew also dives into their favorite games on the original PlayStation and PlayStation 2. But the celebration doesnt end here! Well continue to feature listeners and developers leading up to PlayStations 30th anniversary on December 3.Stuff We Talked AboutNext weeks release highlights:Spirit Mancer | PS5Towers of Aghasba (Early Access) | PS5Stellar Blade x Nier: Automata DLC and Photo ModePlayers Choice Winner Dragon Ball: Sparking ZeroPlayStation Plus Game Catalog for November:Grand Theft Auto VDying Light 2: Stay HumanLike a Dragon: IshinMotoGP 24The Sims 4: Island LivingAnd moreLEGO Horizon Adventures is out nowSpecial listener/developer favorite PlayStation games segmentThe podcast crew highlights personal top games for the original PlayStation and PS2 (to be continued)The CastView and download imageDownload the imagecloseCloseDownload this imageSid Shuman Senior Director of Content Communications, SIEView and download imageDownload the imagecloseCloseDownload this imageTim Turi Content Communications Manager, SIEView and download imageDownload the imagecloseCloseDownload this imageBrett Elston Manager, Content Communications, SIEView and download imageDownload the imagecloseCloseDownload this imageODell Harmon Jr. Content Communications Specialist, SIEThanks to Dormiln for our rad theme song and show music.[Editors note: PSN game release dates are subject to change without notice. Game details are gathered from press releases from their individual publishers and/or ESRB rating descriptions.]0 Commentarios 0 Acciones 132 Views
-
 BLOG.PLAYSTATION.COMPhoto Mode returns in Tomb Raider IV-VI Remastered, launching February 14Lara Crofts legendary adventures continue on February 14 with the release of Tomb Raider IV-VI Remastered! As we patiently await her return, wed love to take a moment to explore some enhanced features created specifically for this remaster.This latest collection not only revitalizes Laras adventures but also brings back a fan-favorite feature Photo Mode to capture all the thrilling moments you encounter.Explore and capture iconic momentsAs you swan-dive back into Lara Crofts darkest adventures, youll have the ability to capture and share in the beauty and excitement of your adventures with your friends.Whether youre scaling the Great Pyramid of Giza in The Last Revelation, sneaking through a high-security complex in Chronicles, or uncovering dark secrets in the shadowy streets of Paris in The Angel of Darkness, Photo Mode lets you freeze, frame, and capture your most memorable moments.Photo Mode featuresNew Poses and Outfits: In addition to including all of the poses and outfits from Tomb Raider I-III Remastered, this new collection will include even more as an added bonus. Tailor each shot to reflect her adventurous spirit and style.Customizable Shots: Set up your scenes with ease using adjustable camera angles, depth of field, and zoom effects. Create the perfect composition to showcase the remastered environments.Dynamic Expressions: Choose from a range of expressions to bring Laras character to life in your photos. Highlight her bravery, determination, or curiosity with ease.Seamless Integration: Use Photo Mode anytime during gameplay to capture those spontaneous, unforgettable moments. Whether its a breathtaking view or a dramatic encounter, your perfect shot is always just a menu away.Step-by-Step GuideActivate Photo Mode: Photo Mode activates by holding down both of your sticks on the DualSense controller.Frame Your Shot: Adjust the camera angle, zoom, and depth of field, using the on-screen controls and find your desired composition.Hit the Dressing Room: Pick from various outfits from across the Tomb Raider I-VI Remastered collection. Equip her with different weapons for an added touch of sass.Express Yourself: Select Laras expression to convey the right mood for your shot. What are we feeling today: a victorious and joyful smile, or a bombastic side-eye?Strike a Pose: Pick your favorite pose from across our Tomb Raider I-VI Remastered collection! Whether its a fierce battle stance or a triumphant pose, have fun customizing it to your liking.Capture and Share: Once youre satisfied with your shot, use the Create button on your controller. Share your best shots with the community and join fellow fans in celebrating Lara Crofts legacy.How about a First Look?As you swan dive into even more details around Tomb Raider IV-VI Remastered, the Photo Mode feature isnt the only exciting addition! Alongside capturing epic moments, fans can look forward to new collectible achievements and unique art badges, each one a striking tribute to Laras legacy.And for those who remember the heart-pounding encounters with the nearly indestructible mini-bosses, were thrilled to showcase a new look at two of Lara Crofts most formidable foes: the relentless Bronze Bull and the fearsome Minotaur from The Last Revelation.Tomb Raider IV-VI Remastered launches on PlayStation 4 & PlayStation 5 on February 14, 2025. Head over to PlayStation Store to pre-order if you havent already.0 Commentarios 0 Acciones 122 Views
BLOG.PLAYSTATION.COMPhoto Mode returns in Tomb Raider IV-VI Remastered, launching February 14Lara Crofts legendary adventures continue on February 14 with the release of Tomb Raider IV-VI Remastered! As we patiently await her return, wed love to take a moment to explore some enhanced features created specifically for this remaster.This latest collection not only revitalizes Laras adventures but also brings back a fan-favorite feature Photo Mode to capture all the thrilling moments you encounter.Explore and capture iconic momentsAs you swan-dive back into Lara Crofts darkest adventures, youll have the ability to capture and share in the beauty and excitement of your adventures with your friends.Whether youre scaling the Great Pyramid of Giza in The Last Revelation, sneaking through a high-security complex in Chronicles, or uncovering dark secrets in the shadowy streets of Paris in The Angel of Darkness, Photo Mode lets you freeze, frame, and capture your most memorable moments.Photo Mode featuresNew Poses and Outfits: In addition to including all of the poses and outfits from Tomb Raider I-III Remastered, this new collection will include even more as an added bonus. Tailor each shot to reflect her adventurous spirit and style.Customizable Shots: Set up your scenes with ease using adjustable camera angles, depth of field, and zoom effects. Create the perfect composition to showcase the remastered environments.Dynamic Expressions: Choose from a range of expressions to bring Laras character to life in your photos. Highlight her bravery, determination, or curiosity with ease.Seamless Integration: Use Photo Mode anytime during gameplay to capture those spontaneous, unforgettable moments. Whether its a breathtaking view or a dramatic encounter, your perfect shot is always just a menu away.Step-by-Step GuideActivate Photo Mode: Photo Mode activates by holding down both of your sticks on the DualSense controller.Frame Your Shot: Adjust the camera angle, zoom, and depth of field, using the on-screen controls and find your desired composition.Hit the Dressing Room: Pick from various outfits from across the Tomb Raider I-VI Remastered collection. Equip her with different weapons for an added touch of sass.Express Yourself: Select Laras expression to convey the right mood for your shot. What are we feeling today: a victorious and joyful smile, or a bombastic side-eye?Strike a Pose: Pick your favorite pose from across our Tomb Raider I-VI Remastered collection! Whether its a fierce battle stance or a triumphant pose, have fun customizing it to your liking.Capture and Share: Once youre satisfied with your shot, use the Create button on your controller. Share your best shots with the community and join fellow fans in celebrating Lara Crofts legacy.How about a First Look?As you swan dive into even more details around Tomb Raider IV-VI Remastered, the Photo Mode feature isnt the only exciting addition! Alongside capturing epic moments, fans can look forward to new collectible achievements and unique art badges, each one a striking tribute to Laras legacy.And for those who remember the heart-pounding encounters with the nearly indestructible mini-bosses, were thrilled to showcase a new look at two of Lara Crofts most formidable foes: the relentless Bronze Bull and the fearsome Minotaur from The Last Revelation.Tomb Raider IV-VI Remastered launches on PlayStation 4 & PlayStation 5 on February 14, 2025. Head over to PlayStation Store to pre-order if you havent already.0 Commentarios 0 Acciones 122 Views -
 WWW.POLYGON.COMDeadpool & Wolverine, Twisters, Netflixs Emilia Prez, and every movie new to streamingEach week on Polygon, we round up the most notable new releases to streaming and VOD, highlighting the biggest and best new movies for you to watch at home.This week, Deadpool & Wolverine, the 34th film in the Marvel Cinematic Universe and starring Ryan Reynolds and Hugh Jackman, arrives on Disney Plus following its VOD premiere early in October. Theres plenty of other new releases to enjoy this week, like Twisters on Peacock, Transformers One on Paramount Plus, the geri-action revenge comedy Thelma on Hulu, and the scintillating crime-drama musical Emilia Prez starring Zoe Saldaa (Guardians of the Galaxy Vol. 3) on Netflix. Not to mention a bunch of new movies arrive on VOD, like Francis Ford Coppolas Megalopolis starring Adam Driver (Star Wars: The Last Jedi) and Magpie starring Daisy Ridley (Star Wars: The Last Jedi).Heres everything new thats available to watch this weekend!New on NetflixEmilia PrezWhere to watch: Available to stream on NetflixGenre: Crime musicalRun time: 2h 12mDirector: Jacques AudiardCast: Zoe Saldaa, Karla Sofa Gascn, Selena GomezCannes Jury Prize winnerEmilia Prezis a crime film, a comedy,anda musical. Based on an opera libretto of the same name,Emilia Prezfollows a cartel leader who wants to complete her gender transition. She hires a lawyer to help her find a surgeon, fake her own death, and hide her family away for their safety. But Emilia cant quite run from her life of crime, and when she tries to reunite with her family, that shady past comes back to haunt her.Close to YouWhere to watch: Available to stream on NetflixGenre: DramaRun time: 1h 40mDirector: Dominic SavageCast: Elliot Page, Hillary Baack, Peter OuterbridgeElliot Page stars as a man named Sam who travels to his hometown for the first time in four years to celebrate his fathers birthday. In the face of familial tension, a lot involving his family struggling to accept his gender transition, Sam reconnects with an old flame.Close to Youpremiered at the 2023 Toronto International Film Festival, with critics praising Pages naturalistic performance.Widow ClicquotWhere to watch: Available to stream on NetflixGenre: DramaRun time: 1h 30mDirector: Thomas NapperCast: Haley Bennett, Tom Sturridge, Natasha OKeeffeThis period drama stars Haley Bennett (Swallow) as Barbe-Nicole Clicquot, the widow of an 18th-century vigneron who becomes the head of their fledgling vineyard after his untimely passing. Weathering financial difficulty and political turmoil, Barbe-Nicole must struggle to make a name for herself and nurture the company to fruition.Hot FrostyWhere to watch: Available to stream on NetflixGenre: Fantasy rom-comRun time: 1h 30mDirector: Jerry CiccorittiCast: Lacey Chabert, Dustin Milligan, Katy MixonThis questionably titled romantic comedy follows Kathy (Lacey Chabert), a recently widowed woman who finds herself alone for the holidays. After accidentally bringing a handsome snowman named Jack (Dustin Milligan) to life, Kathy quickly finds herself head over heels for our sexy new beau. As their relationship heats up, can both of them keep their cool?New on HuluThelmaWhere to watch: Available to stream on HuluGenre:Action comedyRun time:1h 38mDirector:Josh MargolinCast:June Squibb, Fred Hechinger, Richard RoundtreeThelma is a revenge flick about one woman journeying across Los Angeles to reclaim whats been taken from her and also she happens to be 93 years old, so a lot of that trekking is done on a senior mobility scooter.From ourreview:Thelma watches a Mission: Impossible film during the movie, and her Tom Cruise inspiration is not just there in spirit, but in the text itself. After she gets scammed, its seeing Cruises face on a magazine that inspires Thelma to take justice into her own hands. But that kind of sincerity wouldnt work withoutThelmas terrific and committed performances, particularly from Squibb and Roundtree. Both actors are terrifically funny, and Roundtrees charm gives the movie a tremendous amount of heart. For her part, Margolin says Squibb was adamant about owning the Tom Cruise mantle and doing as many stunts as she could herself.Its rare that a summer action movie also happens to be one of the funniest and sweetest movies of the year, butThelmamanages to pull it off. So if youre feeling the lack of Tom Cruise at movie theaters this year, just remember thatThelmaand June Squibb are there, carrying the torch in his honor.New on Disney PlusDeadpool & WolverineWhere to watch: Available to stream on MaxGenre:Superhero actionRun time:2h 8mDirector:Shawn LevyCast:Ryan Reynolds, Hugh Jackman, Emma CorrinRyan Reynolds reprises his role as Deadpool, the so-called Merc with a Mouth, in his first-ever appearance in the Marvel Cinematic Universe. After being abducted by the Time Variance Authority, Deadpool embarks on a quest to recruit an alternate universe version of Wolverine (Hugh Jackman) to help prevent his own universe from being destroyed. Matthew Macfadyen (Succession) plays Mr. Paradox, a rogue member of the TVA, and Emma Corrin (A Murder at the End of the World) portraysCassandra Nova, Professor Xs evil twin sister from an alternate universe.From ourreview:Deadpool & Wolverinehas made its hero the worst kind of comic book character: one who doesnt stand for anything. Its a terrible irony. Fans worried that Disneys corporate control and the MCUs rigid narrative oversight would leech away Deadpools edge: the swearing and the jocular violence. Turns out, that part was fine. Instead, the MCU just took his fuckin heart.New on Paramount PlusTransformers OneWhere to watch: Streaming on Paramount PlusGenre: Sci-fi adventureRun time: 1h 17mDirector: Josh CooleyCast: Chris Hemsworth, Brian Tyree Henry, Scarlett JohanssonThis animated prequel to the Transformers franchise chronicles the origins of Orion Pax (Chris Hemsworth) and D-16 (Brian Tyree Henry) years before they would later become known as Optimus Prime and Megatron. Set on the planet of Cybertron, Transformers One centers on Orion and D-16s friendship before a quirk of fate set them on the path to becoming bitter enemies.From our review:Director Josh Cooleys semi-reboot of the Transformers cinematic universe whether it has any association with the Transformers Bay-verse is somehow unclear is better than its prequel premise (andtrailers) suggests.Transformers Oneis funny, sometimes sweet, occasionally heartbreaking, and utterly convincing in telling an origin story for friends turned foes Optimus Prime and Megatron. Thanks to its strong cast and a solid story buttressed by a classic heros journey,Transformers Onehas a spark that weve rarely seen in a Transformers flick outside of 2018sBumblebee.New on PeacockTwistersWhere to watch: Available to stream on PeacockGenre:Disaster thrillerRun time:2h 2mDirector:Lee Isaac ChungCast:Daisy Edgar-Jones, Glen Powell, Anthony RamosDirector Lee Isaac Chung follows up his 2020 breakthroughMinariwith a stand-alone sequel to the 1996 filmTwister. Starring Daisy Edgar-Jones and Glen Powell,Twistersfollows a dueling group of storm chasers as they attempt to navigate and survive a outbreak of tornadoes wreaking havoc through Oklahoma.New to rentMegalopolisWhere to watch: Available to rent on Amazon, Apple, and VuduGenre: Sci-fi dramaRun time: 2h 18mDirector: Francis Ford CoppolaCast: Adam Driver, Giancarlo Esposito, Nathalie EmmanuelFrancis Ford Coppola has returned with his first film in over a decade! Loosely inspired by the Catilinarian conspiracy of 63 B.C., Megalopolis stars Adam Driver as Cesar Catilina, a visionary architect and the scion of one of the ruling families of the city of New Rome. Cesar clashes with Franklyn Cicero (Giancarlo Esposito), the mayor of New Rome, over their respective visions for the future. The feud only intensifies after Ciceros daughter Julia (Nathalie Emmanuel) meets and subsequently falls in love with Cesar.Saturday NightWhere to watch: Available to rent on Amazon, Apple, and VuduGenre: Biographical comedyRun time: 1h 49mDirector: Jason ReitmanCast: Gabriel LaBelle, Rachel Sennott, Cory Michael SmithThis biographical comedy follows the 90 minutes leading up to the premiere of Saturday Night Live, with an ensemble cast playing some of the iconic comedians in the inaugural SNL lineup. Weve got Gabriel LaBelle as Lorne Michaels, Rachel Sennott as Rosie Shuster, Cory Michael Smith as Chevy Chase, Ella Hunt as Gilda Radner, Dylan OBrien as Dan Aykroyd, and more. The movie comes fromGhostbusters: Afterlife and Ghostbusters: Frozen Empireduo Jason Reitman and Gil Kenan, but critic reviews indicate its much better than those two.GoodrichWhere to watch: Available to rent on Amazon, Apple, and VuduGenre: ComedyRun time: 1h 50mDirector: Hallie Meyers-ShyerCast: Michael Keaton, Mila Kunis, Laura BenantiMichael Keaton stars in this family comedy as Andy, an art gallery owner whose wife leaves him and checks into a 90-day rehab program. With no one else to lean on, Andy resorts to asking Grace (Mila Kunis), his daughter from his previous marriage, to help him as he looks after her 9-year-old twin half-siblings.MagpieWhere to watch: Available to rent on Amazon, Apple, and VuduGenre: ThrillerRun time: 1h 30mDirector: Sam YatesCast: Shazad Latif, Daisy Ridley, Matilda LutzDaisy Ridley (Star Wars: The Last Jedi) and Shazad Latif (The Commuter) star in this new neo-noir thriller as Annette and Ben, a married couple whose daughter is cast in a new film. When Annette grows to suspect that Ben is having an affair with Alicia (Matilda Lutz), a famous actor who is their daughters castmate, their marriage begins to fracture prompting Annette to contemplate the unthinkable.Your MonsterWhere to watch: Available to rent on Amazon, Apple, and VuduGenre: Rom-com horrorRun time: 1h 43mDirector: Caroline LindyCast: Tommy Dewey, Melissa Barrera, Edmund DonovanMonster lovers out there this ones for you. A soft-spoken young actress going through a rough time in her life ends up falling for the literal monster in her closet. Well, at first, hes a bit of a prickly asshole la Beast fromBeauty and the Beast, but the two eventually become confidants before a romance sparks between them. Its based on director Caroline Lindys short film of the same name.0 Commentarios 0 Acciones 118 Views
WWW.POLYGON.COMDeadpool & Wolverine, Twisters, Netflixs Emilia Prez, and every movie new to streamingEach week on Polygon, we round up the most notable new releases to streaming and VOD, highlighting the biggest and best new movies for you to watch at home.This week, Deadpool & Wolverine, the 34th film in the Marvel Cinematic Universe and starring Ryan Reynolds and Hugh Jackman, arrives on Disney Plus following its VOD premiere early in October. Theres plenty of other new releases to enjoy this week, like Twisters on Peacock, Transformers One on Paramount Plus, the geri-action revenge comedy Thelma on Hulu, and the scintillating crime-drama musical Emilia Prez starring Zoe Saldaa (Guardians of the Galaxy Vol. 3) on Netflix. Not to mention a bunch of new movies arrive on VOD, like Francis Ford Coppolas Megalopolis starring Adam Driver (Star Wars: The Last Jedi) and Magpie starring Daisy Ridley (Star Wars: The Last Jedi).Heres everything new thats available to watch this weekend!New on NetflixEmilia PrezWhere to watch: Available to stream on NetflixGenre: Crime musicalRun time: 2h 12mDirector: Jacques AudiardCast: Zoe Saldaa, Karla Sofa Gascn, Selena GomezCannes Jury Prize winnerEmilia Prezis a crime film, a comedy,anda musical. Based on an opera libretto of the same name,Emilia Prezfollows a cartel leader who wants to complete her gender transition. She hires a lawyer to help her find a surgeon, fake her own death, and hide her family away for their safety. But Emilia cant quite run from her life of crime, and when she tries to reunite with her family, that shady past comes back to haunt her.Close to YouWhere to watch: Available to stream on NetflixGenre: DramaRun time: 1h 40mDirector: Dominic SavageCast: Elliot Page, Hillary Baack, Peter OuterbridgeElliot Page stars as a man named Sam who travels to his hometown for the first time in four years to celebrate his fathers birthday. In the face of familial tension, a lot involving his family struggling to accept his gender transition, Sam reconnects with an old flame.Close to Youpremiered at the 2023 Toronto International Film Festival, with critics praising Pages naturalistic performance.Widow ClicquotWhere to watch: Available to stream on NetflixGenre: DramaRun time: 1h 30mDirector: Thomas NapperCast: Haley Bennett, Tom Sturridge, Natasha OKeeffeThis period drama stars Haley Bennett (Swallow) as Barbe-Nicole Clicquot, the widow of an 18th-century vigneron who becomes the head of their fledgling vineyard after his untimely passing. Weathering financial difficulty and political turmoil, Barbe-Nicole must struggle to make a name for herself and nurture the company to fruition.Hot FrostyWhere to watch: Available to stream on NetflixGenre: Fantasy rom-comRun time: 1h 30mDirector: Jerry CiccorittiCast: Lacey Chabert, Dustin Milligan, Katy MixonThis questionably titled romantic comedy follows Kathy (Lacey Chabert), a recently widowed woman who finds herself alone for the holidays. After accidentally bringing a handsome snowman named Jack (Dustin Milligan) to life, Kathy quickly finds herself head over heels for our sexy new beau. As their relationship heats up, can both of them keep their cool?New on HuluThelmaWhere to watch: Available to stream on HuluGenre:Action comedyRun time:1h 38mDirector:Josh MargolinCast:June Squibb, Fred Hechinger, Richard RoundtreeThelma is a revenge flick about one woman journeying across Los Angeles to reclaim whats been taken from her and also she happens to be 93 years old, so a lot of that trekking is done on a senior mobility scooter.From ourreview:Thelma watches a Mission: Impossible film during the movie, and her Tom Cruise inspiration is not just there in spirit, but in the text itself. After she gets scammed, its seeing Cruises face on a magazine that inspires Thelma to take justice into her own hands. But that kind of sincerity wouldnt work withoutThelmas terrific and committed performances, particularly from Squibb and Roundtree. Both actors are terrifically funny, and Roundtrees charm gives the movie a tremendous amount of heart. For her part, Margolin says Squibb was adamant about owning the Tom Cruise mantle and doing as many stunts as she could herself.Its rare that a summer action movie also happens to be one of the funniest and sweetest movies of the year, butThelmamanages to pull it off. So if youre feeling the lack of Tom Cruise at movie theaters this year, just remember thatThelmaand June Squibb are there, carrying the torch in his honor.New on Disney PlusDeadpool & WolverineWhere to watch: Available to stream on MaxGenre:Superhero actionRun time:2h 8mDirector:Shawn LevyCast:Ryan Reynolds, Hugh Jackman, Emma CorrinRyan Reynolds reprises his role as Deadpool, the so-called Merc with a Mouth, in his first-ever appearance in the Marvel Cinematic Universe. After being abducted by the Time Variance Authority, Deadpool embarks on a quest to recruit an alternate universe version of Wolverine (Hugh Jackman) to help prevent his own universe from being destroyed. Matthew Macfadyen (Succession) plays Mr. Paradox, a rogue member of the TVA, and Emma Corrin (A Murder at the End of the World) portraysCassandra Nova, Professor Xs evil twin sister from an alternate universe.From ourreview:Deadpool & Wolverinehas made its hero the worst kind of comic book character: one who doesnt stand for anything. Its a terrible irony. Fans worried that Disneys corporate control and the MCUs rigid narrative oversight would leech away Deadpools edge: the swearing and the jocular violence. Turns out, that part was fine. Instead, the MCU just took his fuckin heart.New on Paramount PlusTransformers OneWhere to watch: Streaming on Paramount PlusGenre: Sci-fi adventureRun time: 1h 17mDirector: Josh CooleyCast: Chris Hemsworth, Brian Tyree Henry, Scarlett JohanssonThis animated prequel to the Transformers franchise chronicles the origins of Orion Pax (Chris Hemsworth) and D-16 (Brian Tyree Henry) years before they would later become known as Optimus Prime and Megatron. Set on the planet of Cybertron, Transformers One centers on Orion and D-16s friendship before a quirk of fate set them on the path to becoming bitter enemies.From our review:Director Josh Cooleys semi-reboot of the Transformers cinematic universe whether it has any association with the Transformers Bay-verse is somehow unclear is better than its prequel premise (andtrailers) suggests.Transformers Oneis funny, sometimes sweet, occasionally heartbreaking, and utterly convincing in telling an origin story for friends turned foes Optimus Prime and Megatron. Thanks to its strong cast and a solid story buttressed by a classic heros journey,Transformers Onehas a spark that weve rarely seen in a Transformers flick outside of 2018sBumblebee.New on PeacockTwistersWhere to watch: Available to stream on PeacockGenre:Disaster thrillerRun time:2h 2mDirector:Lee Isaac ChungCast:Daisy Edgar-Jones, Glen Powell, Anthony RamosDirector Lee Isaac Chung follows up his 2020 breakthroughMinariwith a stand-alone sequel to the 1996 filmTwister. Starring Daisy Edgar-Jones and Glen Powell,Twistersfollows a dueling group of storm chasers as they attempt to navigate and survive a outbreak of tornadoes wreaking havoc through Oklahoma.New to rentMegalopolisWhere to watch: Available to rent on Amazon, Apple, and VuduGenre: Sci-fi dramaRun time: 2h 18mDirector: Francis Ford CoppolaCast: Adam Driver, Giancarlo Esposito, Nathalie EmmanuelFrancis Ford Coppola has returned with his first film in over a decade! Loosely inspired by the Catilinarian conspiracy of 63 B.C., Megalopolis stars Adam Driver as Cesar Catilina, a visionary architect and the scion of one of the ruling families of the city of New Rome. Cesar clashes with Franklyn Cicero (Giancarlo Esposito), the mayor of New Rome, over their respective visions for the future. The feud only intensifies after Ciceros daughter Julia (Nathalie Emmanuel) meets and subsequently falls in love with Cesar.Saturday NightWhere to watch: Available to rent on Amazon, Apple, and VuduGenre: Biographical comedyRun time: 1h 49mDirector: Jason ReitmanCast: Gabriel LaBelle, Rachel Sennott, Cory Michael SmithThis biographical comedy follows the 90 minutes leading up to the premiere of Saturday Night Live, with an ensemble cast playing some of the iconic comedians in the inaugural SNL lineup. Weve got Gabriel LaBelle as Lorne Michaels, Rachel Sennott as Rosie Shuster, Cory Michael Smith as Chevy Chase, Ella Hunt as Gilda Radner, Dylan OBrien as Dan Aykroyd, and more. The movie comes fromGhostbusters: Afterlife and Ghostbusters: Frozen Empireduo Jason Reitman and Gil Kenan, but critic reviews indicate its much better than those two.GoodrichWhere to watch: Available to rent on Amazon, Apple, and VuduGenre: ComedyRun time: 1h 50mDirector: Hallie Meyers-ShyerCast: Michael Keaton, Mila Kunis, Laura BenantiMichael Keaton stars in this family comedy as Andy, an art gallery owner whose wife leaves him and checks into a 90-day rehab program. With no one else to lean on, Andy resorts to asking Grace (Mila Kunis), his daughter from his previous marriage, to help him as he looks after her 9-year-old twin half-siblings.MagpieWhere to watch: Available to rent on Amazon, Apple, and VuduGenre: ThrillerRun time: 1h 30mDirector: Sam YatesCast: Shazad Latif, Daisy Ridley, Matilda LutzDaisy Ridley (Star Wars: The Last Jedi) and Shazad Latif (The Commuter) star in this new neo-noir thriller as Annette and Ben, a married couple whose daughter is cast in a new film. When Annette grows to suspect that Ben is having an affair with Alicia (Matilda Lutz), a famous actor who is their daughters castmate, their marriage begins to fracture prompting Annette to contemplate the unthinkable.Your MonsterWhere to watch: Available to rent on Amazon, Apple, and VuduGenre: Rom-com horrorRun time: 1h 43mDirector: Caroline LindyCast: Tommy Dewey, Melissa Barrera, Edmund DonovanMonster lovers out there this ones for you. A soft-spoken young actress going through a rough time in her life ends up falling for the literal monster in her closet. Well, at first, hes a bit of a prickly asshole la Beast fromBeauty and the Beast, but the two eventually become confidants before a romance sparks between them. Its based on director Caroline Lindys short film of the same name.0 Commentarios 0 Acciones 118 Views -
 WWW.POLYGON.COMCritical Roles fake romantasy novel Tusk Love to be real novel in 2025Fans of Critical Roles second campaign are in for a spicy treat. Penguin Random House announced it will publish the tabletop media empires newest novel, Tusk Love. The fictional smutty romance that started off as an inside joke on the popular actual play has taken on a new, very real, life thanks to their partnership with the traditional publishing house.Written by New York Times bestselling author Thea Guazon, Tusk Love builds on the recent resurgence of the Romantasy genre, alongside A Court of Thorns and Roses and Fourth Wing. While not set in the world of Exandria, Tusk Love has held a special place in the heart of many Critical Role fans, popping up throughout the adventures of the Mighty Nein and making a special appearance in the Legends of Vox Machina animated series. Romantic fans of the actual play pined as Laura Baileys tiefling character Jester Lavorre made allusions to the book while she pursued her romantic interest Fjord (played by Baileys real world husband Travis Willingham).According to the description on the Critical Role books page, the plot of the novel follows the beats one would expect from Jesters favorite romance. Jesters self-insert Guinevere is the daughter of an ambitious merchant (much like the character herself), determined by birth to marry into a noble house and live quietly as a lordlings obedient life. But she wants more. When her caravan is attacked by bandits, Guinevere is saved by the stoic Oskar (Jesters head canon Fjord fantasy), who thinks shes little more than a spoiled waif. The two must put aside their differences to survive the dangerous Amber Road, doing everything in their power to ignore their growing passion as they must choose between the lives that have been chosen for them, or the one they make for themselves.Tusk Love will be Critical Roles seventh book published in partnership with big-five publisher Penguin Random House. Their previous publications include prequel novels such as Kith and Kin by Marieke Nijkamp, The Nine Eyes of Lucien by Madelein Roux, and What Doesnt Break by Cassandra Khaw; along side the official Exquisite Exandria Cook Book, The World of Critical Role production guide, and Critical Role Mad Libs. Tusk Love is set to debut in July 2025, available for $30 wherever books are sold.0 Commentarios 0 Acciones 148 Views
WWW.POLYGON.COMCritical Roles fake romantasy novel Tusk Love to be real novel in 2025Fans of Critical Roles second campaign are in for a spicy treat. Penguin Random House announced it will publish the tabletop media empires newest novel, Tusk Love. The fictional smutty romance that started off as an inside joke on the popular actual play has taken on a new, very real, life thanks to their partnership with the traditional publishing house.Written by New York Times bestselling author Thea Guazon, Tusk Love builds on the recent resurgence of the Romantasy genre, alongside A Court of Thorns and Roses and Fourth Wing. While not set in the world of Exandria, Tusk Love has held a special place in the heart of many Critical Role fans, popping up throughout the adventures of the Mighty Nein and making a special appearance in the Legends of Vox Machina animated series. Romantic fans of the actual play pined as Laura Baileys tiefling character Jester Lavorre made allusions to the book while she pursued her romantic interest Fjord (played by Baileys real world husband Travis Willingham).According to the description on the Critical Role books page, the plot of the novel follows the beats one would expect from Jesters favorite romance. Jesters self-insert Guinevere is the daughter of an ambitious merchant (much like the character herself), determined by birth to marry into a noble house and live quietly as a lordlings obedient life. But she wants more. When her caravan is attacked by bandits, Guinevere is saved by the stoic Oskar (Jesters head canon Fjord fantasy), who thinks shes little more than a spoiled waif. The two must put aside their differences to survive the dangerous Amber Road, doing everything in their power to ignore their growing passion as they must choose between the lives that have been chosen for them, or the one they make for themselves.Tusk Love will be Critical Roles seventh book published in partnership with big-five publisher Penguin Random House. Their previous publications include prequel novels such as Kith and Kin by Marieke Nijkamp, The Nine Eyes of Lucien by Madelein Roux, and What Doesnt Break by Cassandra Khaw; along side the official Exquisite Exandria Cook Book, The World of Critical Role production guide, and Critical Role Mad Libs. Tusk Love is set to debut in July 2025, available for $30 wherever books are sold.0 Commentarios 0 Acciones 148 Views -
 DESIGN-MILK.COM2024 Modern Gift Ideas From Social Media Consultant Maivy TranI like to think everyday moments can be transformed by the right objects a little beauty here, a bit of comfort there. This guide brings together pieces that make routine things feel a little more intentional, each one thoughtfully chosen from my personal wish list to yours! Here are 10 things Id love to gift (or keep for myself!) because they dont just fill a space; they elevate it.Dusen Dusen Slippers \\\ $48Imagine stepping into these slippers every morning youd never have a bad start to your day again! Made in Portugal and Oeko-Tex certified, theyre the ultimate modern-meets-fun gift for anyone who loves a little personality even if its just for lounging around the house. Perfect for those lazy Sundays or adding a bit of cheer, these vibrant stripes bring a bit of oomph to any downtime look.Instax Mini LiPlay \\\ $160I know I have an ancient Instax tucked in a drawer somewhere, but its for a good reason! Those older models were big, bulky, and somehow never captured exactly what I was aiming for. Not anymore! The new Instax Mini LiPlay is perfectly pocket-sized so you can take it anywhere and everywhere. It even doubles as a smartphone printer, so those spontaneous snapshots dont just stay digital! Additionally with its remote shooting feature, getting everyone in the frame has never been easier. Its everything you loved about the classic Instax, now reimagined for todays on-the-go moments.OWIU Goods Candle \\\ $98Ive always adored OWIU Goods handcrafted pieces, and they recently expanded their MATTER line to include candles! Each one takes you on a unique scent journey, like taking a stroll through lush forests or basking in the warmth of island vibes, offering over 40 hours of blissful ambiance. The best part? Once the wax melts away, the stunning vessels can be repurposed as cups or bud vases, keeping the good vibes flowing long after the flame goes out!Open Spaces Pour Over Carafe and Double Wall Glasses \\\ $112After realizing my glass collection was basically a mix of brewery freebies and Marshalls finds, Ive been on the hunt for an upgrade. This bundle brings the sophistication and minimalist charm Ive been looking for! Whether youre pouring coffee, tea, or even a sneaky sangria (my favorite), this duo has you covered with style and durability to match. Cheers to sipping in style!Hommey Robe \\\ $129Theres just something about slipping into a robe that brings an instant upgrade to my daily routine like Im stepping into a fancy hotel, except its right here at home. Hommeys 100% cotton robes are all about comfort without compromise, designed for anything from slow winter mornings to breezy poolside evenings. I love the soft, subtle contrasting colors of this one; an elevated take on the classic pinstripe, its stylish without trying too hard!Daily Rituals Shower Steamers \\\ $24.75Shower steamers are the little pick-me-up I never knew I needed! Perfect for those who want to add a touch of luxury to their routine, they make the whole experience feel less like a chore and more like a daily indulgence. Just pop one on the shower floor, and let the steam do the rest suddenly, youre not just showering; youre unwinding. Whether its for yourself or someone in need of a little pampering, this gift set comes with four delightful scents and a stylish bamboo plate, making it easy to discover your favorite aroma.Kindred Spirits by Stephanie Wahler \\\ $19.95I love a fun date night, and this playful cocktail book brings couples closer together, one sip at a time! Packed with 40 delightful recipes organized by type of date, it serves up everything from espresso martinis to refreshing spritzes while inspiring creative activities. From enjoying cozy movie nights with Hottie Toddies to planning romantic picnics in the park, Kindred Spirits makes it easy to shake things up and keep the romance alive.Lo & Sons Weekender \\\ $150.50Ive become a bit of a homebody lately, but Im hoping to change things up with some local getaways next year, and this stylish weekender bag might be all the push I need! Thoughtfully designed with a separate shoe compartment, cushioned strap, and eco-friendly canvas, its ready for everything from gym runs to mini-escapes. Its travel-savvy, durable, and the perfect companion for a spontaneous weekend away.Tekla Bath Towel \\\ $90Bath towels might seem like a boring gift; however, Id argue theyre anything but especially if its from Tekla! Crafted from 100% organic cotton with a lush, mid-weight terry weave, these towels are incredibly soft while being super absorbent. Also, those dark green stripes on bright white? *immediately add to cart*Guten Co. Home Concentric Coasters \\\ $48I was hunting for coasters that could pull double duty on my bedside table something functional and decorative and found these beauties! Handcrafted from speckled stoneware with a dreamy spiral design, theyre perfect for catching those rogue water drops while adding an earthy, artistic touch to my space. They come in Forest, Cobalt, and Natural Speckle; Forest was my top pick (which is sadly sold out), but Cobalts a close second!Follow along so you dont miss any of our2024 Gift Guidesthis year!This post contains affiliate links, so if you make a purchase from an affiliate link, we earn a commission. Thanks for supporting Design Milk!0 Commentarios 0 Acciones 135 Views
DESIGN-MILK.COM2024 Modern Gift Ideas From Social Media Consultant Maivy TranI like to think everyday moments can be transformed by the right objects a little beauty here, a bit of comfort there. This guide brings together pieces that make routine things feel a little more intentional, each one thoughtfully chosen from my personal wish list to yours! Here are 10 things Id love to gift (or keep for myself!) because they dont just fill a space; they elevate it.Dusen Dusen Slippers \\\ $48Imagine stepping into these slippers every morning youd never have a bad start to your day again! Made in Portugal and Oeko-Tex certified, theyre the ultimate modern-meets-fun gift for anyone who loves a little personality even if its just for lounging around the house. Perfect for those lazy Sundays or adding a bit of cheer, these vibrant stripes bring a bit of oomph to any downtime look.Instax Mini LiPlay \\\ $160I know I have an ancient Instax tucked in a drawer somewhere, but its for a good reason! Those older models were big, bulky, and somehow never captured exactly what I was aiming for. Not anymore! The new Instax Mini LiPlay is perfectly pocket-sized so you can take it anywhere and everywhere. It even doubles as a smartphone printer, so those spontaneous snapshots dont just stay digital! Additionally with its remote shooting feature, getting everyone in the frame has never been easier. Its everything you loved about the classic Instax, now reimagined for todays on-the-go moments.OWIU Goods Candle \\\ $98Ive always adored OWIU Goods handcrafted pieces, and they recently expanded their MATTER line to include candles! Each one takes you on a unique scent journey, like taking a stroll through lush forests or basking in the warmth of island vibes, offering over 40 hours of blissful ambiance. The best part? Once the wax melts away, the stunning vessels can be repurposed as cups or bud vases, keeping the good vibes flowing long after the flame goes out!Open Spaces Pour Over Carafe and Double Wall Glasses \\\ $112After realizing my glass collection was basically a mix of brewery freebies and Marshalls finds, Ive been on the hunt for an upgrade. This bundle brings the sophistication and minimalist charm Ive been looking for! Whether youre pouring coffee, tea, or even a sneaky sangria (my favorite), this duo has you covered with style and durability to match. Cheers to sipping in style!Hommey Robe \\\ $129Theres just something about slipping into a robe that brings an instant upgrade to my daily routine like Im stepping into a fancy hotel, except its right here at home. Hommeys 100% cotton robes are all about comfort without compromise, designed for anything from slow winter mornings to breezy poolside evenings. I love the soft, subtle contrasting colors of this one; an elevated take on the classic pinstripe, its stylish without trying too hard!Daily Rituals Shower Steamers \\\ $24.75Shower steamers are the little pick-me-up I never knew I needed! Perfect for those who want to add a touch of luxury to their routine, they make the whole experience feel less like a chore and more like a daily indulgence. Just pop one on the shower floor, and let the steam do the rest suddenly, youre not just showering; youre unwinding. Whether its for yourself or someone in need of a little pampering, this gift set comes with four delightful scents and a stylish bamboo plate, making it easy to discover your favorite aroma.Kindred Spirits by Stephanie Wahler \\\ $19.95I love a fun date night, and this playful cocktail book brings couples closer together, one sip at a time! Packed with 40 delightful recipes organized by type of date, it serves up everything from espresso martinis to refreshing spritzes while inspiring creative activities. From enjoying cozy movie nights with Hottie Toddies to planning romantic picnics in the park, Kindred Spirits makes it easy to shake things up and keep the romance alive.Lo & Sons Weekender \\\ $150.50Ive become a bit of a homebody lately, but Im hoping to change things up with some local getaways next year, and this stylish weekender bag might be all the push I need! Thoughtfully designed with a separate shoe compartment, cushioned strap, and eco-friendly canvas, its ready for everything from gym runs to mini-escapes. Its travel-savvy, durable, and the perfect companion for a spontaneous weekend away.Tekla Bath Towel \\\ $90Bath towels might seem like a boring gift; however, Id argue theyre anything but especially if its from Tekla! Crafted from 100% organic cotton with a lush, mid-weight terry weave, these towels are incredibly soft while being super absorbent. Also, those dark green stripes on bright white? *immediately add to cart*Guten Co. Home Concentric Coasters \\\ $48I was hunting for coasters that could pull double duty on my bedside table something functional and decorative and found these beauties! Handcrafted from speckled stoneware with a dreamy spiral design, theyre perfect for catching those rogue water drops while adding an earthy, artistic touch to my space. They come in Forest, Cobalt, and Natural Speckle; Forest was my top pick (which is sadly sold out), but Cobalts a close second!Follow along so you dont miss any of our2024 Gift Guidesthis year!This post contains affiliate links, so if you make a purchase from an affiliate link, we earn a commission. Thanks for supporting Design Milk!0 Commentarios 0 Acciones 135 Views -
 DESIGN-MILK.COMArchive for Space Presents the Paper-Like Alu CollectionScrolls are usually a delicate papyrus or pressed fiber pulp, surviving (or not) over centuries with essential information about our histories. They contain stories, personal accounts, journals, all filled with our ancestors thoughts and musings. With the Alu collection by Archive for Space, these notions are upended and upheld simultaneously. Presented by Bton Brut, these meticulously hand wrought aluminum sheets transform humble stock product into fanciful seating. The Alu collection includes the Stool 001, Seat 001, and Bench 001.The aluminum is finished uniquely, minimally changed after production to eventually patina over time. All unfinished metals, and even finished ones, will develop a natural oxidation layer over time, infusing the surface with depth and ranges of color. This will be especially interesting to see how this forms on a chair or stool of this nature, natural oils from hands working passively to produce a unique texture based on use patterns. Similar to the allure of raw denim, the customization and craft is in the actual use of the product, allowing the finish to speak for itself.For now, the Alu collection sits in its original light, brushed aluminum finish. The arc of the seat is expressive, wide and inviting. One would almost imagine the smallest amount of give, highlighting its primary function. The interplay of light between the rounded forms changes by the hour, inviting interest at any time of day.Incredibly light but strong, aluminum is an apt material for paper-like seating. The thickness of the metal couldnt be more than a couple millimeters, adding to the grace and elegance of the form. Similar to an old-world ribbon on a statue, flowing in time yet set it stone, the Alu collection gives life to aluminum, allowing it to shine as a material.Archive for Space founders Arabella Maza and Stephen MaginnArchive for Space is a multidisciplinary design studio based in London and Mallorca, ranging from interiors and architecture to generative art and set design. This is deeply informed by historical and cultural context, neatly categorized in the Archive, a database of inspiration from stories less told. Expanding on their ethos, they explain, We are ardent advocates of knowledge dissemination, for we believe that design flourishes when it thrives upon collective brilliance. The Archive hopefully unfurls a deeper understanding of design through our practices distinctive lens.Founded in 2013 by Sophie Pearce, Bton Brut has quickly become a magnet for the best design from Europe and Japan. Working with both private and trade clients, their capabilities in luxury furnishing and staging are unmatched. Named after the brutalist concrete finish found in modern architecture, Bton Brut stays true original, uncompromising, and honest mirroring self with reflection.For more on Archive for Space, click here,and for more on Bton Brut, click here.Photography by Thea Lvstad.0 Commentarios 0 Acciones 107 Views
DESIGN-MILK.COMArchive for Space Presents the Paper-Like Alu CollectionScrolls are usually a delicate papyrus or pressed fiber pulp, surviving (or not) over centuries with essential information about our histories. They contain stories, personal accounts, journals, all filled with our ancestors thoughts and musings. With the Alu collection by Archive for Space, these notions are upended and upheld simultaneously. Presented by Bton Brut, these meticulously hand wrought aluminum sheets transform humble stock product into fanciful seating. The Alu collection includes the Stool 001, Seat 001, and Bench 001.The aluminum is finished uniquely, minimally changed after production to eventually patina over time. All unfinished metals, and even finished ones, will develop a natural oxidation layer over time, infusing the surface with depth and ranges of color. This will be especially interesting to see how this forms on a chair or stool of this nature, natural oils from hands working passively to produce a unique texture based on use patterns. Similar to the allure of raw denim, the customization and craft is in the actual use of the product, allowing the finish to speak for itself.For now, the Alu collection sits in its original light, brushed aluminum finish. The arc of the seat is expressive, wide and inviting. One would almost imagine the smallest amount of give, highlighting its primary function. The interplay of light between the rounded forms changes by the hour, inviting interest at any time of day.Incredibly light but strong, aluminum is an apt material for paper-like seating. The thickness of the metal couldnt be more than a couple millimeters, adding to the grace and elegance of the form. Similar to an old-world ribbon on a statue, flowing in time yet set it stone, the Alu collection gives life to aluminum, allowing it to shine as a material.Archive for Space founders Arabella Maza and Stephen MaginnArchive for Space is a multidisciplinary design studio based in London and Mallorca, ranging from interiors and architecture to generative art and set design. This is deeply informed by historical and cultural context, neatly categorized in the Archive, a database of inspiration from stories less told. Expanding on their ethos, they explain, We are ardent advocates of knowledge dissemination, for we believe that design flourishes when it thrives upon collective brilliance. The Archive hopefully unfurls a deeper understanding of design through our practices distinctive lens.Founded in 2013 by Sophie Pearce, Bton Brut has quickly become a magnet for the best design from Europe and Japan. Working with both private and trade clients, their capabilities in luxury furnishing and staging are unmatched. Named after the brutalist concrete finish found in modern architecture, Bton Brut stays true original, uncompromising, and honest mirroring self with reflection.For more on Archive for Space, click here,and for more on Bton Brut, click here.Photography by Thea Lvstad.0 Commentarios 0 Acciones 107 Views -
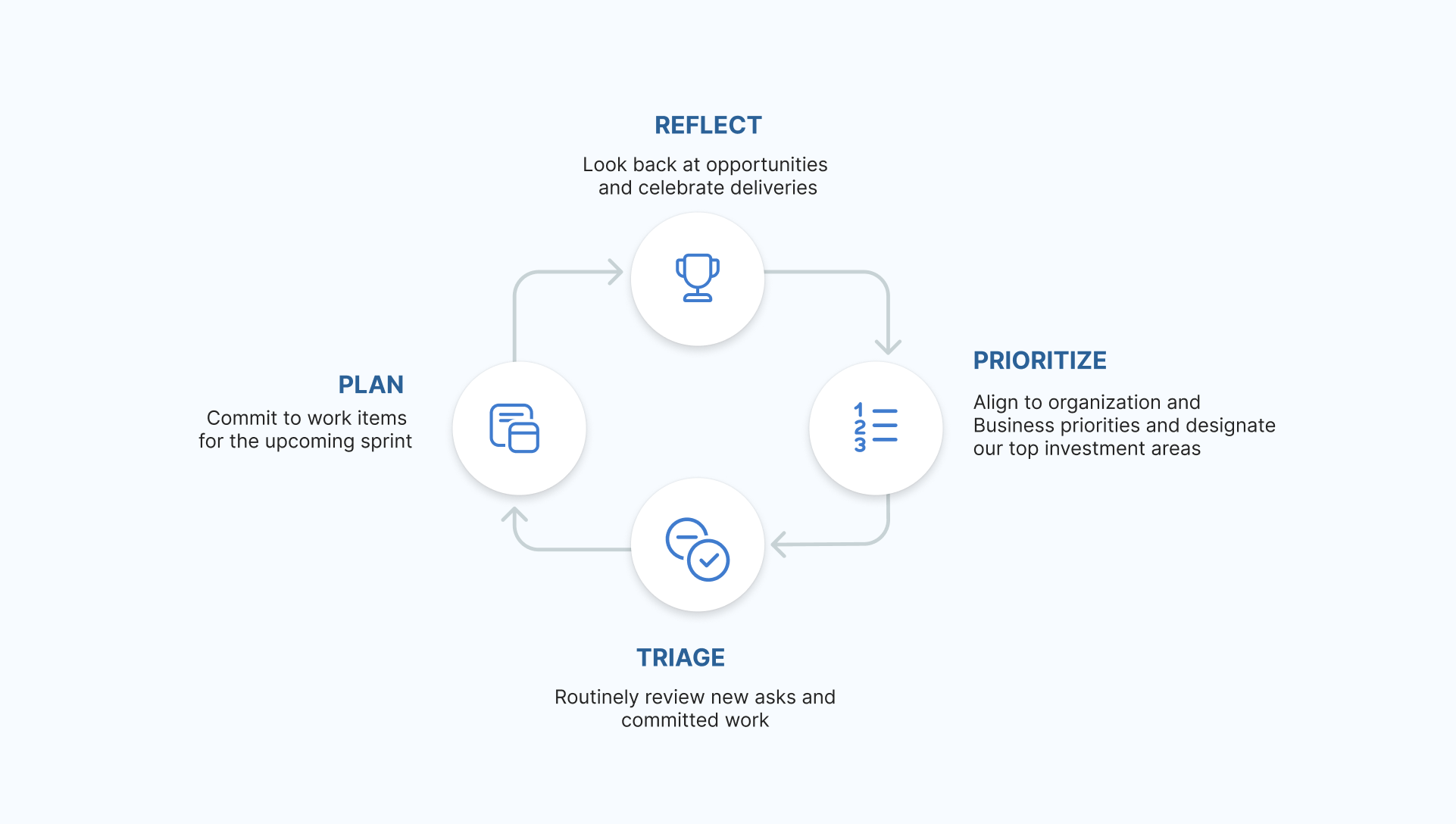 UXDESIGN.CCContinuous planning for UX teamsManage UX backlogs the Agile wayContinue reading on UX Collective0 Commentarios 0 Acciones 126 Views
UXDESIGN.CCContinuous planning for UX teamsManage UX backlogs the Agile wayContinue reading on UX Collective0 Commentarios 0 Acciones 126 Views



