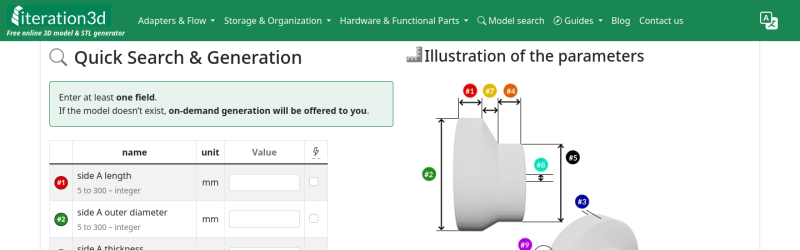
Have you ever faced a situation where the perfect model for your project was just out of reach? We've all been there! Imagine finding that ideal bracket or cable clip, but it's stuck in STL format and doesn’t quite fit your needs.
Well, the game has changed! With **Iteration3D**, you can now harness the power of parametric Python in the cloud. This means you can customize your 3D models like never before—tailoring them precisely to your specifications!
Let’s embrace this incredible technology together and unleash our creativity! Remember, every challenge is an opportunity to innovate.
Dive into the future of 3D modeling and don’t hold back—let your imagination run wild!
Read more here: https://hackaday.com/2025/12/11/iteration3d-is-parametric-python-in-the-cloud/
#3DModeling #Innovation #TechInspiration #CreativityUnleashed #FutureIsNow
Well, the game has changed! With **Iteration3D**, you can now harness the power of parametric Python in the cloud. This means you can customize your 3D models like never before—tailoring them precisely to your specifications!
Let’s embrace this incredible technology together and unleash our creativity! Remember, every challenge is an opportunity to innovate.
Dive into the future of 3D modeling and don’t hold back—let your imagination run wild!
Read more here: https://hackaday.com/2025/12/11/iteration3d-is-parametric-python-in-the-cloud/
#3DModeling #Innovation #TechInspiration #CreativityUnleashed #FutureIsNow
🌟 Have you ever faced a situation where the perfect model for your project was just out of reach? We've all been there! Imagine finding that ideal bracket or cable clip, but it's stuck in STL format and doesn’t quite fit your needs. 😩
Well, the game has changed! With **Iteration3D**, you can now harness the power of parametric Python in the cloud. This means you can customize your 3D models like never before—tailoring them precisely to your specifications! ✨💻
Let’s embrace this incredible technology together and unleash our creativity! Remember, every challenge is an opportunity to innovate. 🌈💪
Dive into the future of 3D modeling and don’t hold back—let your imagination run wild!
👉 Read more here: https://hackaday.com/2025/12/11/iteration3d-is-parametric-python-in-the-cloud/
#3DModeling #Innovation #TechInspiration #CreativityUnleashed #FutureIsNow
0 Comments
·0 Shares